In the ever-evolving realm of cybersecurity, the emergence of AI-powered threats poses unprecedented challenges to organizations worldwide. These sophisticated entities leverage machine learning and other advanced techniques to circumvent conventional security measures.
The need for organizations to stay abreast of emerging threats is imperative. From ransomware to data breaches, understanding the evolving nature of cyber threats is crucial to developing effective defense strategies.
Internal penetration testing is a proactive and strategic measure for safeguarding against the specific challenges posed by AI-powered threats.
This blog will provide a foundational understanding of these threats, setting the stage for a comprehensive exploration of the importance of internal penetration testing in mitigating the associated risks.
AI’s impact on cybersecurity vulnerabilities
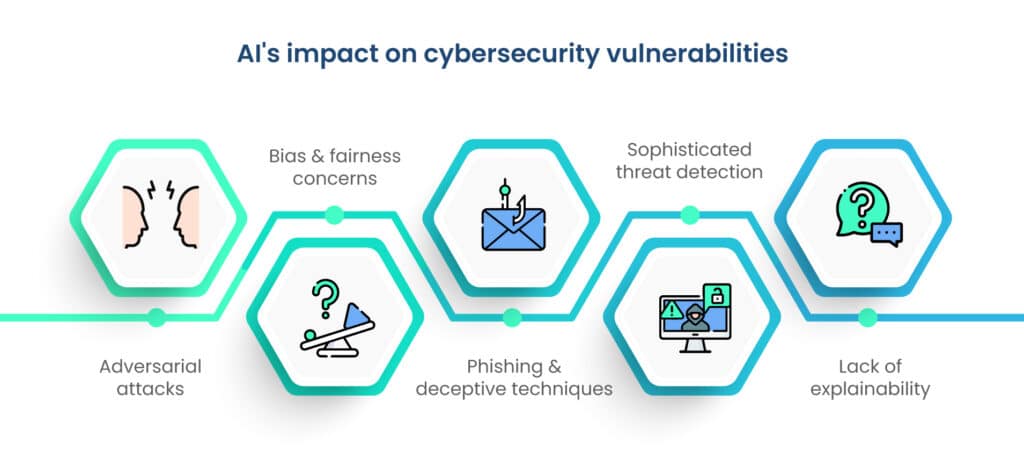
The integration of artificial intelligence (AI) into cybersecurity has transformed the threat landscape, introducing both innovative solutions and new vulnerabilities.
Here is an overview of the impact of AI on cybersecurity vulnerabilities and the challenges organizations face in securing AI-driven systems.
1. Adversarial attacks
AI systems, including those used in cybersecurity, are susceptible to adversarial attacks. Adversaries manipulate input data to deceive AI algorithms, leading to incorrect or compromised outcomes. This emphasizes the need for robust defenses against adversarial manipulation to maintain the integrity of AI-driven security mechanisms.
2. Bias and fairness concerns
AI models used in cybersecurity processes may inadvertently perpetuate biases present in training data, leading to unfair or discriminatory outcomes. Addressing bias in AI algorithms is crucial for ensuring that security decisions are equitable and unbiased, aligning with ethical and legal standards.
3. Phishing and deceptive techniques
AI is increasingly employed in phishing detection, but cybercriminals are also leveraging AI to enhance the sophistication of their attacks. AI-driven phishing campaigns can craft more convincing and personalized messages, challenging traditional detection methods and requiring cybersecurity professionals to adapt their strategies.
4. Sophisticated threat detection
While AI enhances threat detection capabilities, it also presents challenges in identifying sophisticated attacks. AI-powered attacks, such as those using generative adversarial networks (GANs) to create realistic fake content, require advanced defenses that can differentiate between genuine and manipulated data.
5. Lack of explainability
The inherent complexity of some AI models results in a lack of explainability, making it challenging for cybersecurity professionals to understand and interpret the decision-making process of AI systems. This opacity can hinder effective threat analysis and response.
Nature of AI-powered Threats in Cybersecurity

The advent of artificial intelligence has brought forth a new era of cyber threats, characterized by adaptive and intelligent adversaries.
The nature of AI-powered threats represents a paradigm shift in the world of cybersecurity, introducing adversaries that are not only dynamic and adaptive but also capable of learning and evolving their tactics over time.
