In an era where digital threats loom large, and cyberattacks have become a ubiquitous reality, the significance of incident response has never been more pronounced. From stealthy data breaches to disruptive ransomware attacks, organizations of all sizes are continuously at risk of falling victim to a variety of malicious cyber activities.
It’s in this landscape that incident response emerges as the frontline defense, a well-coordinated strategy aimed at mitigating the impact of these security breaches.
A single data breach can cost organizations $4.35 million. System downtimes, on the other hand, cost an average of $100,000 in lost revenues, maintenance charges, and employee productivity.
What is incident response?
Incident response refers to the process of responding to cybersecurity breaches in a timely manner. The process usually involves helping an organization detect security breaches, limit the scope of damages and blast radius, eradicate the root cause, and perform post-incident recovery.
The cybersecurity incident response cycle starts by detecting data security breaches, then limiting the extent of the damage, eliminating the root cause, and generating post-incident recovery reports.
Cybersecurity tools like CAASM can help to spot, flag, investigate, remediate, and recover from such incidents that require an immediate response.
A cybersecurity incident can vary depending on the type of cyber attack, such as violations of regulations (i.e., PCI DSS, GDPR, HIPAA), policies and laws, or authorized access to an organization’s data and cyber assets.
If cybersecurity incidents are not contained and resolved effectively, they could cost your organization millions of dollars and a tarnished reputation.
That’s why it’s crucial for every organization to create a cybersecurity incident response plan to curb financial and reputational damages in the event of security breaches.
What are security KPIs?
Key Performance Indicators (KPIs) related to security are metrics used to measure the effectiveness, performance, and overall health of an organization’s security practices and systems.
These cybersecurity KPIs help organizations track their security posture, identify vulnerabilities, and make informed decisions to improve their security measures. Security KPIs can vary depending on the organization’s industry, size, and specific security goals.
There are plenty of incident response KPIs an organization can track and monitor to identify and diagnose security incidents and resolve them in a timely manner.
But first, an organization must figure out which incident response metrics it needs to prioritize to measure the success of its cybersecurity incident response plan.
Below, we’ve outlined the 9 most important incident response KPIs to help you stay on top of problem identification and remediation efforts.
A. Number of alerts created
If you use an incident response tool, it’s a good idea to start tracking how many alerts are usually generated in a specific time period (i.e., weekly, bi-weekly, monthly, etc.).
Doing so will give you a baseline of how busy your incident response team is and also identify periods where there is a significant increase and decrease in alerts.
B. Mean time to detect
Mean time to detect (MTTD) is a crucial metric as it tells you the average amount of time your team takes to detect a security incident in your organization’s network.
To calculate MTTD, add the total amount of time your team takes to detect security incidents during a specific period and divide that by the number of total incidents.
C. Mean time to acknowledge
Mean time to acknowledge (MTTA) measures the amount of time a member of your incident response team takes to notice and start working on the problem after the system generates an alert.
The higher the MTTA, the longer it will take to start working on resolving the incident.
D. Mean time to respond/resolve/recover
Mean time to respond/resolve/recover (MTTR) is the amount of time your incident response team takes to diagnose and resolve the problem and get the affected assets back up and running again.
To calculate MTTR, take the total amount of downtime for a specific period and divide it by the number of incidents that occurred during the same period.
E. Mean time to contain
Mean time to contain (MTTC) combines MTTD, MTTA, and MTTR together to create a holistic view of how well your organization is currently responding to cybersecurity incidents.
Simply put, it tells you how long your incident response team takes to detect, acknowledge, and resolve a cybersecurity incident and prevent the same incident from occurring again in the future.
F. Mean time between failures
Mean time between failures (MTBF) helps organizations measure the time between repairable system failures of an application, product, or system.
Tracking these metrics is important because it helps to determine if systems are failing more regularly than expected so that they can analyze the root cause and prevent the same issue from repeating.
G. Average incident response time
The average incident response time indicates how quickly your incident response team allocates responsibilities to the designated professional and resolves the threat.
If you find the resolution times to be higher than they should be, organizations must examine the issue and figure out a solution to resolve it.
