Choose risk-first compliance that’s always on, built for you.
Go back to blogs
MAS TRM implementation made simple: A practical guide for 2025
Last updated on
July 25, 2025
min. read

If you work with financial institutions in Singapore, or are planning to, you’re probably already aware of the Monetary Authority of Singapore’s (MAS) Technology Risk Management (TRM) Guidelines.
Here’s what keeps compliance leaders awake at night. Between July 2023 and December 2024, MAS initiated 163 enforcement actions, including 33 criminal convictions, issuing $4.4 million in financial penalties and $7.16 million in civil penalties for technology-related misconduct ranging from insider trading to anti-money laundering (AML) failures.
But here’s the catch. Even if you’re not a bank or insurer yourself, MAS expects you to manage your technology risks at the same level as the regulated entities you support. That is no small task.
MAS TRM is extensive with over 100 pages of technical language and expectations usually aimed at large enterprises. Without a dedicated compliance or cybersecurity team, it's tough to know where to begin.
While these guidelines are not technically law, ignoring them is not really an option. Non‑compliance can trigger regulatory scrutiny, mandatory remediation, and long‑term damage to your brand’s credibility.
So how do you make sense of MAS TRM and actually implement it without getting lost in policy language?
This guide is here to help. It breaks everything down into simple, actionable steps you can follow. Whether you are a lean startup or a security‑conscious scaleup, you will find a practical path forward here.
What is MAS TRM? (and why you should care)
MAS TRM stands for the Technology Risk Management Guidelines published by the Monetary Authority of Singapore (MAS). Updated in January 2021, these guidelines outline how financial institutions and the vendors that support them should manage technology and cyber risks. This includes areas such as IT governance, system availability, incident response, cyber resilience, and third‑party risk management.
While these guidelines are not legally binding in the strictest sense, they are actively enforced. MAS has taken public action against companies that fall short, especially in cases involving cyber incidents or poor risk controls.
So, whether you are a fintech company, a SaaS provider, or a cloud‑based vendor supporting financial institutions, these rules likely apply to you too.
Pro Tip: TRM compliance is a competitive edge. Vendors aligned with MAS TRM are more likely to pass due diligence by banks and insurers. MAS revised the TRM Guidelines in January 2021 following a sharp rise in cyber threats — the word “cyber” appeared 74 times in the update, compared to just 4 in 2013.
The impact of being MAS TRM non-compliant (July 2023 – Dec 2024)

- 163 enforcement cases opened
- 33 criminal convictions
- $4.4 million in financial penalties
- $7.16 million in civil penalties
“MAS has taken strong enforcement actions and deepened relationships with our partners to uphold the integrity and reputation of Singapore as a trusted financial centre,”
said Ms Peggy Pao‑Keerthi Pei Yu, MAS Executive Director of Enforcement.
“Firm and fair action against misconduct ensures trust in the financial system and is essential to building a dynamic and thriving financial centre,” she added
Quick Fact: MAS revised TRM in January 2021 to reflect a sharp rise in cyber threats—“cyber” appears 74 times in the 2021 document versus just 4 times in the 2013 version.
