In the modern digital world, where personal data is increasingly the currency of the online world, ensuring privacy has become a paramount concern.
Privacy frameworks serve as navigational tools, helping individuals and organizations traverse the complex terrain of data protection.
In this blog, we will embark on a journey to understand and compare various privacy frameworks, deciphering their roles in safeguarding personal information.
Understanding data privacy frameworks
Privacy frameworks are comprehensive systems of guidelines, regulations, and practices designed to safeguard personal data and uphold individuals’ rights. They provide structure to data handling, storage, and processing, ensuring transparency and accountability. By adhering to a privacy framework, organizations establish a consistent approach to protecting sensitive information and building trust among stakeholders and consumers.
Data privacy vs. data security: clarifying the difference
Data privacy and data security are two closely related yet distinct concepts.
Data privacy involves controlling access to personal information and determining how it’s collected, used, and shared.
On the other hand, data security focuses on protecting data from unauthorized access, breaches, and cyber threats. Privacy frameworks not only address the lawful use of data but also the technical measures required to keep that data secure.
Data security aims to protect organizational data from unauthorized access, use, disclosure, modification, disruption, or destruction. It can be achieved by implementing technical and non-technical measures such as encryption and access control.
On the other hand, data privacy underlies the philosophy that consumers are the owners of the information about them. Privacy addresses an individual’s concerns about misuse of data against their consent.

How an organization is supposed to collect, use, and disclose an individual’s personal information is guided by the particular data privacy framework.
Consumers are concerned about safeguarding their details and have the right to know how companies share their data with third-party companies. However, consumers are not equipped with the proper knowledge and resources to enforce the correct use of their data by organizations. Hence, legal standards like GDPR, CCPA, and HIPAA exist.
How to choose the right data privacy frameworks
Selecting the right privacy framework requires a thorough assessment of your organization’s industry, geographic scope, and data handling requirements.
- Begin by identifying applicable regulations based on the type of data you process and the locations of your customers.
- Engage a cross-functional team—including cybersecurity, legal, compliance, and business experts—to evaluate existing frameworks within your organization and determine whether they can serve as a foundation.
- Consider privacy-specific frameworks like GDPR, CCPA, and HIPAA, as well as security-related frameworks such as NIST CSF and ISO 27001, which support compliance efforts.
For example:
- Healthcare organizations handling patient data must comply with HIPAA.
- Companies collecting data from California residents need to adhere to CCPA.
- Businesses processing EU, EEA, or UK personal data must follow GDPR.
- Organizations working with the U.S. federal government may require FedRAMP compliance.
By carefully evaluating your operational needs and compliance obligations, you can choose a privacy framework that safeguards sensitive data while aligning with business objectives.

Exploring key data privacy frameworks:
1. GDPR (General Data Protection Regulation)
The GDPR (General Data Protection Regulation), is a comprehensive data protection and privacy regulation introduced in 2018. It applies to organizations processing personal data, offering goods/services to EU, UK, or EEA residents, or monitoring their behavior.
It affects both data controllers and processors, aiming to protect individuals (data subjects) and their rights. GDPR covers sensitive data and has global reach due to its extraterritorial scope. It’s relevant to the public/private sectors and requires compliance to avoid penalties. It grants individuals rights such as data access, rectification, and erasure.
Organizations must ensure lawful processing, obtain explicit consent, and report data breaches promptly or face substantial penalties.
The purpose of the GDPR is to safeguard consumers’ personal information and prevent its misuse in any manner.
It is not only applicable to European companies; any organization that stores EU,UK, and EEA residents’ personal data must maintain this standard.
Maintaining the proper controls to safeguard consumers’ data is entirely the responsibility of organizations.
GDPR defines reasons for collecting personal data, and under that:
- Data collected must be for a specific and legitimate purpose and should not be used for any other purpose
- Organizations should collect data that must be limited to what is necessary for the purpose
In instances where an organization lapses in upholding GDPR compliance, substantial fines are levied against them. These penalties can be applied in situations where a data breach occurs due to deliberate actions or oversight.
Factors taken into account for penalty determination include the gravity of the infringement, the length of the breach, the quantity of individuals whose data is compromised, and the extent of harm inflicted upon the affected users.
The penalties are categorized into two levels.
- Lower level: The fine is up to €10 million or 2% of global revenue from the previous year, whichever is higher.
- Upper-level: €20 million or 4% of global revenue from the previous year, whichever is higher.