At the core of these threats is the integration of machine learning (ML) and other advanced techniques, enabling malicious actors to circumvent conventional security measures with unprecedented sophistication.
1. They leverage machine learning as a weapon
AI-powered threats leverage machine learning algorithms to autonomously analyze vast amounts of data, identify patterns, and refine their attack strategies. This ability allows them to dynamically adjust their tactics in response to changes in the cybersecurity landscape, making traditional, static defenses less effective. The use of machine learning also empowers these threats to launch more targeted and personalized attacks, increasing the likelihood of success.
2. They evade detection by adapting to security measures
One hallmark of AI-powered threats is their capacity to evade detection by learning from and adapting to security measures. These threats can continuously analyze the responses of security systems, identify weaknesses, and adjust their behaviors to avoid detection. This constant evolution makes it challenging for static security protocols to keep pace, as AI adversaries can exploit vulnerabilities faster than they can be patched.
3. They excel in automation and exhibit high speed and scale
AI-powered threats excel in automation, allowing them to carry out attacks on a massive scale without direct human intervention. From crafting sophisticated phishing emails to executing complex social engineering schemes, these threats can operate tirelessly and efficiently. The scale and speed at which AI adversaries can operate amplify the challenges faced by security teams, necessitating proactive measures to detect and counteract them.
4. They employ sophisticated deception techniques
To enhance their effectiveness, AI-powered threats often employ sophisticated deception techniques. This includes mimicking legitimate user behavior, generating convincing deepfake content, or even impersonating trusted entities. By blending into the normal flow of network activities, these threats can operate surreptitiously, increasing the difficulty of detection.
5. They circumvent conventional security measures
Conventional security measures, such as signature-based antivirus software or rule-based intrusion detection systems, are often ill-equipped to handle the dynamic and unpredictable nature of AI-powered threats.
These threats can learn to manipulate vulnerabilities, bypass access controls, and exploit weaknesses in real-time, requiring a more adaptive and proactive approach to cybersecurity.
Unique vulnerabilities within internal systems
Internal systems pose distinctive vulnerabilities that demand targeted assessment to fortify an organization’s cybersecurity defenses. These vulnerabilities often include insider threats, misconfigurations, and insufficient access controls.
Insider threats may arise from disgruntled employees or inadvertent actions, while misconfigurations and lax access controls can expose critical assets to unauthorized access. Addressing these unique vulnerabilities requires a comprehensive understanding of internal network architecture and user behaviors.
Distinctive features of internal penetration testing

By exploring the distinctive features of internal penetration testing and its intersection with AI security, organizations can enhance their overall cybersecurity resilience in the face of evolving threats and technologies.
Key features include:
1. Testing AI models
Internal penetration testing extends to AI systems, evaluating their security from both a functional and adversarial perspective. This involves assessing the robustness of AI models against potential attacks.
2. Securing AI training data
Internal testing addresses the security of AI training datasets, ensuring that they are free from biases, manipulation, or malicious inputs that could compromise the integrity of AI models.
3. AI-driven threat detection
Leveraging AI for internal penetration testing enhances the detection of sophisticated threats within the organization’s network, providing a proactive defense against AI-specific vulnerabilities.
4. Integration with incident response
Internal testing helps organizations refine their incident response plans to effectively address security incidents involving AI systems, ensuring a swift and well-coordinated response to emerging threats.
A comprehensive internal penetration testing checklist is essential for ensuring a systematic examination of internal systems. This checklist may include assessing user access controls, evaluating network segmentation, testing for misconfigurations, scrutinizing the effectiveness of intrusion detection systems, and simulating insider threats.
By incorporating both internal and external penetration testing into an organization’s cybersecurity strategy and adhering to a thorough checklist, businesses can identify and address vulnerabilities from multiple perspectives, enhancing their overall resilience against a diverse range of cyber threats.
Internal vs external penetration testing
While internal and external penetration testing shares the common goal of identifying and mitigating vulnerabilities, they adopt different perspectives to offer a comprehensive assessment of an organization’s overall cybersecurity posture.