H. SLA compliance rate
This incident response KPI helps to measure the percentage of incidents that are handled as per the pre-defined service level agreement (SLA) timeframe.
Tracking your SLA compliance rate is crucial because it helps to ensure that your cybersecurity incident response plan is fulfilling its pre-defined objectives and delivering the promised results.
I. Cost per incident
Finally, the cost per incident measures the average cost incurred by your organization to resolve and recover from each security breach or incident.
Tracking this metric is important because it is helpful in assessing the financial impact of cybersecurity incidents, determining which methods are most effective, and prioritizing investments to minimize future incidents.
These are the main metrics an organization should be tracking to measure the performance of its incident response plan.
However, these metrics can vary significantly depending on your organization’s unique goals, data types, etc.
While these are all important metrics, sometimes they’re not enough to truly evaluate an incident response.
What are the limitations of basic security KPIs?
While traditional security KPIs like MTTD and MTTR are valuable for measuring incident response success, they have certain limitations that can hinder a comprehensive assessment of an organization’s security posture and incident response effectiveness.
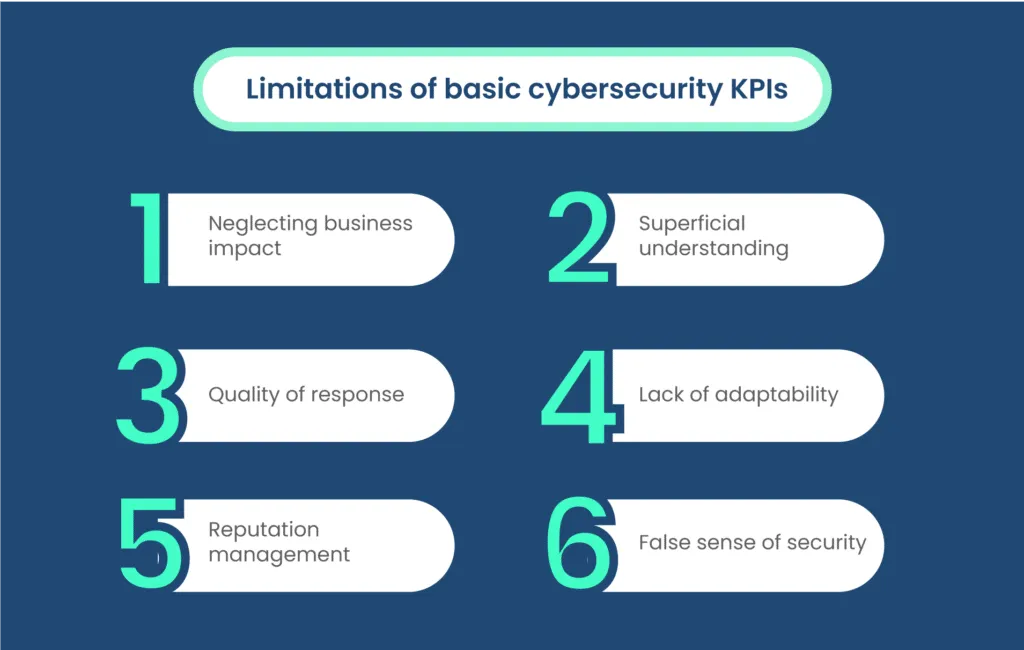
Here are some of the limitations:
A. Neglecting business impact
MTTD and MTTR focus primarily on response times without considering the broader business impact of security incidents. Organizations may prioritize speedy resolution at the expense of thoroughly understanding the incident’s potential consequences on operations, customer trust, and reputation.
Example: A company experiences a data breach and quickly mitigates the issue but fails to adequately communicate with affected customers, leading to confusion and eroding customer trust.
B. Superficial understanding
Relying solely on MTTD and MTTR can result in a superficial understanding of the incident response process. These cybersecurity KPIs do not delve into the complexity of the incident, the depth of analysis, or the steps taken to prevent similar incidents in the future.
Example: An organization quickly identifies and removes malware from its network but doesn’t perform a thorough investigation to determine the source of the attack or the potential data exfiltrated.
