Your latest penetration test came back clean. Auditors gave the green light. On paper, everything looks secure. But here’s the catch: a pen-test is only a snapshot in time. It tells you how things looked on the test day, not the day after, the week after, or six months later.
The world doesn’t freeze after an audit. Developers push new code daily. Dependencies shift. Zero-day vulnerabilities emerge overnight. Attackers never stop probing. By the time that report is in your inbox, the ground has already moved beneath your feet.
This creates a dangerous illusion for CISOs and engineering leaders: confidence based on outdated information. The reality is harsher; your security posture can change faster than your ability to measure it.
Why pen-tests alone fall short
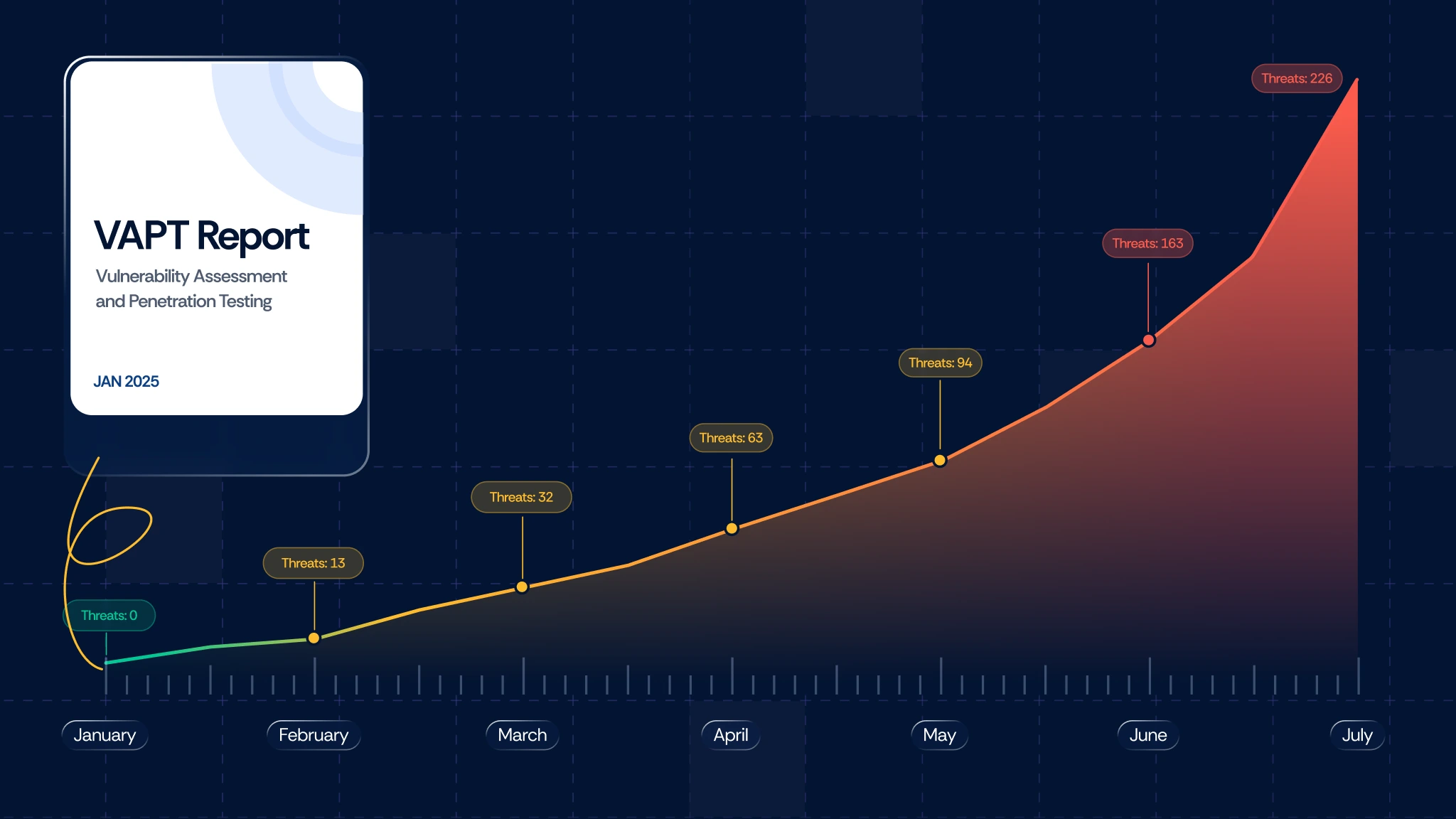
Penetration testing has been a trusted practice for decades. It simulates real-world attacks, uncovers critical flaws, and checks compliance boxes. But it’s still a point-in-time exercise. If your last test was in January and the next is in July, what happens in between? That’s a six‑month blind spot that allows plenty of time for an attacker to slip in unnoticed.
