Choose risk-first compliance that’s always on, built for you.
Go back to blogs
PCI DSS 4.0 requirements: a complete breakdown for 2025
Last updated on
October 21, 2025
4
min. read

Your payment data security strategy just became outdated. In March 2024, PCI DSS 4.0 became mandatory, with organizations given time until March 31, 2025, to comply with new requirements. Any incidence of non-compliance can cost your business up to $500,000 in fines alone, not to mention escalating cybersecurity costs and loss of new business.
Imagine the fallout from a customer data breach—it erodes trust, hurts your bottom line, and creates operational chaos. In 2024, the average cost of a data breach hit a record $4.88 million, reinforcing why proactive compliance is critical.
PCI DSS 4.0, the updated global standard for protecting cardholder data, is indispensable for organizations that store, process, or transmit credit card information. PCI DSS 4.0 requirements introduce a shift from the prescriptive style of version 3.2.1 to a more flexible, risk-based model.
PCI DSS 4.0 prioritizes outcome-driven security, continuous monitoring, and strong authentication.
In this guide, we’ll break down what’s changed with PCI DSS, what it means for your business, and how to simplify the transition through automated compliance platforms.
PCI DSS 4.0: Why it’s mission-critical now
First released in 2022, PCI DSS 4.0 marked a significant shift in digital payment security with 64 new requirements. Its predecessor, PCI DSS v3.2.1, was officially retired on March 31, 2024, making PCI DSS 4.0 the primary standard for compliance.
While 13 of its requirements were enforced immediately, 51 initially designated as “best practices” became mandatory as of March31, 2025. Now that the final transition date has passed, organizations are expected to fully comply with all aspects of PCI DSS 4.0.
So, what makes PCI DSS 4.0 fundamentally different?
Unlike its predecessor, PCI DSS 4.0 moves away from a rigid, checklist-based model toward a flexible, risk-based approach. It reframes compliance as an ongoing process—one that’s woven into day-to-day operations rather than revisited annually.
This shift calls for a mindset change: security is no longer a one-time exercise. It’s a continuous commitment tailored to your business risks. The traditional “set it and forget it” model no longer applies.
And now that PCI DSS 4.0 requirements are fully enforced, staying ahead means taking a proactive stance—ensuring your compliance strategy evolves in tandem with emerging threats and business changes.
Besides, several other factors make complying with PCI DSS 4.0 requirements crucial:
- Staying ahead of cyber threats: Cyberattacks are evolving faster than ever. The enhanced controls in PCI DSS 4.0 requirements are designed to protect sensitive cardholder data from increasingly sophisticated threats.
- Increased scrutiny from auditors: With the PCI DSS 4.0 requirements in full force, auditors and Qualified Security Assessors (QSAs) will expect clear, auditable evidence of compliance across every control. Ambiguity or partial efforts will no longer suffice.
- Magnified risks of non-compliance: The shift from reactive response to continuous vigilance leaves less room for error. Any compliance gaps or unintentional missteps aren’t minor issues anymore. They can lead to:
- Significant regulatory fines and lawsuits.
- Revocation of payment processing privileges.
- Increased risk of data breaches and associated costs.
- Loss of customer trust and brand reputation.
- Loss of business and partnerships.
- A strategic business enabler: Achieving and maintaining compliance with PCI DSS 4.0 requirements is a smart business move. By demonstrating a commitment to security, you can build stronger relationships with your customers and attract new investors or partners who insist on rigorous data protection.
Key changes in PCI DSS 4.0
PCI DSS 4.0 isn’t just a minor update; it introduces significant shifts designed to help merchants and payment facilitators tackle sophisticated security threats more effectively.
Here’s a quick summary of the most important changes:
1. Your compliance, your way: the customized approach
One of the most notable additions to the PCI DSS 4.0 requirements is the introduction of the customized approach, alongside the traditional defined approach, which requires you to follow the specified requirements and testing procedures exactly as written.
