In today’s increasingly digital world, the significance of cybersecurity culture cannot be overstated. It goes beyond just implementing robust technical solutions and firewalls.
Cyber threats continue to evolve, and a strong defense requires more than just technology; it demands a change in organizational culture.
An effective cybersecurity culture ensures that every employee, from the C-suite to the interns, is aware of the role they play in safeguarding sensitive information. It’s a proactive approach to security that fosters an environment where security is not just the responsibility of the IT department but a collective commitment.
In this blog, we’ll explore why cybersecurity culture is crucial and how to cultivate it within your organization.
Understanding the security mindset
A security mindset is a fundamental component of a robust cybersecurity culture. It represents the organization’s collective attitude and approach to cybersecurity, emphasizing that security is everyone’s responsibility.
It goes beyond compliance checklists and delves into the realm of active vigilance, where employees are not only aware of potential threats but are also prepared to respond to them.
Having a security mindset means being cautious, informed, and willing to take the necessary actions to protect sensitive data. It’s about fostering a culture where cybersecurity is integrated into daily operations, becoming second nature to employees, much like workplace safety practices. This security mindset creates a dynamic defense against ever-evolving cyber threats.
Components of a security mindset-cybersecurity culture
Building a strong cybersecurity culture requires a deep understanding of the key components that form the foundation of a security mindset within an organization.
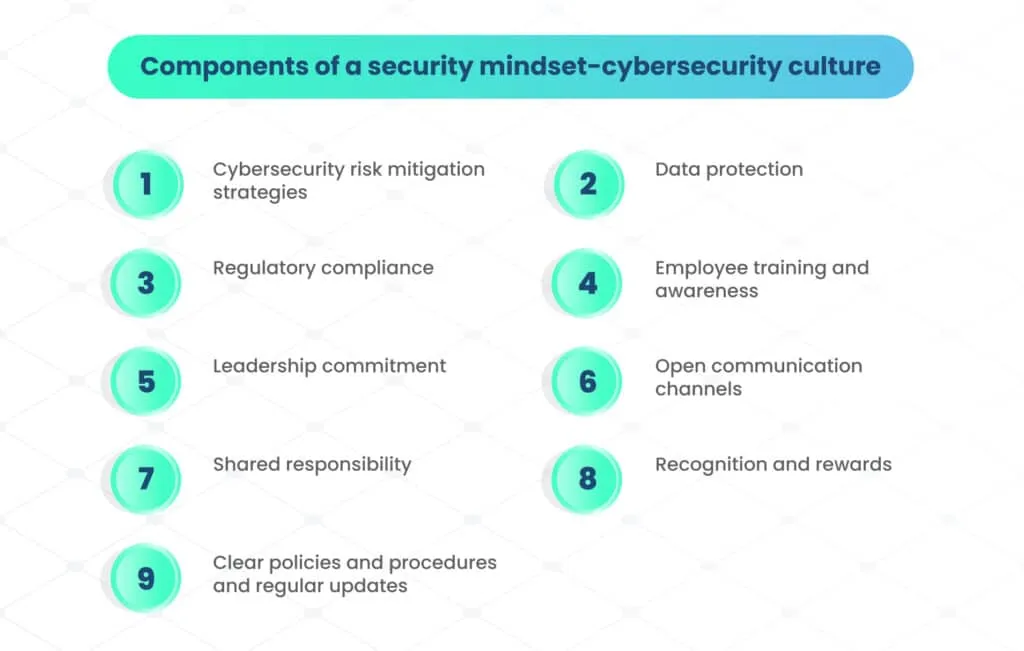
1. Cybersecurity risk mitigation strategies
A security mindset forms the foundation for implementing effective cybersecurity risk mitigation strategies. When employees understand and embrace their role in safeguarding the organization, the likelihood of cyber threats causing significant damage is greatly reduced.
2. Data protection
In an era where data is an invaluable asset, a security-conscious workforce plays a pivotal role in data protection. A security mindset ensures that employees prioritize data security and handle sensitive information with the utmost care.
3. Regulatory compliance
Compliance with cybersecurity regulations is non-negotiable for many industries. A security mindset ensures that all employees are aware of these regulations and actively adhere to them, reducing the risk of legal complications.
4. Employee training and awareness
The foundation of a strong cybersecurity culture is the awareness and training of employees. Security training programs equip your workforce with the knowledge and skills to recognize potential cybersecurity threats and respond appropriately.
This includes understanding the dangers of phishing attacks, recognizing suspicious behavior, and knowing how to report security incidents. By investing in ongoing security awareness training, you empower employees to become the first line of defense against cyber threats.
Additionally, regular training sessions can help keep employees updated on emerging threats and best practices, ensuring that cybersecurity remains a top priority.