Some hefty fines levied on well-known companies are:
- Amazon: A €793 million fine was levied on Amazon.com Inc. when an infringement concerning Amazon’s advertising targeting system was identified, in which customer data was processed without proper consent.
- Instagram: €405 million was levied for GDPR violations by Ireland’s Data Protection Commission for how it handles children’s data.
2. HIPAA (Health Insurance Portability and Accountability Act)
The Health Insurance Portability and Accountability Act (HIPAA) is a legal standard or law that secures protected patient health information (PHI). It provides consumers with trust about the safeguarding of their medical data with the respective authorities without any disclosure to third parties.
HIPAA addresses the use and disclosure of an individual’s health information by entities subject to the privacy rule. These individuals and organizations are termed covered entities.
Covered entities include:
- health care insurers (health insurance companies, company health plans, and government plans)
- health care providers (doctors, clinics, psychologists, dentists, chiropractors, nursing homes, and pharmacies)
- health care clearinghouses (middlemen between healthcare providers and insurers)
- business associates (people or organizations that work on behalf of one of the entities above)

To comply with HIPAA, all covered entities must ensure the confidentiality, integrity, and availability of all e-PHI, detect and safeguard against anticipated threats, and protect against disclosures that are not allowed.

If your organization fails to comply with HIPAA, a penalty can be imposed.
Penalties for civil violations
- Tier 1: When the entity is unaware of violation: a fine of $100 to $5000 per violation, with an annual maximum of $25,000 for repeated violations.
- Tier 2: When the entity is aware of a violation but could not avoid it with reasonable care: a fine of $1000 to $50000 per violation, with an annual maximum of $100,000 for repeated violations.
- Tier 3: If the violation is a result of willful neglect and an attempt is made to correct it: a fine of $10000 to $50000, with an annual maximum of $250,000 for repeated violations.
- Tier 4: If the violation is a result of willful neglect and no attempt is made to correct it: $50000 per violation, with a maximum of $1.5 million annually
3. CCPA (California Consumer Privacy Act)
The CCPA is a state-wide data privacy law that regulates how businesses worldwide are allowed to handle the personal information (PI) of California residents. The CCPA gives consumers more control over the data that companies collect.

Under this law, sensitive data includes people’s browsing history, geolocation data, and a visitor’s interactions with a website or application. It covers employees’ as well as consumers’ data.
According to this compliance standard, companies should give consumers the option to choose not to have their data shared with third parties. It allows California customers to demand to see the information a company has saved and the list of third-party companies with which the data is shared. It also allows consumers to sue other companies if the privacy guidelines are violated.
Organizations need to be CCPA compliant to do business in this region. It promotes, protects, and enforces the rights of consumers. Suppose you are CCPA compliant; you gain the consumers’ trust that their personal data is safe with the company.

The CCPA allows consumers to know and apply the following rights to maintain their data security.
Right to know
Consumers have the right to access the data companies have stored and used for their needs, such as data sharing. For this, they need to formally ask for access to what data is stored in the companies and how they use it. They can ask about data stored, shared, disseminated, and sold to third parties.
Right to delete
Consumers have the right to have their personal data stored by companies deleted if it can become a security issue for them. They can ask the companies about the procedures and follow them. Consumers have to do this through a formal application.
It gives the users the authority to erase their data from companies, which means withdrawing consent; thus, companies won’t be able to use, manipulate, or sell this data to third-party companies.
Right to opt-out
Companies collect personal data and sell it to third parties. So, users can withdraw their consent from the user agreement and opt out of the company-stored data not being used for selling and other issues as it can hamper their security. You have the right to opt out of such a situation without much struggle.
Non-Discrimination Entitlement
The CCPA ensures that consumers are protected against any form of retaliation by companies when they exercise their rights to access information, request deletion of data, or opt-out of data usage. This empowers consumers to confidently inquire about their rights and utilize them without encountering any obstacles.
In cases of CCPA violations, consumers retain the right to file complaints and seek reparations for the harm caused. The compensation mandated ranges from $100 to $750 for each consumer incident, or the actual amount of damages suffered—whichever is of greater value.
