Choose risk-first compliance that’s always on, built for you.
Go back to blogs
HIPAA Compliance Checklist: Implementation & Free Template
Last updated on
September 16, 2025
min. read

The Health Insurance Portability and Accountability Act (HIPAA) sets the standard for how healthcare organizations safeguard Protected Health Information (PHI), but for technical teams, it often becomes the rulebook that defines day-to-day security architecture and operations. Whether you’re running an electronic health record (EHR) system, designing APIs for patient data exchange, or maintaining cloud infrastructure that stores PHI, the stakes are high. A single misstep can mean hefty fines, reputational damage, or worse, compromising patient trust.
That’s where a structured HIPAA compliance checklist comes in. Instead of scrambling to interpret the legal jargon, technical leaders can use a checklist to translate requirements into concrete, actionable steps: configure access controls, encrypt PHI at rest and in transit, monitor logs, and maintain clear audit trails.
In this blog, you’ll find a detailed breakdown of HIPAA requirements mapped into a practical checklist. We’ll also share a downloadable template you can adapt for your own environment, helping your teams stay audit-ready without drowning in documentation.
Key requirements under HIPAA
HIPAA is not a single law but a collection of interrelated rules that together define how healthcare organizations, their business associates, and their vendors must handle PHI. Each rule sets specific expectations: some high-level, others deeply technical.

1. Privacy Rule
The Privacy Rule establishes the baseline: how PHI can be used and disclosed. It applies to all forms of PHI, electronic, paper, and oral. Technical teams may not directly configure privacy policies, but their systems must support them, for example:
- Implementing role-based access so only authorized personnel can access PHI.
- Logging disclosures and ensuring system capabilities to honor patient rights (like data access or amendment requests).
2. Security Rule
The Security Rule zeroes in on ePHI (electronic PHI) and outlines three safeguard categories:
- Administrative safeguards: Risk assessments, workforce training, access management, and contingency planning.
- Physical safeguards: Controlling physical access to servers, devices, and facilities.
- Technical safeguards: Access controls, audit logging, encryption, and integrity protections.
This is the rule with the heaviest technical lift, as it dictates system configurations, monitoring, and cloud security practices.
3. Breach Notification Rule
This rule requires covered entities and business associates to notify affected individuals, HHS (the U.S. Department of Health and Human Services), and sometimes the media, after a data breach. From a technical perspective, this means:
- Implementing monitoring to detect unauthorized access quickly.
- Maintaining audit trails that can confirm or disprove PHI compromise.
- Documenting incident response steps for compliance proof.
4. Enforcement Rule
The Enforcement Rule lays out how HIPAA is enforced by HHS, including investigation procedures, penalties, and resolution agreements. While not technical in nature, it reinforces why precise documentation, automated monitoring, and thorough audit readiness are critical; fines escalate quickly when violations are tied to systemic negligence.
5. Omnibus Rule
The Omnibus Rule (2013) expanded HIPAA’s scope. It clarified the responsibilities of business associates (cloud service providers, billing vendors, SaaS partners), strengthened patient rights, and increased penalty structures. For technical teams, the key takeaway is this: vendors handling PHI are directly accountable, and their integrations and configurations must meet HIPAA standards.
Together, these rules form the compliance foundation. The Privacy Rule defines “what” must be protected, the Security Rule defines “how,” and the Breach Notification, Enforcement, and Omnibus Rules ensure accountability when safeguards fail or gaps are ignored.
How to implement HIPAA compliance: A step-by-step guide
Understanding HIPAA’s requirements is one thing; translating them into daily technical operations is another. The rules define what you must do, but the real challenge is figuring out how to do it in your own environment. That’s where a structured, step-by-step approach helps.
The following guide breaks the journey into four clear phases so your teams can move from interpreting regulations to running systems that actually meet them. Think of it as the practical path from policy to implementation, with checkpoints along the way that keep you audit-ready and reduce the risk of costly missteps.
Phase 1: Foundation and scoping
- Scope your environment and data flows
Map where PHI and ePHI live, how they move, and who touches them. Confirm whether you are a covered entity, a business associate, or both. List systems, APIs, cloud services, and data stores tied to PHI.
- Stand-up governance
Appoint a Privacy Officer and a Security Officer, set up a steering group, and agree on approval paths for policies and exceptions. Keep minutes and decisions—these records matter during enforcement reviews.
- Execute business associate agreements
Identify every vendor that creates, receives, maintains, or transmits PHI on your behalf. Execute BAAs that meet HIPAA content requirements and track renewal dates in a register.