C. Quality of response
Basic security KPIs do not assess the quality and effectiveness of the response itself. Focusing on time metrics alone might lead to hasty decisions or overlooking crucial details, resulting in recurring incidents.
Example: An organization responds promptly to a security incident by shutting down affected systems but fails to properly eradicate the underlying cause, leading to repeated breaches.
D. Lack of adaptability
Basic cybersecurity KPIs might not account for the evolving nature of security threats and the need for adaptive responses. Organizations need to consider the flexibility of their incident response strategies to address emerging threats effectively.
Example: A company’s incident response plan is tailored to a specific type of attack, but when faced with a novel attack vector, the predefined security KPIs fail to capture the organization’s ability to adapt and respond effectively.
E. Reputation management
While traditional cybersecurity KPIs focus on technical aspects of incident response, they may not adequately measure the organization’s ability to manage the fallout from a security incident in terms of public relations, brand reputation, and customer communication.
Example: A company experiences a major breach and successfully mitigates the incident within the defined MTTR, but the lack of transparency in communicating the incident to stakeholders results in negative media coverage and customer backlash.
F. False sense of security
Relying solely on basic cybersecurity KPIs can create a false sense of security if the organization perceives itself as well-prepared due to meeting time-based goals. This can lead to complacency and a failure to continuously improve security practices.
Example: An organization consistently meets its MTTD and MTTR targets, leading it to believe that its incident response capabilities are strong. However, a security audit reveals multiple gaps and vulnerabilities in its response procedures.
To overcome these limitations, organizations should complement traditional security KPIs with additional metrics that assess the business impact, depth of analysis, response quality, adaptability, and reputation management aspects of incident response. This holistic approach ensures a well-rounded evaluation of incident response effectiveness and helps organizations make informed decisions to enhance their security strategies.
What are the factors influencing comprehensive incident response evaluation?
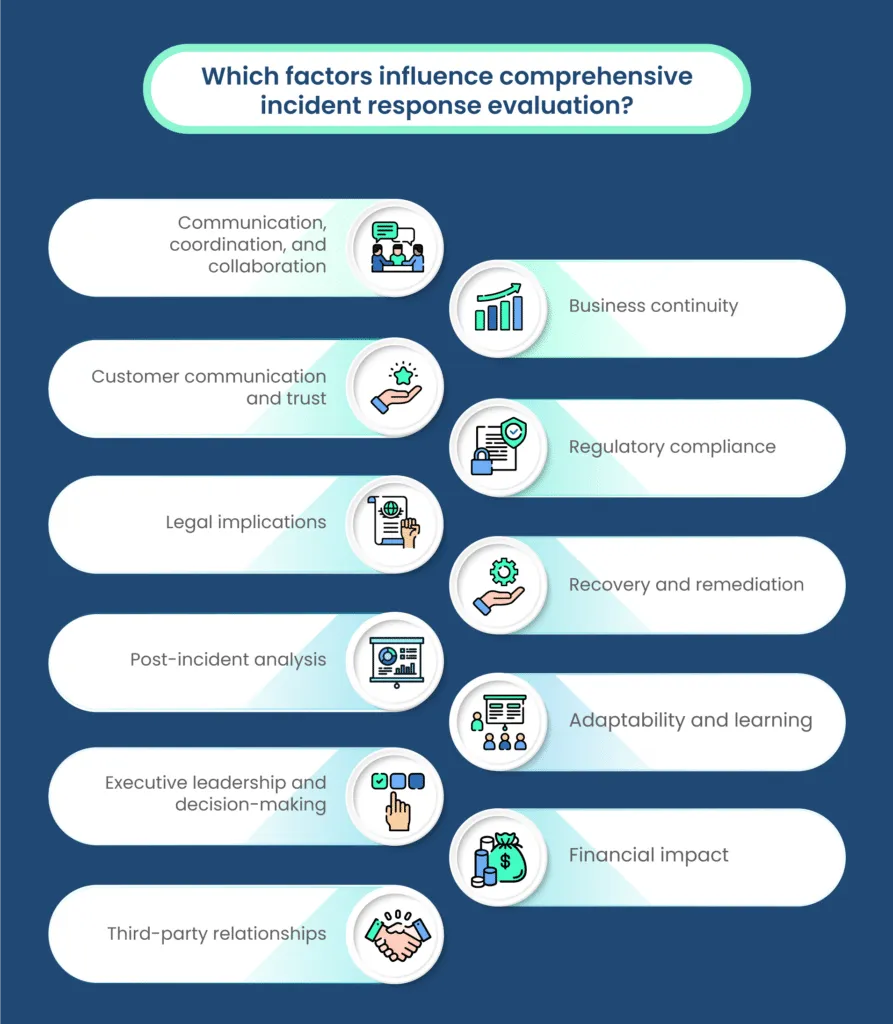
Comprehensive evaluation of incident response effectiveness requires taking into account various factors beyond just technical aspects. This holistic approach acknowledges the interconnectedness of technical, organizational, and regulatory elements. Here’s why considering these factors is crucial:
A. Communication, coordination, and collaboration
Effective incident response hinges on seamless communication, coordination, and collaboration among cross-functional teams. The ability of teams to share information, insights, and decisions in a timely manner significantly impacts response quality and speed.
