How can SaaS Startups create an Enterprise-Friendly Security Posture?
Many SaaS platforms store massive amounts of sensitive data that can be accessed from any device, putting critical information at risk.
As a result, SaaS providers face unique security challenges in meeting enterprise customers’ expectations in terms of delivering products and services.
Without implementing proper security controls, it is nearly impossible for startups to sell their products to enterprises.
This article will guide you through the best practices for creating an enterprise-friendly security posture to help you close large deals.
Your security posture measures your organization’s vulnerability to cyber attacks or data breaches.
To strengthen your security posture, you must maintain an up-to-date inventory of the information assets. Once inventory is taken, tracking who has access to this information is critical. Also, enabling multi-factor authentication, firewall, and other security tools can help enhance the security posture. Anti-phishing and email security tools can assist businesses in preventing spam from reaching users’ inboxes as part of a comprehensive security posture.
Now, let’s discuss about compliance certifications.
Compliance is a Sign of Strong InfoSec Posture
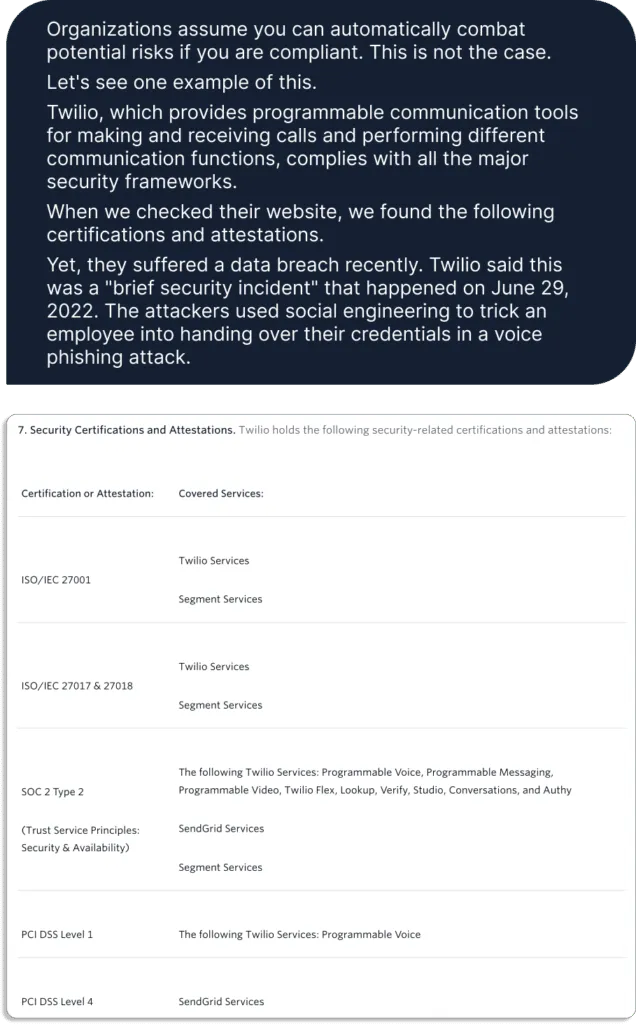
Are promises and privacy policies enough to show that your startup has good security controls? Definitely NO! Does it mean there are better ways available to improve your security posture? Well, Yes.
Businesses can do it via compliance certifications, reports and attestations. To comply with these security and privacy frameworks (such as GDPR, SOC 2, ISO 27001, etc.) companies setup controls that are reflected in their privacy policies and procedures.
You might think, how can compliance help you earn and keep trust. To help you understand that, below we have listed some of the pointers for the same:
- It’s not easy for companies to get compliance certifications.
- Since most of the compliance standard was made by highly trusted independent bodies (ISO, CIS, etc,), which are highly specialized in their domain, unlike normal customers, their standards are very high. Unlike normal customers, companies cannot trick/confuse them with complex jargon.
- Moreover, compliance certificates (or reports or attestations) are given by independent third-parties neutral bodies, called auditors, and they are deemed more trustable than assurance from your salespeople or CTO. They do not have any conflict of interest, unlike the salespeople or CTOs.
- Compliance is not new; it’s been here for years. For example, ISO 27001 was released in 2005. But does that mean, there hasn’t been any change in its policy? No, that’s not the case. The body that maintains these frameworks keeps on improving them based on changing business needs.
- Furthermore, many of the frameworks are enforced by the law of the land, and there are heavy fines and penalties for violations.
For example, fine for GDPR violation

Fine for HIPAA violation

Fine for CCPA

An intro to different privacy frameworks
Moreover, there is a reputational risk associated with compliance violations.
When you respond to their RPF, you would find a security questionnaire section where you need to state if you are compliant with certain standards and regulations. Most enterprises won’t even consider your sales proposal unless you have certain security certifications.
Risk, Governance, and Compliance: The Need for More Than Just Compliance
Governance, risk, and compliance have a lot in common. Each discipline generates valuable information for the other two, impacting the organization’s success.
For example, a company may be subject to a new industry data security standard, which requires the implementation of internal data-protection controls (a governance activity), which help reduce cyber risk (a risk management activity).
With the compliance-first approach, organizations frequently experience a false sense of security after meeting the regulatory requirements of an industry standard.
Scrut provides you with single-window observability into your InfoSec risks. What makes us stand apart from other GRC platforms is that we are a “risk-first” GRC platform rather than a “compliance-first” one.
The concept of a risk-first approach is that each organization prioritizes its unique risks; addressing compliance requirements becomes just one component of a comprehensive risk management strategy.
