Choose risk-first compliance that’s always on, built for you.
Go back to blogs
ISO 27001 vs ISO 27002: Key Differences Explained
Last updated on
August 13, 2025
min. read

If you’ve been looking into information security standards, you’ve likely encountered both ISO 27001 and ISO 27002 along the way. These two standards are often mentioned together, and while they’re closely related, they serve very different functions within a cybersecurity program.
At first glance, they might seem interchangeable. But treating them as such can lead to confusion during implementation, internal audits, or certification efforts. One is about establishing the foundation of your information security program; the other is about bringing that foundation to life through practical controls.
Here’s the simplest way to understand the difference:
- ISO 27001 defines the requirements for building and maintaining anInformation Security Management System (ISMS).
- ISO 27002 offers in-depth guidance on putting the security controls from ISO 27001 into practical action.
In other words, ISO 27001 tells you what must be done to manage risk and secure information. ISO 27002 tells you how to do it.
Understanding this distinction is critical, especially for teams juggling certification readiness, stakeholder expectations, and the reality of daily security operations. Without ISO 27001, you lack a structured governance framework. Without ISO 27002, implementation can feel vague and inconsistent. Used together, they help you align strategy with execution, from boardroom policy to technical control.
Let’s dive deeper into how each standard works, where they differ, and how to use them effectively in tandem.
ISO 27001 vs ISO 27002: key differences
When to use ISO 27001 vs ISO 27002
ISO 27001 and ISO 27002 aren’t alternatives, they’re built to complement one another. While ISO 27001 lays down the governance framework for managing information security, ISO 27002 helps bring that framework to life. ISO 27002 provides the implementation guidance that helps bring that framework to life.
That said, depending on your role, priorities, or stage in the compliance journey, you may find yourself relying more heavily on one over the other.
Here’s how to think about it:
Use ISO 27001 when:
- You’re building a formal security program from the ground up
You need to define a structured, organization-wide ISMS that aligns with business risks and stakeholder expectations. - You’re aiming for ISO 27001 certification
Your customers, partners, or regulators require third-party assurance, and you need to demonstrate that your security posture meets international standards. - You’re defining top-level policies, responsibilities, and governance structures
You're in charge of setting the tone at the top establishing accountability, defining roles, and building the risk governance model that underpins your security program. - You want to centralize and formalize security decision-making
Rather than siloed, ad-hoc efforts, you need a consistent and repeatable process for managing security risks across the organization.
Use ISO 27002 when:
- You need practical, control-level guidance for implementation. You’re looking to understand what each ISO 27001 Annex A control really means, and how to operationalize it in your specific business and technical environment.
- You’re designing or optimizing specific technical controls
Whether it's access management, network security, or monitoring, ISO 27002 helps you apply controls in a way that’s relevant to your tools, cloud stack, and maturity level. - You’re conducting internal audits, control testing, or training
ISO 27002 can act as a checklist, playbook, or onboarding guide helping internal teams align on how controls should look and function. - You want to tailor implementation across teams or geographies
The guidance helps ensure consistency while allowing room for variation based on regional risks, business functions, or team responsibilities.
What is ISO 27001?
ISO/IEC 27001 is the internationally recognized standard for establishing, implementing, maintaining, and continuously improving an ISMS. Developed jointly by the International Organization for Standardization (ISO) and the International Electrotechnical Commission (IEC), ISO 27001 lays out a structured, risk-driven approach to managing information security across an organization.
At its foundation, ISO 27001 enables organizations to assess and address risks that could impact the confidentiality, integrity, or availability of their information assets. Whether it’s customer data, internal IP, or operational systems, ISO 27001 ensures that these assets are protected through a unified, risk-based approach. It brings together people, processes, and technology to create a centralized security program that is auditable and certifiable.
Unlike ad-hoc or reactive security approaches, ISO 27001 takes a proactive, responsive, and adaptive governance-first model. It guides organizations to:
- Understand the internal and external context of their business
- Identify relevant stakeholders and regulatory requirements
- Conduct risk assessments to identify threats and vulnerabilities
- Select appropriate controls to mitigate identified risks
- Define clear security policies, roles, and responsibilities
- Monitor, audit, and improve the system on an ongoing basis
The goal isn’t to prescribe specific tools or technologies. Instead, ISO 27001 helps organizations design a flexible, risk-aligned program that fits their business size, industry, and risk appetite.
One of the defining features of ISO 27001 is that it is certifiable. Organizations can undergo an independent audit by an accredited certification body to demonstrate their compliance. For many, this certification is not just a badge of credibility. It’s a business enabler that helps win customer trust, unlock enterprise deals, and meet regulatory or vendor security requirements.
