Choose risk-first compliance that’s always on, built for you.
Go back to blogs
From Risk to Resilience: Building an Effective Risk Management Process
Last updated on
April 17, 2025
13
min. read

An effective risk management process is essential for organizations to identify, assess, mitigate, and monitor risks that could impact their objectives. It involves a systematic approach that includes risk identification, analysis, evaluation, and response planning. All the details after identification and analysis are then included in a risk register.
Effective risk management also requires regular monitoring and reassessment of risks to ensure that controls and mitigation strategies remain relevant and effective.
By integrating risk management into decision-making processes and fostering a risk-aware culture, organizations can enhance their resilience, seize opportunities, and protect their assets and reputation.
In order to integrate risk management into an organization’s processes, it is critical that an effective risk management process is in place. Building an effective risk management process requires teams to follow 4 key steps, and they are discussed as follows.
4 key steps for building an effective risk management process
The IT risk management process inherently involves dealing with uncertainties. It is important for organizations to acknowledge and address these uncertainties by adopting a proactive and adaptive approach.
This involves continuously monitoring the risk landscape, staying informed about emerging threats and technologies, and regularly reassessing and updating risk management strategies and controls.
Step 1: Identifying the type of uncertainty in the IT risk management process
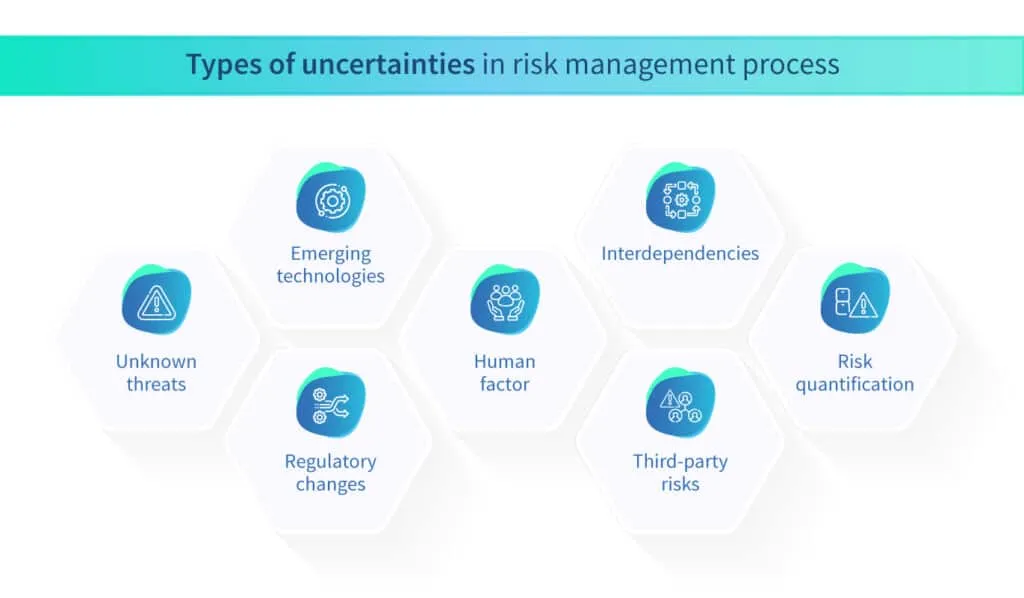
Some of the uncertainties associated with the IT risk management process are shown below:
- Unknown threats: The rapidly evolving landscape of cyber threats means that new and unknown risks constantly emerge. Identifying and understanding these unknown threats can be challenging, as their characteristics and potential impacts may not be fully known or understood.
- Emerging technologies: The adoption of emerging technologies such as artificial intelligence, Internet of Things (IoT), blockchain, and cloud computing introduces uncertainties in terms of their associated risks. As these technologies evolve, their vulnerabilities and potential impacts on IT systems and operations may not be fully predictable.
- Regulatory changes: The regulatory environment surrounding IT and cybersecurity is constantly evolving. Changes in laws, regulations, and compliance requirements introduce uncertainties in terms of how organizations must adapt their risk management practices to remain compliant and address emerging regulatory risks.
- Human factor: Human behavior and actions introduce a level of uncertainty in IT risk management. Employees, contractors, and other insiders can unintentionally or intentionally pose risks to IT systems and data through errors, negligence, or malicious activities.