The customized approach offers greater flexibility. It allows you to design and implement security controls tailored to your unique business needs. However, this is allowed as long as you can clearly demonstrate that your custom controls meet the intent of the PCI DSS 4.0 requirements and provide equivalent or stronger security outcomes. This also involves performing a targeted risk analysis for each custom control and maintaining detailed documentation.
For example, instead of using a prescribed technology, you might implement an alternate solution. But you must confidently prove it delivers the same or better security outcomes.
Note: The customized approach requires formal assessment and validation by a QSA and is ideal for organizations with mature risk management programs and advanced security capabilities.
2. Continuous compliance, not annual check-ins
PCI DSS 4.0 shifts away from the “once-a-year audit” mindset. It emphasizes the importance of continuous compliance, requiring you to monitor, test, and validate controls throughout the year.
This shift helps organizations treat compliance as an ongoing discipline—one that adapts with changing risks and helps build a durable, “always-on” security posture.
3. Expanded multi-factor authentication (MFA)
MFA is now required for all access to the cardholder data environment—not just administrator accounts. Every user accessing the cardholder data environment must authenticate using at least two different types of credentials (e.g., a password plus a one-time code from an authenticator app), reducing the risk of unauthorized access.
4. Addressing modern threats: phishing, password hygiene, and risk analysis
Several new PCI DSS 4.0 requirements target today’s most pressing security concerns. These include enhanced controls to prevent phishing attacks (such as stronger security awareness training), upgraded password policies (a minimum of 12 characters), and mandatory targeted risk analyses.
Full PCI DSS 4.0 requirements checklist
PCI DSS 4.0 retains the familiar structure of 12 core requirements, grouped under six key security goals. While the framework remains consistent, PCI DSS 4.0 introduces essential updates that reflect today’s complex threat landscape.
Below is a breakdown of each security goal and its corresponding requirements—along with what’s changed in PCI DSS 4.0 and how to approach them in practice.
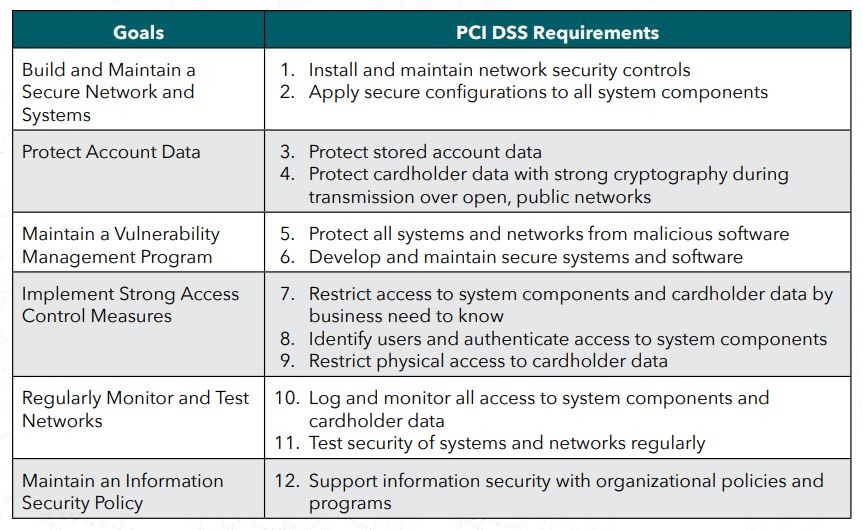
Goal 1: Build and maintain a secure network and systems
PCI DSS Requirement 1: Install and maintain network security controls
This is your first line of defense—network security controls, such as firewalls, are essential to prevent unauthorized access to your cardholder data environment.
Key v4.0 updates:
- The term “firewalls” has been broadened to “network security controls” to accommodate a wider range of security technologies.
- Organizations must document and assign roles and responsibilities for managing these controls.
Practical tip: Review your NSC configurations and rules at all network boundaries every six months. Make sure unauthorized traffic is filtered before it ever reaches your internal systems.