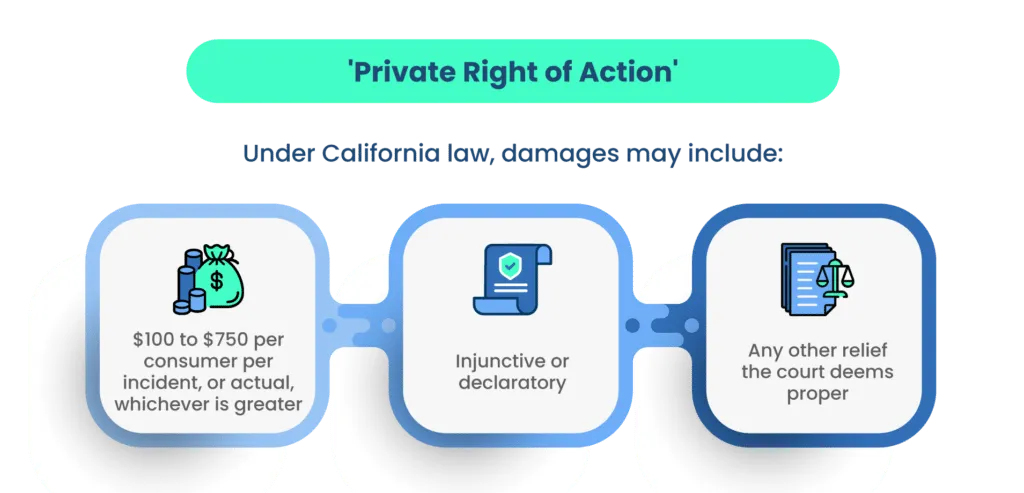
Once a violation is observed, the organization has 30 days to comply with CCPA. If they fail to comply within the stipulated time, a civil penalty of up to $2500 per violation or $7500 for each intentional violation will be levied.
4. Singapore PDPA (The Personal Data Protection Act)
The Personal Data Protection Act (PDPA) sets standards for the protection of personal data in Singapore. It comprises many requirements governing the collection, use, disclosure, and care of personal data in Singapore.
The purpose of this act is to govern the collection, use, and disclosure of personal data by organizations in such a way that both the right of individuals to protect their data and the need of the organizations to collect, use, and disclose personal data is maintained.
PDPA ensures that any organization that regularly collects data keeps track of the following things:
- What personal data is being collected, and what is the purpose of collecting it
- Who is collecting the personal data, and where it is being stored
- To whom the information about personal data is disclosed
Under PDPA, the following obligations occur: accountability, notification, consent, purpose limitation, accuracy, protection, retention limitation, transfer limitation, access and correction, data breach notification, and data portability.
It provides a regime to safeguard personal data from misuse and to maintain individuals’ trust in organizations to manage data. It strengthens the organization by regulating the flow of personal data among businesses.
If your organization is found to be non-PDPA compliant, then authorities can impose a financial penalty of up to $1 million. Also, you have to stop collecting or disclosing personal data and destroy previous data collected without consent.
- Spize was fined $20,000 for 100 customers’ data leaks.
- Karaoke Bar K Box was fined $50,000 for 3,17,000 customers’ data leaks.
5. HITRUST (Health Information Trust Alliance) CSF
HITRUST CSF offers a versatile and streamlined approach to achieving regulatory compliance and managing risks effectively. The acronym HITRUST stands for Health Information Trust Alliance, an organization that introduced a cybersecurity standard aimed at aiding entities in handling data, compliance, and information-related risks.
This comprehensive framework integrates requirements from a multitude of other established standards and regulations, such as GDPR, PCI DSS, HIPAA, and more. A significant advantage of adhering to the HITRUST framework is its readiness to encompass a wide array of privacy frameworks.
For entities involved in the creation, access, storage, or exchange of personal health information, HITRUST CSF certification becomes mandatory. This certification serves as a crucial marker of compliance.
HITRUST CSF certification aids organizations in mitigating risks through enhanced information security measures, enabling the establishment of robust frameworks for safeguarding information.