MAS TRM implementation in a nutshell: 8 Key Steps
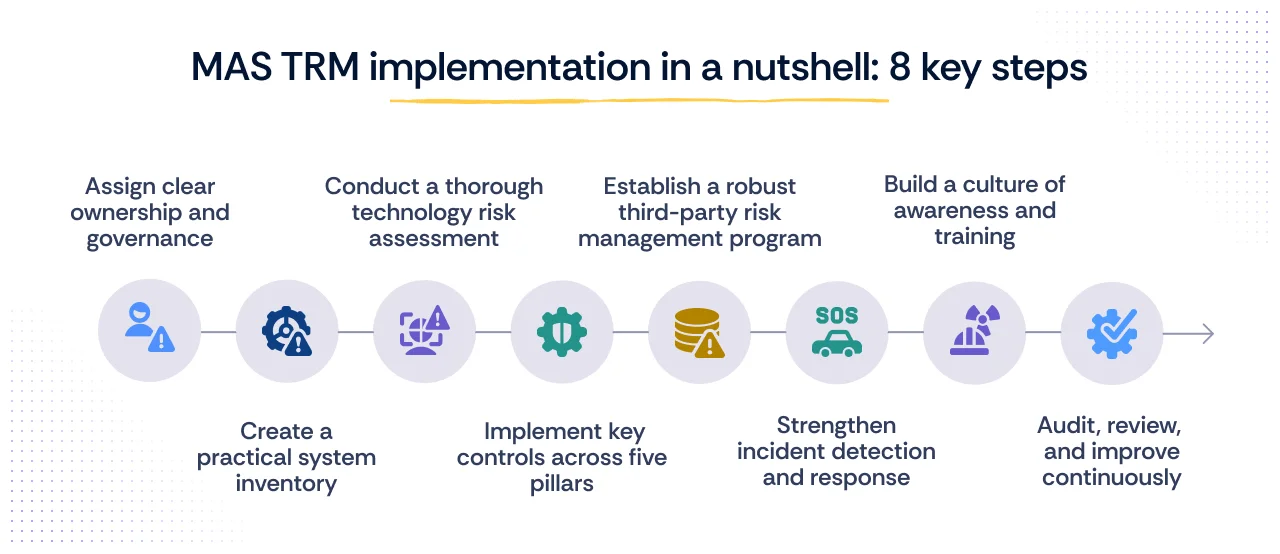
Implementing MAS TRM might seem complex at first glance, but you don’t have to do it all at once. Here’s a simplified, 8-step approach to get started:
1. Assign clear ownership and governance
Start by making it clear who’s in charge. MAS expects your Board and senior management to take full accountability for technology and cyber risks. This doesn't mean they need to get into the weeds, but they must stay informed and engaged.
- Get a senior stakeholder to sign off: Someone at the C-level — ideally your CTO or CEO — should be officially responsible for cyber risk oversight. They don’t need to write your policies, but they should be looped into regular updates, at least once a quarter.
- Appoint a day-to-day owner: You don’t need a full-time CISO right away. What you need is someone who understands your tech stack, security posture, and vendor risks — and can take initiative. This person should own implementation and serve as the point of contact for internal queries or external audits.
- Define responsibilities across teams: Clearly document who handles what between IT, engineering, security, risk, and compliance functions. Overlaps create confusion; gaps create exposure.
- Set up a Technology Risk Committee if needed: If your business is scaling fast or has complex infrastructure, consider forming a cross-functional group to track risks, incidents, and key initiatives.
Scrut makes it easy to assign, track, and audit ownership of every control, risk, and task. Define responsibilities across teams, route tasks to the right owners, and keep leadership in the loop with real-time dashboards and audit-ready reports. Book a Scrut demo now.
2. Create a practical system inventory
Before you can secure anything, you need to know what’s critical. MAS expects you to identify and protect your “critical systems” — but there's no universal checklist for what qualifies. Instead of relying on a vague definition, start by asking the people who know your tech stack best.
Sit down with your DevOps lead, product manager, or engineering head and ask:
"If this system went down or got compromised, what would break?"
To define what counts as a critical system, look for systems that meet one or more of these criteria:
- Handles sensitive customer data or high data volumes
- Plays a role in financial transactions or revenue generation
- Supports core business operations or customer-facing services
- Has regulatory or compliance implications if disrupted
- Has few or no redundancies or fallback options
3. Conduct a thorough technology risk assessment
Before you can protect your systems, you need to understand where the real risks lie. A technology risk assessment helps you do exactly that by identifying your critical systems, spotting vulnerabilities, and understanding the threats that matter most to your business.
- List out your critical assets: These might include payment systems, cloud infrastructure, customer databases, or internal tools. Focus on anything that, if disrupted, could impact operations or compliance.
- Assess risks using the CIA triad: Evaluate each system for threats to confidentiality, integrity, and availability. Ask where sensitive data is stored, what could disrupt services, and what controls already exist.
- Identify gaps: Look beyond what is working. Find areas where controls are missing or weak. These are your highest-priority risks and will guide your next steps.
Scrut gives you a centralized risk register to document, assess, and prioritize tech risks using pre-built risks. Map risks directly to critical assets, uncover control gaps, and assign owners—all in one place. Book a Scrut demo now.
4. Implement key controls across five pillars
The MAS TRM Guidelines highlight five main control areas to organize your technology risk controls. It breaks the 100+ pages of detailed requirements into five manageable focus areas. This way, you can triage which pillar poses the greatest risk instead of tackling all (e.g., if your backups aren’t tested, tackle IT operations first).
- IT operations: Focus on patch management, backup strategies, and disaster recovery planning to reduce downtime and exposure.
- Cybersecurity: Strengthen your defenses with tools for network security, endpoint protection, and data loss prevention.
