The audit risk model (ARM) is a key tool in modern auditing, helping make audits more accurate and reliable. Originally used in financial statement audits, it’s now relevant for industries where regulatory compliance is critical, like healthcare, banking, and technology.
Missing controls or oversight gaps can lead to serious consequences. ARM breaks these risks into three components: inherent, control, and detection, helping audit teams see where issues are most likely and plan their work accordingly. It provides a structured way to quantify vulnerabilities and guide effective audit planning.
In this article, you’ll get a step-by-step explanation of the audit risk model formula, an overview of how its components interact, and a look at the model’s limitations. We also cover how automating some audit risk tasks can save time, reduce errors, and keep your records organized.
What is the audit risk model?
The audit risk model (ARM) is a framework auditors use to assess and manage the risks associated with an audit engagement. It starts from a simple premise: every audit carries some level of risk, and auditors must take steps to reduce it.
Audit risk specifically refers to the risk that auditors will issue an inappropriate audit opinion due to undetected material misstatements in the financial statements. This could mean concluding that financial statements are fairly presented when they actually contain significant errors or fraud, or conversely, identifying issues where none exist.
ARM breaks audit risk into three key components:
- Inherent risks.
- Control risks.
- Detection risks.
The primary purpose of ARM is to keep the overall audit risk at an acceptably low level. It helps auditors plan the nature, timing, and extent of audit procedures. For example, if inherent and control risks are high, auditors must lower detection risk by performing more detailed or extensive testing. Auditors use the audit risk model to determine the type and extent of evidence required for different risks.
Audit Risk (AR) = Inherent Risk (IR)× Control Risk (CR) × Detection Risk (DR)
Three key components of the audit risk model
1. Inherent risk
Inherent risk is the natural vulnerability of a business to errors, fraud, or non-compliance before any controls are in place. It stems from the nature of the business itself, and several factors contribute to the risk.
- Business operations: Handling sensitive customer data, managing complex financial transactions, or depending on third parties creates baseline exposure just from operating in the industry.
Consider companies that handle health or financial records. They face a constant risk of data breaches or misuse.
- Human error: This accounts for 95% of all data breaches, making it a significant inherent risk factor across all organizations.
- External factors: Regulatory changes and policy shifts introduce additional layers of risk that are beyond a company's direct control.
For example, the recent U.S. tariff announcements could affect costs, shift demand for goods and services, and alter competitiveness, showing how external factors contribute to inherent risk.
In short, inherent risk is the baseline risk every organization faces just by operating in its industry. Understanding inherent risk is critical. It sets the foundation for audit planning and highlights where controls need to be strongest.
2. Control risk
Control risk arises when your internal controls fail to detect or prevent material misstatements in financial statements. This occurs due to several key factors:
- Poor design: Controls that aren't designed well from the start.
- Implementation failures: Controls that aren't implemented properly.
- Operational breakdowns: Controls that break down during day-to-day operations.
For example, if your company follows GDPR, you may have a policy to delete user data after a request or once it’s no longer needed. Without automated monitoring, data could remain in your system, creating a compliance violation.
Regulators hold you accountable not just for having policies, but for ensuring your controls actually work. Even a control failure can make you liable.
Managing control risk is a continuous effort. By monitoring and improving your controls regularly, you can catch gaps early, reduce operational and compliance risks, and avoid fines or reputational damage.
3. Detection risk
Detection risk occurs when you or your compliance team fail to spot instances of non-compliance during monitoring activities.
Even with controls and audits in place, material issues can go unnoticed, giving the false impression that everything is in order. It highlights the limits of audits, monitoring tools, and testing procedures.
