Picture this: your organization is a fortress of data and operations, but lurking in the shadows are threats that could dismantle everything you’ve built. This is where the art of risk management steps in as the guardian of your digital kingdom, determining whether your defenses are robust or riddled with vulnerabilities.
But here’s the twist – the world of risk calculation isn’t a one-size-fits-all affair. It’s a vast landscape with various methods, each holding its unique power.
Choosing the right method is akin to selecting the perfect tool for the job. And that’s precisely what we’re here to uncover in this blog.
What are the different types of risk calculation methods?
Close your eyes for a moment and imagine wielding a sword to slay a dragon. Sounds heroic, right? But what if you needed a shield instead? That’s the essence of selecting the right risk calculation method.
An inappropriate choice can leave you ill-equipped to face the challenges ahead, leading to costly mistakes and missed opportunities. Brace yourselves; we’re about to delve deep into the art of choosing your digital armor.
There are three principal types of risk calculation methods, as shown below:

A. Qualitative risk assessment
Qualitative risk assessment is a method of evaluating risks that focuses on descriptive and subjective measures rather than precise quantitative data. It involves the assessment of risks based on their characteristics, attributes, and expert judgment rather than assigning specific numerical values to them. Qualitative risk assessment helps organizations gain a broad understanding of potential risks without relying on extensive data or complex calculations.
What are the different methods of qualitative risk assessment?
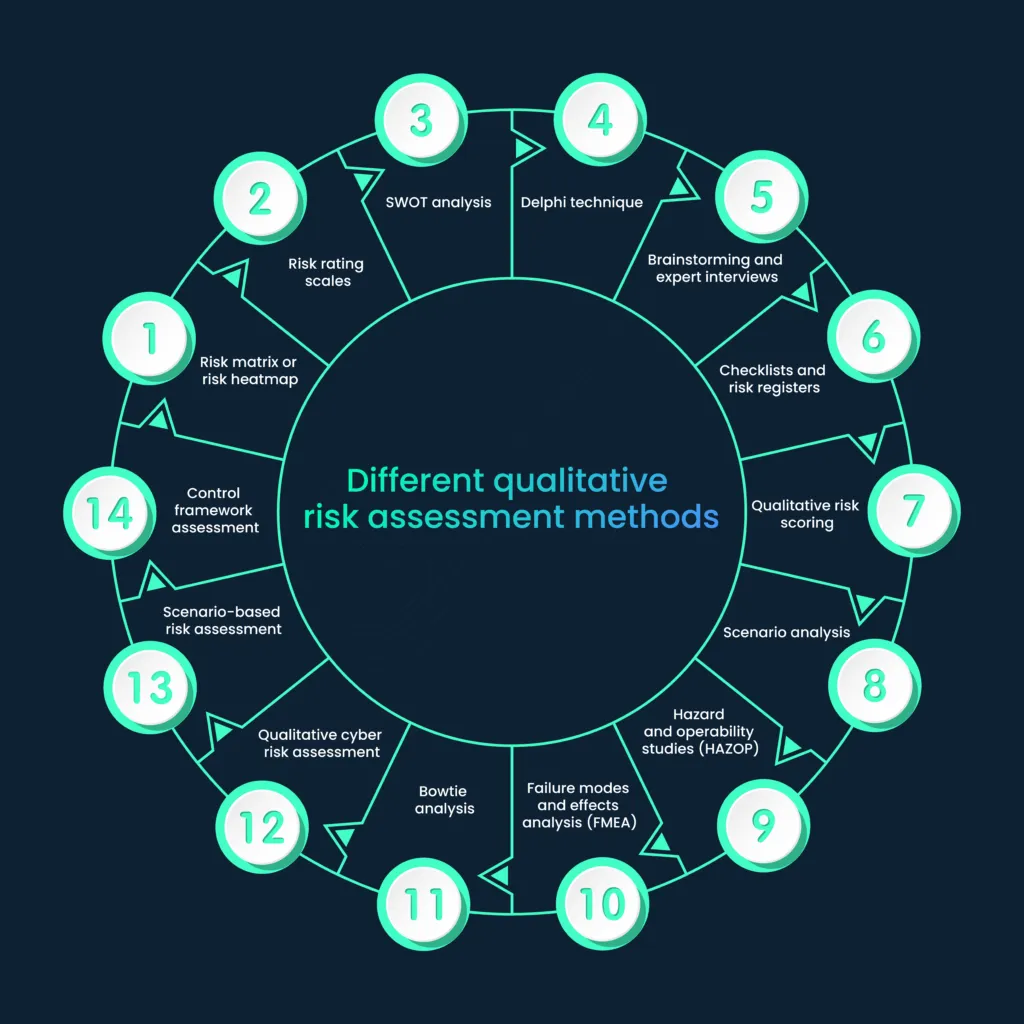
Qualitative risk assessment methods are diverse and rely on expert judgment and subjective evaluation rather than quantitative data. Here are some common types of qualitative risk assessment methods:
1. Risk matrix or risk heatmap:
A risk matrix categorizes risks based on their likelihood and impact using a color-coded matrix. It provides a visual representation of risks, making it easy to identify high-priority ones.