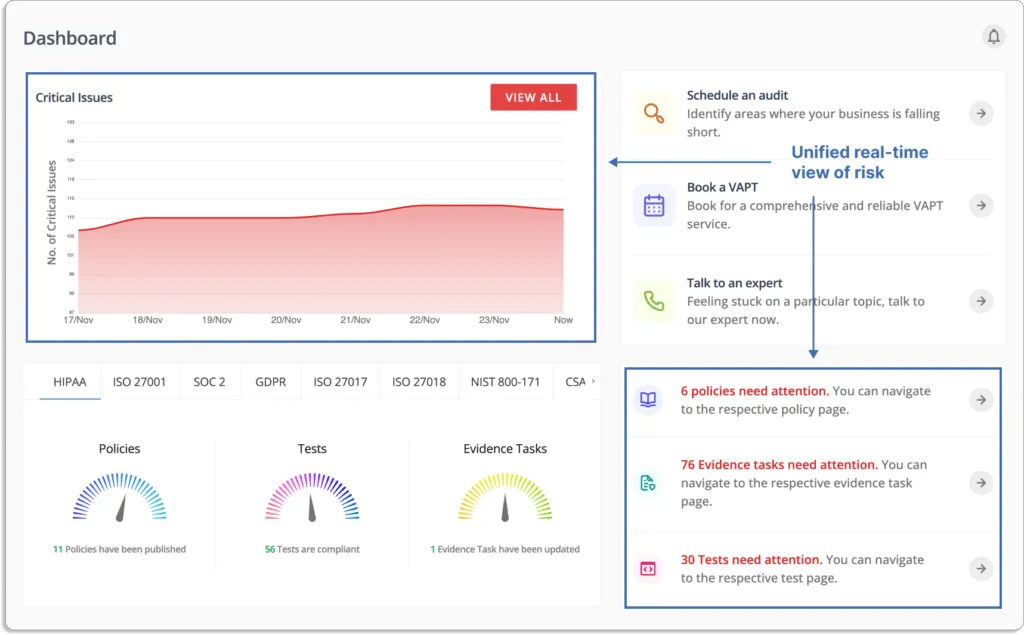
Risk visibility is a vital element of all InfoSec programs. Without visibility into all your risks, you cannot work on them and stay secure and compliant. You must discover risks to establish governance in your organization and stay compliant.
Instead of being secure at a specific point in time, Scrut keeps you secure by continuously monitoring your multi-cloud environment and zeroes down all risks and misconfigurations in real-time.
To uncover all the risks in your organization,
- Scrut first discovers all your assets
- Then it maps the relationships between all the assets
Additionally, Scrut gives you the context into these risks. With this context, you can prioritize how to act on those risks.
How Scrut Helps Startups Create an Enterprise Friendly Security posture
As we have seen above, risk observability is the foundation for creating a strong InfoSec posture.
Now, let’s see how Scrut helps startups with risk management. You can establish governance in your organization and stay secure with proper risk management. Scrut provides a consolidated view of your risk and compliance posture.
Using Scrut, you can make your risk posture efficient and enterprise-friendly, which will help you close your deals with enterprises.

You can follow the below-mentioned risk management plan to strengthen your startup risk posture:
1. Risk management with Scrut
Scrut’s risk management module provides the visibility required to stay safe from threats and effectively communicate the impact of risk on critical business activities. Let’s see how the platform helps in different steps involve in risk management.
- Risk identification: It is the first step in a risk management plan that involves analyzing IT assets, such as systems, software, networks, devices, vendors, and data.

Scrut’s risk management module simplifies the identification, evaluation, and reduction of IT and cyber risk by providing complete visibility into your risk posture.
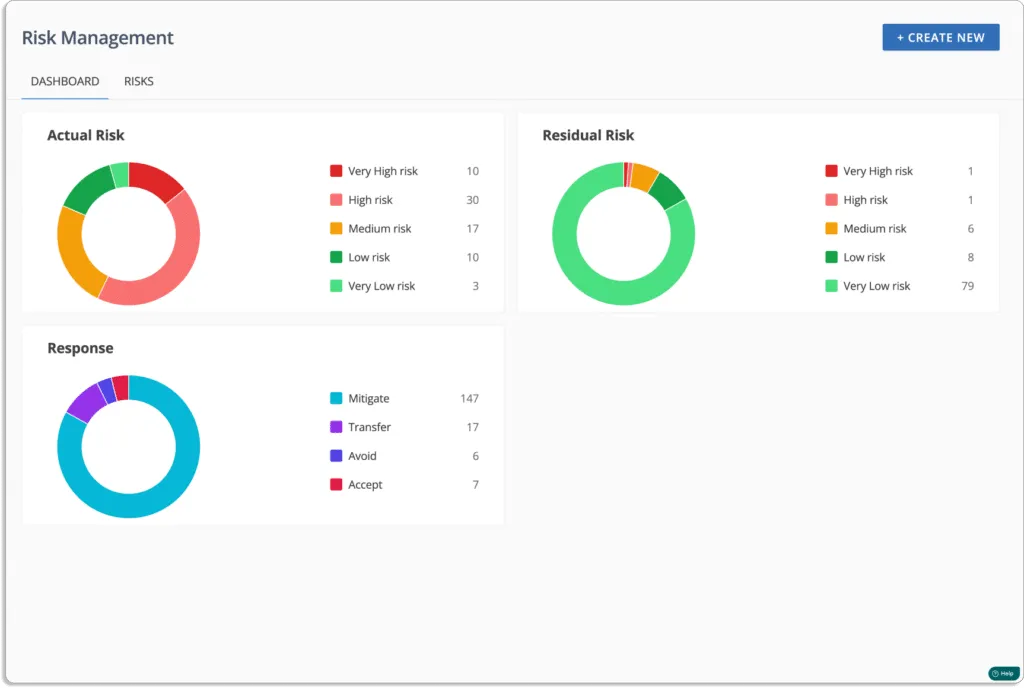
The platform automatically detects risks by scanning your ecosystem across infrastructure, applications, vendors, employees, etc.
Users can use Scrut’s pre-mapped risk library to create a risk register quickly.