B. Business continuity
Incident response should aim not only to contain and mitigate the immediate impact of an incident but also to ensure minimal disruption to business operations. Evaluating how well the organization managed to maintain critical functions during the incident is essential.
C. Customer communication and trust
Transparency and timely communication with customers about incidents are crucial to maintaining their trust. Evaluating how well the organization communicated with affected customers and stakeholders can have a long-term impact on reputation and customer loyalty.
D. Regulatory compliance
Many industries are subject to regulatory requirements regarding incident reporting, data protection, and breach notification. Failing to comply with these regulations can lead to legal consequences. Evaluating whether incident response adhered to relevant regulatory standards is vital.
E. Legal implications
Incident response may involve legal considerations such as preserving evidence for potential legal actions. Failing to handle these aspects appropriately can have legal ramifications down the line.
F. Recovery and remediation
Beyond containment, the effective incident response also involves thorough recovery and remediation efforts. Evaluating how well the organization restored affected systems, data, and services is crucial to overall resilience.
G. Post-incident analysis
Conducting post-incident analyses is essential for understanding the root causes of incidents and implementing preventive measures. An effective incident response evaluates the depth of analysis conducted after the incident to prevent future occurrences.
H. Adaptability and learning
Incident response effectiveness is not solely based on predefined plans but also on the organization’s ability to adapt to new and evolving threats. Evaluating the organization’s capacity to learn from incidents and continuously improve its response strategies is vital.
I. Executive leadership and decision-making
Senior leadership’s involvement in incident response decisions and support for necessary actions play a pivotal role. Evaluating their engagement and decision-making effectiveness is essential.
J. Financial impact
Incidents can have direct financial implications, including costs associated with remediation, legal actions, and potential revenue loss. Evaluating the financial impact of an incident helps quantify the effectiveness of the response.
K. Third-party relationships
Incidents can impact relationships with third-party vendors, partners, and customers. Evaluating how well the organization manages these relationships during and after an incident is important.
In summary, comprehensive incident response evaluation goes beyond technical metrics and considers the broader organizational, communication, regulatory, and business-related factors that influence the overall effectiveness of the response. A multidimensional assessment helps organizations understand not only how well they address technical issues but also how well they manage the operational, reputational, legal, and compliance aspects of security incidents.
Which are the advanced metrics for holistic incident response assessment?

Let’s delve into advanced metrics that contribute to a more comprehensive assessment of incident response effectiveness:
A. Business impact metrics
These metrics assess the tangible effects of an incident on an organization’s bottom line and operations. They include
- Revenue impact: Measuring the financial losses incurred due to downtime, reduced sales, or customer churn.
- Productivity impact: Evaluating how the incident disrupts internal workflows, causing delays or inefficiencies.
- Customer satisfaction impact: Gauging how the incident affects customer experience, loyalty, and retention.