PCI DSS Requirement 2: Apply secure configurations to all system components
Default passwords and settings are an open invitation to cybercriminals, as they can simply guess or find these default passwords online. This requirement focuses on system hardening—changing defaults, removing unused functions, and applying secure settings across all components.
Key v4.0 updates:
- Applies secure configuration requirements beyond just vendor defaults.
- Clear role assignment and documentation are now expected for configuration activities.
Practical tip: Change all default credentials, from servers to network devices and security tools. Maintain detailed change logs for every configuration update to ensure traceability.
Goal 2: Protect account data
PCI DSS Requirement 3: Protect stored account data
A best practice? Don’t store sensitive data unless absolutely necessary. If you must, protect it using strong security mechanisms like encryption, masking, truncation, and hashing.
Key v4.0 updates:
- Emphasizes minimizing storage of account data.
- Requires encrypting any sensitive authentication data if stored before the transaction is complete
- Use technology to prevent unauthorized copying or relocation of Primary Account Numbers (PANs) during remote access.
Practical tip: Use strong encryption and tokenization. Rotate encryption keys regularly, and maintain detailed documentation of all mechanisms and tools used.
PCI DSS Requirement 4: Protect cardholder data with strong cryptography during transmission over open, public networks
Cardholder data is especially vulnerable in transit. This requirement ensures cardholder data is protected using strong cryptography across all open and public channels.
Key v4.0 updates:
- Requires maintaining an inventory of all trusted cryptographic keys and SSL/TLS certificates used for PAN transmission.
- Ensure certificates are valid and not expired or revoked.
Practical tip: Record all endpoints where sensitive account data is transferred and make sure it is encrypted before transmitting it over public networks. Monitor the validity of your certificates and immediately renew them when they expire.
Goal 3: Maintain a vulnerability management program
PCI DSS Requirement 5: Protect all systems and networks from malicious software
Anti-virus software is foundational for environments handling sensitive financial data. This requirement ensures that systems interacting with cardholder data—across endpoints like workstations, servers, on-site computers, and mobile devices—are protected from evolving threats.
Key v4.0 updates:
- “Anti-virus” has been replaced with “anti-malware” to account for advanced technologies like AI-driven threat detection.
- Introduces mechanisms to protect personnel against phishing attacks.
- Requires anti-malware solutions to be used for any removable electronic media.
Practical tip: Deploy anti-malware solutions across your entire IT environment, with automatic updates enabled. Run real-time and periodic scans, and maintain detailed audit logs for each anti-malware application.
PCI DSS Requirement 6: Develop and maintain secure systems and software
Whether your software is developed in-house or outsourced, security must be embedded in all your systems and software. This requirement emphasizes incorporating secure development practices at every stage of the software lifecycle—from design and coding to patching and vulnerability remediation.
Key v4.0 updates:
- Requires maintaining an inventory of your bespoke and custom software to better manage associated vulnerabilities.
- For public-facing web applications, organizations must deploy an automated technical solution to continually detect and prevent web-based attacks and manage scripts on payment pages.
Practical tip: Conduct a thorough risk assessment before developing and deploying any new system or software. Embed strong security practices throughout your software development lifecycle and implement both automated and manual code reviews.
Goal 4: Implement strong access control measures
PCI DSS Requirement 7: Restrict access to system components and cardholder data by business need-to-know
A 2024 data breach report found that 68% of breaches involved a human element. To prevent costly human errors, follow the principle of least privilege and implement strict role-based access control mechanisms. This means users can access cardholder data that they need to perform their job, nothing more.
Key v4.0 updates:
- Requires regular reviews of all user accounts and their access privileges.
- Mandates clearly defined roles and responsibilities for system access.
Practical tip: Clearly define user roles and implement strict role-based access contol. Regularly update these roles and permissions when employees get onboarded, change roles, or exit the company. Monitor access logs to catch and respond to suspicious behavior quickly.
