Choose risk-first compliance that’s always on, built for you.
Go back to blogs
How to define your SOC 2 audit scope: Key steps and challenges
Last updated on
September 7, 2025
min. read
.webp)
Before a SOC 2 audit even begins, the toughest part is often deciding the boundaries. Too broad, and you spend time and money auditing systems no one cares about. Too narrow, and customers may question the credibility of your report.
The real challenge is knowing what’s worth including and what’s not. This blog walks through how the SOC 2 audit scope works, who sets it, and how to think about what should be in scope for your audit.
What is the SOC 2 scope?
The SOC 2 scope defines which systems, services, and Trust Services Criteria (security, availability, processing integrity, confidentiality, and privacy) are included in the audit. The scope is set by the organization’s management, since they decide which areas are most relevant for customers and the business.
Why is scope important for SOC 2 reports?
The scope is the starting point for SOC 2 audit preparation because it sets the boundaries of what the auditor will evaluate. It determines which systems, services, and types of reports are included in testing, which directly shapes the usefulness of the report for customers and other stakeholders.
A well-defined scope avoids the trap of over-scoping, where audits become unnecessarily complex and expensive, and under-scoping, where important risks are left unaddressed. Getting scope right also ensures that the report strikes the right balance between being comprehensive and being focused.
In addition, a well-defined scope drives audit efficiency, reduces delays, and helps the final report demonstrate to its readers, such as customers, partners, and vendors, that your controls are aligned with business commitments. Clear scope can also be included in vendor SLAs, reinforcing trust and accountability.
What is covered in the SOC 2 scope?
While the Trust Services Criteria are central and mandatory for SOC 2, the scope goes beyond them, defining the full boundaries of your organization’s environment to show how services are actually delivered. The main items that fall into scope include:
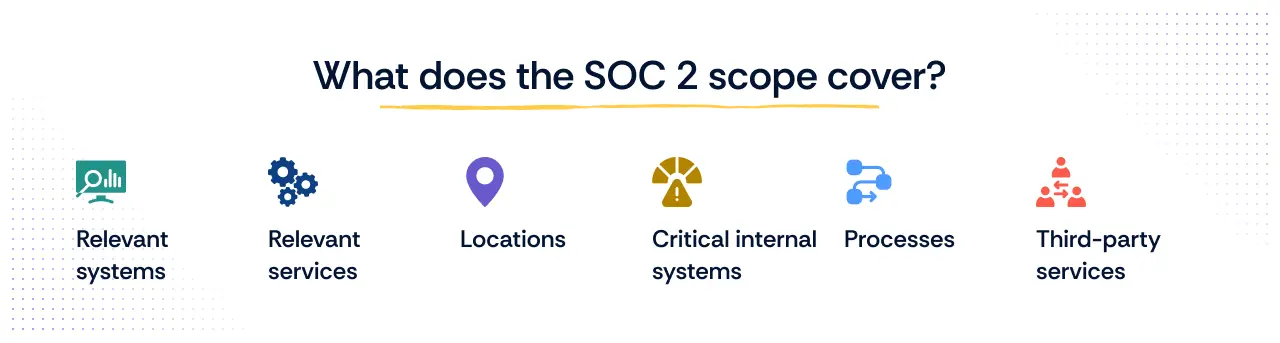
- Relevant systems: The technology components that process or store customer data, such as databases, applications, or cloud platforms.
- Relevant services: The offerings provided to customers that rely on these systems, such as a SaaS application or managed service.
- Locations: Physical sites where systems and data are hosted, including offices, data centers, or cloud regions.
- Processes: The business and operational workflows that support secure and reliable service delivery, such as access control or incident response.
- Critical internal systems: Internal tools that are essential for maintaining security and compliance, like identity management or monitoring systems.
- Third-party services/Subservice organizations: Vendors or partners that play a role in delivering your service, such as hosting providers, payment processors, or managed security partners.
How to create your SOC 2 audit scope
Creating a SOC 2 scope is about being intentional. The goal is to capture the systems, services, and criteria that really matter without turning the audit into an endless exercise. A step-by-step approach makes it easier to get the scope right and ensure the final report is both credible and efficient.
Step 1: Map your services and supporting systems
Start by identifying the services your customers rely on, the systems that deliver them, and the people and processes that support those services. This could include your SaaS product, databases, APIs, internal teams, workflows, and the infrastructure that runs behind the scenes. Anything that stores, processes, or transmits customer data should be considered for inclusion.