Audit risk model diagram
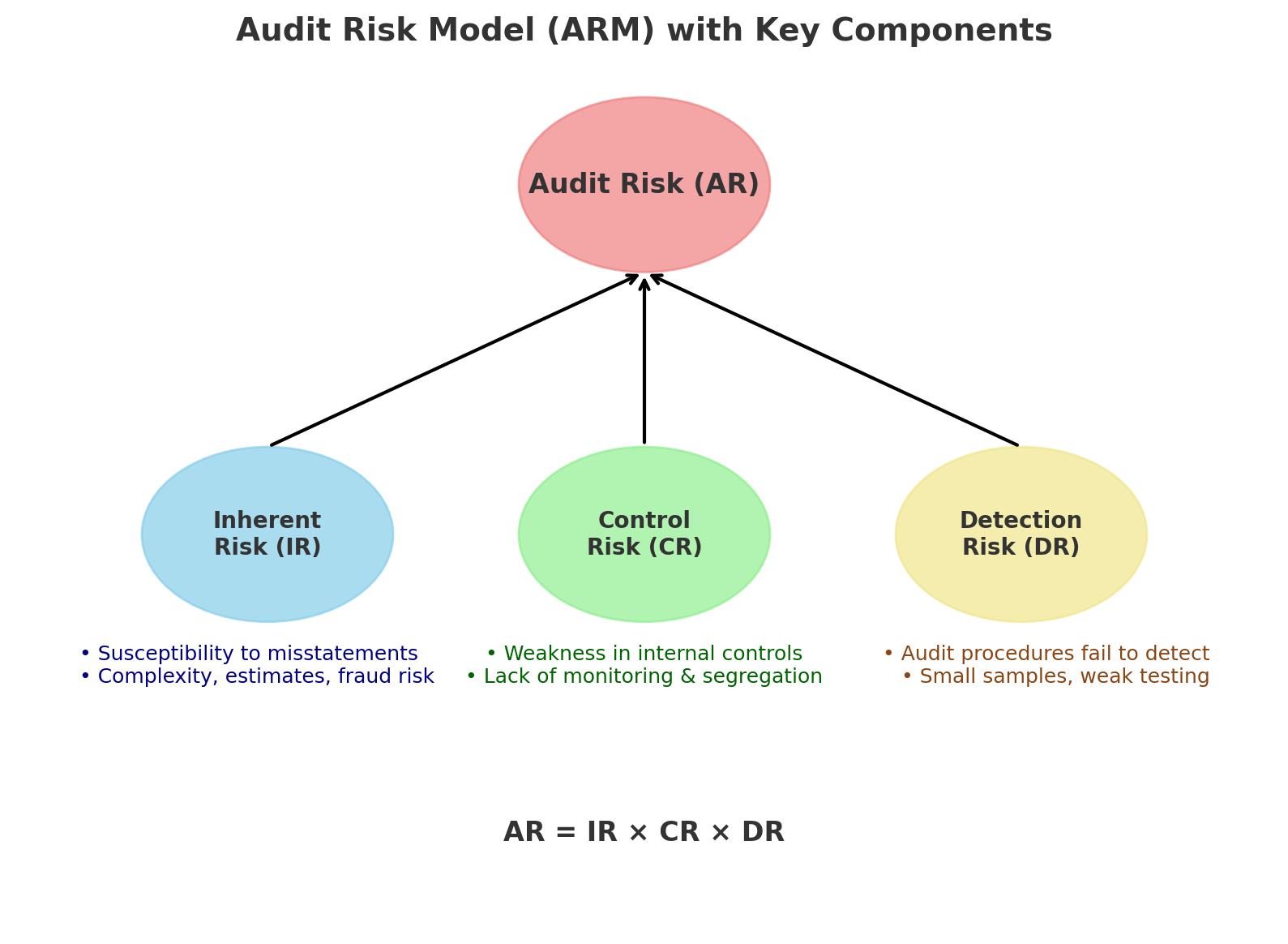
- Inherent risk (IR): Susceptibility to misstatements, complexity, and fraud risk before considering internal controls.
- Control risk (CR): Weak controls, poor monitoring, and a lack of segregation leading to failure to detect material misstatements.
- Detection risk (DR): Audit procedures failure, small samples, or weak testing resulting in material misstatements passing through scrutiny without detection.
Limitations of the traditional audit risk model
Relying on the traditional audit risk model comes with several challenges. Its dependence on periodic assessments, static assumptions, and manual processes makes it less effective in a business environment, where regulations change frequently and threats constantly evolve.
1. Static assessments lead to compliance gaps
Traditional audits evaluate compliance at predetermined intervals, checking a sample of records or configurations at a single point in time. This leaves gaps between audits, during which issues can go unnoticed.
2. Lack of real-time updates
Traditional audits evaluate risks at fixed intervals, not continuously. Without continuous monitoring, your organization becomes more vulnerable to sudden threats like cyber intrusions or rapidly evolving money laundering schemes.
Auditors relying on a traditional audit risk model may underestimate these risks, leaving you exposed to emerging issues.