2. Risk rating scales:
Risk rating scales assign scores to risks based on predefined criteria, such as severity, likelihood, and potential consequences. These scales help prioritize risks without assigning numerical values.
3. SWOT analysis:
Strengths, Weaknesses, Opportunities, Threats (SWOT) analysis assesses an organization’s internal and external factors, including potential risks and opportunities.
4. Delphi technique:
The Delphi technique involves gathering expert opinions and conducting iterative rounds of questionnaires to achieve a consensus on risks and their potential impacts.
5. Brainstorming and expert interviews:
Brainstorming sessions and expert interviews facilitate open discussions among stakeholders to identify and qualitatively assess risks based on their knowledge and experience.
6. Checklists and risk registers:
Risk checklists and registers help organizations systematically list and categorize potential risks, enabling qualitative assessment and tracking.
7. Qualitative risk scoring:
This method assigns scores or rankings to risks based on subjective assessments of their likelihood and impact. These scores help prioritize risks.
8. Scenario analysis:
Scenario analysis explores potential future events or scenarios and assesses how they could impact an organization. It involves qualitative assessments of various outcomes.
9. Hazard and operability studies (HAZOP):
HAZOP is commonly used in process industries to identify and assess risks associated with operational processes, focusing on deviations from design intent.
10. Failure modes and effects analysis (FMEA):
While often used quantitatively, FMEA can also be applied qualitatively to identify potential failure modes, their causes, and their effects without assigning numerical values.
11. Bowtie analysis:
The Bowtie analysis is a visual representation of risks, their causes (threats), and the potential consequences. It helps organizations understand the relationship between causes and effects.
12. Qualitative cyber risk assessment:
In cybersecurity, qualitative methods may involve assessing threats, vulnerabilities, and controls based on expert judgment to identify potential risks.
13. Scenario-based risk assessment:
Organizations can use scenarios, such as “what-if” scenarios or hypothetical risk events, to qualitatively assess their impact and likelihood.
14. Control framework assessment:
This method involves evaluating the effectiveness of existing controls and their ability to mitigate risks, often through expert assessment.
These qualitative risk assessment methods offer organizations flexibility in assessing risks based on expert knowledge, discussions, and subjective judgment. They are particularly useful when quantitative data is limited or when a quick, qualitative overview of risks is needed.
Which are the situations where qualitative methods are most appropriate?

- Early-stage risk identification: Qualitative methods are useful in the initial stages of risk assessment when detailed data may be limited, helping organizations identify potential threats and vulnerabilities.
- Rapid risk assessment: In situations where quick decisions are needed, such as responding to emerging threats, qualitative methods can provide valuable insights without time-consuming data collection and analysis.
- Expertise-based insights: When organizations have access to subject matter experts who can provide valuable qualitative input, this approach can be effective in capturing their knowledge.
- Resource constraints: Smaller organizations or those with limited resources may find qualitative methods more practical due to lower costs and resource requirements.
- Non-numeric risk factors: Qualitative methods are suitable for risks that are difficult to quantify, such as reputational or geopolitical risks.