5. Leadership commitment
Building a cybersecurity culture starts at the top. Senior management should lead by example when it comes to cybersecurity. When leaders demonstrate a strong commitment to security, it sets a powerful precedent for the entire organization.
Leadership commitment is paramount for fostering a security-focused environment. When leaders prioritize and actively support cybersecurity initiatives, it sends a clear message throughout the organization. It demonstrates that cybersecurity is not just an IT concern but a fundamental business objective.
Leaders can set an example by adhering to security policies, engaging in training, and openly discussing the importance of cybersecurity. Their commitment reinforces the security mindset and motivates employees to follow suit.
6. Open communication channels
Effective communication channels and reporting mechanisms are integral to a cybersecurity culture. Employees need to feel comfortable reporting potential security incidents or concerns without fear of repercussions.
Establish a clear process for reporting incidents, and ensure that it is well-communicated throughout the organization. Open lines of communication foster transparency, allowing issues to be addressed promptly.
Moreover, regularly sharing information about the latest threats and best practices keeps employees informed and alert.
Encourage employees to report cybersecurity incidents or express concerns without fear of repercussions. Accessible communication channels can be the first line of defense,To further strengthen cybersecurity awareness and foster collaboration, organizations often organize engaging webinars that educate teams on real threats, best practices, and how to adopt secure behaviors across departments.
7. Shared responsibility
Promote the concept that security is everyone’s responsibility. Employees should understand that their actions directly impact the organization’s cybersecurity posture.
8. Recognition and rewards
Recognize and reward employees who exemplify a strong security mindset. Incentives, acknowledgments, or cybersecurity certifications can motivate individuals to stay vigilant.
9. Clear policies and procedures and regular updates
Well-defined security policies and procedures provide employees with a roadmap for safeguarding sensitive information. These documents outline expectations, responsibilities, and consequences for non-compliance.
Clear policies help standardize security practices across the organization, ensuring everyone is on the same page. Employees should be aware of the policies that govern their use of technology and the handling of data.
Regular reviews and updates of these policies are essential to adapting to evolving threats and technologies.
Keep cybersecurity policies, protocols, and cybersecurity mitigation strategies up-to-date. The digital landscape evolves rapidly, so it’s crucial that your security measures evolve with it.
How to build cybersecurity awareness
Building cybersecurity awareness includes several measures:
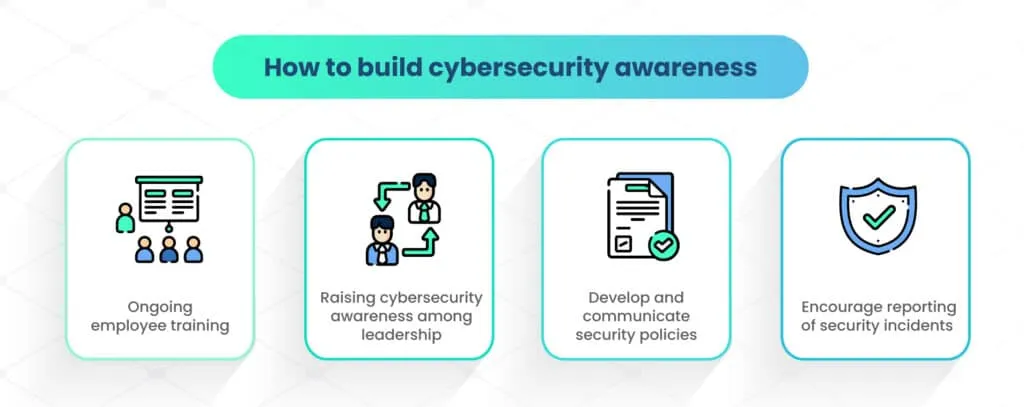
A. Ongoing employee training
Employee training is the cornerstone of building cybersecurity awareness within your organization. It equips your workforce with the knowledge and skills they need to recognize and respond to cyber threats effectively.
Training should cover a wide range of topics, from understanding phishing attacks to practicing secure password management. Moreover, it should be an ongoing process, as the cybersecurity landscape is continuously evolving.
Regular training sessions keep employees informed about emerging threats and reinforce the importance of their role in the organization’s security. A well-trained workforce serves as a vital layer of defense against cyberattacks.
B. Raising cybersecurity awareness among leadership
Cybersecurity awareness should extend to all levels of your organization, including leadership. Leaders set the tone and direction for the entire workforce, and their commitment to cybersecurity initiatives is crucial.
By engaging leadership in cybersecurity training and discussions, you ensure that security is a top-down priority. Leadership should not only support cybersecurity but actively participate in discussions and initiatives. This approach reinforces the importance of cybersecurity and encourages employees at all levels to follow suit.