Why organizations choose ISO 27001
Organizations opt for ISO 27001 for a variety of strategic reasons. Here are the most common drivers behind its adoption:
- To establish a structured and certifiable security program
- To gain a competitive edge through third-party audits and certification
- To meet contractual or vendor compliance obligations
- To enhance stakeholder trust through transparent governance
- To formalize risk-based decision-making across the business
What is ISO 27002?
While ISO 27001 defines the requirements for building an ISMS, ISO/IEC 27002 serves as its companion guide, offering detailed, real-world guidance on how to implement the security controls referenced in Annex A of ISO 27001.
ISO 27002 is not a certifiable standard. You cannot be audited or certified against it. Instead, it functions as a reference library of security controls, explaining the intent behind each control, how it can be implemented in practice, and what factors to consider based on your organization’s context.
Each control in ISO 27002 is broken down into:

- A control objective
- A description of the control
- Practical implementation guidance
- Explanatory notes for clarity
- In the 2022 version, even attributes like control type (preventive, detective, corrective), security property (confidentiality, integrity, availability), and applicable use cases
This makes ISO 27002 especially valuable for technical and operational teams, from IT and DevOps to GRC specialists, who need to translate high-level security policies into specific, repeatable, and auditable actions.
But it’s important to understand:While ISO 27002 is not a certifiable framework and was designed to support ISO 27001, some organizations do use it as a standalone reference for implementing security best practices. Its value only becomes clear when used in conjunction with ISO 27001, where it provides the “how” to ISO 27001’s “what.”
If ISO 27001 says, “You must implement access controls,” ISO 27002 says, “Here’s what effective access control looks like, and how to implement it across your infrastructure.”
Why ISO 27002 matters
- Offers detailed, real-world guidance to interpret ISO 27001 controls
- Promotes consistency across teams, regions, and business units
- Helps tailor implementation to your organization’s unique risks
- Acts as a training and onboarding reference for technical teams
What changed in the 2022 updates?
The 2022 revisions of ISO 27001 and ISO 27002 were some of the most significant updates to the standards in over a decade. They were designed to make both standards more relevant to today’s dynamic threat landscape, including the rise of cloud-native environments, remote workforces, automation, and increasingly sophisticated cyber threats.
These revisions didn’t just refresh the content; they aligned the two standards more tightly, simplified the structure, and added important new guidance to help teams operationalize controls more effectively.
ISO 27001:2022 — what’s new?
- Annex A alignment with ISO 27002:
The updated Annex A now mirrors the structure and thematic grouping used in ISO 27002. This makes it much easier to cross-reference controls and implement them consistently across both standards. - Simplified, clearer language:
The language across the 10 clauses and Annex A has been cleaned up to reduce ambiguity and improve interpretability, especially for non-native English readers and global teams. - Stronger emphasis on risk-based implementation:
ISO 27001:2022 reinforces the importance of aligning controls to the organization's risk context and business objectives. It encourages more tailored, flexible control selection based on specific threats and risk appetite.
ISO 27002:2022 — what’s new?
The 2022 revision of ISO 27002 brought one of the most significant updates since its 2013 version with clearer structure, modernized controls, and better alignment to today's cloud-native environments. If you're still aligned with the 2013 edition, remember that the transition deadline is 31 October 2025.
1. Control count reduced from 114 to 93
Many overlapping or redundant controls were merged or removed to reduce confusion and streamline implementation.
2. Introduction of four thematic control categories
Controls are now grouped under clearer themes, replacing the older 14-domain model:
- Organizational controls
- People controls
- Physical controls
- Technological controls
3. 11 new controls introduced, including modern security priorities such as:
- Threat intelligence
- Data masking
- Cloud service governance
- Monitoring activities
- Information deletion
- Web filtering
- Secure coding
4. Control attributes added for better filtering and reporting:
Each control now includes metadata to support automation and governance:
- Control type: Preventive, detective, or corrective
- Information security properties: Confidentiality, integrity, availability (CIA triad)
- Cybersecurity concepts: Based on NIST concepts like identification, protection, and detection
- Implementation guidance and purpose: Practical advice for tailoring each control
These changes make ISO 27002 far more usable for operational teams, especially in regulated industries, fast-moving cloud environments, and modern DevSecOps pipelines.
