It is a common misconception that security and compliance are the same thing, and they are often used interchangeably. For the uninitiated, being compliant may equate to being secure and vice versa. But this is far from accurate. If you look closely, they are as similar as fraternal twins.
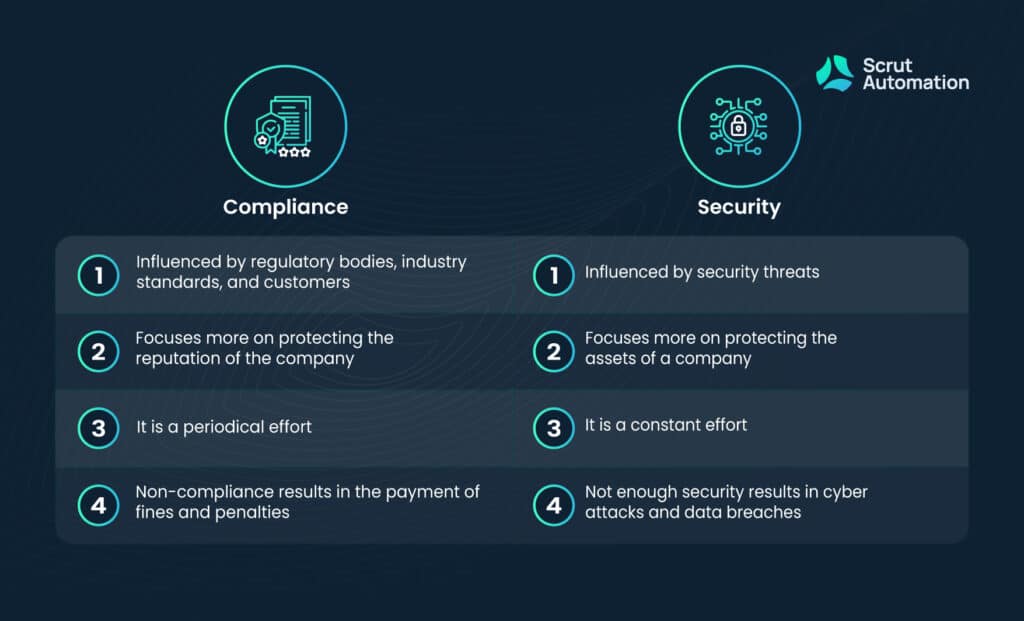
Both compliance and security are integral when it comes to the safety of a company. However, compliance, very often, fulfills only the bare minimum of security requirements in order to get a seal of approval from regulatory bodies, while security actively prevents, monitors, and resolves threats against a company.
Though a compliant company is secure on paper, this may not be true in reality. For example, Uber, which is ISO 27001 and PCI DSS 3.2 compliant, fell victim to a data breach in December 2022 that led to the leak of source code, IT asset management reports, and other corporate information.
Most companies do their best to stay compliant in a bid to not only pass security compliance standards but to also be secure. Unfortunately, simply being compliant does not equate to being secure. Very often, when a company focuses too much on compliance, its ability to allocate time and resources to data security is compromised.
Let’s explore in detail how compliance and security differ and why security scores higher in the need hierarchy of a company’s safety.
What is compliance?
Compliance refers to the state achieved by a company when it adheres to the security standards set by an industry or regulatory body. These standards are set with the intention to keep a company secure and reliable. They seek to protect not only the company but the customers, investors, and third-party vendors who interact with it.
Being compliant is a constant effort, but it is well worth it since a non-compliant company is a walking red flag. Customers, investors, and vendors will be wary of associating with any company that is not compliant.
Both government and non-government bodies dictate compliance standards. There are compliance frameworks that impose mandatory standards and others that can be opted for by a company to ensure that it is in line with the best industry practices.
For instance, Health Insurance Portability and Accountability Act (HIPAA) is a mandatory compliance framework that healthcare companies have to adhere to, while Service Organization Control Type 2 (SOC2) is a framework companies can choose to follow if they need guidance to deal with data securely.
Compliance is a comprehensive process that takes into account regulatory standards, industry practices, security standards, and business optics.
What is security?

Security refers to the processes, tools, and frameworks that a company has in place in order to protect its assets from being accessed, modified, stolen, damaged, or leaked by unauthorized elements. The gamut of security is extensive, and it employs various tools, controls, and practices to optimize safety.
Security is ensured by overseeing the following processes, controls, and components.
IT framework
The IT framework of an organization includes all the elements of a computer network. This covers both hardware and software, operating systems, internet connections, servers, and data cloud storage. Antivirus and antimalware software can help secure the IT infrastructure of a company.
Network access
Security ensures that access to a company’s data and assets is restricted only to authorized users. It does this by implementing security practices such as the use of firewalls and identity access management tools that deny access to unwanted elements.
Authentication
Authentication is an important part of a company’s defense system. Authentication methods help verify the identity of users and ensure that only authorized personnel are able to access information that pertains to them. Two-factor authentication and multifactor authentication are some of the effective ways that help verify user identity.