How Internal Penetration Testing Addresses Traditional Threats
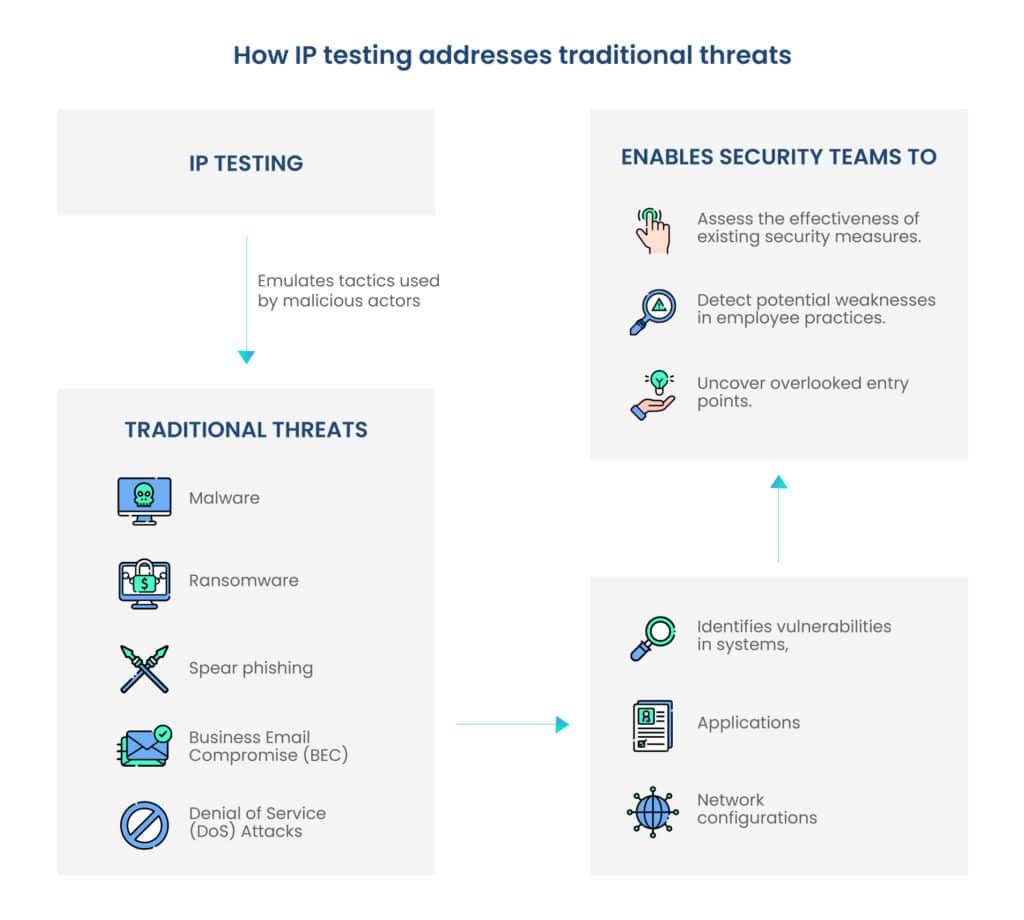
As technology advances, so too do the tactics employed by cyber adversaries. Organizations must continually reassess and fortify their defenses to keep pace with the evolving nature of cyber threats.
Internal penetration testing plays a crucial role in addressing traditional threats by simulating real-world attack scenarios within an organization’s network and infrastructure.
Traditional threats include
- Malware: Malicious software is constantly evolving, with new variants and techniques to evade detection.
- Ransomware: This subset of malware has become particularly concerning, with attackers encrypting data and demanding ransom payments.
- Spear phishing: Targeted attacks against specific individuals or organizations, often using personalized information.
- Business Email Compromise (BEC): Phishing attacks that target employees with access to financial or sensitive information.
- Denial of Service (DoS) Attacks: Coordinated attacks from multiple sources overwhelm a system, making it inaccessible.
By emulating the tactics used by malicious actors, internal penetration testing helps identify vulnerabilities in systems, applications, and network configurations that could be exploited by common traditional threats such as malware and phishing.
This proactive testing approach enables security teams to assess the effectiveness of existing security measures, detect potential weaknesses in employee practices, and uncover overlooked entry points that adversaries might exploit.
Additionally, internal penetration testing provides valuable insights into the overall security posture of an organization, allowing for the implementation of targeted remediation strategies to fortify defenses against traditional cyber threats, ultimately enhancing the resilience of the entire cybersecurity infrastructure.