B. Quantitative risk assessment
Quantitative risk assessment is a systematic approach that uses numerical data and mathematical models to assess and quantify various aspects of risks. Unlike qualitative methods, which rely on descriptive and subjective measures, quantitative risk assessment assigns specific numerical values to risk factors, enabling organizations to calculate the likelihood and potential impact of risks more precisely. This method often involves statistical analysis, data-driven models, and probability calculations to arrive at quantitative risk metrics.
What are the different methods of quantitative risk assessment?
Quantitative risk assessment methods encompass various techniques and models used to analyze and quantify risks in numerical terms.
A simplified version of the risk score calculation method is:
Risk Score = Probability × Impact
Based on the above, other methods are developed. Here are some common types of quantitative methods:
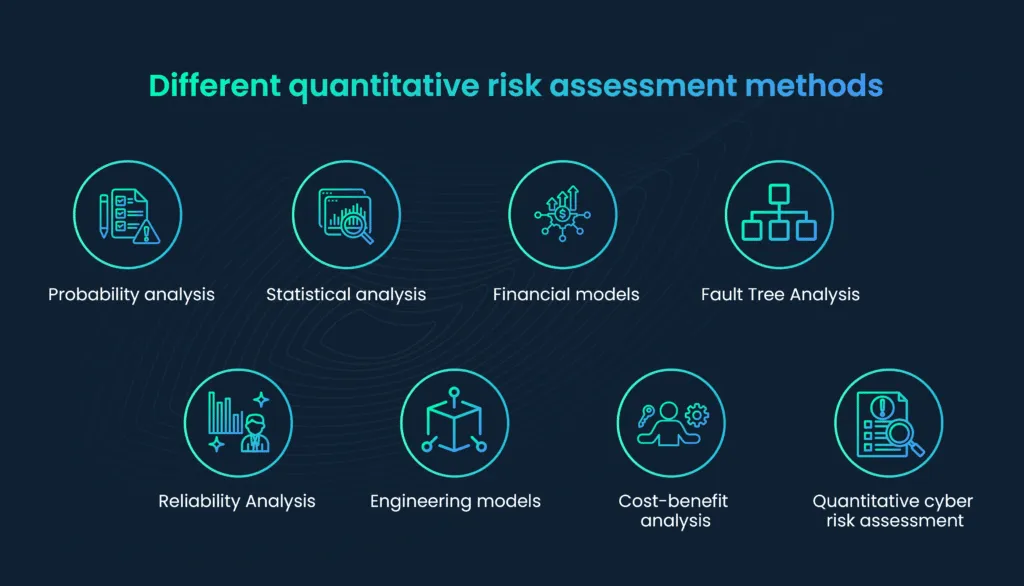
1. Probability analysis:
- Monte Carlo Simulation: This method involves using random sampling and probability distributions to model the behavior of a system or process over time, enabling the estimation of risk probabilities.
Risk calculation formula:

- Event Tree Analysis: Event trees are graphical representations of possible sequences of events and their associated probabilities, helping assess the likelihood of specific outcomes.
2. Statistical analysis:
- Regression analysis: Regression models can identify relationships between variables and predict outcomes, allowing organizations to assess the impact of various factors on risk.
- Bayesian analysis: Bayesian statistics use Bayes’ theorem to update the probability for a hypothesis as more evidence or information becomes available, making it valuable for updating risk assessments.
3. Financial models:
- Value at Risk (VaR): VaR measures the potential loss in value of a portfolio or investment over a specific time horizon, often used in financial risk assessment.
Risk calculation formula for VaR = Portfolio Value × (Z-score × Portfolio Standard Deviation)
Where: Portfolio Value is the total value of the investment. Z-score corresponds to the desired confidence level (e.g., 1.96 for 95% confidence). Portfolio Standard Deviation is the statistical measure of the investment’s risk.
- Cash Flow Analysis: This method evaluates the cash flows associated with different risk scenarios, helping organizations understand the financial impact of risks.
4. Fault Tree Analysis:
Fault tree analysis is a graphical method used to identify the combinations of events or failures that can lead to an undesired outcome. It quantifies the probability of specific events contributing to a risk.
5. Reliability Analysis:
- Reliability Block Diagrams (RBD): RBDs depict the reliability of a system’s components and their interconnections, enabling organizations to assess the reliability and risk of system failures.