C. Develop and communicate security policies
Well-defined security policies are the guiding principles of your cybersecurity culture. These policies outline the expectations, responsibilities, and best practices for safeguarding sensitive information. However, having policies alone is not enough; they must be effectively communicated throughout the organization.
Employees should be aware of the policies that govern their use of technology and data handling. Regular reviews and updates of these policies ensure that they remain relevant and adaptable to emerging threats and technologies.
D. Encourage reporting of security incidents
Encouraging the reporting of security incidents is a vital component of building cybersecurity awareness. Employees need to feel comfortable reporting potential security threats or concerns without fear of reprisal.
Establish a clear process for reporting incidents and ensure that it is well-communicated throughout the organization.
An open reporting culture promotes transparency and allows issues to be addressed promptly. It also serves as a valuable feedback loop, helping organizations identify areas that require additional training or security measures.
Challenges encountered when nurturing a security mindset
Nurturing a security mindset is a crucial aspect of safeguarding an organization’s digital assets, yet it is not without its challenges.
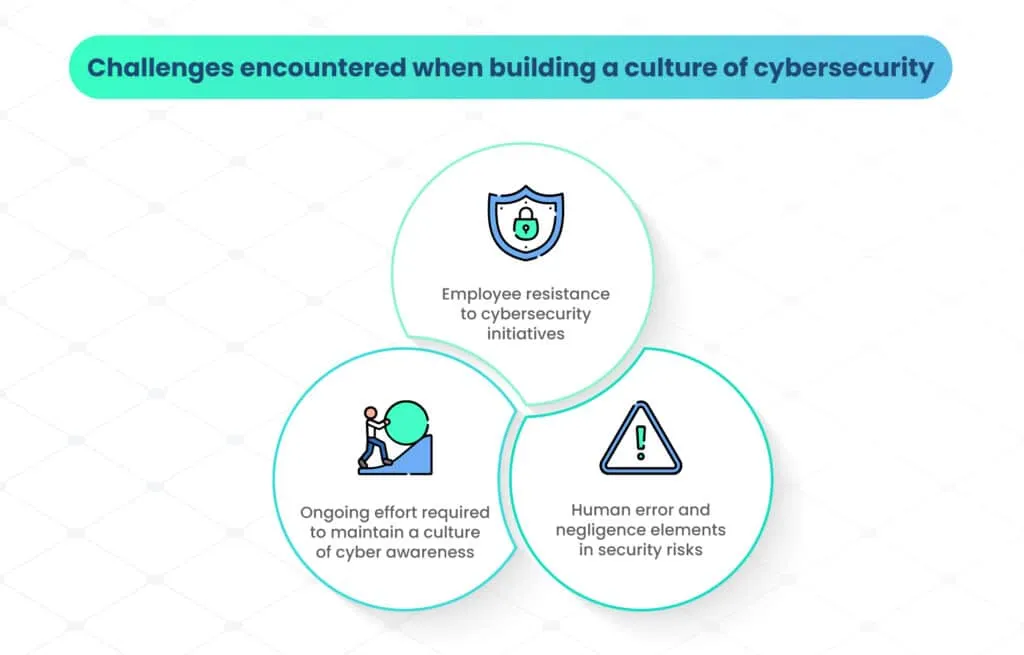
A. Employee resistance to cybersecurity initiatives
Resistance to cybersecurity initiatives can be a common challenge in building a culture of cyber awareness. Some employees may view these initiatives as cumbersome or intrusive, potentially leading to resistance.
Overcoming this resistance requires effective communication and leadership support. Explain the rationale behind cybersecurity measures, emphasizing their role in protecting sensitive data and the organization’s reputation. Show employees that these measures are not just for compliance but are fundamental to safeguarding the organization and their jobs.
B. Human error and negligence elements in security risks
Human error and negligence are significant contributors to security risks. Despite the best technical safeguards, individuals can inadvertently compromise security through actions such as clicking on malicious links or mishandling data.
To address this challenge, organizations should focus on comprehensive security awareness training. Educate employees about the potential consequences of their actions and how they can actively mitigate security risks.
C. Ongoing effort required to maintain a culture of cyber awareness
Maintaining a culture of cyber awareness is an ongoing effort. It requires continuous reinforcement and adaptation to evolving threats.
One common pitfall is assuming that once a cybersecurity culture is established, it will sustain itself. To maintain the culture, organizations should regularly update training, policies, and communication strategies.
Additionally, the cybersecurity culture should align with the organization’s overall mission and values, emphasizing that security is a shared responsibility for all employees.
In the upcoming sections, we’ll explore each of these components and challenges in more detail, offering insights and strategies to nurture a culture of cybersecurity awareness.