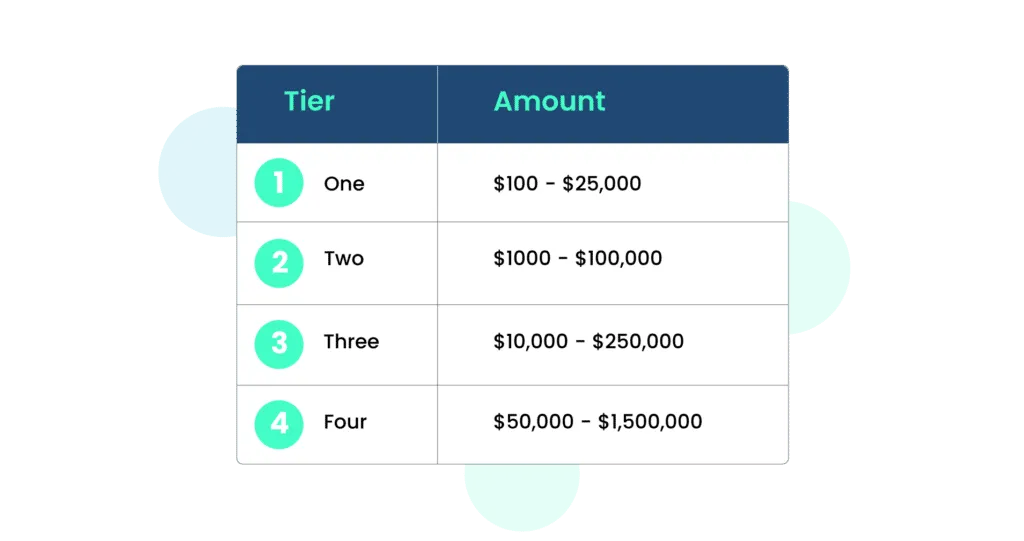
Failure to achieve HITRUST compliance may lead to the imposition of one of four potential penalties:
- Tier One: Fines ranging from $100 to $25,000 per infraction. This amount can be revised within a 30-day window if the organization was unaware of the breach and responded promptly once it was identified.
- Tier Two: Fines varying from $1,000 to $100,000. When the organization was oblivious to the breach and failed to rectify it promptly, fines can be levied for each violation.
- Tier Three: Penalties spanning from $10,000 to $250,000 for each transgression. In cases where an organization deliberately disregards proper security implementation and due diligence, a 30-day grace period is provided for protocol enhancement.
- Tier Four: Fines ranging between $50,000 and $1.5 million per violation. This applies when the organization possesses knowledge of the breach and deliberately neglects to address identified vulnerabilities within a 30-day interval.
Often misunderstood to be similar, HIPAA and HITRUST are quite different. HIPAA is legislation, and HITRUST is an organization. HITRUST Alliance is an independent organization that offers an organization flexible and comprehensive approach to HIPAA compliance and risk management.
6. IRAP
The Australian Signals Directorate (ASD) spearheads the Information Security Registered Assessors Program (IRAP), a pioneering effort designed to guarantee the provision of top-tier information and communication technology (ICT) security assessment services by various organizations to the government.
The IRAP certification extends the means for Australian government clients to affirm the adequacy of controls addressing the mandates outlined in the Australian Government Information Security Manual (ISM), a creation of the Australian Cyber Security Centre (ACSC).
With a core focus on the information and communication technology (ICT) infrastructure responsible for the storage, processing, and transmission of data, the IRAP endeavors to fortify the security of data held by Australian federal, state, and local government entities.
IRAP Assessors play a pivotal role in ensuring your organization attains the requisite physical certification. They meticulously evaluate security controls, enhancing your comprehension of your system’s architecture. Furthermore, they proffer recommendations for mitigation strategies, facilitating well-informed, risk-based decisions concerning the system’s suitability for its security imperatives.
7. FedRamp
The Federal Risk and Authorization Management Program (FedRamp) is a US federal security risk management program for the procurement of cloud products and services used by government agencies. It provides a standardized approach to security assessment, authorization, and continuous monitoring for cloud services and products.
FedRAMP ensures that cloud apps and services used by government agencies are safe. It enables efficient and cost-effective procurement of information systems and eliminates duplication of effort and risk management costs.
If your organization provides cloud computing services (including SaaS, PaaS, and IaaS) and wants to do business with US government agencies, you need to be FedRAMP certified.
If you are a software as a service (SaaS) provider, you need to keep your data on a FedRAMP-compliant cloud service provider, and your software must also comply with the framework.
To be FedRamp compliant, you need access control, awareness and training, audit and accountability, security assessment and authorization, configuration management, contingency planning, identification and authentication, and incident response.
US federal agencies require FedRAMP because it increases consistency with similar standards like the National Institute of Standards and Technology (NIST) and the Federal Information Security Management Act (FISMA). Together, these frameworks collectively contribute to maintaining transparency in the relationships between cloud providers and the US government.
8. ISO 27701
ISO/IEC 27701 stands for International Organization for Standardization/International Electrotechnical Commission 27701.
It is a privacy extension to the ISO/IEC 27001 and 27002 standards, providing guidelines and requirements for establishing, implementing, maintaining, and continually improving a Privacy Information Management System (PIMS).
This standard focuses on helping organizations manage personal data privacy and meet the requirements of various privacy regulations.
Furthermore, it outlines requirements for establishing, implementing, maintaining, and continually improving a privacy-specific information security management system.