- Interdependencies: IT systems and operations are often interconnected and interdependent. Changes or disruptions in one area can have cascading effects on others, introducing uncertainties in terms of how risks may propagate and impact the overall IT infrastructure.
- Third-party risks: Organizations often rely on third-party vendors, suppliers, or service providers for IT services and support. The risks associated with these third-party relationships, including their security practices, data handling processes, and vulnerabilities, introduce uncertainties that need to be managed.
- Risk quantification: Assigning precise quantitative values to risks, such as likelihood and impact, is inherently uncertain. Estimating the probabilities of events and assessing their potential impacts may involve assumptions and uncertainties that can impact the accuracy of risk quantification.
What are the three techniques for risk identification in the risk management process?
- Brainstorming and workshops:
Brainstorming sessions and workshops are effective techniques for identifying risks. By bringing together key stakeholders, subject matter experts, and team members, organizations can tap into their collective knowledge and expertise to generate a comprehensive list of potential risks.
During brainstorming sessions, participants freely share their ideas, thoughts, and concerns related to potential risks. Workshops provide a structured environment for focused discussions, allowing participants to delve deeper into specific areas and uncover risks that may not have been initially apparent.
Brainstorming and workshops encourage creativity, collaboration, and open dialogue, fostering an environment where diverse perspectives can be shared. These techniques enable organizations to identify both known and emerging risks that may arise from new technologies, processes, or external factors.
It is important to create a safe and non-judgmental space during these sessions, encouraging participants to freely express their thoughts and ideas without fear of criticism.
- Risk registers and assessment tools:
Risk registers and assessment tools are valuable resources for systematically capturing and analyzing risks. A risk register is a document or database that serves as a central repository for recording and managing risks throughout the organization.
It typically includes information such as the description of the risk, its likelihood and impact, risk owner, mitigation measures, and current status. Risk registers provide a structured framework for categorizing and prioritizing risks, ensuring that no risks are overlooked.
Assessment tools complement risk registers by providing a systematic approach for evaluating risks based on predefined criteria. These tools may include risk assessment matrices, scoring models, or qualitative and quantitative analysis methods.
They help in assessing the likelihood and impact of each identified risk, enabling organizations to prioritize risks based on their significance. Risk assessment tools provide a consistent and objective approach to evaluating risks, enhancing the accuracy and reliability of the risk identification process.
An IT risk management solution can provide both a risk register and assessment tools for the organization.
- Evaluating key pointers from historical data:
Learning from past experiences is a valuable technique for identifying risks. Lessons learned and historical data analysis involve reviewing and analyzing previous projects, incidents, or similar initiatives to identify patterns, trends, and potential risks.
This technique leverages the collective wisdom gained from past successes and failures to improve risk identification in current and future endeavors. Organizations can conduct thorough reviews of past projects or incidents to uncover risks that were encountered, the impact they had, and the mitigation measures that were effective or ineffective.
By analyzing historical data, organizations can identify common risk themes, recurring issues, or vulnerabilities that may exist in their systems, processes, or operations. This insight helps in identifying potential risks that may arise in similar contexts and enables organizations to proactively address them.
Lessons learned and historical data analysis also involve learning from industry trends, best practices, and benchmarking against peers. By staying informed about industry developments and understanding the risks faced by similar organizations, it becomes easier to identify risks that may be relevant to one’s own organization.
Step 2: Cultivating a risk management mindset
The second step in building an effective risk management process is integrating risk management as a mindset for your organization – which will happen once all the following steps are adhered to.