- Failure Modes and Effects Analysis (FMEA): FMEA identifies potential failure modes in a system, rates their severity, occurrence, and detectability, and calculates a risk priority number (RPN) to prioritize mitigation efforts.
6. Engineering models:
- Finite Element Analysis (FEA): FEA is used to model and analyze the behavior of complex structures and systems, including assessing structural risks and vulnerabilities.
- Computational Fluid Dynamics (CFD): CFD is applied to assess risks related to fluid dynamics, such as in industries like aerospace or environmental engineering.
Risk calculation formula:
Risk Score = Likelihood Score × Consequence Score
7. Cost-benefit analysis:
Cost-benefit analysis quantifies the costs associated with risk mitigation measures and compares them to the expected benefits, helping organizations make informed decisions about risk management strategies.
8. Quantitative cyber risk assessment:
- In the context of cybersecurity, methods like the Common Vulnerability Scoring System (CVSS) are used to quantitatively assess the severity and impact of software vulnerabilities.
- Cyber risk quantification models, such as the FAIR (Factor Analysis of Information Risk) framework, provide a structured approach to estimating financial losses associated with cyber threats.
Cyber risk calculation formula:
Cyber Risk = Likelihood of Threat × Impact of Threat
These are just a few examples of quantitative risk assessment methods. The choice of method depends on the specific nature of the risk being assessed, the availability of data, and the organization’s goals for risk analysis and management.
Which are the situations where quantitative methods are most appropriate?
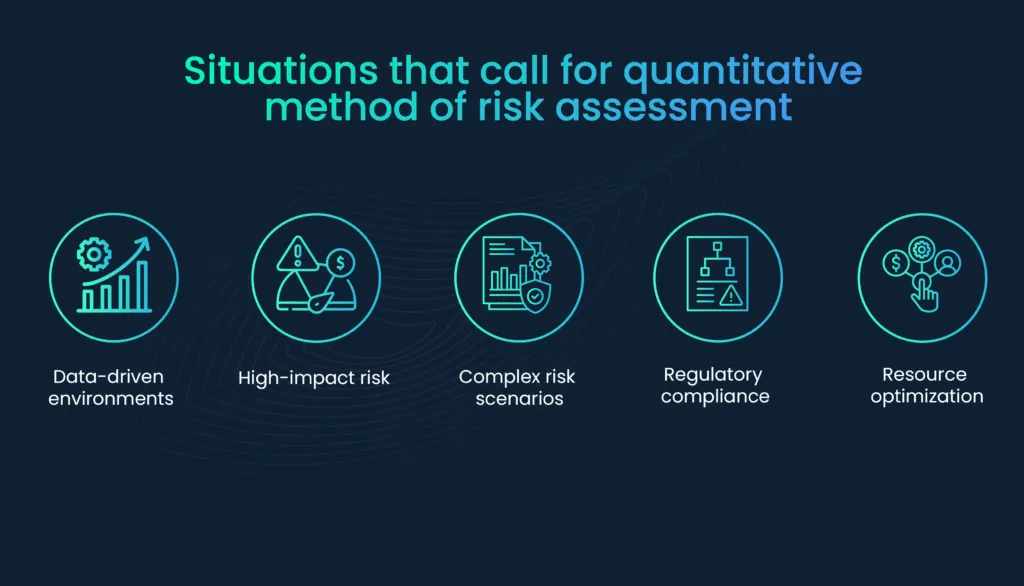
- Data-driven environments: Organizations with access to comprehensive and reliable data sources are well-suited for quantitative risk assessment.
- High-impact risks: For risks with potentially significant financial, operational, or safety consequences, quantitative methods provide a clear understanding of their potential impact.
- Complex risk scenarios: When risks involve multiple variables, dependencies, and intricate interrelationships, quantitative analysis can provide valuable insights.
- Regulatory compliance: Some industries and regulations mandate the use of quantitative risk assessment to ensure compliance and safety.
- Resource optimization: Organizations seeking to optimize resource allocation for risk mitigation strategies benefit from quantitative assessments.
C. Semi-quantitative risk assessment
Semi-quantitative risk assessment is a risk assessment approach that combines elements of both qualitative and quantitative methods to evaluate and prioritize risks within an organization or a project. It offers a more structured and systematic way to assess risks compared to purely qualitative methods while still providing some degree of quantitative analysis without the full precision and complexity of purely quantitative methods.