In today’s CI/CD pipelines, where elite teams deploy code multiple times a day, that gap is perilous. What was secure on Monday is ancient history by Tuesday. Relying solely on pen-tests is like getting a home security assessment once a year while leaving the front door unlocked every night.
Take the Log4j crisis in 2021. Countless organizations had just passed pen-tests and audits. Days later, they were exposed to one of the most severe vulnerabilities in recent memory. Snapshots simply couldn’t keep pace with reality.
To bridge this gap, many teams turn to Dynamic Application Security Testing (DAST) scanners. But while they promise continuous coverage, they often deliver continuous chaos.
Traditional DAST scanners: continuous but chaotic
In theory, DAST provides an "attacker's view" of your application. In practice, with the false positive rates that can exceed 50%, they drown teams in noise. But the problems run much deeper than just false positives.
Scanners create friction instead of clarity. Security leaders get volume, not insight. Engineering teams burn cycles chasing down noise while critical fixes wait. This is unsustainable for DevSecOps leaders who are already under pressure from constant product improvements. Scanners shift the burden instead of reducing the risk.
For example, a scanner might list dozens of cookie-related warnings, low-severity headers, and a critical authentication flaw that exposes sensitive customer data. Security teams then have to sift through a wall of findings without clarity on which risks could damage the business.
.webp)
Over time, this noise makes linking vulnerabilities with compliance requirements harder, widening the gap between day‑to‑day security practices and audit reporting. For instance, a scanner may flood teams with hundreds of low‑priority findings while the few issues that directly map to PCI DSS or HIPAA controls get buried. The result is a clean compliance report while genuine risks remain unresolved.
The hidden cost of compliance and security in silos
Most organizations manage application security in one system while compliance is handled in another. What emerges is not collaboration but fragmentation between the functions. The result?