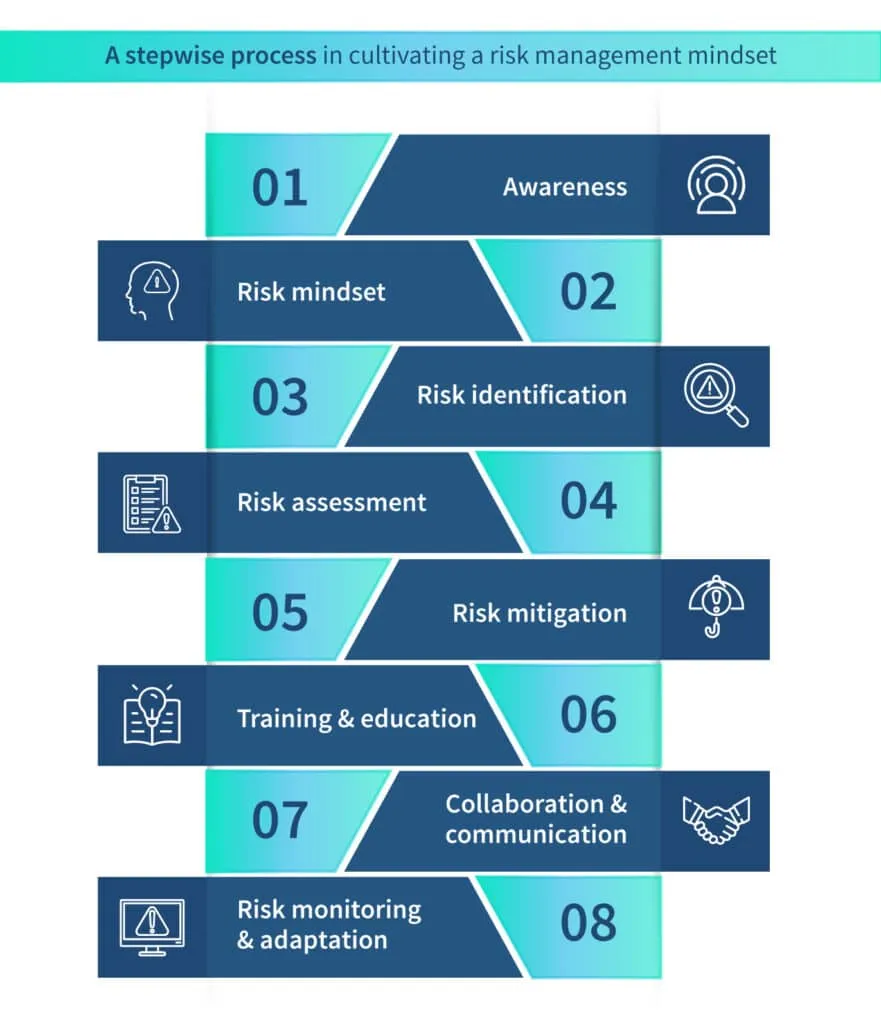
1: Awareness
Begin by developing a strong awareness of the importance of risk management. Understand that risks are inherent in any endeavor and that taking a proactive approach to managing them is crucial for success.
It’s important to acknowledge that risk management is a collective responsibility, extending beyond any specific team or department.
2: Risk mindset
Cultivate a mindset that acknowledges and embraces risk as an opportunity for growth and improvement rather than solely focusing on negative consequences. Encourage open discussions about risks and foster a culture where employees are encouraged to identify and report risks without fear of criticism.
3: Risk identification
Train yourself and your team to actively identify risks. Encourage a systematic approach to risk identification by conducting regular risk assessments, engaging stakeholders, and leveraging tools and techniques such as brainstorming, checklists, and lessons learned from past experiences.
4: Risk assessment
Develop the ability to assess risks by analyzing their potential likelihood and impact. Prioritize risks based on their significance and focus on those that could have the most significant consequences. Use qualitative or quantitative methods to assess risks, depending on the available data and resources.
5: Risk mitigation
Emphasize the importance of taking proactive measures to mitigate risks. Encourage the implementation of risk controls and countermeasures to reduce the likelihood or impact of identified risks.
Foster a culture where risk mitigation strategies are regularly reviewed, improved, and integrated into day-to-day operations.
6: Training and education
Promote a learning mindset within your organization by encouraging the analysis of past risk management efforts. Encourage ongoing education and training to stay updated on emerging risks, industry best practices, and new methodologies in risk management.
7: Collaboration and communication
Foster a collaborative environment where risk information is shared across teams and departments. Promote effective communication channels to ensure that risks are effectively communicated to stakeholders, enabling timely decision-making and action.
8: Risk monitoring and adaptation
Establish a system for ongoing risk monitoring and review. Regularly assess the effectiveness of risk mitigation measures, monitor key risk indicators, and adapt risk management strategies as needed to address changing circumstances and emerging risks.