Phase 2: Risk management and safeguards
- Run a security risk analysis
Conduct a documented “accurate and thorough” risk analysis covering confidentiality, integrity, and availability of ePHI. Include inventories, threat models, vulnerability scans, and likelihood/impact scoring.
- Build and execute your risk management plan
Translate risks into mitigations with clear owners and deadlines. Track residual risk after treatment.
- Implement administrative safeguards
Apply access authorization, security awareness training, sanction policies, incident response procedures, and contingency planning (backup, DR, emergency mode).
- Implement physical safeguards
Secure facilities, restrict workstation access, and enforce device/media handling and disposal policies.
- Implement technical safeguards
Configure access controls, audit logging, encryption, automatic logoff, and integrity protections. Document choices where HIPAA defines a safeguard as “addressable.”
Phase 3: Operational execution
- Document policies, procedures, and configurations
Maintain policies aligned with actual practices. Keep versioned evidence of configurations, diagrams, and SOPs. Retain HIPAA documentation for six years.
- Establish monitoring, logging, and audit trails
Enable logs for access, admin actions, data exports, and failed logins across systems. Centralize logs, route to SIEM, and build alerts for anomalies.
- Prepare incident response and breach notification
Define intake, triage, and escalation paths. Conduct tabletop drills. For breaches affecting 500+ individuals, notify affected parties, HHS, and possibly the media within 60 days. For smaller breaches, report to HHS annually.
- Vendor security and change control
Vet vendors handling PHI, confirm least-privilege access, and align contracts with HIPAA obligations. Route major system/vendor changes through risk analysis.
- Train your workforce and enforce sanctions
Provide training on PHI handling, log attendance, and enforce sanctions for violations.
Phase 4: Continuity and assurance
- Test backups and recovery
Run periodic DR drills, verify backup integrity, and measure RTO/RPO performance.
- Perform periodic evaluations
Carry out technical and non-technical evaluations when your environment changes to confirm safeguards remain effective. Feed findings back into risk analysis.
- Get audit-ready
Build an evidence matrix mapping safeguards to proof (policies, screenshots, logs, BAAs, IR reports). This ensures you can answer auditor requests quickly and consistently.
Common pitfalls technical teams face
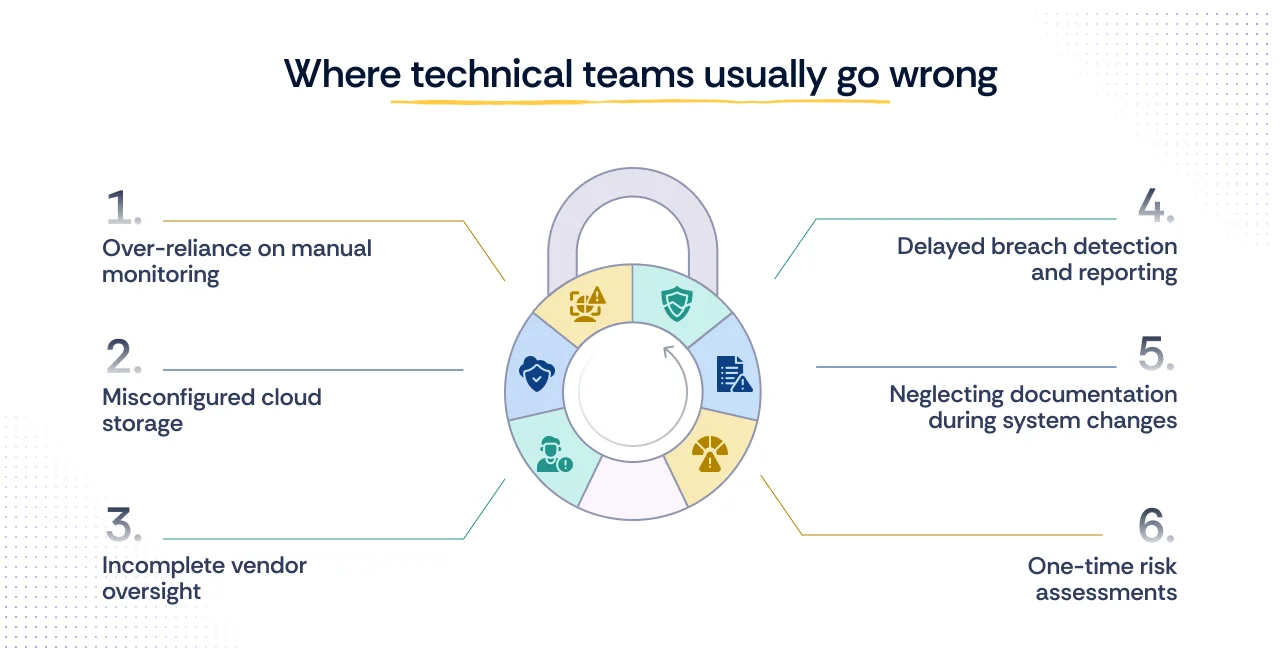
Even with a clear roadmap, technical teams often stumble on the same issues. Recognizing these pitfalls upfront can save both time and costly remediation later.