3. Manual processes increase human error
Manual audits rely heavily on auditor judgment. This can produce inconsistent or unreliable assessments, especially if auditors aren’t familiar with your business or internal controls.
4. Oversimplification of audit risk
The traditional model oversimplifies complex compliance environments by reducing risk into three fixed components: inherent, control, and detection risk.
This linear quantitative equation cannot fails to capture qualitative factors such as organizational complexity and corporate culture, even as they significantly influence risk.
5. Resource and time constraints
Implementation of the traditional audit risk model is resource-intensive and time-consuming. Additionally, the model restricts audit coverage, increasing the likelihood of overlooked compliance gaps and leaving your organization vulnerable to threats.
Automating audit risk management
Traditional audit risk model processes are often effort-intensive, time-consuming, and error-prone. Automating these audit risk management processes helps you streamline workflows, reduce compliance monitoring risks and respond faster to emerging regulatory threats.
1. Continuously monitor risk components
Continuous compliance streamlines audits by maintaining near real-time records, automating tracking, and ensuring ongoing policy enforcement. With near real-time monitoring and reporting, you can track risk across your infrastructure, applications, and frameworks. Constant oversight ensures you’re always audit-ready.
2. Automated control testing
Automated testing of cloud and application systems validates security, access controls, and configuration settings required by regulations like the Health Insurance Portability and Accountability Act (HIPAA).
These automated tests enable you to instantly detect deviations, misconfigurations, unauthorized access, and vulnerabilities in real time.
By providing the latest audit-ready data, automation eliminates last-minute data collection and reduces human error.
3. Automated evidence collection reduces detection risks
Automated evidence collection pulls data from your connected applications, leading to a reduction of audit preparation efforts and compliance monitoring gaps since violations or anomalies are unlikely to go unnoticed during audits.
Automation tools gather audit evidence like system logs, transaction histories, and access records continuously and accurately. You can set custom intervals for collecting data, minimizing sampling errors and oversight, giving auditors complete, reliable datasets.
4. Real-time dashboards and alerts
Automation platforms present compliance risks visually through dashboards and trigger alerts when thresholds are breached. For example, unusual login patterns or unapproved data transfers prompt instant notifications.
Real-time dashboards visualize compliance status and provide a consolidated view of overall progress, risks, vendors, audits, and frameworks.
4 practical steps to implement the audit risk model with automation
Automating audit risk processes like evidence collection, risk assessment, and data analysis helps you work faster, reduce errors, and gain clearer insights into potential risks. While automation cannot eliminate detection risk, it can provide more comprehensive and reliable data for auditors to examine. It lets you focus on high-value tasks, shifting from reactive checks to proactive, predictive risk management.
Step 1: Identify key risks
Identify high-risk areas such as data privacy, access controls, or financial transactions with significant amounts of inherent and control risks. Review compliance processes and controls to uncover hidden risks and ensure the effectiveness of existing controls. Track changes in relevant laws and regulations and update the compliance framework, which will help you proactively identify new risks.
Step 2: Map controls
Link potential threats to the internal safeguards (controls) and mitigation strategies designed to address them. This mapping enables clear accountability, streamlines reporting, and highlights compliance gaps quickly, reducing the chance that ineffective safeguards remain unnoticed during audits. The goal isn’t to cover everything; it is to cover what matters most. This means ensuring that every key risk is tied to the appropriate controls and response plans.
Step 3: Configure monitoring
It involves establishing a system that continuously and automatically observes key risk indicators (KRIs) and operational processes. Use automation tools to monitor systems, transactions, and user behavior constantly.
With automation, audit moves from a snapshot-in-time review to a continuous assessment of the risk landscape. Though external audits are periodic, automation enhances internal monitoring, improving organizational audit readiness and the quality of data when auditors conduct their scheduled reviews.
Step 4: Set alerts and review cycles
Set automated alerts to notify compliance teams when thresholds or risk indicators are breached. Pair these with structured review cycles to reassess risks and controls periodically.
The combination of automated alerts and reviews provides both real-time responsiveness and ongoing evaluation. It ensures audit risk management stays current and aligned with regulatory expectations.
How Scrut enhances the audit risk model
While ARM remains essential for financial statements audit organizations also need robust compliance and risk management capabilities. Scrut’s help you create audits projects based on frameworks or specific controls to match your broader compliance and audit needs. It allows you to manage internal and external audits from a single platform.