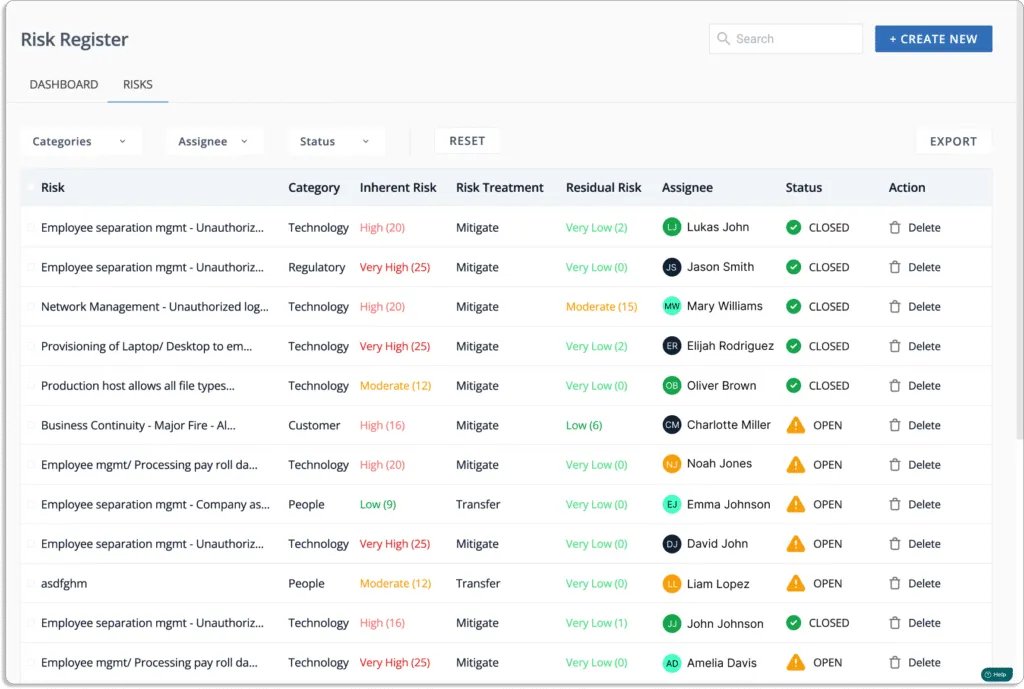
You can create your custom risk categories with the Scrut platform. While creating, you can also assign an owner.
- Risk assessment: It is crucial for a company’s risk management plan that helps startups identify and prioritize potential risks, allowing them to focus on the most important ones.
Scrut’s risk scoring system evaluates risks based on their likelihood and potential impact, as depicted in the provided screenshot.

- Likelihood = 5, which is a very high
- Impact = 4, which is high
- Inherent Risk = 20, which is high (Risk = Likelihood * Impact)
The final score lies between 0 – 25.
- 0 – 5 – Very Low
- 6 – 10 – Low
- 11 – 15 – Moderate
- 16 – 20 – High
- 21 – 25 – Very High
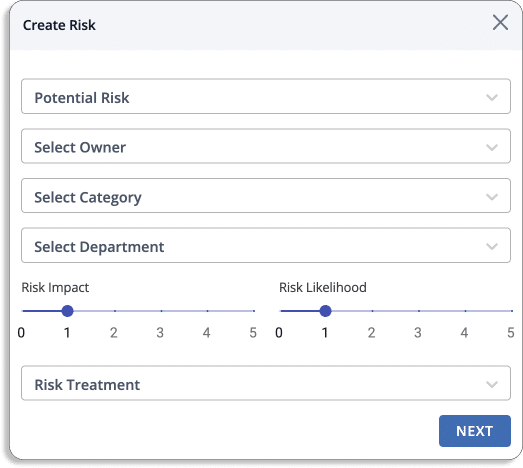
- Risk Treatment: The next step after a risk assessment is to work on the risk, known as risk treatment.
For each risk, the Scrut’s risk management module provides the following treatment options:
- Accept: To acknowledge the risk while determining that any actions to avoid or mitigate the risk would be too costly or time-consuming.
- Transfer: To take action by transferring the risk to another entity.
- Mitigate: To take action to reduce the potential impact of risk by implementing mitigating controls.
- Avoid: To take action that will completely eliminate the risk.
With Scrut, you can also assign risks to team members, as shown in the screenshot below.
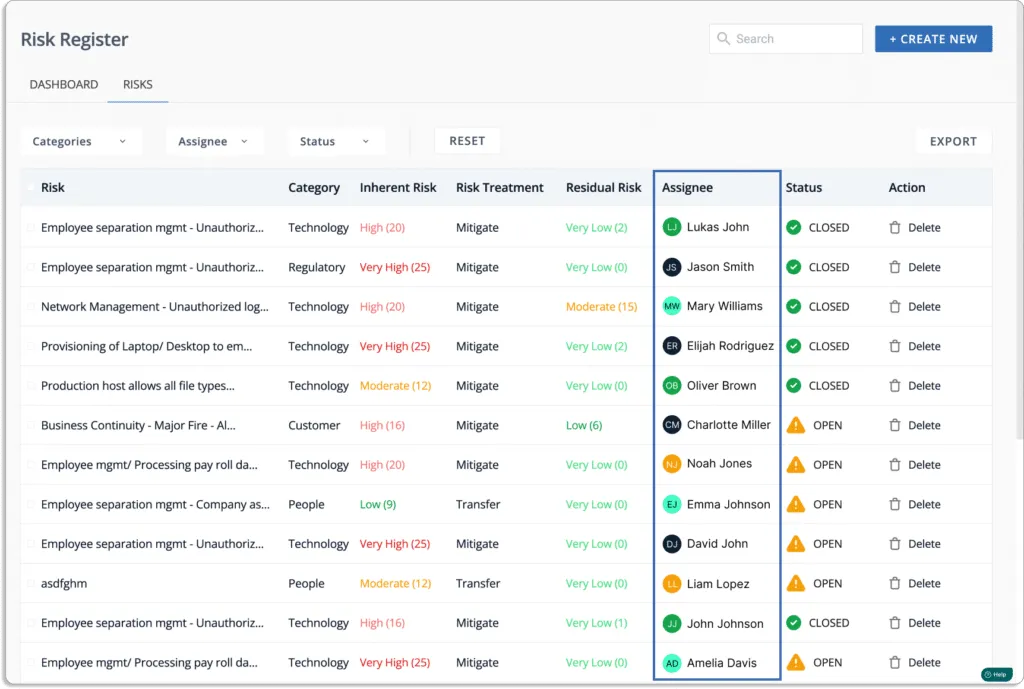
You can refer to this article for more details on how Scrut helps with risk management.