By embracing these steps and fostering a risk management mindset, individuals and organizations can proactively identify, assess, and manage risks, leading to better decision-making, improved resilience, and increased opportunities for success.
Step 3: Developing key skills for an effective IT risk management process
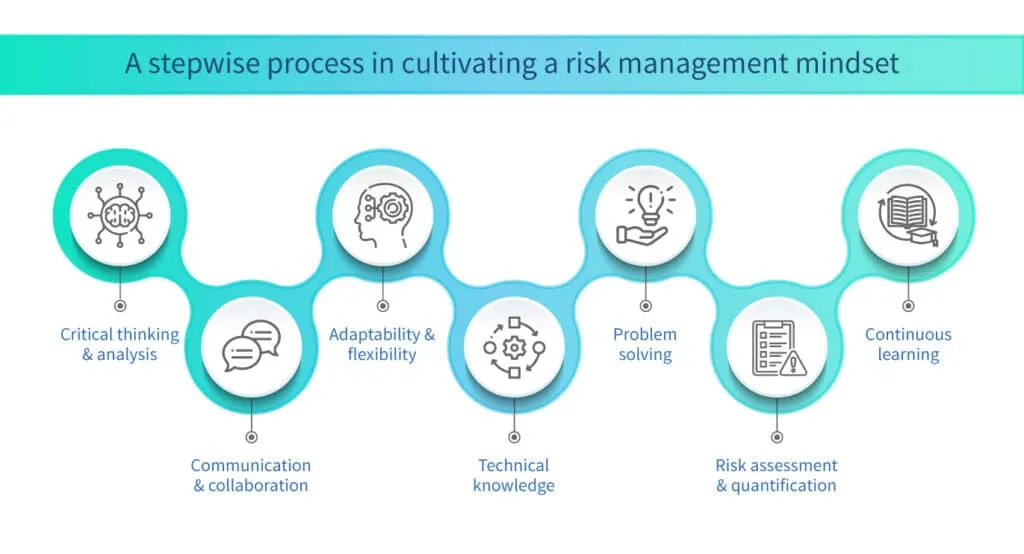
Organizations can enhance the effectiveness of the IT risk management process, make informed decisions, and ensure the security and resilience of IT systems within the network by honing key skills as shown below:
Critical thinking and analysis
Developing strong critical thinking skills are essential for an effective risk management process. It involves the ability to analyze complex situations, identify patterns, and make informed decisions based on available data. This skill helps in assessing the likelihood and impact of risks, evaluating the effectiveness of mitigation strategies, and identifying potential gaps or vulnerabilities.
Communication and collaboration
Effective communication is crucial for successful risk management. This skill involves the ability to clearly articulate risks, their potential impacts, and the recommended mitigation strategies to stakeholders at all levels of the organization. Additionally, collaboration skills enable effective teamwork and engagement with cross-functional teams, encouraging the sharing of information, perspectives, and expertise.
Adaptability and flexibility
The IT risk management process requires the ability to adapt and respond to changing circumstances and emerging risks. Being open to new information, remaining flexible in adjusting risk management strategies, and proactively adapting to technological advancements and evolving threat landscapes are key aspects of this skill. It involves continuously monitoring the risk environment, staying updated on industry trends, and adjusting risk mitigation plans accordingly.
Technical knowledge
Having a strong understanding of IT systems, infrastructure, and security concepts is vital for an effective IT risk management process. This includes knowledge of network architecture, software development processes, cybersecurity principles, and industry-specific regulations and standards. A solid technical foundation enables risk managers to better assess and mitigate risks specific to IT environments.
Problem-solving
The IT risk management process often involves dealing with complex problems and finding practical solutions. Developing strong problem-solving skills helps in identifying the root causes of risks, brainstorming alternative approaches, and implementing effective risk mitigation measures. It involves a systematic approach, creativity, and the ability to evaluate trade-offs to reach optimal solutions.
Risk assessment and quantification
Being skilled in risk assessment and quantification allows risk managers to effectively analyze risks, assign probabilities and impacts, and prioritize mitigation efforts. This includes knowledge of risk assessment methodologies, data analysis techniques, and risk modeling. Understanding how to measure and communicate risks in a quantifiable manner aids in decision-making and resource allocation.