Semi-quantitative risk assessment combines elements of both qualitative and quantitative methods in the following ways:
- Qualitative assessment: It starts with a qualitative assessment of risks, identifying and describing them based on their potential impact and likelihood. This helps in understanding the nature and context of the risks.
- Quantitative data: It incorporates quantitative data or metrics where available, such as financial data, historical incident data, or probability estimates. These data points are used to assign numerical values to different risk parameters.
- Numerical scoring: These numerical values are often used to calculate an overall risk score or ranking for each identified risk. This score can help prioritize risks and allocate resources based on their relative risk calculation.
What are the different types of semi-quantitative methods for risk assessment?
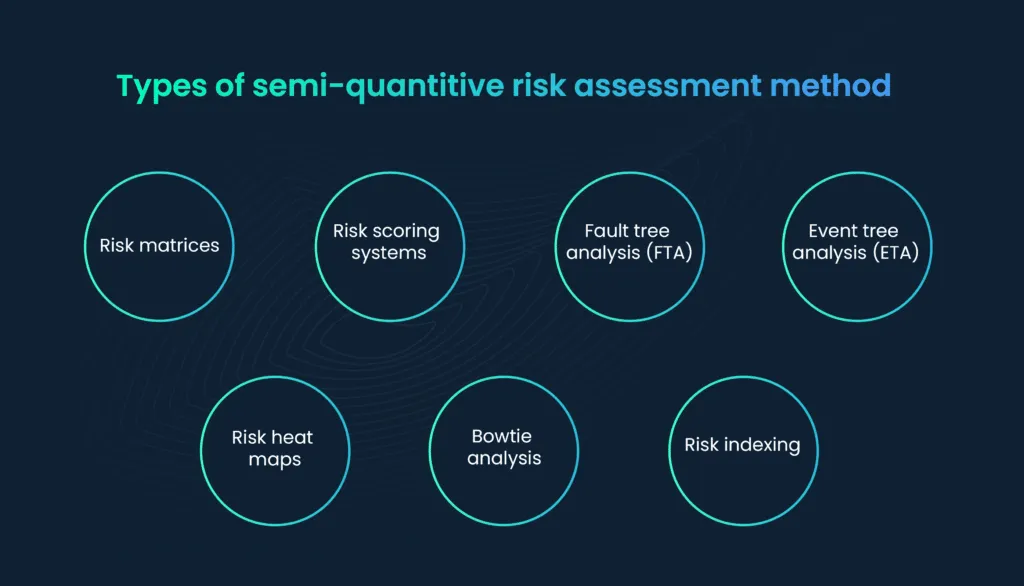
Semi-quantitative risk assessment methods offer flexibility in assessing and prioritizing risks by combining both qualitative and quantitative elements. There are several approaches and techniques within the realm of semi-quantitative risk assessment, including
1. Risk matrices:
Risk matrices are a common semi-quantitative tool used for risk assessment. They involve categorizing risks based on two factors: likelihood and consequence. Likelihood is often expressed as a probability or frequency, while consequence is assessed in terms of impact, severity, or other relevant factors. Risks are then plotted on a matrix, typically with a color-coded or numerical scale, to visually represent their level of risk. This approach helps prioritize risks based on their position within the matrix.
2. Risk scoring systems:
In a risk scoring system, risks are assigned numerical scores based on various parameters, such as probability, impact, vulnerability, or exposure. These scores are then used to calculate an overall risk score for each risk. Risks with higher scores are considered more critical or significant. The specific parameters and scoring scales can vary depending on the organization’s needs and industry standards.
3. Fault tree analysis (FTA):
Fault Tree Analysis is a semi-quantitative method used to analyze the potential causes of a specific event or failure. It involves constructing a diagram that represents the logical relationships between various events and conditions that can lead to the undesirable outcome. FTA assigns probabilities or likelihoods to these events, allowing for a semi-quantitative assessment of the overall risk associated with the event.
4. Event tree analysis (ETA):
Event Tree Analysis is similar to FTA but focuses on analyzing the potential consequences and outcomes of an initiating event. It models the sequence of events that may follow a specific incident or hazard. Probabilities are assigned to each branch of the tree, helping to assess the likelihood and consequences of different outcomes.