How internal penetration testing addresses emerging concerns

Internal penetration testing proves instrumental in addressing emerging concerns within the cybersecurity landscape by mimicking advanced attack scenarios and uncovering vulnerabilities that may be exploited by evolving threats.
Emerging threats include:
A. Supply chain attacks
- Attackers compromise the software supply chain: This is done to distribute malware, affecting numerous organizations downstream.
- Hardware supply chain: Concerns about compromised hardware components being inserted during manufacturing.
B. Zero-day vulnerabilities
- Unknown exploits: Attacks that target vulnerabilities unknown to the software vendor, leaving little time for patching.
- Exploit Marketplaces: A thriving underground market where hackers buy and sell zero-day exploits.
C. AI and machine learning threats
- Adversarial attacks: Manipulating AI systems by inputting carefully crafted data to deceive or mislead.
- Automated threats: Malicious use of AI for tasks like generating convincing deepfake content or automating attacks.
D. Internet of Things (IoT) Security
- Device vulnerabilities: Many IoT devices lack robust security measures, making them susceptible to exploitation.
- Massive attack surface: The proliferation of connected devices increases the overall attack surface.
E. Cloud security
- Misconfigurations: Improperly configured cloud services can expose sensitive data.
- Shared responsibility model: Understanding the division of security responsibilities between cloud service providers and users.
F. Cybersecurity skills gap
- Shortage of experts: The demand for cybersecurity professionals exceeds the available talent.
- Continuous training: The need for ongoing education due to rapidly evolving threats and technologies.
G. Legal and compliance challenges
- Data protection laws: Complying with various regulations such as GDPR, CCPA, and others.
- Incident reporting: Legal requirements for reporting security incidents and breaches.
Mitigation strategies used after internal penetration testing
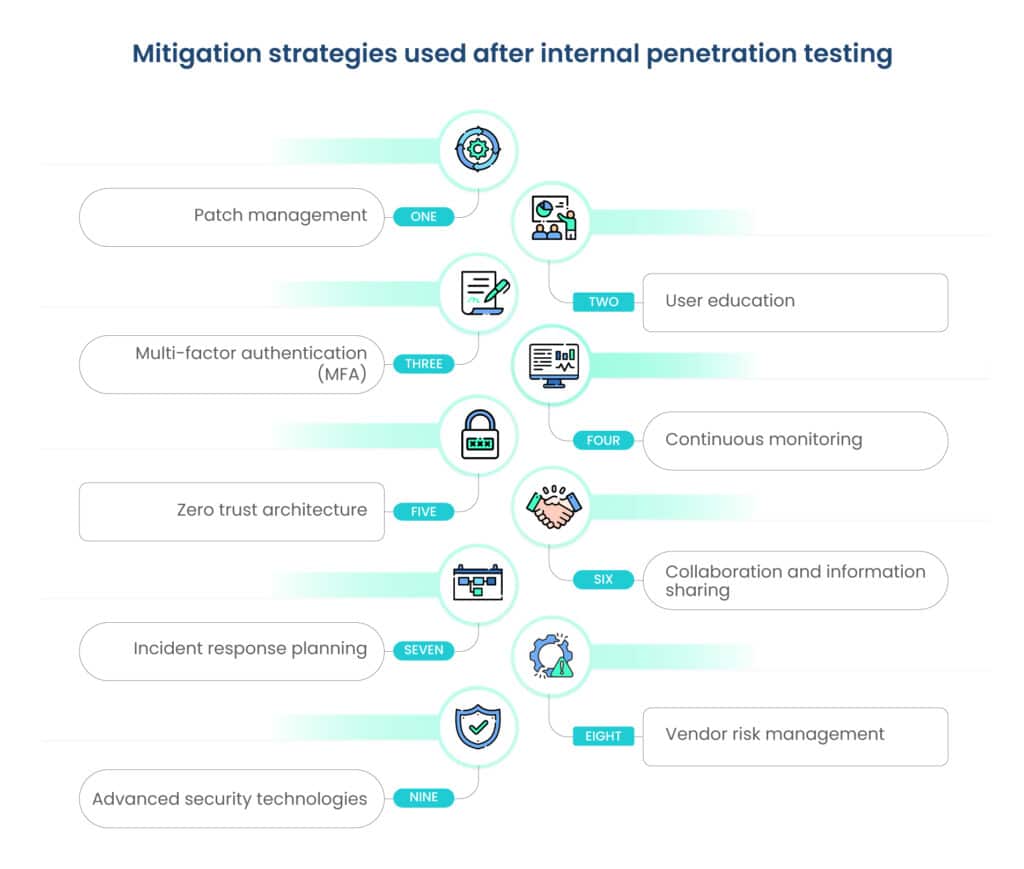
Internal penetration testing is a critical component of a comprehensive cybersecurity strategy, providing organizations with valuable insights into potential vulnerabilities and weaknesses within their internal networks. Once vulnerabilities are identified through the testing process, the next crucial step involves implementing robust mitigation strategies.