Why these changes matter
For teams managing ISO compliance, these updates make the standards:
- Easier to understand and communicate across departments
- More adaptable to risk-based security programs
- Better suited for automation, filtering, and control mapping
- More aligned with real-world threats and cloud-native infrastructure
Combined, the 2022 updates enable organizations to shift from checkbox compliance to a more practical, measurable, and security-driven approach, making ISO 27001 and ISO 27002 better aligned with today’s cybersecurity demands.
How ISO 27001 and ISO 27002 work together
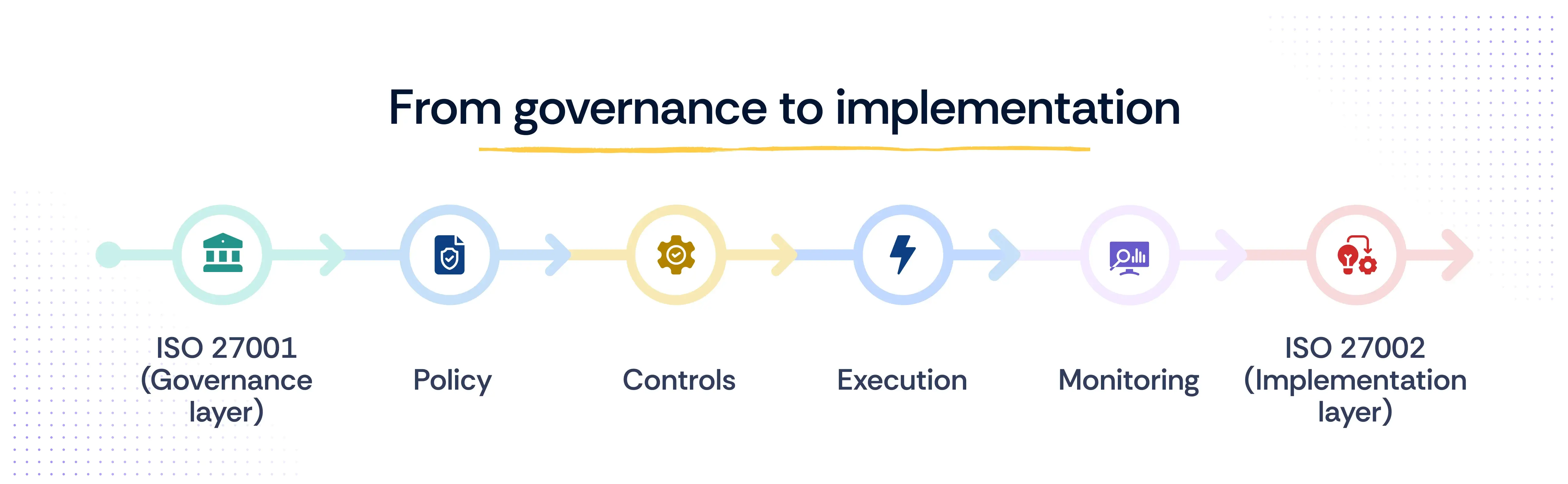
ISO 27001 and ISO 27002 are not separate or competing standards, they’re designed to complement each other. Think of them as a blueprint and a builder’s guide. One lays out the structure, while the other provides the step-by-step instructions to bring it to life.
Here’s how they work together:
- ISO 27001 says: “You need to identify risks and implement appropriate controls to manage them within a formal security management system.”
- ISO 27002 says: “Here’s what those controls look like in practice, and how to implement them effectively in your environment.”
ISO 27001 provides the management framework by defining the objectives, structure, roles, and risk governance, while ISO 27002 offers the implementation playbook that translates high-level intent into specific, operational action.
For example:
- ISO 27001 might require that access to information is controlled based on business need.
- ISO 27002 will then explain how to enforce this, suggesting user access provisioning, least privilege, multi-factor authentication, logging, and periodic access reviews.
It’s important to understand that ISO 27002 is not meant to stand alone. It was never designed to be implemented independently, and it is not certifiable. Its purpose is to support ISO 27001 by providing practical guidance for teams responsible for deploying and maintaining controls.
Together, they ensure full alignment between governance and execution, helping organizations:
- Build a security strategy that aligns with both your operational goals and regulatory requirements
- Implement it effectively across people, processes, and technology
- Monitor, audit, and improve security posture with measurable outcomes
In essence, ISO 27001 sets the direction. ISO 27002 provides the map to get there.
Other ISO standards to keep in mind
Once your ISO 27001 foundation is established, you might realize that your security and compliance needs go beyond just managing information security risks. Depending on your industry, regulatory environment, and data sensitivity, there are several other ISO standards that can extend and enrich your ISMS.