- User access management: Use the principle of least privilege, enforce strong authentication, and schedule regular access reviews.
- Change management: Ensure changes are logged, approved, versioned, and rolled out in a controlled manner.
- System availability: Maintain uptime using redundancy, capacity planning, and real-time service monitoring.
Begin with the controls that will make the biggest difference, such as encryption, secure software development practices, and managing privileged access.
5. Establish a robust third-party risk management program
Your vendors are part of your risk surface, and MAS expects you to manage their risks as thoroughly as your own systems.
- Maintain a central vendor inventory: List all third-party providers that access your systems or data. Classify them based on the level of risk they introduce (critical/important/non-critical).
- Evaluate vendors before onboarding: Check their security practices, compliance records, and incident history.
- Include TRM-aligned terms in contracts: Add clauses that cover audit rights, data handling requirements, breach reporting timelines, and service termination plans.
- Ensure board-level reporting: Flag high-risk vendors and major incidents to senior management or your Technology Risk Committee at least quarterly.
- Monitor vendor performance continuously: Conduct periodic vendor reviews, automated performance checks, and require independent audits (every 1–3 years for critical vendors).
MAS has taken enforcement action against financial institutions that failed to manage their vendor risks. Being proactive here can help you avoid similar scrutiny.
Scrut’s lets you track vendor risks end-to-end—from onboarding assessments and contract compliance to continuous monitoring. Classify vendors by criticality, run due diligence questionnaires, and schedule periodic reviews—all in one place, aligned with MAS TRM expectations. Book your demo now.
6. Strengthen incident detection and response
Even with strong controls in place, incidents can still occur. What matters is how quickly and effectively you detect and respond to them.
- Set up detection capabilities: Use security logs, automated monitoring tools, and threat intelligence to stay ahead of issues.
- Define clear response plans: Prepare playbooks for common scenarios like ransomware, data breaches, or service disruptions. Make sure every stakeholder knows their role.
- Follow MAS notification timelines (where applicable): In severe incidents, banks and regulated financial institutions may be required to notify MAS within one hour under Notices 644 or 655. If you're a non-bank vendor, check your contract terms — notification obligations are usually routed through your financial client, not MAS directly.
- Conduct post-incident reviews: Perform root cause analysis, document what went wrong, and improve processes to prevent repeat events.
7. Build a culture of awareness and training
Technology alone cannot protect you. People play a critical role, and MAS emphasizes the need for regular training and awareness.
- Train across all departments: Launch a simple, engaging training program for every team—engineering, sales, finance, HR, and beyond. Focus on the “why” using real-world breach examples, and the “how” with clear, actionable dos and don’ts.
- Simulate threats: Use phishing simulations and tabletop exercises to reinforce learning through real-world scenarios.
- Make it part of onboarding: Introduce TRM from Day 1—walk new hires through the basics, run a quick scenario or quiz, and connect them to your security Slack channel. Follow up annually with a short, engaging refresher.
Scrut’s training module helps you roll out organization-wide security awareness programs that stick. Assign TRM-aligned training, track completion across departments, and automate annual refreshers. Book a Scrut demo now.
8. Audit, review, and improve continuously
TRM is not a one-time project. MAS recommends conducting assessments annually or whenever there are major events—like a cyberattack, system overhaul, or operational shift. Treat it as a living process that evolves with your environment and threat landscape.
- Conduct regular internal audits: Establish a formal audit calendar—such as annual comprehensive audits and quarterly spot checks—to evaluate your IT control design and operational effectiveness consistently.
- Engage external experts: Use third-party auditors or consultants to validate controls and reveal compliance gaps.
- Define and track risk metrics: Set down KPIs (e.g., open critical findings, average remediation time, control-test pass rates) and report them alongside qualitative findings.
- Document and track remediation: Record audit findings, assign owners, and follow through with evidence of resolution.
- Report progress to leadership: Provide the board and senior management with regular updates on your TRM status and upcoming priorities.
Documentation you’ll likely need to present
While MAS doesn’t publish a “TRM checklist,” these are commonly expected during inspections or regulatory queries:
- Technology Risk Framework
- Risk Assessment Reports
- IT Policies (Access, Backup, Change Management, etc.)
- Incident Response Plan and Logs
- Third-Party Risk Assessments and Contracts
- Cybersecurity Architecture Diagrams
- Training Records
- Audit Reports and Management Responses
Pro Tip: With Scrut, all these documents and policies reside in one central hub—versioned, time-stamped, and ready to export at a moment's notice.