Security awareness training
It is not uncommon for data breaches to be caused by the errors of employees. This is why it is important for the security team to educate all employees in a company about the best security practices so as to avoid any leeway for security breaches.
Physical controls
Physical controls are just as important as technical and administrative measures. Everything from identity cards to fingerprint scanners helps in keeping a company’s assets safe from security threats.
Exploring the differences between security & compliance
Both cyber security compliance and IT security are responsible for protecting an organization’s data. How they do it, why they do it, and the results of their efforts differ among other factors. Here is a look at how compliance and security differ.
Compliance vs. Security: A Quick Glance
They are confronted by different forces
Regulatory bodies, industry standards, and customers dictate the steps a company has to follow in order to be seen as compliant. The security of a company is reviewed during compliance audits. These audits allow dialogue between the company and the reviewers.
For instance, PCI DSS, which is a compliance framework for financial organizations, mandates compliance cyber security awareness training for all employees, and it expects all employees to acknowledge in writing that they have completed the training. If one or two employees do not do this for whatever reason, the company has the ability to explain why to the auditors and negotiate a positive outcome.
This is not possible when it comes to security, which faces off against faceless entities that lurk around, ready to attack at any time. Cybercriminals or threat actors are ruthless adversaries whose only goal is to find vulnerabilities in a security system, attack it, and get away with as much as they can. While compliance deals with white-collar agents, security has to battle cyber ninjas who appear without warning.
They have different goals
The main aim of compliance is to build trust and confidence with customers, stakeholders, and partners by exemplifying a commitment to security and privacy.
The objective of information security is to prevent unauthorized access, use, disclosure, modification, or destruction of sensitive information. It seeks to prevent cyber attacks, reduce their impact, and resolve them. It also carries out damage control after the occurrence of security incidents by restoring affected assets.
They differ in urgency
Frequent audits may be held which leads to compliance being a constant effort. However, no matter how frequent the audits are, companies are still given time, however short, to gather and produce evidence of compliance. Meeting compliance is a periodical effort. There is no surprise element to them.
Security, on the other hand, is always on its toes. Since security threats do not announce their arrival and are constantly on the prowl, the need for security is always pressing.
They have different approaches
Compliance tends to be a reactive process. Companies are given specific standards to follow within a set time. They follow the prescribed security protocol and fulfill the given requirements. There is not much intuition or innovation when it comes to achieving compliance.
Security adopts a dynamic approach. For a company to be secure, it has to adopt a proactive security posture that is constantly evolving to face any security threat that may arise. Security has to constantly stay on top of advancing technology and threats in order to avert security crises.
They are influenced by different factors
Companies are slotted under different categories, each of which has a different set of standards to adhere to. Fulfilling these requirements is what influences the process of compliance.
Security is influenced by the smallest change in an organization’s operation, its technology, or its employees’ activities. Every variation is a call to action in a company with a good security posture.
Security goes deeper
Though compliance is meant to ensure the security of a company, certain companies tend to approach it with a more superficial attitude. They treat compliance as a way save face and look good on paper. They tick boxes of compliance standards just to gain the trust of their customers and the approval of regulatory bodies. This detracts from taking care of urgent security needs.
A company that focuses on security makes safety its priority. It goes deeper when it comes to security and focuses on predicting, analyzing, and tackling security risks by constantly updating its technology and processes to protect the company in real-time.
Effects of poor implementation
When a company does not follow compliance standards to a tee, it is forced to pay fines and penalties. It also becomes vulnerable to security risks.
A company with a bad security posture is constantly at risk of cyber attacks, data breaches, and other security threats. Cyber attacks can lead to companies shutting down for several hours or longer, leading to a loss of revenue. They lead to the loss of data and corruption of devices. A company that faces a data breach also loses the trust of its customers, and its reputation takes a hit.
Why a compliance-first approach is detrimental to a company’s safety
It is not unusual for companies to adopt a compliance-first approach, and they cannot be blamed for doing so. Compliance is often advertised as the ultimate solution for all security needs. It is a well-defined framework that provides actionable steps, which on completion gives companies the perception of being safe.
Very often, compliance leads to complacency in a company. Some companies, on being tagged as compliant, assume that they are safe till the next audit. Let’s explore how a compliance-first approach could hamper the safety of a company.
Security becomes a tickbox
Some companies treat compliance solely as a means to project an image of security. They take all the steps necessary to make a company audit-ready. However, this does not result in the company being attacker-ready.
Frequent audits are taxing, and it takes up a lot of time and resources to fulfill the requirements of a compliance framework. Sometimes companies may even lie to come across as compliant. Since so much has to be done just to come across as secure, efforts to actually be secure are put on the back burner by some companies.
Makes it easy for attackers

When a company follows a compliance-first or compliance-only approach, it makes life easy for attackers. It’s not difficult for cybercriminals to gain access to compliance frameworks. This allows even the most basic cybercriminal to figure out the security program of a company and determine where its vulnerabilities lie.