2. Employee risk management
Scrut streamlines employee information security by providing an automated solution. The platform includes a pre-built, expert-vetted 30-minute information security course that provides employees with a thorough understanding of potential risks.
Scrut makes employee security training easier by centralizing policies and procedures in one place. The tool’s dashboard makes tracking training completion and employee acknowledgment simple.

The awareness training aims to educate users and employees about their role in preventing data breaches. Scrut uses quizzes and tests to evaluavte employees’ awareness about different cybersecurity practices. It enables you to grade employee performance using configurable minimum score thresholds and ensures that your employees are prepared to deal with threats.
3. Vendor risk management
Scrut provides a streamlined and intelligent vendor risk assessment solution that provides a comprehensive way to evaluate, monitor, and manage vendor risks all in one place. The tool provides a clear picture of how vendors are performing and whether their security posture aligns with your organization’s needs.


- You can automate vendor audit programs and evaluate vendor risk profiles using Scrut’s vendor risk management module.
- It makes vendor management simple by developing customized programs for vendors of all risk levels.
- You can easily compare vendor responses and make informed decisions to reduce vendor risks with an intuitive dashboard.
- You can use the platform to generate vendor security reports for auditors and demonstrate compliance.
Now, let’s take a closer look at how Scrut’s vendor risk management module works.

- Upload a security questionnaire: Scrut’s vendor risk management module allows you to upload a security questionnaire or use pre-built templates, eliminating the need for traditional vendor security evaluation methods.
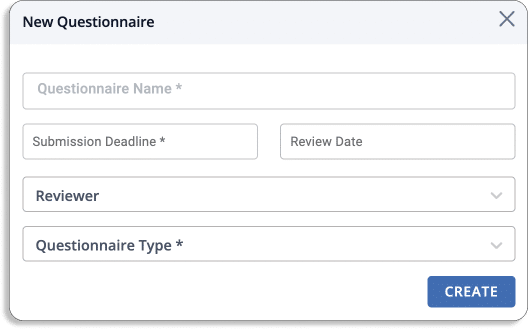
- Invite vendors: Vendors can be invited to complete security audit questionnaires on the platform, allowing vendor comparison to select the one with the lowest risk or develop a risk management strategy based on vendor risk categories.

- Examine your information security posture: Scrut’s vendor risk management module enables rapid assessment of vendor compliance by providing a centralized dashboard to send security surveys and identify deviations.
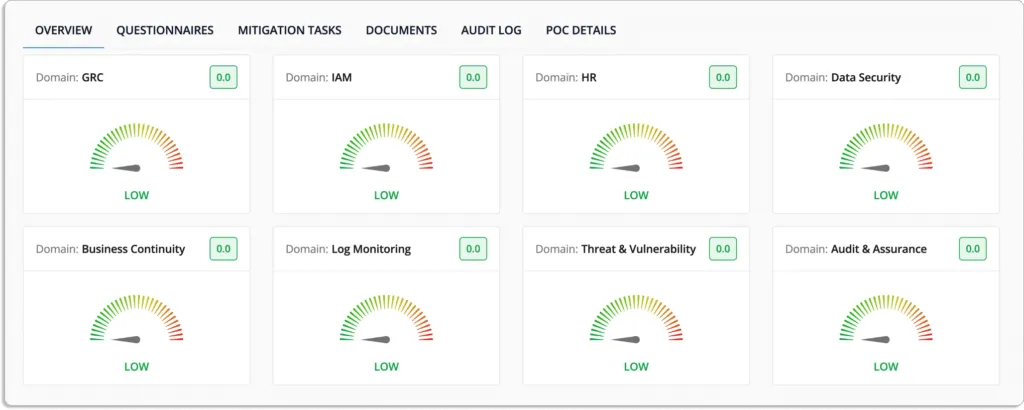
4. Cloud risk management
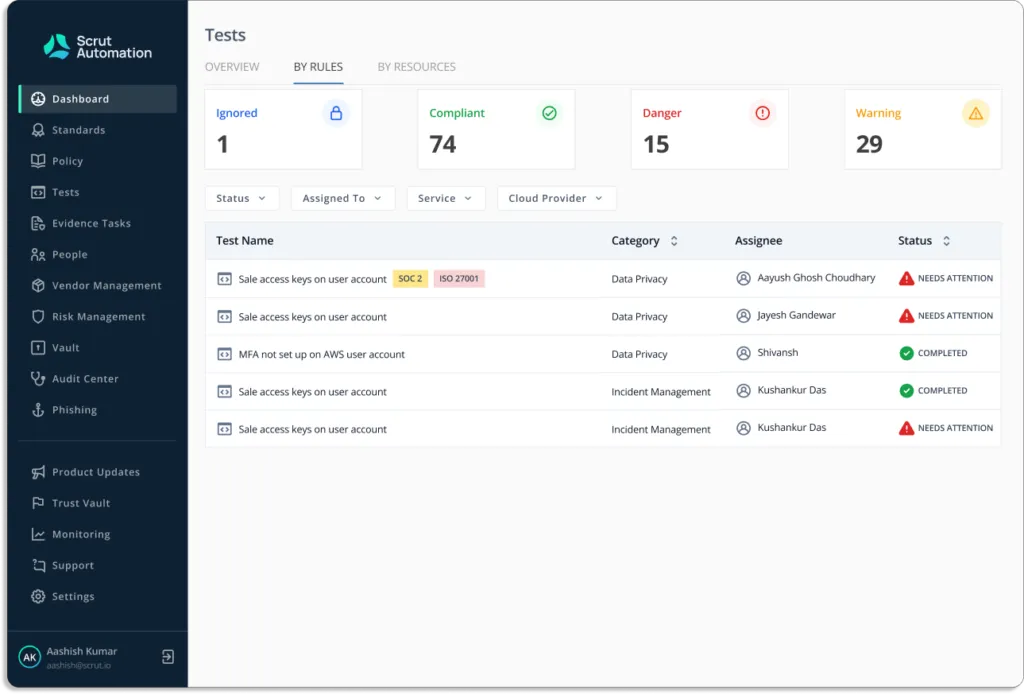
Scrut’s cloud security module goes beyond traditional cloud security posture management tools by scanning and monitoring misconfigurations in your public cloud accounts, including AWS, Azure, and Google Cloud Platform.