This involves the following measures:
- Patch management: Regularly update software and systems to address known vulnerabilities.
- User education: Train users to recognize and avoid phishing attempts and other social engineering tactics.
- Multi-factor authentication (MFA): Enhance access control with an additional layer of authentication.
- Continuous monitoring: Implement tools for real-time threat detection and response.
- Zero trust architecture: Assume that no user or system is inherently trustworthy and verify everything.
- Collaboration and information sharing: Share threat intelligence within the industry to enhance collective defense.
- Incident response planning: Develop and regularly test incident response plans to minimize damage in case of a security incident.
- Vendor risk management: Assess and monitor the security practices of third-party vendors.
- Advanced security technologies: Implement next-generation firewalls, endpoint protection, and intrusion detection/prevention systems.
Organizations can leverage the findings from internal penetration testing to improve employee awareness and training programs, reducing the risk of falling victim to social engineering tactics.
Additionally, the insights gained from these tests enable organizations to fine-tune incident response plans, ensuring a swift and effective response in the event of a security incident.
By combining internal penetration testing with proactive mitigation strategies, organizations can significantly enhance their cybersecurity resilience and create a more secure internal environment that can withstand both traditional and emerging cyber threats.
The significance of internal testing in AI security
Internal testing plays a pivotal role in securing AI systems within an organization’s cybersecurity framework.
1. Testing AI models
Internal testing involves evaluating the security of AI models from both functional and adversarial perspectives. This includes assessing the robustness of AI algorithms against various attack vectors to identify and mitigate potential vulnerabilities.
2. Securing AI training data
Internal testing extends to securing the training data used to train AI models. Ensuring the integrity and reliability of training datasets is crucial to prevent biases, manipulations, or poisoned data that could compromise the effectiveness of AI-driven security systems.
3. AI-driven threat detection
Leveraging AI in internal testing enhances the detection of sophisticated threats within the organization’s network. This proactive approach enables the identification of potential vulnerabilities and the development of effective countermeasures against AI-specific attacks.
4. Integration with incident response
Internal testing helps organizations integrate AI-specific incident response measures into their cybersecurity protocols. This ensures a coordinated and swift response to security incidents involving AI systems, minimizing potential damage and ensuring a resilient security posture.
5. Continuous adaptation of defense strategies and enhancement of overall security
Given the evolving nature of AI and cybersecurity threats, internal testing facilitates continuous adaptation. Regular assessments allow organizations to stay ahead of emerging vulnerabilities, update defense strategies, and enhance the overall security of AI-driven systems.
Internal penetration testing tools in AI context
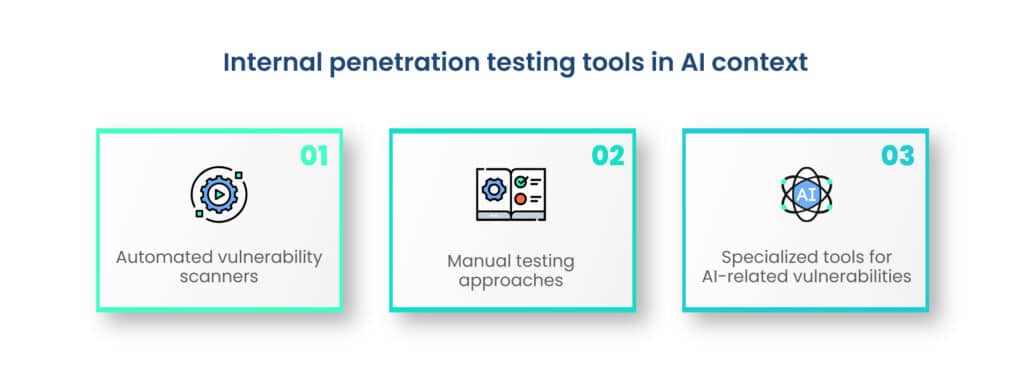
- Automated vulnerability scanners: Automated vulnerability scanners play a pivotal role in internal penetration testing by efficiently identifying known vulnerabilities across AI systems. These tools streamline the detection process, enabling organizations to rapidly assess potential risks and prioritize remediation efforts.