Compliance requirements cannot keep up with security needs
Both technology and security threats evolve constantly. This makes compliance standards obsolete the moment they are established. These standards are updated periodically after much deliberation about what is crucial for a company’s security posture.
Though this is done with the best intentions, the time taken to come up with these standards is long enough for uncountable new security threats to spawn. It sometimes takes several years to update compliance standards.
It’s easy for threat actors to get past outdated measures that were developed to combat their forerunners. Using a compliance-first approach is like carrying a rusty old knife to a gunfight.
Discourages the security team
A compliance-first approach puts a damper on the security operations of a company. Since importance is placed on fulfilling compliance requirements alone, it leaves the security team feeling neglected and underutilized.
Security practitioners are meant to actively predict, prevent, and resolve any security threat that may arise, but companies that prioritize compliance over security make them do the most mundane tasks to fulfill basic compliance requirements. Compliance-first companies also tend to ignore the needs of the security team and may refuse to allocate funds for their operations.
Leads to inefficient security practices
There is no compliance framework out there that is completely equipped to effectively tackle all security threats. When a company adopts a compliance-first approach, it leans mainly on compliance standards alone to ensure its safety.
Some companies on successfully passing audits assume that they are secure and carry on with a false sense of security. Compliance should not be treated as a one-and-done process, and it certainly should not replace a company’s security program.
It is true that compliance standards can spur companies to adopt practices that help in security such as compliance security awareness training for employees. However, their role is only supplementary when it comes to ensuring a company’s safety. Compliance should work together with security to improve a company’s security posture.
Why a security-first approach is better

Cyber-attacks have become extremely sophisticated and deadly. Thankfully, cybersecurity has not trailed behind. It is no longer just a tickbox for companies but a business driver that instills trust and confidence in customers and allows a company to scale and grow without worrying about security incidents. Here is how adopting a security-first approach benefits companies.
Protects information
Security goes above and beyond to protect any data that is sensitive from unauthorized access, alteration, and destruction. When it comes to data protection, security has three main functions:

Confidentiality: All sensitive information is kept confidential by preventing unauthorized access to them. It does this by employing the best identity and access management techniques such as multifactor authentication.
Integrity: Security ensures that authorized personnel has access to sensitive information that has not been altered in any way by unauthorized elements.
Availability: A good security system lets authorized personnel have access to data at any given time. It makes information unavailable to unauthorized users. Security measures such as the Zero Trust model do not allow even the employees of an organization to access data that does not pertain to them.
Tackles security breaches
Security breaches are the modern-day goliaths standing in the way of a company’s security and credibility. A good security team deals with security breaches by reducing the magnitude of the impact of security breaches. They respond to cyber-attacks and resolve them.
In case they are unable to stop an attack, they perform damage control by restoring assets that have been compromised. A proactive security system analyzes and predicts threats. It also monitors both assets and security threats in real-time to reduce the probability of security breaches.
Keeps the entire company informed about the best security practices
Security is a company-wide effort. There have been several instances of security breaches caused by the oversight of employees. Even the most comprehensive security strategy is bound to fail if employees are not kept informed of the best security practices.
Clicking on phishing links, losing company devices, and not using strong passwords are just some of the ways employees can jeopardize a company’s safety. This is why security training is an important part of a good security plan.
If you are interested in learning about how to adopt a security-first approach to protect your company, click here.
How compliance can help security
Though putting compliance first is not an ideal approach to security, compliance can still act as a baseline for security. For instance, cloud security compliance offers guidelines on how digital data can be used and stored. IT security compliance helps improve the cybersecurity posture of an organization with useful actionable steps such as internal audits and employee training.
Security frameworks such as PCI, SOC 2, and ISO can act as great reference points for improving cybersecurity posture. They can help manage customer data better, strengthen a company’s Information Security Management System (ISMS), and improve data security standards.
By studying the requirements of compliance frameworks, security teams can get an idea of what to prioritize. They can help in reviewing and analyzing the company’s security posture and enforcing good security practices. Using feedback from compliance audits can also help identify areas where security can be improved.
Conclusion
Both compliance and security are vital for any organization’s survival. It is hard to have one without the other. A company that is not compliant will be penalized out of existence, and a company that is not secure will be attacked beyond repair by security threats.
By adopting a security-first approach, an organization will always be audit-ready, since a comprehensive security posture will cover the basic requirements of most compliance frameworks. It will also be able to take on any security threat that comes its way.
Compliance ensures that a company is in line with the security standards imposed by a regulatory body or industry. It is important, but it should not take precedence over security.
Compliance should act as a roadmap to chart out security rather than be a roadblock to it. Compliance and security should work hand in hand and not compete with one another. When the two align, they fortify a company against threats to its safety and credibility.
Both data security and compliance can be maintained effectively by adopting the right kind of software. Software such as Scrut can help make both processes easier and more efficient by streamlining and automating them. If you are interested in learning more, click here to book a demo.






