Continuous learning
The IT risk management process requires staying updated with industry trends, emerging technologies, and new risks. Developing a habit of continuous learning helps in expanding knowledge and skills, keeping pace with evolving threats, and adopting best practices. Engaging in professional development activities, attending conferences, and actively seeking out new learning opportunities are essential for staying relevant in IT risk management.
Step 4: Integrating approaches in the IT risk management process
There are numerous standards and frameworks that govern the IT management process of the organization, directly or indirectly. An organization should follow these standards and frameworks for a better security posture.
These standards and frameworks also bring other advantages like increased trust in the market, improved transparency, adherence to rules and regulations, and streamlining of processes and procedures of the organization.
Implementing common industry frameworks
Common frameworks provide organizations with a structured approach to risk management, offering guidelines and best practices for identifying, assessing, and mitigating risks. ISO 31000 and NIST SP 800-30 are two widely recognized frameworks used in IT risk management.
ISO 31000
ISO 31000 is an international standard that provides principles, a framework, and a process for managing risks effectively. It emphasizes the importance of integrating risk management into the organization’s overall governance and decision-making processes.
By following ISO 31000, organizations can establish a risk management framework tailored to their specific needs, ensuring a systematic and proactive approach to risk identification, assessment, treatment, and monitoring.
NIST SP 800-30
NIST SP 800-30 is a special publication by the National Institute of Standards and Technology (NIST) that provides guidance on conducting risk assessments for federal information systems. It outlines a structured approach to assessing risks associated with IT systems, including the identification of assets, threats, vulnerabilities, likelihood, and impact analysis.
NIST SP 800-30 helps organizations understand their risk landscape and make informed decisions regarding risk mitigation strategies.
Understanding and incorporating these frameworks into the risk management process provides organizations with a solid foundation for effectively managing IT risks, aligning with industry standards, and enhancing their overall cybersecurity posture.
Assessing risk tolerance and appetite
Assessing risk tolerance and appetite is a critical step in the risk management process. Risk tolerance refers to the level of risk that an organization is willing to accept or tolerate, considering its objectives, resources, and overall risk appetite. Risk appetite, on the other hand, represents the willingness of an organization to take on risk in pursuit of its goals.
To assess risk tolerance and appetite, organizations need to consider factors such as their industry, regulatory requirements, strategic objectives, financial capabilities, and stakeholder expectations. This involves engaging key stakeholders, including executives, board members, and risk management professionals, in discussions to define the organization’s risk tolerance levels.
By clearly understanding the organization’s risk tolerance and appetite, risk managers can align their risk management strategies and controls accordingly. This ensures that risks are managed within acceptable levels and that decisions regarding risk mitigation efforts are consistent with the organization’s overall risk appetite.
Developing a risk management plan
A risk management plan outlines the strategies, processes, and activities that an organization will undertake to manage its risks effectively. It provides a roadmap for implementing risk management practices and ensures that risk management efforts are aligned with the organization’s objectives and risk tolerance.
When developing a risk management plan, organizations should consider the key components of the risk management process, including risk identification, risk assessment, risk mitigation, and risk monitoring and review.