Here are some of the most relevant add-ons to consider:
1. ISO 27005 — Risk assessment for ISO 27001
ISO 27005 complements ISO 27001 by providing a structured methodology for conducting information security risk assessments. While ISO 27001 mandates a risk-based approach, ISO 27005 shows you how to do it — from identifying and analyzing risks to evaluating and treating them. Use it to build a repeatable, defensible risk assessment process and strengthen your risk register.
2. ISO 27701 — Privacy extension to ISO 27001
ISO 27701 extends ISO 27001 to include privacy controls, turning your ISMS into a Privacy Information Management System (PIMS). It helps manage personally identifiable information (PII) in compliance with laws like GDPR, CCPA, and India’s DPDP. Use it when handling personal data and aligning privacy with your broader security program.
3. ISO 27017 — Cloud security guidance for ISO 27001
ISO 27017 builds on ISO 27001 by offering specific guidance for cloud environments. It addresses shared responsibility models and control implementation across SaaS, PaaS, and IaaS setups — both from a customer and provider perspective. Use it when your infrastructure is cloud-based and you need clearer direction on securing cloud services.
4. ISO 27018 — Public cloud privacy controls for ISO 27001
ISO 27018 focuses on protecting PII in public cloud settings. It complements ISO 27001 and ISO 27701 by providing a code of practice for cloud service providers processing personal data on behalf of customers. Use it if you store or process customer data in public cloud environments and need to demonstrate privacy safeguards.
How do these standards fit into your compliance roadmap?
Each of these standards is designed to enhance ISO 27001, not replace it. ISO 27001 is your foundation — these are modular extensions that help you tailor your ISMS to your cloud setup, risk maturity, or regulatory requirements. Scrut helps you map, implement, and automate these extensions as part of a unified GRC strategy — no duplication, no audit fatigue.
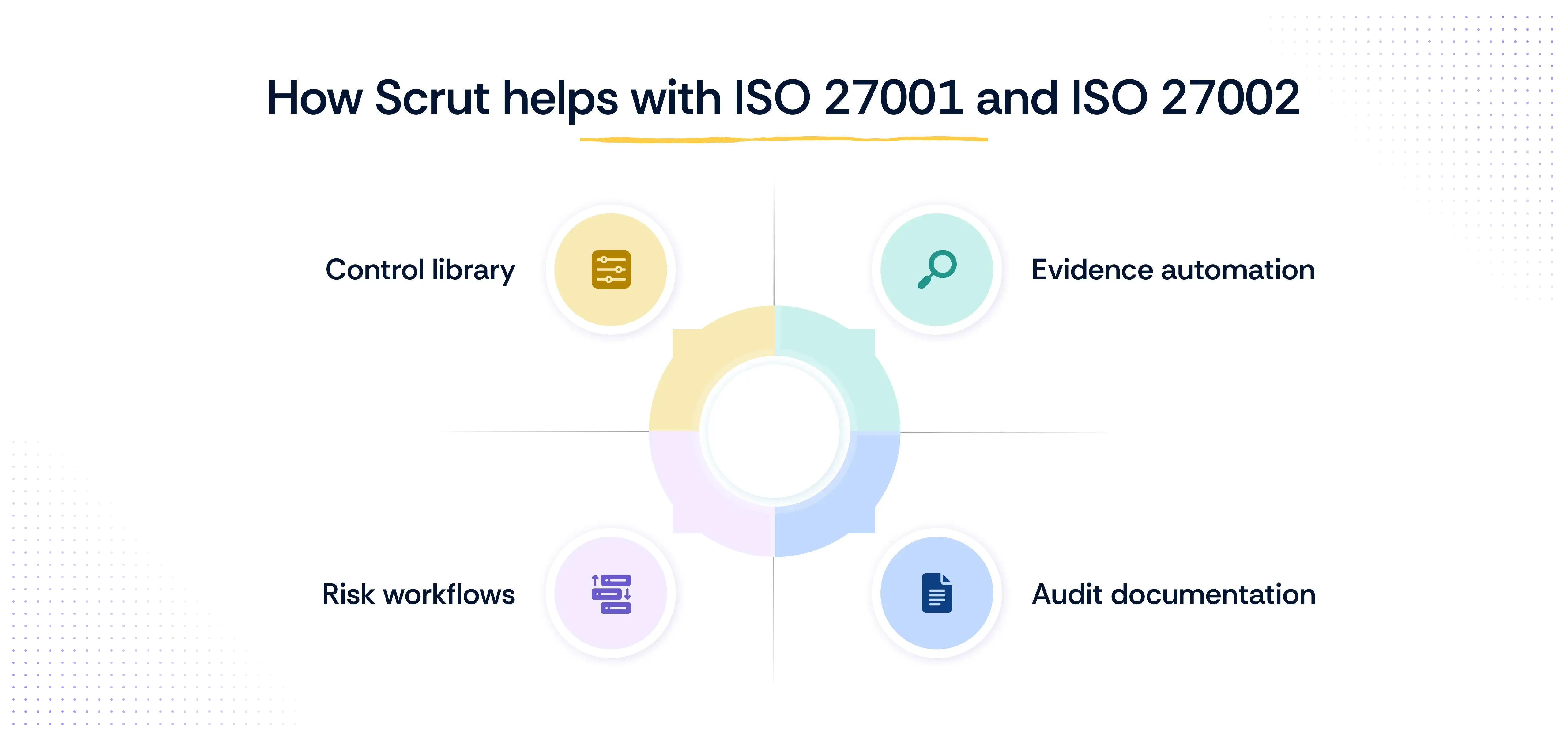
How Scrut helps with ISO 27001 and ISO 27002
Implementing ISO 27001 and ISO 27002 can be complex, especially if you’re juggling spreadsheets, scattered evidence, manual audits, and multiple stakeholders. That’s where Scrut comes in.