Step 2: Choose the Trust Services Criteria that apply
Security is always required, but availability, processing integrity, confidentiality, and privacy are optional. Pick the criteria that align with your customer contracts, industry expectations, or the type of data you handle. For example, if you handle sensitive customer data, confidentiality is often essential. Once you identify the relevant criteria, all the controls related to those criteria should be tested. For more on how scope differs between report types, see our guide on SOC 2 Type 1 vs SOC 2 Type 2.
Step 3: Include locations and third-party vendors
The scope should cover where your services live, whether that is an office, data center, or cloud environment. It also needs to account for third-party providers or subservice organizations that play a role in delivering your service, such as hosting platforms or managed security vendors.
Step 4: Define the audit period
A Type I report looks at controls at a single point in time, while a Type II report tests controls over a period of months. Being clear about the time frame helps the report meet stakeholder expectations.
Step 5: Align with customer and vendor expectations
Before finalizing your SOC 2 scope, review it against any relevant customer or vendor expectations, including contractual obligations or SLAs. This ensures the audit covers what stakeholders consider important and reinforces trust in the report.
Step 6: Validate with your auditor
Before finalizing, review your proposed scope with the CPA firm conducting the audit. They can confirm whether it is reasonable, highlight any gaps, and ensure the scope will result in a report that holds value for your customers and partners.
Which time frame is used for the SOC 2 scope?
For defining your SOC 2 scope, the audit period depends on the report type:
- A Type I report captures controls at a specific point in time. For example, “as of September 30, 2025.” It provides a snapshot of whether the system’s controls are properly designed.
- A Type II report evaluates how controls operate over a span of time, typically between 3 to 12 months.
What are some common challenges in defining the scope for SOC 2 audits?
Defining the SOC 2 scope sounds simple, but many teams run into these roadblocks:
- Over-scoping – Including too many systems or services, which drives up time, cost, and effort.
- Under-scoping – Leaving out critical processes or third parties.
- Third-party dependencies – Deciding how to handle subservice organizations and vendors that impact your controls.
- Changing environment – Adapting scope as your business scales, adds new products, or enters new markets.
- Misalignment with stakeholders – When leadership, IT, and compliance teams don’t agree on what’s “in scope,” it leads to confusion and rework.
- Report usefulness – A poorly defined scope can make your final SOC 2 report less credible or valuable to customers and partners.
How to automate the SOC 2 audit process
Manual SOC 2 prep can drain time and resources, from collecting evidence to tracking controls. Automation makes the process faster, more accurate, and audit-ready at any point. Key areas where automation helps include:
- Continuous monitoring of controls instead of periodic checks
- Automated evidence collection from your existing tools
- Centralized dashboards to track progress in real time
- Pre-mapped controls to simplify auditor reviews
With Scrut, you can automate evidence collection across your tech stack, continuously monitor controls, manage risks in real time, and collaborate with auditors through a single dashboard. Instead of chasing documents, you stay audit-ready every day.

FAQs
What happens if you don’t include the relevant items in the SOC 2 scope?
If key systems, controls, processes, or third parties (subservice organizations) are omitted from the scope, it can lead to an incomplete audit. This may result in a qualified opinion or a disclaimer of opinion and ultimately increases your organization’s risk exposure.
How long is a SOC 2 scope considered valid?
A SOC 2 report doesn’t formally expire, but it is generally accepted as valid for 12 months from the report’s issue date. After this, clients may consider it outdated and seek a more recent audit.
Do you need to change the SOC 2 scope with every audit?
Not necessarily, but you will need to revisit and potentially adjust your scope if there have been changes in your systems, controls, processes, or Trust Services Criteria applicability. Many organizations update scope as part of their annual audit cycle.
Is the SOC 2 scope the same for Type I and Type II reports?
Yes, the scope elements, such as systems, services, Trust Services Criteria, and locations, can remain the same for both. The key distinction lies in time frame:
- Type I evaluates controls at a specific point in time.
- Type II covers how controls perform over a period, typically 3–12 months.
What are the key elements included in SOC 2 scope?
Your SOC 2 scope should include the following components:
- Services
- Systems
- People
- Processes
- Policies
Table of contents


