- Manual testing approaches: Manual testing remains indispensable for uncovering nuanced vulnerabilities that automated scanners might overlook. Skilled penetration testers simulate sophisticated attack scenarios, leveraging their expertise to identify weaknesses in AI models, algorithms, and data handling processes.
- Specialized tools for AI-related vulnerabilities: Addressing the unique challenges posed by AI-driven systems requires specialized tools. These tools assess adversarial robustness, analyze biases in AI algorithms, and scrutinize the resilience of AI models against emerging threats.
Frequency and integration of internal penetration into cybersecurity strategy
- Determining testing frequency: The frequency of internal penetration testing should align with the dynamic nature of both internal systems and AI advancements. Regular assessments, conducted at least annually, are essential to adapt to evolving threats and ensure the ongoing efficacy of security measures.
- Integrating internal penetration testing into overall security strategies: Internal penetration testing should be seamlessly integrated into an organization’s overarching cybersecurity strategy. By aligning testing activities with risk management initiatives, organizations can effectively prioritize and address vulnerabilities within their internal systems.
Best practices for effective internal penetration testing
- Establishing testing protocols: Define clear testing protocols to ensure consistency and comprehensiveness in internal penetration testing. Standardized procedures help teams systematically evaluate internal systems, fostering a proactive security posture.
- Collaboration with AI security measures: Collaboration between internal penetration testing teams and AI security measures is essential. This synergistic approach ensures that AI-specific vulnerabilities are systematically assessed and addressed, optimizing the overall effectiveness of cybersecurity defenses.
- Adapting internal testing to AI advancements: As AI continues to advance, internal penetration testing must evolve accordingly. Future trends involve incorporating AI-driven tools in testing methodologies, assessing the security of AI training datasets, and staying abreast of emerging AI-related threats.
Wrapping up: The crucial role of internal penetration testing
Internal penetration testing is indispensable for identifying and mitigating unique vulnerabilities within an organization’s internal systems. By employing a combination of automated scanners, manual testing approaches, and specialized tools, and integrating testing into overall cybersecurity strategies, organizations can proactively strengthen their defenses against evolving threats.
As organizations navigate the complex intersection of internal systems and AI, a robust call to action is necessary. By taking decisive action, organizations can fortify their cybersecurity defenses against the evolving landscape of AI-related threats. Scrut can help you strengthen your cybersecurity defenses against AI threats. To learn more, schedule a demo today.
Internal penetration testing focuses on evaluating vulnerabilities within an organization’s internal systems. Unlike external testing, it simulates an attack from within the network, providing insights into potential risks and weaknesses that external threats may exploit.
Internal penetration testing is crucial in the face of AI threats as it helps identify vulnerabilities specific to internal systems. AI-powered adversaries may exploit these internal weaknesses, making it essential to assess and fortify defenses from within.
The frequency of internal penetration testing depends on the organization’s risk profile, industry regulations, and the evolving threat landscape. Regular assessments, at least annually or more frequently for high-risk environments, are recommended to ensure ongoing resilience against AI threats.
Various methodologies and tools, such as automated vulnerability scanners, manual testing, and threat modeling, are employed in internal penetration testing. Additionally, specialized tools may be used to assess AI-related vulnerabilities, ensuring a comprehensive evaluation.
Yes, internal penetration testing should be an integral part of an organization’s cybersecurity strategy. By identifying and addressing vulnerabilities from within, it contributes to the long-term resilience against AI threats, helping organizations stay ahead of evolving cybersecurity challenges.





