Contribution: Business impact metrics shed light on the real-world consequences of security incidents, emphasizing the importance of swift and effective incident response to minimize financial losses and operational disruptions.
B. Reputation Management Metrics
These metrics focus on the perception of the organization among customers, stakeholders, and the public after an incident. They include
- Media coverage: Measuring the extent of media attention and framing of the incident.
- Social media sentiment: Analyzing social media mentions and sentiment to gauge public opinion.
- Brand perception: Tracking changes in brand sentiment and reputation in the aftermath of the incident.
Contribution: Reputation management metrics highlight the significance of transparent communication, timely response, and proactive measures to mitigate the potential long-term damage to an organization’s image and trustworthiness.
C. Regulatory compliance metrics
These metrics assess the organization’s adherence to relevant legal and industry regulations during and after an incident. They include
- Regulatory violations: Identifying instances where the incident response process deviated from regulatory requirements.
- Breach notification timeliness: Measuring how well the organization adhered to mandatory breach notification timelines.
- Data protection compliance: Evaluating whether personal and sensitive data were appropriately safeguarded during the incident.
Contribution: Regulatory compliance metrics emphasize the importance of aligning incident response activities with legal obligations and industry standards, reducing the risk of legal penalties and reputational damage.
D. Lessons learned metrics
These metrics focus on the organization’s ability to learn from incidents and improve its incident response capabilities over time. They include
- Post-incident recommendations implemented: Measuring the percentage of post-incident recommendations that were effectively integrated into the organization’s security practices.
- Incident recurrence rate: Tracking the frequency of similar incidents occurring after implementing lessons learned from previous incidents.
- Incident response plan updates: Evaluating how frequently incident response plans are reviewed, updated, and tested.
Contribution: Lessons learned metrics emphasize the importance of continuous improvement by analyzing past incidents, identifying weaknesses, and implementing changes to enhance future incident response effectiveness.
By incorporating these advanced metrics into the assessment of incident response, organizations gain a more holistic understanding of their capabilities. This broader evaluation extends beyond technical aspects, encompassing business impact, reputation management, regulatory alignment, and ongoing improvement. Such a comprehensive approach ensures that incident response efforts are not only efficient from a technical standpoint but also aligned with the organization’s strategic goals and the expectations of customers, stakeholders, and regulators.
How to implement advanced evaluation techniques
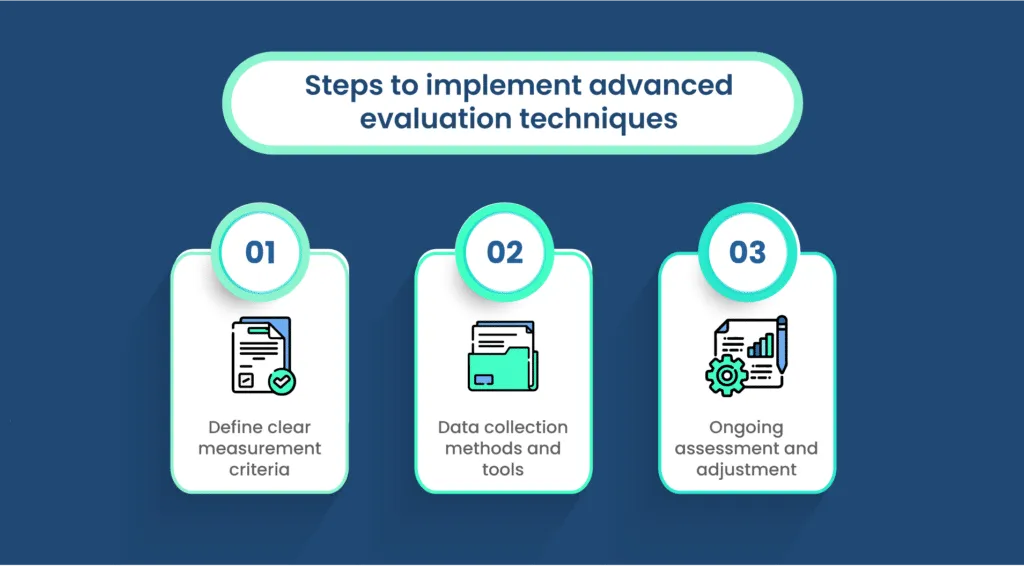
Incorporating advanced metrics into your incident response evaluation strategy involves careful planning, defined measurement criteria, proper data collection methods, and a commitment to ongoing assessment and improvement. Here’s a step-by-step guide to help you implement these techniques:
A. Define clear measurement criteria
For each advanced metric (business impact, reputation, compliance, and lessons learned), establish clear and quantifiable criteria that align with your organization’s goals and objectives. These criteria should define what success looks like for each metric.