- Over-reliance on manual monitoring
Relying solely on manual log reviews or ad-hoc checks leaves too much room for human error. HIPAA expects continuous, consistent monitoring of access and activity around PHI, and manual approaches rarely scale.
- Misconfigured cloud storage
Public cloud buckets, unmanaged IAM policies, or weak encryption defaults are a frequent source of PHI exposure. Teams often assume that using a HIPAA-eligible service automatically ensures compliance, but configuration mistakes are still their responsibility.
- Incomplete vendor oversight
Business Associate Agreements (BAAs) alone don’t guarantee security. If third-party tools or SaaS providers aren’t vetted for technical safeguards (encryption, access logs, breach response), your compliance program has a blind spot.
- Delayed breach detection and reporting
Without strong audit trails and alerting, teams may fail to detect unauthorized access quickly. The Breach Notification Rule sets a hard 60-day reporting window, but investigations without proper logging can drag on, risking non-compliance.
- Neglecting documentation during system changes
It’s common to apply new configurations or roll out infrastructure changes without updating associated policies and procedures. This gap is often flagged in audits, where auditors compare system evidence against outdated documentation.
- One-time risk assessments
Treating risk analysis as a “once and done” activity instead of a recurring exercise leads to blind spots. HIPAA requires evaluations whenever environments or operations change, not just during initial compliance setup.
How Scrut helps you with HIPAA compliance
Scrut simplifies HIPAA compliance by automating evidence collection, mapping HIPAA safeguards to 1,500+ pre-built controls, and continuously monitoring your cloud and SaaS systems for misconfigurations. It also centralizes vendor risk reviews and BAAs, and keeps all audit-ready documentation organized in Trust Vault, so you’re always prepared when auditors come knocking.

FAQs
What is a HIPAA compliance checklist?
A structured list of HIPAA requirements translated into actionable steps for ensuring PHI is protected and audit-ready.
Who is this HIPAA compliance checklist for?
Healthcare providers, insurers, business associates, and vendors handling PHI, especially CISOs, CTOs, compliance, and IT security teams.
Is there a specific HIPAA compliance checklist for IT?
Yes. It focuses on technical safeguards like access controls, encryption, logging, backup and recovery, and monitoring.
How do I know my documentation is sufficient to pass the HIPAA compliance audit?
If every safeguard is backed by dated, version-controlled evidence (risk assessments, policies, training, logs, BAAs) retained for at least six years.
Who is responsible for implementing and monitoring the HIPAA regulations?
Covered entities and business associates, with day-to-day oversight by designated Privacy and Security Officers.
Why do organizations need a Privacy and Security Officer?
To provide accountability, the Privacy Officer manages PHI policies, while the Security Officer enforces safeguards for ePHI.
What are the HIPAA compliance requirements?
Compliance requires meeting the Privacy, Security, Breach Notification, Enforcement, and Omnibus Rules, covering safeguards for PHI, risk assessments, workforce training, vendor agreements, and proper breach handling.
What happens if you fail a HIPAA audit?
Failure can result in corrective action plans, ongoing monitoring by regulators, and potential financial penalties depending on the severity of non-compliance.
Does HIPAA apply outside the U.S.?
Yes, if an overseas organization handles PHI on behalf of a U.S. covered entity or business associate, it must comply with HIPAA requirements.
What are the penalties for breaching HIPAA?
HIPAA penalties follow a four-tier structure based on the level of negligence:
- Tier 1 (Unknowing): $141 – $71,162 per violation, capped at $2.1M annually
- Tier 2 (Reasonable Cause): $1,424 – $71,162 per violation, capped at $2.1M annually
- Tier 3 (Willful Neglect, corrected within 30 days): $14,232 – $71,162 per violation, capped at $2.1M annually
- Tier 4 (Willful Neglect, not corrected): $71,162 – $2.1M per violation, capped at $2.1M annually
On top of civil penalties, criminal penalties can apply for intentional violations, ranging from fines up to $250,000 and imprisonment of up to 10 years for the most serious cases.
Table of contents