- Continuously check for cloud controls: Scrut’s cloud security module maintains a strong information security posture by continuously monitoring your cloud configurations against over 200 cloud controls.
- Fix cloud misconfigurations: Scrut’s cloud security module ensures that your cloud infrastructure is always compliant. The platform sends alerts with specific instructions for correcting any misconfigurations.
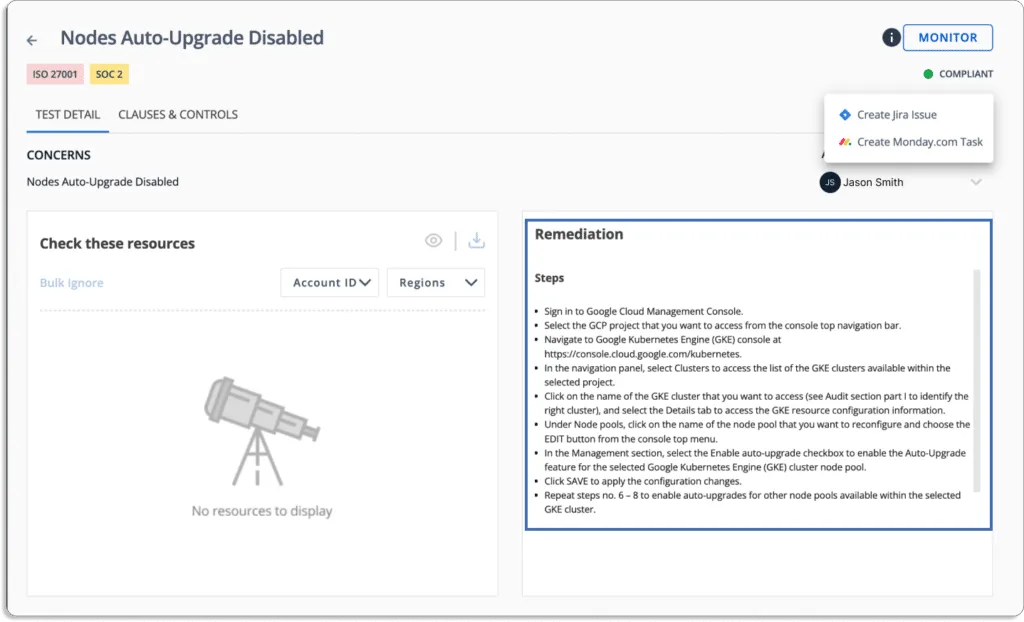
You can also assign tasks to team members to fix misconfigurations, as shown in the screenshot below.
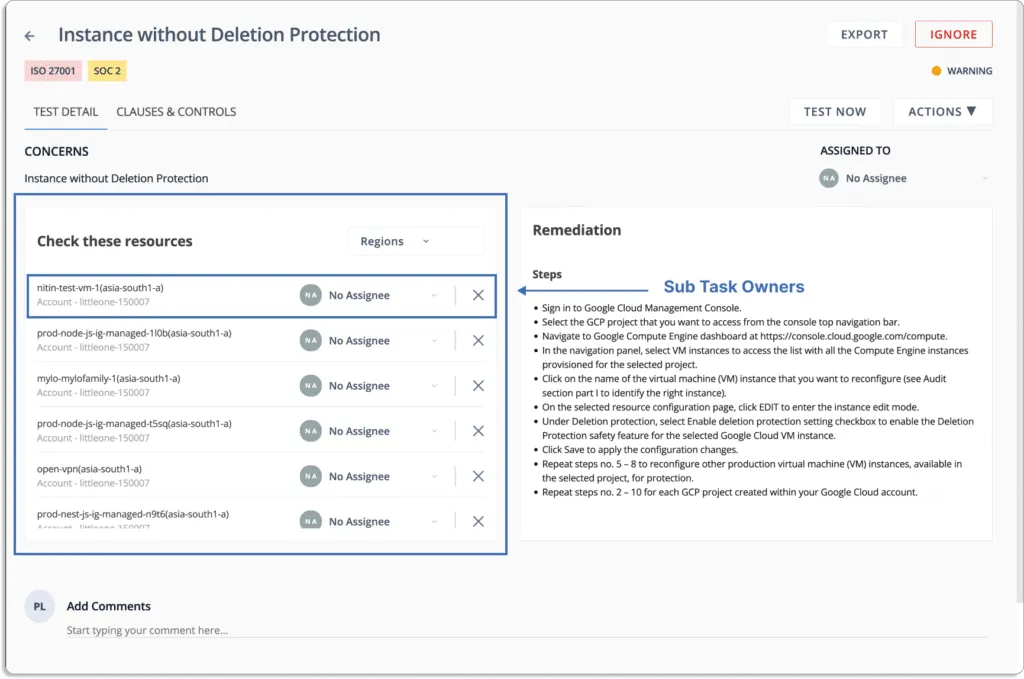
Scrut’s cloud security module stands out among other CSPM platforms by providing contextual and accurate alerts. Through internal research, we discovered that this is a key factor that customers appreciate about our platform. We have specifically designed Scrut’s cloud security module to act easily on these alerts. Unlike other CSPM platforms, Scrut does not overwhelm security teams with irrelevant alerts.
