Vulnerability scanning and penetration testing are frequently confused but serve distinct purposes.
Penetration testing provides a detailed report of potential vulnerabilities and the damage they could cause, allowing you to prioritize fixes based on risk level. Vulnerability scanning, however, can provide general information on what should be fixed and what needs to be addressed.
In this article, we’ll review the two most common security testing methods businesses use for compliance initiatives: penetration testing and vulnerability scanning.
What is the Penetration Test?
A penetration test is a detailed examination that includes a live person nudging into the complexities of your network to exploit weaknesses in your systems. During a penetration test, a pentester imitates the activities of a real-world black-hat hacker and uses manual tests to find potential vulnerabilities and misconfigurations, exploit weaknesses, and infiltrate business assets.
A penetration tester’s work cannot be automated. They use manual vulnerability assessments and penetration testing to conduct attacks. Through hands-on research and exploiting vulnerabilities, a penetration test simulates a hacker breaking into a business system. Penetration testing aims to verify all your security controls, such as authentication, authorization, integrity, confidentiality, and comply with industry standards.
Why do you need Penetration Testing?
Penetration testing allows you to understand the risk a specific vulnerability poses. Because manual pen-testers confirm each vulnerability, you get detailed instructions on reproducing it without worrying about false positives.
Benefits of Penetration Testing?
The benefits of penetration testing are as follows:
- A penetration test will reveal the vulnerabilities in the target environment and the associated risks. A high-order risk assessment classifies the vulnerabilities as high/medium/low-risk issues.
- It provides an independent assessment of the effectiveness of existing security processes, ensuring that configuration management practices have been followed correctly.
- Penetration testing investigates existing flaws in your system or application configurations as well as your network infrastructure. A report informs you of your security vulnerabilities so you can decide what software and hardware improvements to make.
- IT departments address the compliance and auditing aspects of procedures such as PCI DSS, HIPAA, GLBA, SARBANES – OXLEY, and report penetration testing requirements identified in PCI DSS or NIST/FISMA directives. Complete records of your penetration tests can help you avoid significant penalties for noncompliance.
What is Vulnerability Scan?
A vulnerability scan is an activity carried out by an automated tool with minimal human intervention. Identifying potential vulnerabilities in network devices, such as firewalls, routers, switches, servers, and applications, is known as vulnerability scanning.
A vulnerability scanner determines the structure of the scanned asset and then performs a series of automated tests on each element of that structure. Vulnerability scanning searches your assets for known vulnerabilities and generates a report, often highlighting the aspects which pose the greatest risk to your organization. It is mostly automated and is usually used on many assets on a corporate network.
Why do you need Vulnerability Scanning?
Cyber criminals are constantly looking for unpatched systems to exploit. Even if a patch for a specific vulnerability already exists, criminals can exploit the time lag between the vulnerability becoming known and a patch being published to a given system being patched. Vulnerability scanning is necessary because internet-connected systems are constantly scanned and attacked. This is why timely patching of systems is critical, and running a vulnerability scan will help identify missing patches that need to be applied.
Benefits of Vulnerability Scanning?
The benefits of penetration testing are as follows:
- Many vulnerabilities are difficult to find and are not noticeable until they are identified. Vulnerability scanning identifies these flaws, allowing you to correct them.
- It’s difficult to keep track of all the components, which range from on-premise to public and private clouds and everything in between. Regular vulnerability scans can keep you updated on new vulnerabilities and attack vectors, allowing you to change configurations more effectively.
- Automated scans are simple and will save you money in the long run. This is because vulnerability scanning reduces the risks of a data breach, which will incur various costs, including remediation and customer loss due to reputational damage.
- A vulnerability assessment can help protect assets if malicious code is hidden in any of the said assets. It also assists in achieving and maintaining compliance with any applicable federal and international security regulations.
Penetration Testing vs. Vulnerability Scanning
The following table shows the difference between a penetration test and a vulnerability scan:
Both tests have unique features and approaches. Vulnerability scans provide valuable insight into your network security on a weekly, monthly, or quarterly basis, whereas penetration tests are a thorough way to examine your network security thoroughly. A vulnerability assessment aims to improve the security system and create a more mature, integrated security program. Penetration testing, on the other hand, only provides a snapshot of the effectiveness of your security program.
How Does Scrut Help?
Scrut Risk Management software assists organizations in managing penetration tests and vulnerability assessments as part of a security assessment plan. It provides a centralized interface for identifying, assessing, and mitigating IT and cyber risk. The platform gives organizations the awareness they require to stay ahead of risks and conveys the consequences of risk on high-priority strategic targets.