Siloed systems = Increase Risk
This chaos creates more problems than it intended to solve. Now,
- Risks get lost between siloed dashboards.
- Audit checklists pass, even while exploitable vulnerabilities linger in another system.
- Security findings rarely translate into compliance readiness.
- Teams duplicate effort, wasting precious cycles chasing evidence in different systems.
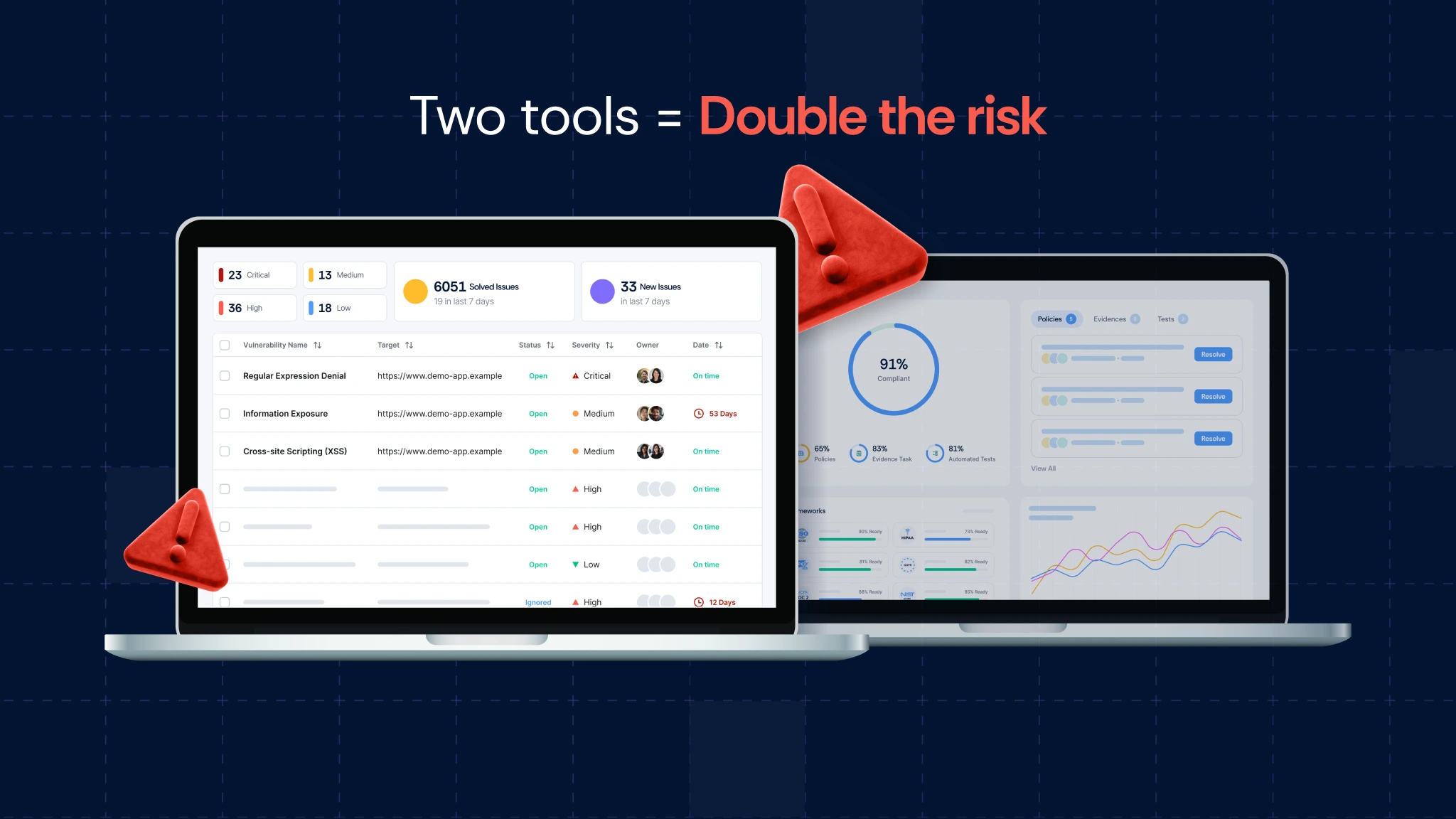
Ironically, both functions share the same mission, yet compliance and AppSec don’t talk, and the risk multiplies..
A practical lens for security leaders
When evaluating your current posture, ask yourself:
- What risk accumulates between our pen-tests?
- How many hours go to triaging false positives vs. fixing actual risk?
- Do we see findings in near-real time or only at audit time?
- Do we have a single, business-aligned view of risk—or stitched-together screenshots?
If these questions give you pause, you’re not alone. Many organizations struggle with the same disconnects. The difference between resilience and exposure often comes down to whether leaders tackle these blind spots head‑on.
Rethinking the future: security unified with compliance
What’s needed isn’t just more testing. It’s a fundamental shift in how organizations think about assurance. Point-in-time checks and noisy scanners can’t keep pace with today’s threat landscape. Security leaders need a new model: continuous runtime security that is always on, business‑aligned, and supports your compliance program:
- Always-On Protection: Security that never sleeps—continuously evaluating code pushes, runtime changes, and dependency drift.
- Meaningful Findings: Validate, de-duplicate, and rank by exploitability and business impact—not just CVSS.
- Aligned Workflows: Security and compliance share context; findings map directly into risk registers and control evidence.
- Actionable Clarity: Engineers fix what matters; CISOs see posture in near-real time
This isn’t a technical tweak. It’s a mindset shift: from snapshots to continuity and from silos to an integrated system.





