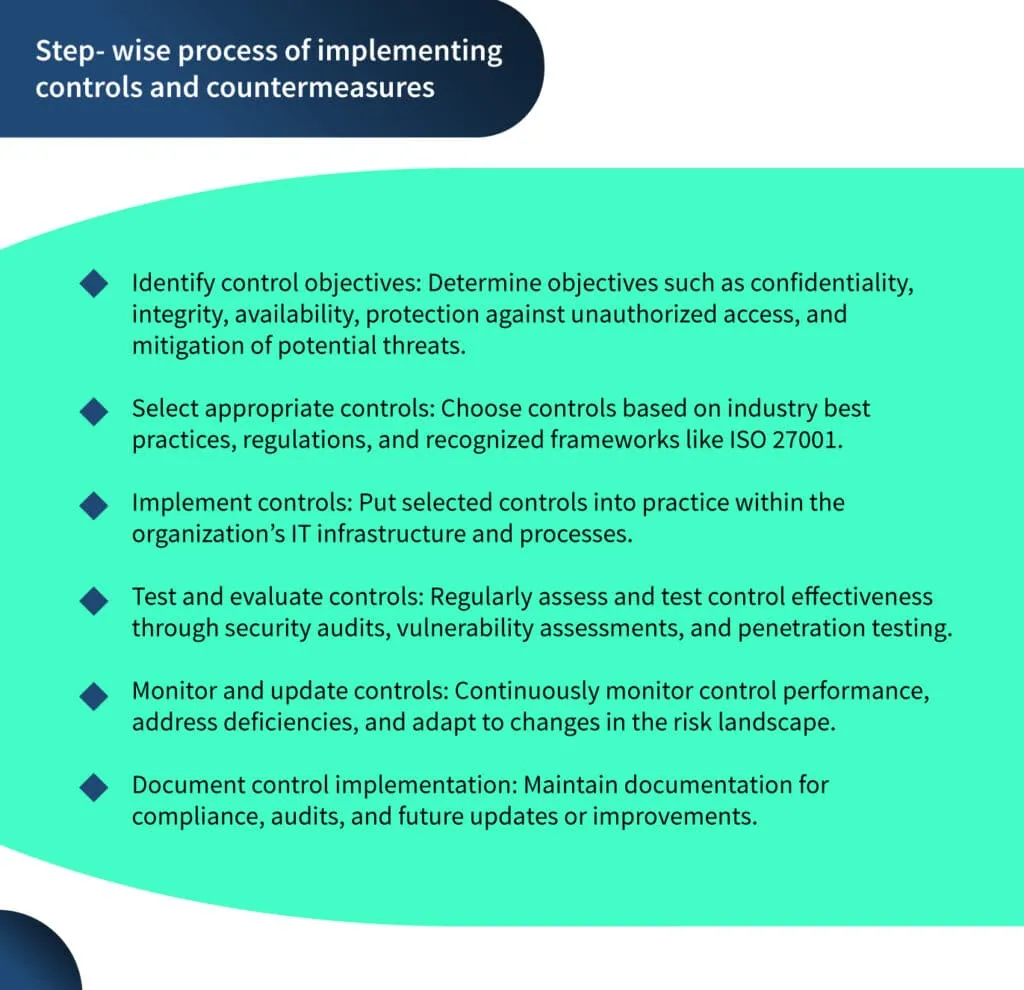
Implementing controls and countermeasures
Implementing controls and countermeasures is a crucial aspect of the risk management process. Controls are measures put in place to prevent, detect, and respond to risks, while countermeasures are specific actions taken to mitigate identified risks.
Conclusion
In conclusion, building an effective risk management process is essential for organizations to navigate the uncertainties and challenges they face. By following a systematic approach that includes risk identification, analysis, evaluation, and response planning, organizations can proactively manage risks and enhance their resilience.
Cultivating a risk management mindset, developing key skills, and integrating frameworks and approaches further strengthen the risk management process. Assessing risk tolerance, developing a risk management plan, and implementing controls and countermeasures are critical steps to ensure effective risk management.
By embracing these principles and practices, organizations can protect their assets, reputation, and achieve their objectives in an ever-changing and complex business environment.
Scrut can help you gain a competitive advantage by gaining a complete understanding of your risk posture. If you have any questions regarding the automation of the risk management process, reach out to Scrut.
FAQs
What are the key steps for building an effective risk management process?
The key steps for building an effective risk management process are:
Step 1: Identifying the type of uncertainty in the risk management process.
Step 2: Cultivating a risk management mindset.
Step 3: Developing key skills for an effective IT risk management process.
Step 4: Integrating frameworks and approaches in the IT risk management process.
What is a risk management plan?
A risk management plan outlines the strategies, processes, and activities that an organization will undertake to manage its risks effectively. It provides a roadmap for implementing risk management practices and ensures that risk management efforts are aligned with the organization’s objectives and risk tolerance.
How important is continuous learning in IT risk management?
Continuous learning is vital in IT risk management as it helps professionals stay updated with industry trends, emerging technologies, and new risks. It enables the expansion of knowledge and skills, the adoption of best practices, and the ability to make informed decisions in a rapidly evolving landscape. Engaging in professional development activities and seeking out new learning opportunities are essential for staying relevant in IT risk management.
Table of contents


