- Improve your cloud-native security: Scrut’s cloud security module protects all of your cloud-native deployments, including databases, containers, and serverless, by applying best-practice security policies consistently across your hybrid and multi-cloud infrastructure.
How Scrut Helps in Establishing Governance in Startups
With Scrut, you can increase customer trust by providing security evidence of compliance with multiple standards and win more business deals.
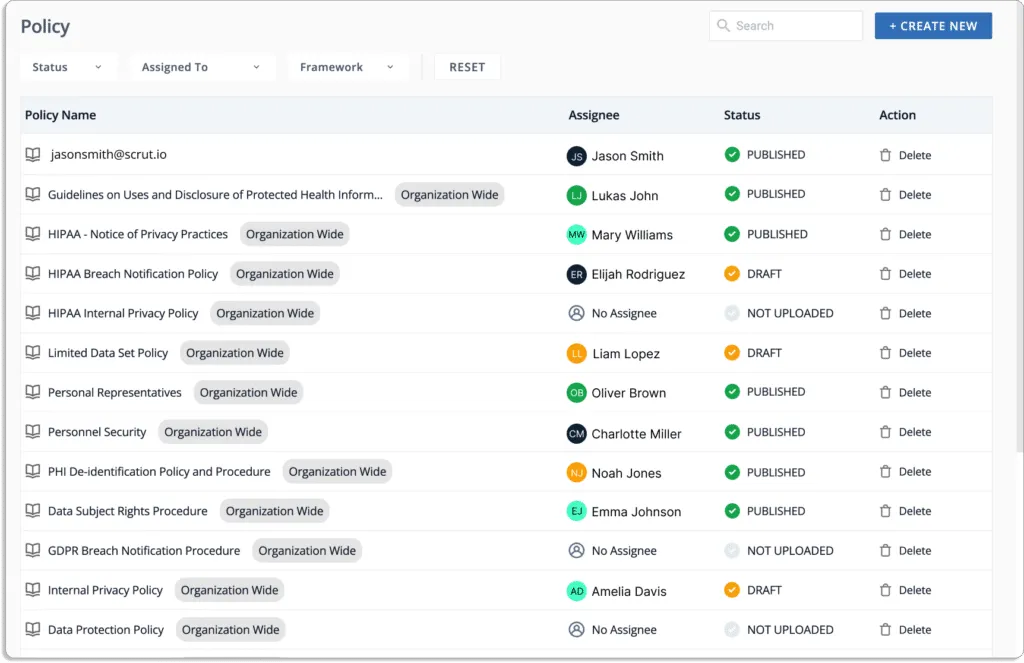
- Policy templates
Scrut provides you with pre-built policies that are reviewed by industry experts.
You can use the built-in inline editor to customize these policies.
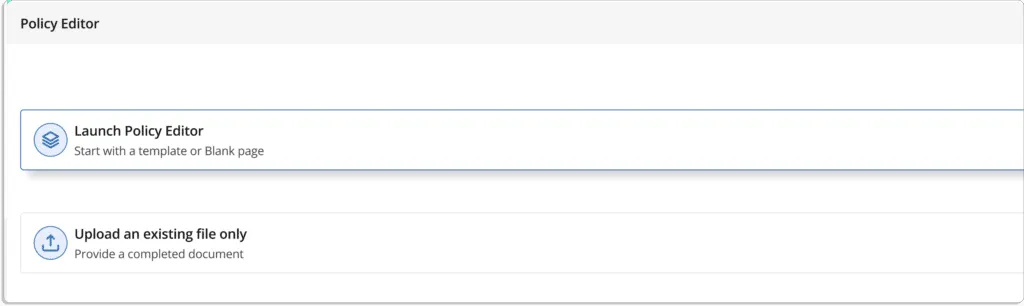
If needed, users can create a new policy by clicking on “Create New,”option as shown in the screenshot below.
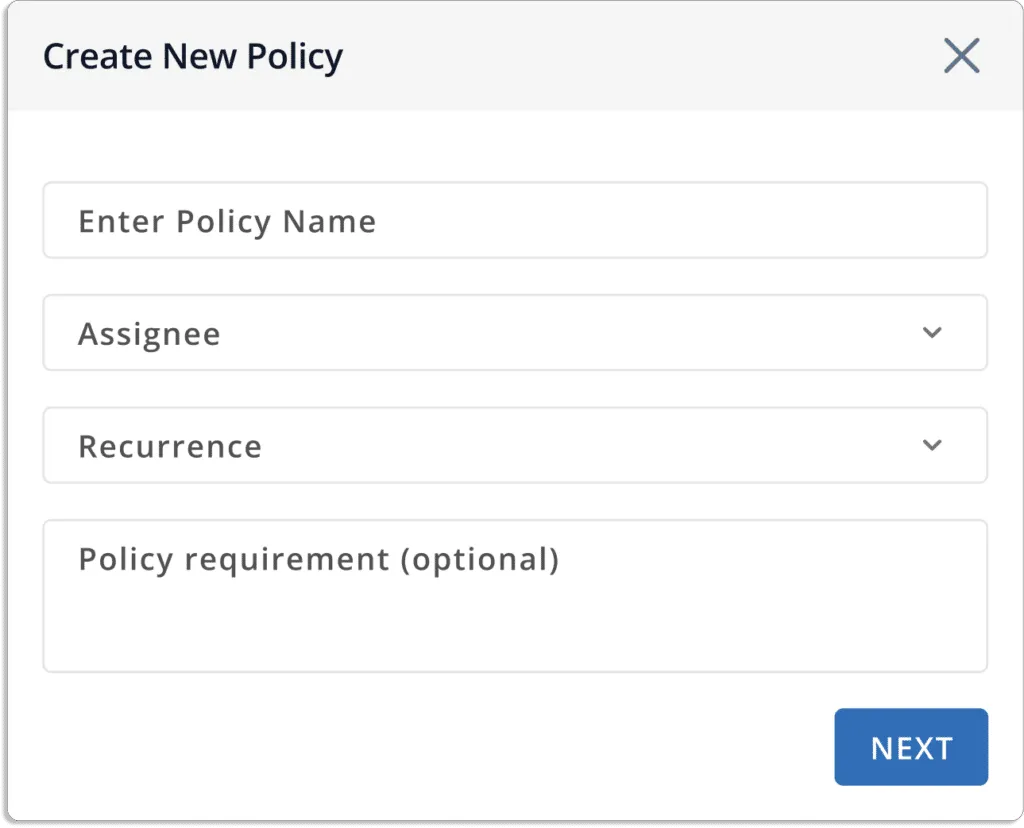
After that, a pop-up box will appear, as shown in the screenshot below. Fill in the appropriate fields and submit.