Risk Identification
The tool enables organizations to create and maintain their risk registers. It allows you to use the pre-loaded risk library or create custom risks, establish the treatment method, define mitigation workflows, and assign tasks in one place.
Scrut’s risk register dashboard displays detailed information about each risk to your business, such as the nature of the risk, mitigation measures to address it, and more.
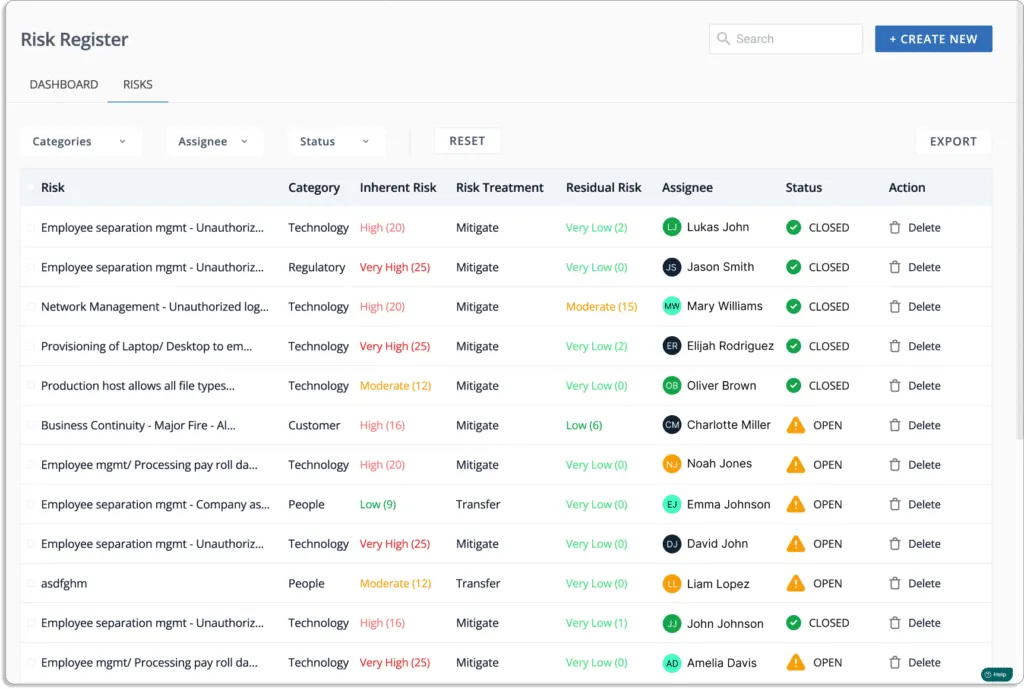
The tool automatically maps these risks against various compliance frameworks and controls, as shown in the screenshot below.
Risk Assessment
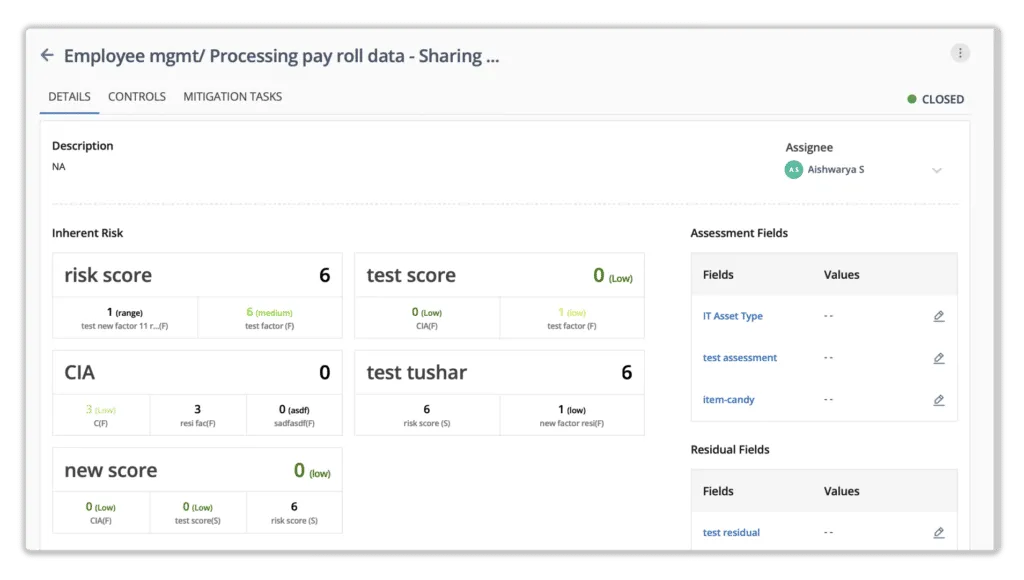
Scrut provides automated workflows for performing risk assessments and implementing risk remediation, acceptance, transference, or avoidance treatment plans. It generates risk scores based on the likelihood and impact of events.

Risk = Likelihood * Impact
Likelihood (5) * Impact (4) = 20 (high)
This frees up your team’s time and optimizes their bandwidth. It improves visibility into an organization’s risk posture by automatically rescoring risks in response to updates in related risks and mitigation tasks. With built-in scoring methodologies, expert-provided inherent risk scores, and automated workflows, creating new IT risk programs to avoid, control, and mitigate risk is quick and easy.
The table below can help you interpret the final score:
Risk Treatment Plan
Scrut makes it simple for you to understand your risk exposure by identifying and mitigating major risk areas. The tool provides four ways to treat a risk:
- Avoid: To remove the possibility of risk by correcting an error.
- Transfer: Transferring the risk to another entity is a form of action.
- Mitigate: To act to reduce the potential impact of a risk by putting in place mitigating controls.
- Accept: Sometimes, you have to accept the risk because the cost of treatment is greater than the damage caused by the risk.
The platform also allows you to create and document mitigation tasks, as shown in the screenshot below.

Case study – Find out how BarRaiser used Scrut Automation to automatically monitor its cloud environment for risks and misconfigurations. By automating GRC, they have simplified the process of maintaining continuous compliance with ISO 27001, SOC 2, and GDPR.
You can schedule a demo to learn more about our product, Scrut.






