B. Data collection methods and tools
Determine how you will collect data to measure each metric. This may involve using a combination of automated tools, manual data collection, surveys, interviews, and data analytics. Consider the following approaches:
- Business impact: Integrate incident response data with financial and operational metrics to assess revenue, productivity, and customer satisfaction impact.
- Reputation management: Monitor social media sentiment, track media coverage, and conduct post-incident customer surveys to gauge public perception.
- Regulatory compliance: Document incident response processes, breach notifications, and data protection measures to demonstrate compliance.
- Lessons learned: Conduct post-incident reviews, gather feedback from stakeholders, and track the implementation of recommendations.
C. Ongoing assessment and adjustment
Regularly review and adjust your evaluation techniques based on the changing threat landscape, organizational goals, and stakeholder expectations. Continuously refine your measurement criteria and data collection methods to ensure accuracy and relevance.
The path forward: Achieving comprehensive incident response assessment
In the journey towards achieving comprehensive incident response assessment, several key points stand out:
A. Balancing technical metrics and broader considerations
While traditional technical metrics like MTTD and MTTR offer valuable insights, it’s essential to balance them with a broader perspective. Business impact, reputation, regulatory compliance, and lessons learned metrics provide a more complete understanding of incident response effectiveness.
B. Incorporating advanced metrics
Advanced metrics such as business impact, reputation management, regulatory compliance, and lessons learned contribute to a more holistic evaluation. These metrics provide insights into financial repercussions, customer trust, legal adherence, and the organization’s capacity to learn and adapt.
C. Data collection and measurement criteria
Implementing advanced metrics requires defined measurement criteria and well-thought-out data collection methods. Each metric should have clear, quantifiable goals that align with organizational objectives.
D. Ongoing assessment and evolution
Incident response evaluation strategies should be dynamic and adaptable. Regularly assess and adjust your techniques to account for changing threats, stakeholder expectations, and organizational shifts. Embrace a culture of continuous improvement.
Conclusion
In a rapidly evolving digital landscape, incident response effectiveness hinges on more than just technical proficiency. Organizations must embrace a multifaceted evaluation approach that encompasses business impact, reputation, compliance, and lessons learned. By combining traditional technical metrics with advanced evaluation techniques, organizations can make informed decisions, enhance their incident response capabilities, and safeguard their operations, reputation, and customer trust. As threats evolve, so should our strategies. It’s time to redefine incident response assessment and move towards a more holistic understanding of success.
FAQs
1. Why is traditional incident response assessment not enough?
Traditional assessment metrics like MTTD and MTTR provide valuable insights but focus solely on technical aspects. The comprehensive evaluation considers broader factors, such as financial losses, customer trust, legal compliance, and the organization’s capacity to learn from incidents.
2. What are advanced metrics in incident response evaluation?
Advanced metrics include business impact, reputation management, regulatory compliance, and lessons learned. These metrics provide a more holistic understanding of incident response effectiveness by considering financial consequences, public perception, legal adherence, and continuous improvement efforts.
3. How can organizations benefit from a comprehensive approach?
A comprehensive approach to incident response evaluation provides a clearer picture of the impact of incidents on business, reputation, compliance, and learning. This helps organizations make proactive improvements and better protect operations, reputation, and customer trust.
4. How can I balance technical and non-technical metrics?
While technical metrics like MTTD and MTTR are important, combining them with non-technical metrics offers a more well-rounded assessment. Balancing both perspectives ensures that incident response efforts align with organizational goals and stakeholder expectations.