Lastly, a list of all the policies will be displayed on your screen.
You can use the policy library, which is mapped to frameworks such as SOC 2, ISO 27001, and others, as shown in the screenshot below.
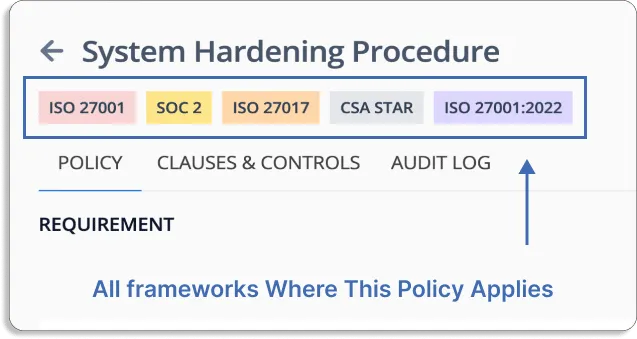
- Controls
You can design controls based on your risks and use pre-built control mapping to map them against your required compliance frameworks.
The Best Way to Build Trust with Your Enterprise Buyers – Trust Vault
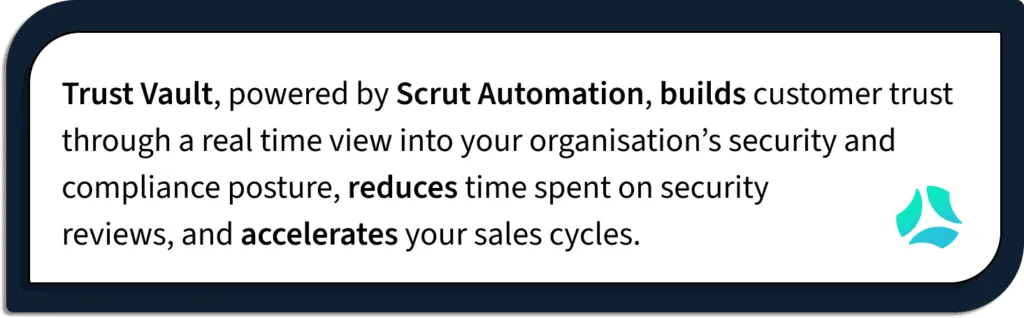
Scrut’s trust vault module allows you to stay one step ahead of the competition by building customer trust from day one. You can close enterprise deals faster by gaining potential customers’ trust and demonstrating a solid security posture with customized and easy-to-build auto-populated security pages.

The platform lets you see your security and compliance posture in real-time. It eliminates the hassle of fielding manual requests for security questions, reports, and certificates.

The platform boosts your enterprise sales by displaying all of your compliance certifications, attestations, and reports in one place.
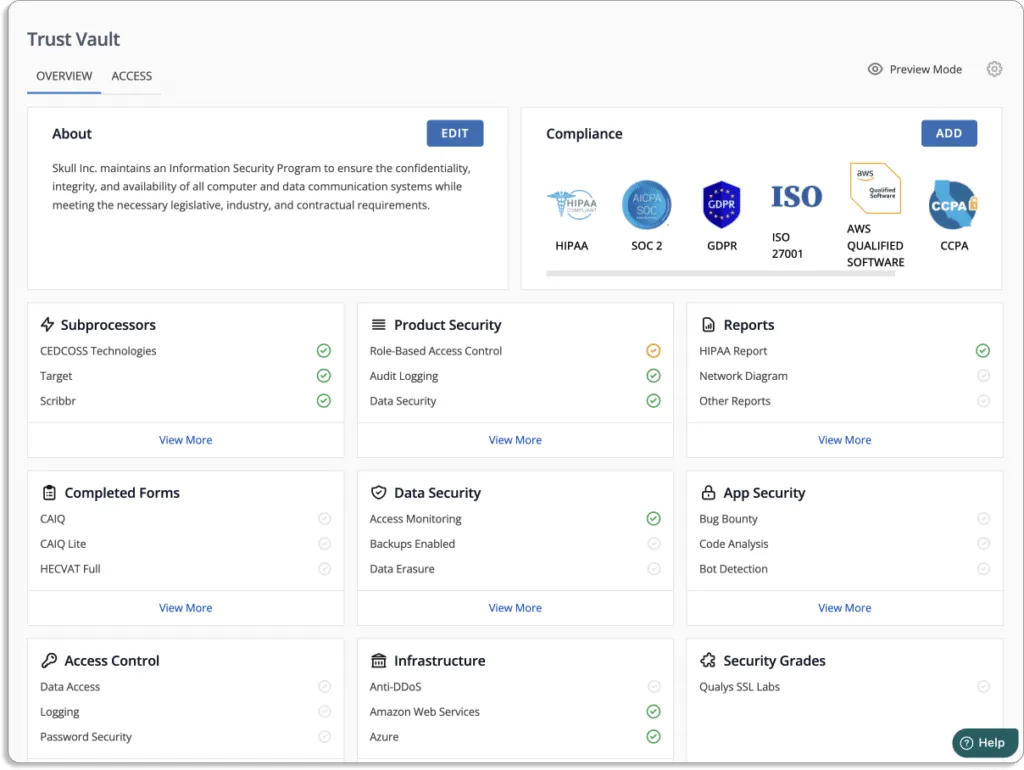
You can configure which controls to highlight and upload relevant documents, certificates, or other reports with Scrut’s trust vault module. It allows you to customize the trust vault with your logo, colors, favicon, and description to create and share a customizable branded security page to demonstrate your information security posture. You can publish it on your domain and include it on your website.