Common implementation challenges (and how to tackle them)

How Scrut simplifies MAS TRM implementation
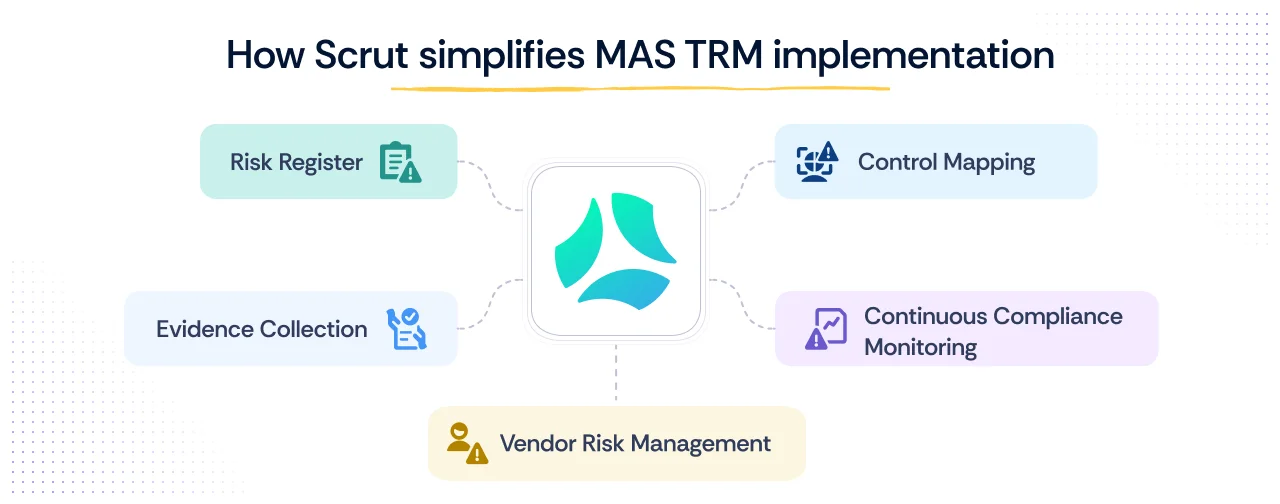
Implementing MAS TRM can feel like a huge lift, especially for lean teams balancing product, security, and compliance. Scrut helps simplify this process with a risk-first, automation-driven approach built for startups and financial vendors working in regulated environments.
Here’s how Scrut makes MAS TRM implementation more manageable:
- Start with a ready-to-go risk register: With Scrut, you gain access to a prebuilt risk library populated with both industry-standard risks and those identified by Scrut experts as relevant.
- Pre-mapped controls: Scrut’s Unified Control Framework ensures that all relevant controls are pre-mapped to MAS TRM, along with other 60+ out-of-the box frameworks. This helps reduce duplication if you're working across multiple standards.
- Continuous control monitoring: Scrut integrates with over 100 tools, including AWS, Google Workspace, GitHub, and more. Scrut then monitors your controls in real time, pulls evidence via the Scrut Monitor, and flags misconfigurations along with remediation steps.
- Audit-ready evidence collection: Scrut automatically gathers, organizes, and tags compliance proof from your connected tools in real time, so you have complete, up-to-date documentation for internal reviews or external audits.
- Vendor Risk Management: Scrut centralizes all your third-party risk workflows—automatically onboarding vendors, standardizing assessments with prebuilt questionnaires, and sending timely reminders—so you gain full visibility into each vendor’s compliance posture.
Bottom line: MAS TRM doesn’t have to become a resource-heavy, manual project. With Scrut, you can keep your compliance program running smoothly while focusing on growth.
MAS TRM compliance is a journey, not a checkbox
The MAS TRM Guidelines are detailed for a reason. They help protect Singapore’s financial ecosystem from real and evolving threats. But that does not mean compliance is only for large or mature companies.
With the right mindset, a clear plan, and smart tooling, even small and fast-growing teams can implement a strong, audit-ready technology risk program.
Whether you're expanding into Singapore, supporting a bank customer, or prepping for your first internal audit, Scrut can help you move forward with confidence.
Ready to get MAS TRM compliant with confidence?
Book a demo with Scrut today and see how easy compliance can be.
Table of contents


