According to Dr. Andreas Wolf, Chair of the ISO/IEC technical committee that developed the standard, ISO 27701 is designed to help businesses not only meet the legal requirements they are subject to, but also demonstrate their commitment to the social responsibilities that come with collecting and processing user data.
Please be aware that ISO 27701 does not have an independent certification process. To attain 27701 certification, organizations must first hold an existing ISO 27001 certification. Alternatively, there is an option to implement ISO 27001 and ISO 27701 concurrently, streamlining the auditing process.
The presence of ISO 27701 signifies an advanced level of data protection for consumers. The combined effect of both certifications instills assurance among stakeholders within your organization, as it showcases the establishment of a comprehensive data privacy management system.
ISO 27701 requires that companies regularly produce documentation about personal data handling against breaches. Transparency about a company’s data governance assures consumers, employees, investors, clients, and the government that you are serious about protecting the privacy of your associates.
9. ISO 27018
ISO 27018 focuses on the protection of personal data on the public cloud. It is based on ISO/IEC security standard 27002 and guides the implementation of public cloud personally identifiable information (PII). It also sets additional controls to address public cloud PII protection requirements not managed by the existing ISO/IEC 27002 control set.
Note that, according to the latest changes, ISO 27018 is a document, not a standard.
Benefits
ISO 27018 compliance is a competitive advantage for both cloud service providers and their customers.
- ISO 27018 ensures confidence to customers of cloud service providers that their data is safe and won’t be used for any purposes for which they haven’t provided consent.
- It ensures organizations’ local and international privacy and data security regulations and mitigates risks associated with PII through the cloud.
- It helps public cloud service providers comply with applicable obligations when acting as a PII processor.
- It assists the cloud service customer and the public cloud PII processor in entering a contractual agreement.
- It provides a cloud service mechanism for exercising audit and compliance rights and responsibilities.
How Scrut helps you get compliant faster with privacy frameworks?
Scrut smartGRC delivers a faster, easier, and smarter path to security and privacy compliance frameworks, eliminating tedious manual processes and keeping you up-to-date on the progress and effectiveness of your GRC programs.
With seamless integrations across your application landscape, you gain a unified, real-time view of risk and compliance, providing the contextual insight needed to make smart, strategic decisions that keep your organization secure and earn the trust of your customers, partners, and employees.
Scrut allows you to track all compliance activities in one place. Since there is a good overlap between many frameworks, you can work on multiple security and compliance frameworks simultaneously.
Frequently Asked Questions
1. What exactly are privacy frameworks, and why are they important?
Privacy frameworks are structured sets of guidelines, regulations, and practices designed to ensure the protection of personal data and uphold individuals’ rights. They play a crucial role in guiding organizations on how to handle, store, and process sensitive information while maintaining transparency and accountability. Privacy frameworks help address the growing concerns surrounding data privacy and security.
2. How do data privacy and data security differ within the context of privacy frameworks?
Data privacy involves controlling the collection, use, and sharing of personal information, ensuring individuals’ rights are respected. Data security, on the other hand, pertains to safeguarding data from unauthorized access, breaches, and cyber threats. While data privacy focuses on the lawful handling of data, data security addresses the technical measures required to keep that data safe.
3. How do I choose the right privacy framework for my organization?
Choosing the appropriate privacy framework requires a thoughtful evaluation of various factors. Consider the industry you operate in, as different frameworks cater to specific sectors. Assess the geographic scope of your operations, as privacy regulations can vary by region. Evaluate the type of data you handle and the rights of individuals involved. Align these factors with the requirements of available frameworks to make an informed decision.
4. What are some prominent privacy frameworks and their key features?
Various significant privacy frameworks cater to specific needs:The General Data Protection Regulation is a European Union regulation on Information privacy in the European Union and the European Economic Area; HIPAA sets health data protection standards; CCPA empowers Californian residents with data control; Singapore’s PDPA oversees data use and consent; ISO 27701 integrates privacy into ISO 27001, fostering a holistic approach.
5. What challenges do organizations commonly face when implementing privacy frameworks, and how can they overcome them?
Implementing privacy frameworks can present challenges such as complex compliance requirements, potential data breaches, and the need for transparent communication with individuals. Organizations can mitigate these challenges by investing in robust cybersecurity measures, conducting regular privacy audits, providing comprehensive employee training, and maintaining open lines of communication with stakeholders.





