Scrut allows you to protect your documents with NDA-backed gated access.
Any organization requires its sub-processors to satisfy equivalent obligations as them. Scrut automatically pulls your sub-processors from the underlying smartGRC tool by eliminating the need to update sub-processors to ensure privacy compliance manually.
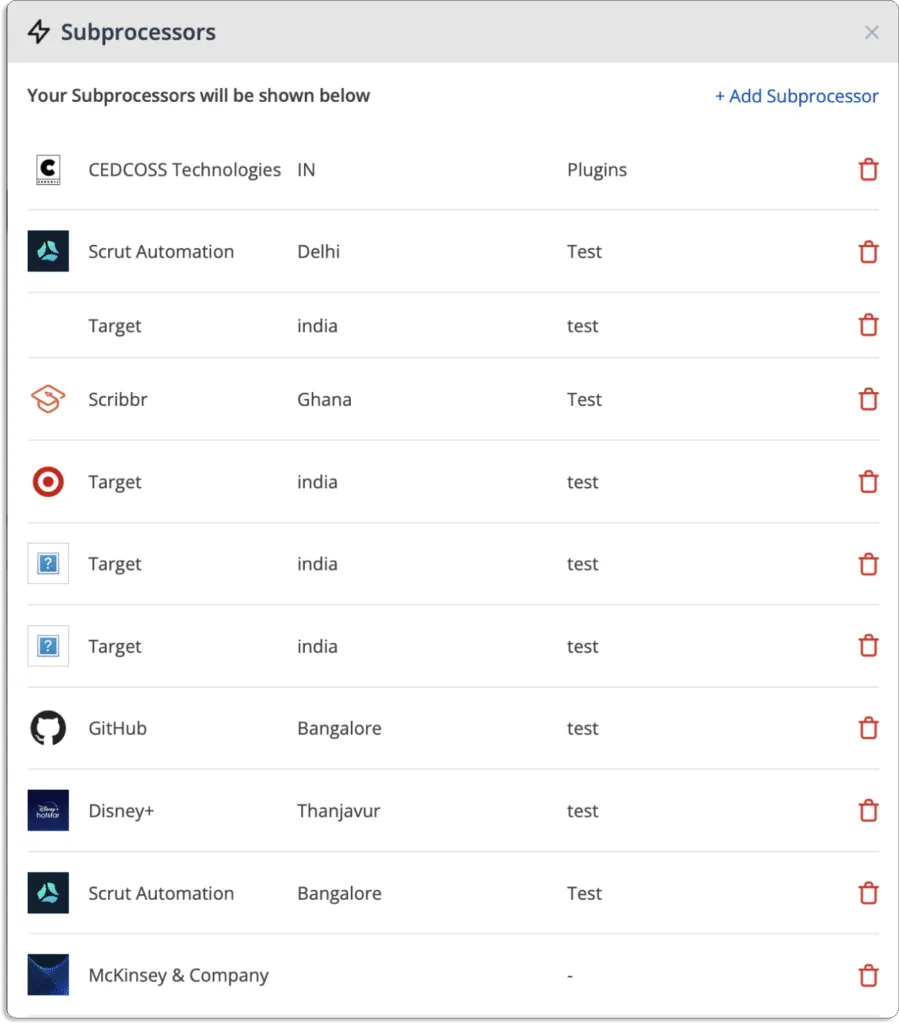
You can demonstrate real-time compliance transparency to your clients by using the auto-populated Trust Vault page, which is updated to show the most recent updates across controls, compliances, and sub-processors.
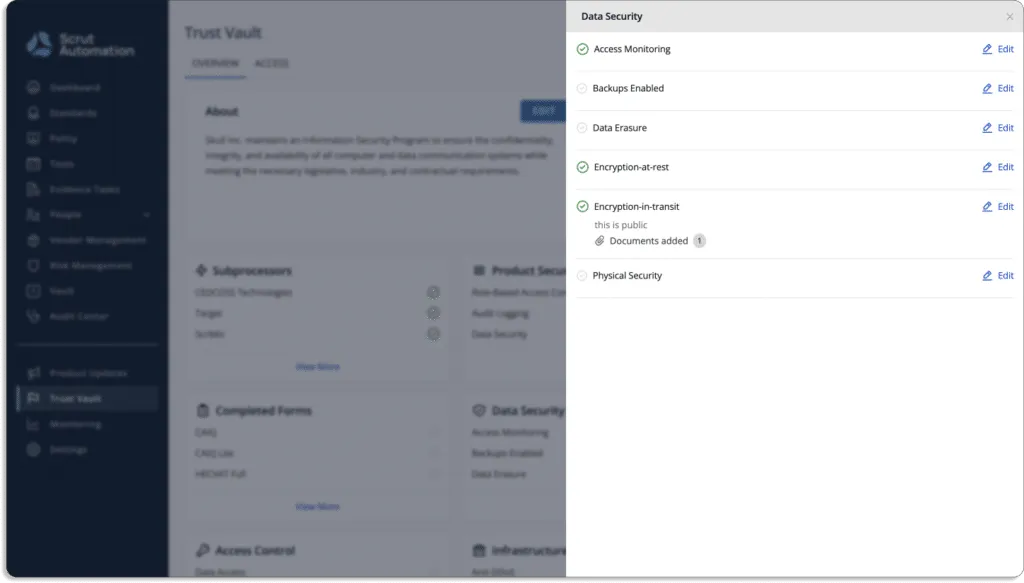
The Scrut product security page provides real-time security insights, as shown in the screenshot below.
To learn more about how to create an enterprise-friendly risk posture with Scrut, schedule a demo.





































