Featured Post
Blog Not Found !
Blog
Explore security-first insights and the latest from Scrut, to help you build resiliant and compliant security programs.


Learn from the latest blogs by our community
Thank you! Your submission has been received!
Oops! Something went wrong while submitting the form.
No item found.





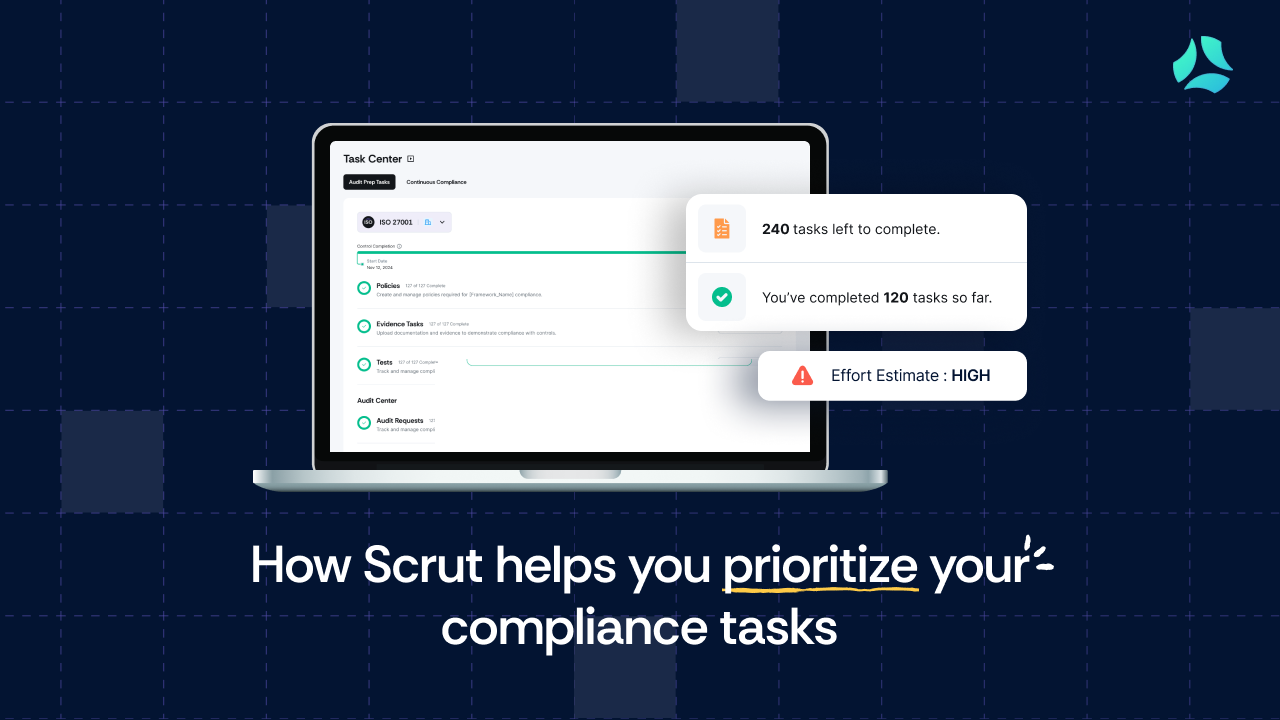






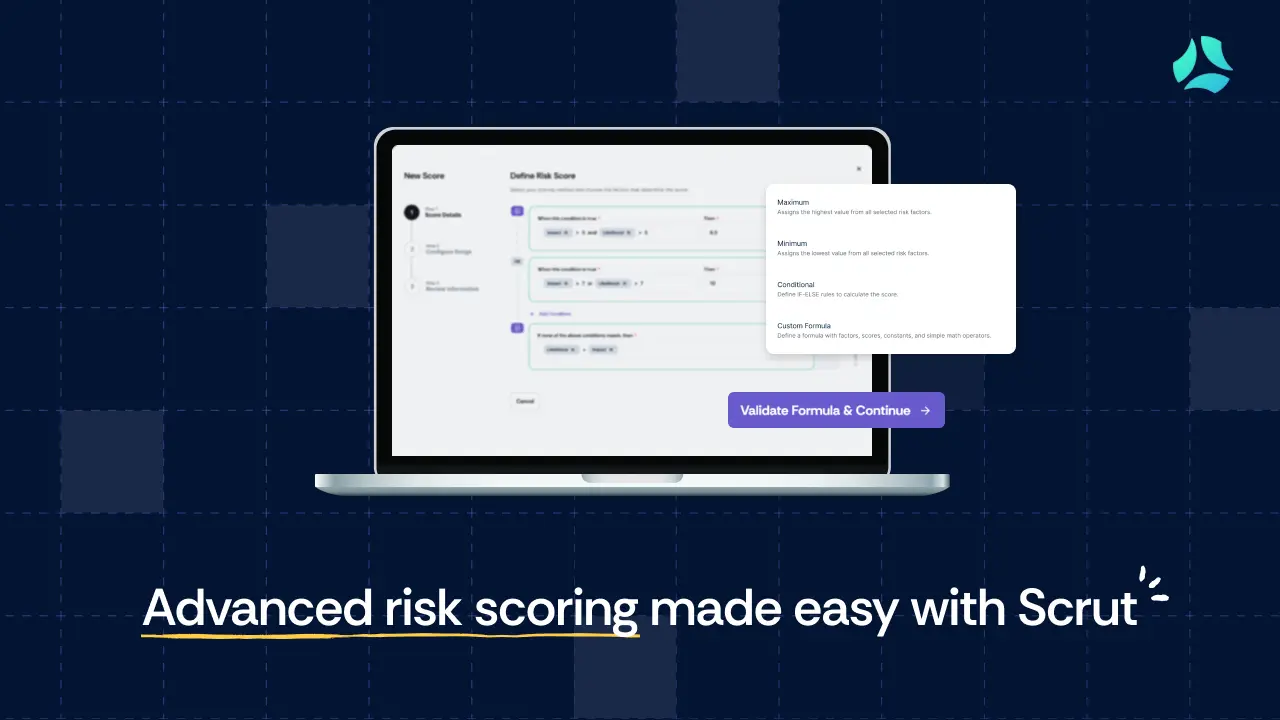




