
The platform connects with a wide range of tools for continuous monitoring, which makes compliance easy to manage.
Tailor any framework to your needs, or upload your own with a simple CSV. No hunting for templates, no switching between tools. Scrut keeps it all in one place.
Demonstrate strong security controls, build customer trust, and accelerate growth. Our built-in SOC 2 controls help you navigate complexities and achieve compliance with ease.
Keep your payment security airtight. Breeze through PCI DSS compliance with real-time monitoring, automated evidence collection, gap analysis, and expert guidance.
Follow HIPAA best practices and automate your compliance workflows. Protect your PHI while taking the complexity out of HIPAA compliance.
Prove your commitment to security, unlock enterprise opportunities, and achieve ISO 27001 compliance faster with prebuilt controls and automated workflows.
If you’re a business incorporating AI, Scrut helps you manage your AI risks by adopting the NIST AI Risk Management Framework to ensure safety, transparency, and responsibility.






The Health Insurance Portability and Accountability Act (HIPAA) oversees the privacy and security of medical information.
It applies to healthcare providers, health plans, clearing houses, and business associates handling Protected Health Information (PHI).

Stay compliant with HIPAA regulations by continuously adhering to all privacy and security requirements. Avoid costly penalties that might range up to $1.5 million per violation.

Ensure your employees learn and maintain best practices to protect PHI, at all times.

Get our in-house HIPAA compliance experts to build an action plan, fix control gaps, and implement the right security controls.
Minimize duplication, reduce effort, and accelerate compliance across all standards.


Use our Compliance Compass to get a detailed report on the compliance frameworks that align with your business priorities.
Scrut simplifies your HIPAA journey so you can secure customer and stakeholder trust from day one.
Jumpstart your compliance journey with prebuilt controls for a faster start and a content library mapped with HIPAA requirements.
Upload/sync your policies or create new ones with expert‑vetted HIPAA templates.
Each control is mapped directly to specific HIPAA standards, such as Administrative, Physical, or Technical Safeguards, enabling automatic validation and ongoing testing aligned with the right section of the Privacy and Security Rules.
.webp)
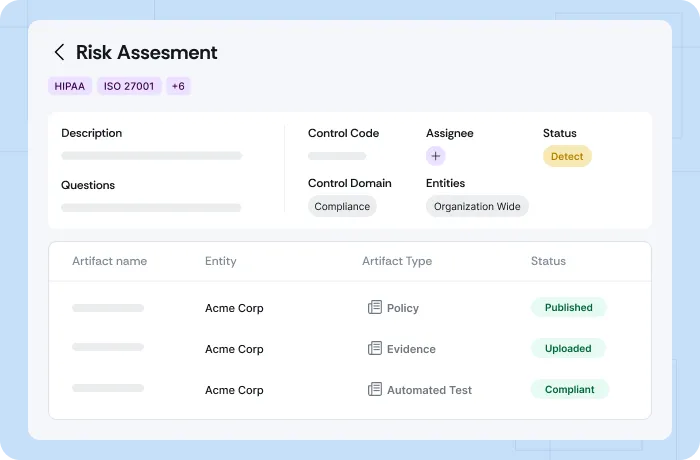
Leverage hundreds of prebuilt tests to identify gaps against HIPAA controls. Let the platform monitor your HIPAA controls continuously, and automatically gather evidence in auditor‑friendly formats.
Scrut’s daily automated tests track HIPAA-specific safeguards, such as encryption enforcement, access control configurations, and audit log integrity, and link each test result with time-stamped evidence folders for easy export.


Preparing for a HIPAA audit? Bring your auditors or use our trusted partner network. With Scrut’s centralized Audit Center, you can collaborate, track progress, and manage the entire audit process in one place.
Invite auditors directly to your HIPAA audit project, they’ll have access to mapped ePHI controls, can request evidence, and raise findings, all within an interface that supports full traceability.
.avif)
Scrut’s in-house compliance experts support you in implementing security controls and closing identified gaps.
Build and maintain an audit-ready security posture aligned with current industry standards.
The Scrut Platform also helps map PHI workflows, interpret breach notification thresholds, and guide secure communication controls in line with the HIPAA Breach Notification Rule and PHI access audit requirements.


The platform connects with a wide range of tools for continuous monitoring, which makes compliance easy to manage.
.webp)


Scrut helped our company navigate the complexities of SOC 2, ISO 27001, HIPAA, GDPR, CCPA, and PCI compliance with ease.
.webp)


Scrut made our audits smoother and multi-framework compliance more efficient.


.svg)



%20(1).png)
%20(1).png)




Connect your your cloud infrastructure, application stack and security toolkit to the Scrut platform for real-time visibility into your security posture.
Automatically map your technical controls to HIPAA’s security rule requirements and identify gaps in data protection, access control, and encryption.
Identify potential vulnerabilities in your admin, physical, and technical safeguards.
Evaluate risks against HIPAA’s security, privacy, and breach notification rules.
Get a detailed report with prioritized remediation actions.
Get a guided remediation workflow with clear action items to align your security measures with HIPAA.
Assign tasks, collaborate with internal teams, and implement corrective actions to comply with HIPAA-mandated safeguards.
Validate compliance before external audits with Scrut’s in-house experts.
Demonstrate compliance with low manual effort with automated evidence collection and audit-ready reports.
Always stay aligned with HIPAA regulations with automated control monitoring.
Stay ready for the next audit with automated evidence collection, detailed compliance reports, and real-time alerts for policy revisions and test failures.






In the current macroeconomic environment, lower revenues, workforce reduction, and higher production costs are normalized. On one hand, an influx of cybercrime at unprecedented levels necessitates more vigilance, while on the other...

The Payment Card Industry Data Security Standard (PCI DSS) underwent a major update in March 2022. Following this, a limited revision, PCI DSS 4.0.1, was introduced to refine and enhance the standard’s usability.

As a patient engagement platform on a mission to allow patients access medical care with 10x less stress and effort, Cortico knew all too well about the multiple compliance requirements that arise at the intersection of health care & technology.

ISO 27001 is a well-known system for handling information security. Companies in different fields, such as IT, healthcare, finance, and manufacturing, use it around the world. This standard helps businesses build a...

As Artificial Intelligence (AI) technologies become more widespread, managing risks such as bias, security vulnerabilities, and unpredictability is increasingly important.
Securing your PHI shouldn’t be a constant hassle. Scrut automates your workflows, from risk assessments to monitoring, so you can put your compliance worries on the back burner.