Scrut simplifies and accelerates every step of your ISO compliance journey, from control design to real-time monitoring, so your team can focus on security outcomes, not administrative overhead.
Whether you’re starting from scratch or scaling an existing program, Scrut gives you the tools to confidently operationalize ISO requirements across your organization.
Here's how:
- Pre-mapped control libraries aligned with ISO 27001 and ISO 27002
Start with a library of mapped controls based on the latest 2022 updates, including Annex A and ISO 27002 guidance, so you don’t have to build your ISMS from the ground up. - Automated evidence collection from your SaaS and cloud stack
Connect to AWS, GCP, Okta, Jira, and more to automatically collect logs, configurations, and reports that prove control effectiveness, without chasing screenshots or manual exports. - Real-time control monitoring via customizable dashboards
Get a live view of your compliance posture with dashboards tailored to ISO standards. Detect drift, assign remediation, and keep stakeholders informed, all in one place. - Built-in risk assessment and gap analysis workflows
Conduct ISO-aligned risk assessments directly within the platform. Identify gaps in control coverage, tailor mitigation plans, and align with ISO 27005 or business-specific risks.
Scrut acts as your end-to-end ISO compliance hub, helping CISOs, GRC leads, and technical teams stay aligned, from high-level governance to control-level execution.

FAQs
What’s the main difference between ISO 27001 and ISO 27002?
ISO 27001 defines the formal requirements for building and maintaining an ISMS, including policies, processes, roles, and risk treatment plans.
ISO 27002 offers practical control-level guidance for applying the controls outlined in Annex A of ISO 27001. In simple terms, ISO 27001 defines what needs to be done, while ISO 27002 explains how to actually do it.
Do I need both standards?
Yes. Most organizations use both together.
- ISO 27001 lays down the overarching governance structure for information security and is the standard against which organizations can achieve formal certification.
- ISO 27002 supports implementation by offering detailed best practices and examples to operationalize controls.
You won’t be certified against ISO 27002, but you’ll almost certainly reference it when preparing for ISO 27001 audits.
Is ISO 27002 required for ISO 27001 certification?
Technically, no. ISO 27001 certification only requires you to implement and justify the controls in Annex A, not necessarily to follow ISO 27002.
However, ISO 27002 is the de facto reference guide for those controls. Most auditors and implementation teams rely on it to ensure consistent, complete, and effective control execution.
Is ISO 27001 legally required?
In many regions, ISO 27001 isn’t legally required but is often adopted voluntarily to meet industry expectations or customer demands. But it is frequently required by:
- Enterprise customers as part of vendor onboarding
- Regulated industries (finance, healthcare, SaaS) to demonstrate due diligence
- Procurement teams to assess supplier risk
Even without a legal mandate, ISO 27001 often becomes a commercial necessity to win deals or access sensitive data.
Can ISO 27002 be used alone?
No. ISO 27002 is a supporting standard, not a standalone framework. It is designed to complement ISO 27001, and cannot be implemented or certified independently.
If you're applying ISO 27002 controls without the structure of ISO 27001, you're missing the governance layer that gives those controls strategic direction and auditability.
That said, many organizations informally use ISO 27002 as a best-practice reference, especially when they’re not pursuing ISO 27001 certification but still want a comprehensive control library to strengthen their security posture.
Table of contents