5. Risk heat maps:
Risk heat maps provide a visual representation of risks based on their likelihood and impact. The risks are plotted on a two-dimensional grid, with one axis representing likelihood (e.g., probability) and the other representing impact (e.g., severity). The intensity of colors or numerical values indicates the risk level. This method is useful for quickly identifying high-priority risks.
6. Bowtie analysis:
The bowtie analysis combines elements of FTA and ETA to visualize and analyze risks. It uses a diagram resembling a bowtie, with the initiating event in the center and various risk controls, consequences, and barriers on either side. This approach helps organizations assess the effectiveness of their risk mitigation measures and identify areas of improvement.
7. Risk indexing:
Risk indexing involves assigning scores or indices to specific risk factors, such as hazard severity, exposure, or vulnerability. These indices are then combined to calculate an overall risk index for each risk. The risks can be ranked based on their index values, aiding in prioritization.
The choice of a semi-quantitative risk assessment method depends on the nature of the organization, the specific risks being assessed, the available data, and the desired level of detail and precision in the assessment. Different methods may be more suitable for different industries and applications.
When should you use semi-quantitative methods for risk analysis?
Semi-quantitative risk assessment is particularly useful in the following situations:
- When there is a need for a more structured and systematic approach to risk assessment compared to purely qualitative methods.
- When there is a limited availability of quantitative data, and it is challenging to perform a fully quantitative risk assessment.
- When there is a desire to prioritize risks and allocate resources based on a combination of quantitative and qualitative factors.
- When there is a need to communicate risk information to stakeholders more understandably and visually, semi-quantitative methods often result in risk matrices or heat maps that are easy to interpret.
Comparative analysis of popular risk assessment methods
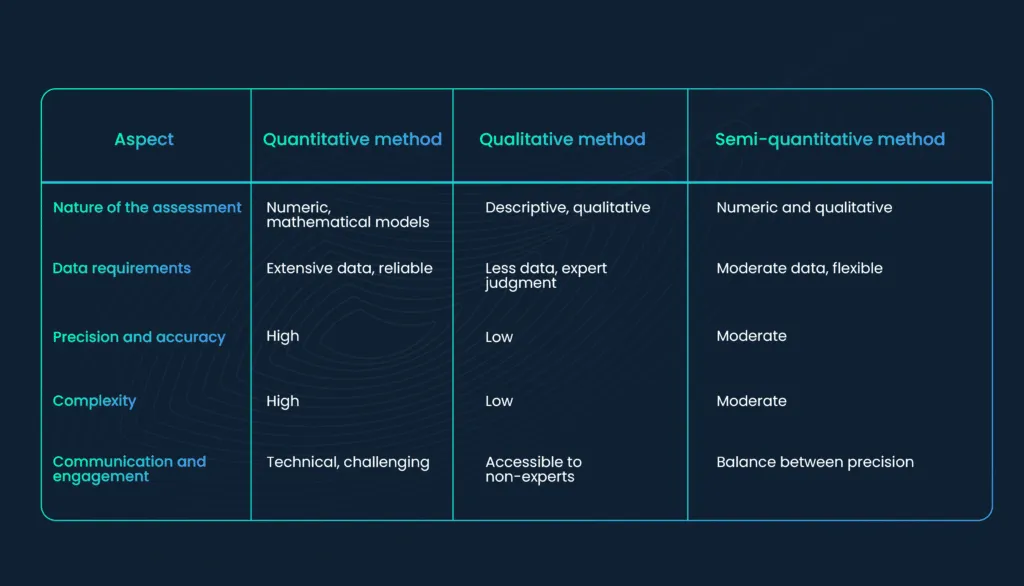
How do you choose an appropriate risk calculation method?

When choosing a risk calculation method, it’s essential to follow a systematic process to ensure that the selected method aligns with your organization’s needs and objectives. Here are the steps to take when choosing a risk calculation method:
Step 1: Define the purpose and objectives
- Clearly articulate the purpose of the risk assessment and what you aim to achieve.
- Define specific objectives, such as identifying and prioritizing risks, quantifying risk exposures, or supporting decision-making.