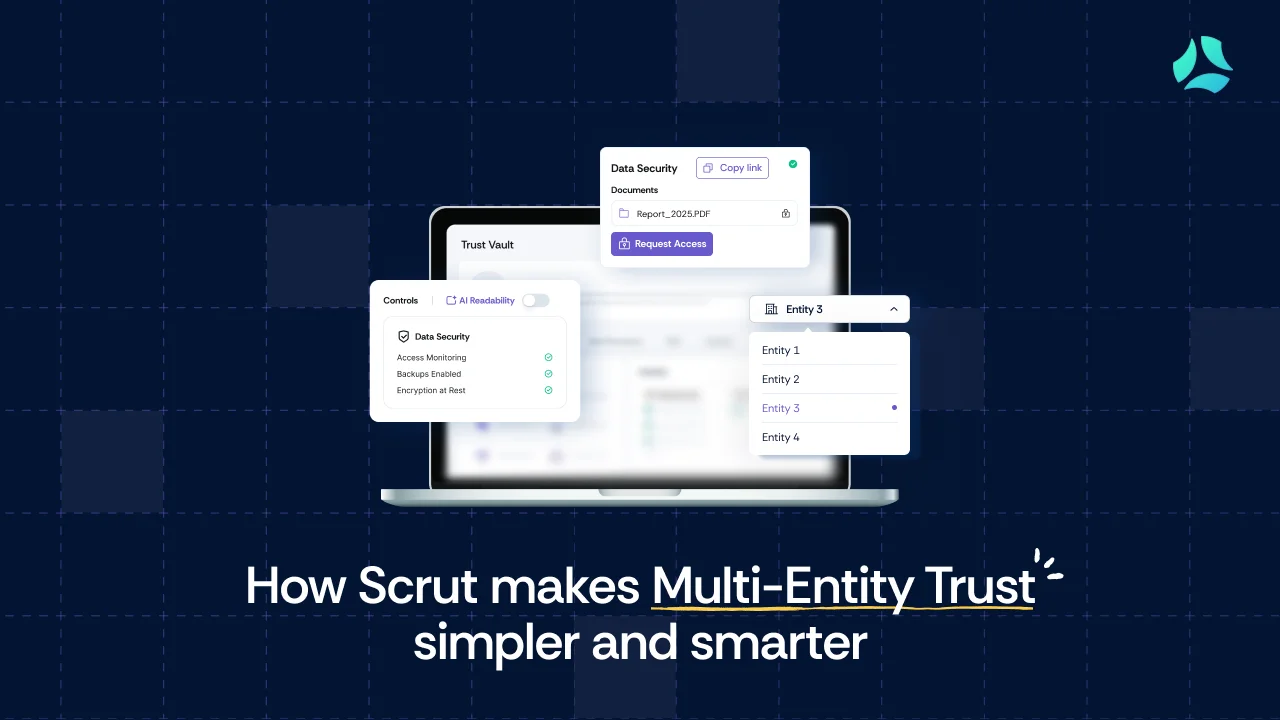












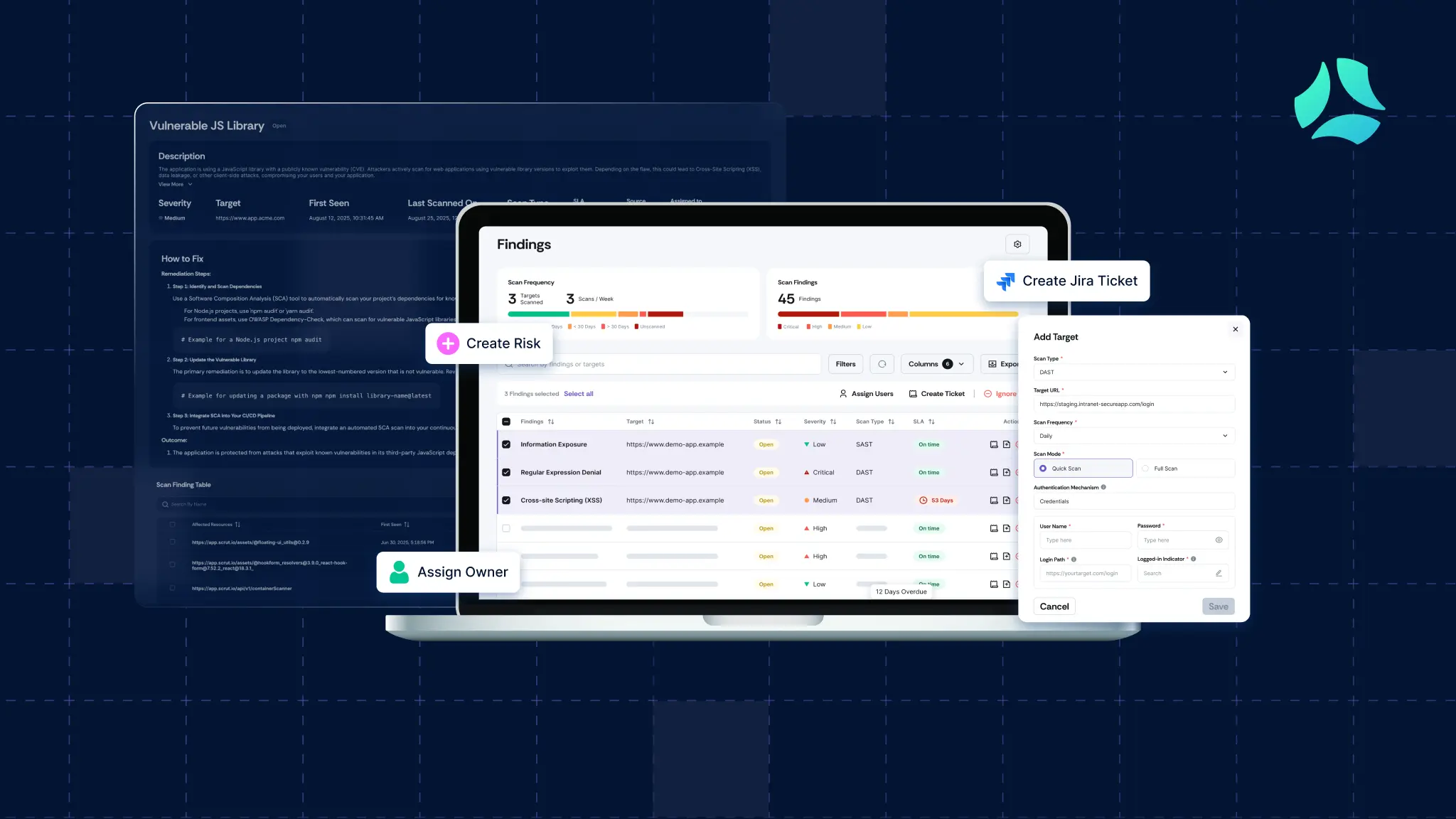









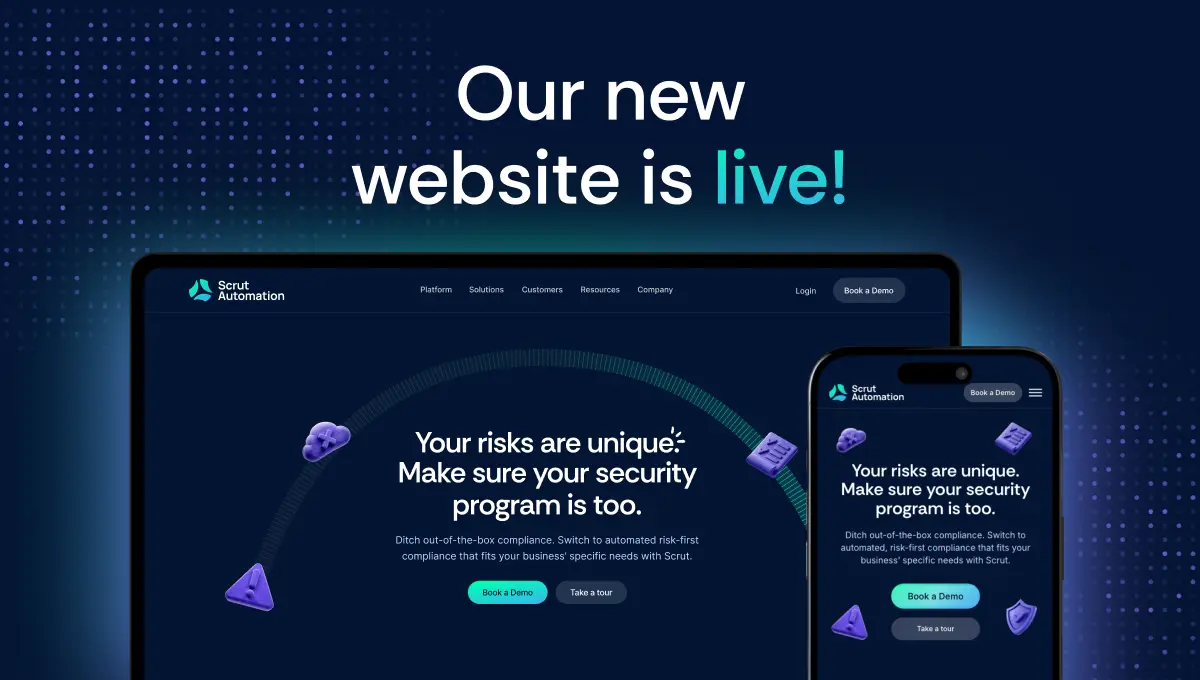














































.webp)












.webp)






.webp)
.webp)































.png)
.png)


.png)



.webp)



































.webp)















.png)











.webp)






