PCI DSS Requirement 8: Identify users and authenticate access to system components
Every user accessing the cardholder data environment must have a unique ID. This not only protects the cardholder data environment from cybercriminals but also lets you monitor and understand who accessed the data. This makes it possible to detect insider threats. In addition, strong authentication methods like 2FA or MFA must be implemented, and passwords must be sufficiently complex and changed regularly.
Key v4.0 updates:
- MFA is now required for all user access to the cardholder data environment, not just remote or admin access.
- Passwords must now be at least 12 characters.
Practical tip: Enforce complex passwords for all system access with regular password changes. Deploy more robust MFA solutions across all access points to track and secure user credentials and protect your cardholder data environment.
PCI DSS Requirement 9: Restrict physical access to cardholder data
Protecting physical cardholder data environments—such as data centers, paper documents, point-of-sale terminals, and servers where data is stored or transmitted—is as vital as safeguarding digital infrastructure. Requirement 9 of PCI DSS 4.0 focuses on controlled access to physical systems and facilities. This can be implemented by placing security cameras at key locations and ensuring permission only to authorized personnel.
Key v4.0 updates:
- Requires a targeted risk analysis to decide how often point-of-interaction (POI) devices should be inspected for tampering or unauthorized replacement.
Practical tip: Grant access only to authorized employees and retain access logs and surveillance recordings. Keep an inventory of all your POI devices and secure or destroy any physical media containing cardholder data after use.
Goal 5: Regularly monitor and test networks
PCI DSS Requirement 10: Log and monitor all access to system components and cardholder data
Monitoring user activity and maintaining secure audit trails is critical—especially when investigating incidents or tracing anomalies. This requirement mandates retaining tamper-proof logs for at least 12 months, with a minimum of three months readily available. Audit logs, including user ID, date, time, invalid access attempts, and system changes, must be sent to your InfoSec team daily for review to identify any suspicious behavior or malicious activity.
Key v4.0 updates:
- Use automated mechanisms to perform audit log reviews.
- All entities (not just service providers) must detect, alert, and promptly address failures of their critical security control systems.
Practical tip: Use a security information and event management (SIEM) tool to centralize your logs and detect anomalies.
PCI DSS Requirement 11: Test the security of systems and networks regularly
Security threats evolve fast—and so must your defenses. This PCI DSS 4.0 requirement ensures that systems are regularly tested through vulnerability scans and penetration testing to identify weaknesses before attackers can exploit them.
Key v4.0 updates:
- Internal vulnerability scans must now be performed using authenticated scanning methods.
- Organizations must deploy change-and-tamper detection mechanisms on payment pages loaded in consumers' browsers.
Practical tip: Run quarterly wireless access point and vulnerability scans through PCI-approved scanning vendors (ASVs). Set up change detection tools that alert your team to unauthorized alterations of critical files or systems.
Goal 6: Maintain an information security policy
PCI DSS Requirement 12: Support information security with organizational policies and programs
A strong information security (InfoSec) policy is foundational to PCI compliance. It should align with your broader governance, risk, and compliance (GRC) strategy and be communicated clearly across the organization—from leadership to frontline teams.
Key v4.0 updates:
- Use targeted risk analyses to determine the frequency of security activities where the standard allows a customized approach.
- Make sure to include threats like phishing and social engineering in the security awareness training.
- Document and validate your PCI DSS scope at least annually.
Practical tip: Use a centralized platform like Scrut to manage policies, automate risk tracking, and drive continuous compliance. Train employees regularly—not just on policies, but on real-world attack methods and response tactics.
Overcoming common challenges in PCI DSS 4.0 compliance with automation
The PCI DSS 4.0 requirements updates bring several benefits—including security reinforcements, breach cost savings, global recognition, and improved business outcomes.
However, several organizations struggle with the added complexities of the new requirements. Spreadsheets, endless evidence chasing, and the constant fear of falling out of compliance—this is the reality many teams face.
The good news? There’s a smarter path forward: compliance automation.