Step 2: Identify the scope and context
- Determine the scope of the risk assessment, including the areas, processes, projects, or aspects of the organization that will be covered.
- Consider the broader context, including the industry, regulatory requirements, and external factors influencing risk assessment.
Step 3: Understand the nature of risks
- Analyze the types of risks you are dealing with, such as financial, operational, strategic, or compliance-related risks.
- Consider the characteristics of these risks, including their frequency, severity, and potential impact on the organization.
Step 4: Assess data availability and quality
- Evaluate the availability and quality of data that can be used for risk assessment.
- Determine whether you have access to historical data, financial records, incident reports, or other relevant information.
Step 5: Identify stakeholders and expertise
- Identify key stakeholders, including decision-makers, subject matter experts, and team members, who will be involved in the risk assessment process.
- Assess the expertise and skills of those who will perform the assessment or provide input.
Step 6: Review existing methodologies
- Explore existing risk calculation methodologies and frameworks that are commonly used in your industry or domain.
- Consider industry standards, best practices, and guidance documents for risk assessment.
Step 7: Select the appropriate methodology
Based on the information gathered and the objectives defined, choose the most suitable risk calculation methodology. Options may include
- Quantitative methods (e.g., probabilistic modeling, Monte Carlo simulation) for precise numerical risk assessment.
- Qualitative methods (e.g., risk matrices, risk heat maps) for descriptive risk assessment.
- Semi-quantitative methods (e.g., risk scoring systems, fault tree analysis) for a balance between quantitative and qualitative approaches.
Step 8: Consider resource constraints
- Assess the available resources, including budget, time, and expertise, that can be allocated to the risk assessment.
- Ensure that the chosen methodology aligns with the organization’s resource constraints.
Step 9: Evaluate flexibility and scalability
- Consider whether the chosen methodology can adapt to changes in the organization’s risk landscape and objectives.
- Assess its scalability to handle larger or more complex risk assessments in the future.
Step 10: Risk communication and reporting
- Evaluate how the selected methodology facilitates the communication of risk information to stakeholders and decision-makers.
- Ensure that it supports clear and effective reporting of assessment results.
Step 11: Pilot and test the methodology
- Before full-scale implementation, consider conducting a pilot risk assessment using the chosen methodology.
- Use the pilot to identify any challenges, refine the process, and ensure that the methodology works as intended.
Step 12: Document the decision
- Document the rationale for selecting the chosen risk calculation method, including the factors considered and the expected benefits.
- Maintain clear records of the decision-making process for future reference.
Step 13: Review and update as needed
- Periodically review and update the chosen methodology to ensure it remains aligned with the organization’s evolving needs and objectives.
By following these steps, organizations can select a risk calculation method that best suits their specific risk assessment requirements and supports informed decision-making and risk management efforts.
Winding up
In conclusion, the right risk calculation method is essential in today’s digital age. We’ve explored three types: qualitative, quantitative, and semi-quantitative.
- Qualitative methods rely on expert judgment and discussions for a broad understanding of risks.
- Quantitative methods use data and mathematical models for precise risk quantification.
- Semi-quantitative methods strike a balance between the two.
Choosing the appropriate method hinges on factors like risk nature, data availability, resources, and organizational goals. It’s crucial to select the method that best suits your specific needs to protect your digital assets effectively.
Ready to enhance your risk management strategy? Explore Scrut’s powerful tools and solutions today to safeguard your organization’s future. Take the first step towards smarter risk assessment and mitigation. Get started now!
FAQs
1. What is the primary goal of risk calculation methods?
Risk calculation methods aim to assess and manage potential risks that an organization may face. They help in understanding the nature, severity, and impact of these risks, allowing for informed decision-making and risk mitigation.
2. How do organizations choose the most appropriate risk calculation method?
Organizations should consider factors such as the nature of the risk, data availability and quality, resource constraints, and organizational objectives when selecting a risk calculation method. A systematic approach helps align the method with specific needs.
3. Can risk calculation methods be adapted to changing circumstances?
Yes, organizations can periodically review and update their chosen risk calculation method to ensure it remains aligned with evolving needs and objectives. Flexibility and scalability are key considerations when selecting a method.





