Here’s how Scrut enhances the audit risk model:.
1. Catalog inherent, control, and detection risks
An improper risk assessment is often the primary reason for audit delays. Scrut offers a prebuilt library of risks that guides organizations in identifying relevant risk areas and uncovering often-overlooked risks. A risk register provides a comprehensive view of all organizational risks, the strategies and actions adopted to manage them, and the residual risks.
With platform cataloging all risks, there is a minimal chance of the auditor not detecting a material misstatement.
2. Integrates with existing compliance frameworks
The pre-built policy library contains policies mapped to popular industry frameworks like SOC 2, ISO 27001, and more. You can customize these policies using built-in inline editors to meet your unique business needs. It enables you to initiate your infosec programs promptly and utilize policies for effective audit management.
3. Flags anomalies automatically
Scrut continuously monitors your cloud infrastructure, automatically detecting cloud misconfigurations and reducing the risk of security breaches. Real-time monitoring keeps your security posture visible, The near real-time monitoring of your organization security posture enables you to quickly identify deviations and address them.
It prevents risks from persisting in the system, avoiding collateral damage and enabling your organizations to comply with security policies and standards.
4. Improve audit-readiness
The platform offers tracking of audit progress, evidence collection, and control compliance, helping you stay organized and audit-ready. You can easily manage project scope and pull auditor-friendly evidence automatically from the platform in a few clicks.
Scrut includes trackers to manage corrective actions, findings, and requests, simplifying the process of rectifying audit deficiencies.
The dashboard helps you to keep track of the timelines of upcoming audits for corresponding frameworks, assisting in audit readiness beforehand.
5. Generates audit-ready reports
Scrut generates automated risk assessment reports that you can readily share with compliance auditors for SOC 2, ISO 27001, PCI DSS, GDPR, and other infosec frameworks.
Additionally, the platform captures all changes and actions in detailed logs to get complete visibility and accountability into compliance tasks. The role-based access for auditors enables them to access relevant projects securely, ensuring data protection and transparency.
6. Collaborative workflow improves audit efficiency
The collaborative workflow enhances teamwork among internal and external stakeholders, improving efficiency. The platform simplifies audits by allowing you to invite security and compliance auditors to the platforms, share artifacts, and monitor status in real-time for seamless and efficient audits.
Schedule a demo today to see how Scrut can help you automate audit risk management and gain complete visibility across the entire audit cycle.
FAQs
What is the audit risk model?
The audit risk model is a framework that auditors use to understand and manage the risk of giving an incorrect audit opinion. It breaks down audit risk into three components, inherent risk, control risk, and detection risk, which together help auditors determine how much evidence they need and how to plan their audit procedures.
What is the formula for the audit risk model?
Audit Risk (AR)=Inherent Risk (IR)×Control Risk (CR)×Detection Risk (DR)
The formula helps auditors quantify the overall risks of issuing an inappropriate audit opinion. The formula helps auditors assess the levels of inherent and control risk to determine the necessary testing (which controls detection risk) to achieve the desired low level of audit risk.
What are the three components of the audit risk model?
The three components of the audit risk model are inherent risk, control risk, and detection risk. Inherent risk exists due to the nature or complexity of the business, while control risk indicates the possibility that a company's controls may fail to prevent or detect errors. Detection risk refers to the possibility of an organization failing to identify instances of non-compliance through its monitoring activities.
What is an example of an audit risk model in internal auditing?
Example: audit risk model in external auditing
Consider a healthcare company handling sensitive patient data in a complex, cloud-based environment. Here’s how the audit risk model applies:
- Inherent risk (IR): Assessed as High, due to the sensitive nature of patient data with personally identifiable information (PHI) such as names, addresses, social security numbers, and more.
- Control risk (CR): Medium to High. Weak data encryption or inadequate access controls may allow unauthorized users to view or alter records. The firm has implemented multi-factor authentication (MFI); however, role-based access control is missing.
- Detection risk (DR): If monitoring tools or audits rely only on periodic reviews, breaches or unauthorized access attempts might remain undetected for months. The DR is set at 25%.
Audit risk = 0.7 * 0.5 * 0.25 = 0.0875 (8.75%)
This shows how quantifying each component helps you focus on the areas that matter most, prioritize controls, and reduce overall audit risk.





