Let’s have a look at the top challenges and how compliance automation can help you overcome them:
Identifying gaps in legacy systems
Trying to make legacy systems meet the new PCI DSS 4.0 requirements can feel like an uphill task. These systems often weren't built for modern security and can't support the new requirements like advanced MFA or longer passwords.
Worse, many are no longer supported by vendors, leaving you exposed to unpatchable vulnerabilities and compliance gaps. Even basic requirements like unique user identification can be difficult to implement on outdated infrastructure.
But that doesn’t mean you're stuck.
Here’s how automation can help you move forward:
- Start with a targeted risk analysis to clearly understand your specific threats and compliance gaps.
- Lean on automation where you can. Automated gap analysis platforms, such as Scrut, can help you quickly identify where your legacy systems fall short of the new PCI DSS 4.0 requirements.
- Once you’ve identified the gaps, you can leverage a couple of options permitted by PCI, such as using "compensating controls" or adopting the "customized approach." However, both require solid expertise and thorough documentation to justify your approach, which can consume many resources.
Misalignment between security controls and compliance evidence
In PCI DSS 4.0, security alone doesn’t cut it—you have to prove it.
PCI DSS 4.0 requirements expect live, continuously updated records to demonstrate ongoing compliance. Point-in-time compliance snapshots? No longer acceptable. Auditors expect to see real-time alignment between your security controls and evidence.
This is a huge challenge if you use custom controls and/or lack automation. What is the result of doing this manually? Delays, errors, missed compliance gaps, and increasing audit fatigue.
This is where compliance platforms like Scrut can help you:
- Map your controls directly to PCI DSS 4.0 requirements so nothing falls through the cracks.
- Streamline monitoring, audit logging, and compliance documentation, cutting manual efforts substantially.
- Automatically collect and centralize evidence, so it’s organized and ready when auditors ask for proof.
Difficulty staying compliant across multiple departments and tools
Keeping PCI DSS 4.0 compliance on track when your organization is spread across different departments, each with its own tech stack, is challenging. Every team might handle security differently, making it tough to keep everyone on the same page.
Decentralized operations entail a higher risk of essential controls slipping through cracks. For instance, a department may forget to update a policy, or someone uses a tool that doesn’t quite meet the new standards.
Here are the practical solutions to ensure everyone is aligned:
- Use a centralized risk and compliance platform that provides a single source of truth to enhance visibility into your organization’s compliance posture.
- Automate your compliance checks to ensure consistency and accountability.
- Conduct cross-team training, ensuring everyone knows their roles and responsibilities and follows standardized compliance processes.
How Scrut helps you stay PCI DSS 4.0 compliant?
Scrut is the leading global compliance automation platform with support for multiple industry frameworks, including the PCI DSS digital payment compliance standard.
With Scrut, you replace manual, error-prone processes involving PCI DSS 4.0 requirements with automation built for modern digital environments.
Here’s how Scrut accelerates your audit readiness with features designed to overcome PCI DSS 4.0’s complex updates:
- Pre-mapped controls to PCI DSS 4.0: Get started fast with controls pre-mapped to the latest PCI DSS 4.0 requirements, saving significant time and effort.
- Built-in templates: Access Scrut’s library of customizable policy templates vetted by industry experts to standardize the document preparation process across departments.
- Automated evidence collection: Connect to multiple third-party business apps in your tech stack to automatically collect and map evidence to the right controls, eliminating spreadsheets and manual screenshots.
- Role-based task assignment: Assign owners, track progress, and enforce accountability with automated workflows designed to keep remediation moving.
- Customizable dashboards and reports: Monitor audit readiness in one place with clear, up-to-date insights on control status and milestones.
- Continuous monitoring to reduce last-minute surprises: Rely on daily automated control tests to identify and address gaps proactively, helping you maintain a continuous, “always-on” state of compliance and audit readiness.
Preparing to comply with the PCI DSS 4.0 requirements? Schedule a demo to see how Scrut automates your compliance journey from day one.
Table of contents


