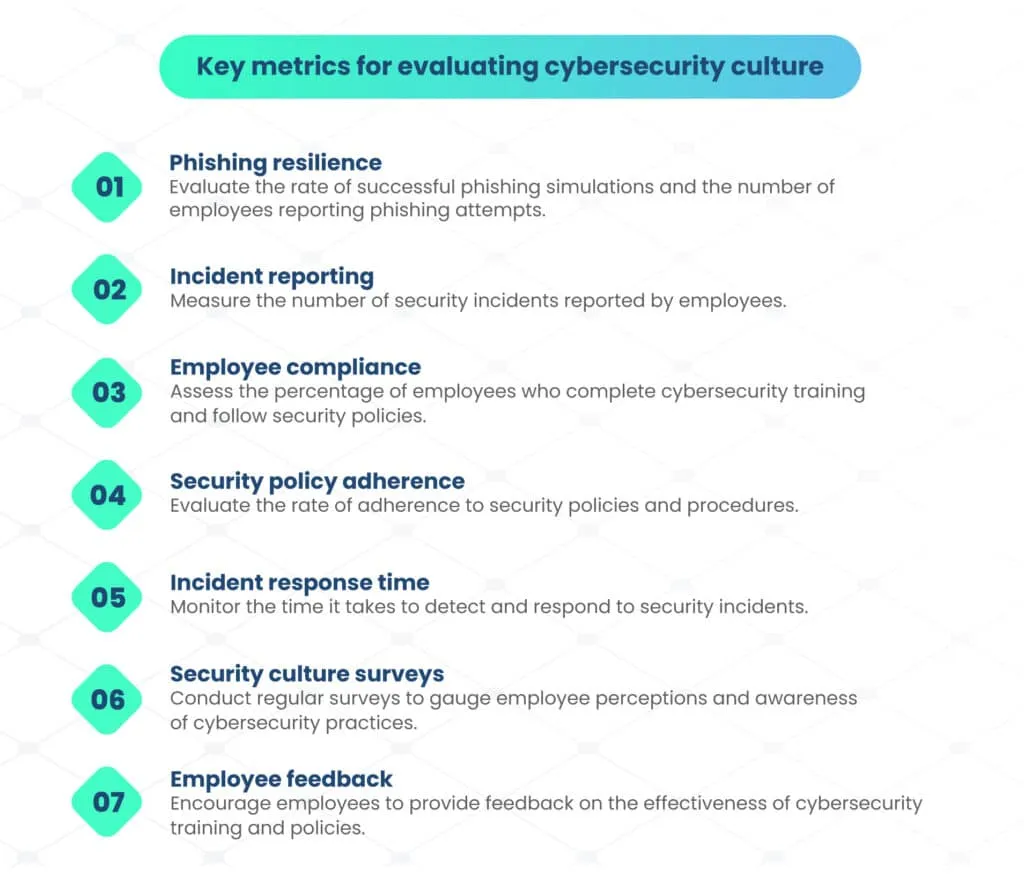
Measuring success of cybersecurity culture in an organization
Identifying and measuring the right key metrics is indispensable when evaluating the effectiveness of a cybersecurity culture in an organization, providing valuable insights into its security practices and overall preparedness.
Key metrics for evaluating cybersecurity culture
Measuring the success of your organization’s cybersecurity culture is essential to ensuring its effectiveness. Key metrics help assess the impact of your cybersecurity initiatives and employee engagement. These metrics may include:
Examples of successful cybersecurity cultures
Examining organizations with successful cybersecurity cultures can provide valuable insights into what works. Several renowned companies have excelled at nurturing a strong culture of cyber awareness.
For instance, Microsoft is known for its robust security culture, which encompasses regular training, strict policies, and a strong incident response framework.
Google is another example, emphasizing cybersecurity as a shared responsibility and fostering a culture of continuous improvement.
By studying these success stories, organizations can adapt best practices and cybersecurity strategies to enhance their own cybersecurity cultures.
Cisco Systems is renowned for its holistic approach to cybersecurity culture, emphasizing education and shared responsibility.
Adobe Systems is another company that consistently invests in cybersecurity training and communication, empowering employees to actively participate in security efforts. By learning from these examples, organizations can gain insights on the practical steps and initiatives that contribute to robust cybersecurity cultures.
Strategies for building and sustaining cyber awareness
Building and sustaining cyber awareness requires a strategic approach. To help organizations in this endeavor, experts recommend:

Building a cybersecurity culture: An ongoing journey
Nurturing a cybersecurity culture is an ongoing journey, not a one-time project. Organizations must commit to continuous improvement, adapt to emerging threats, and refine their strategies for building awareness. Success in this endeavor significantly contributes to overall cyber resilience and data protection.
Cybersecurity is not solely the responsibility of IT departments but a shared duty that spans across all employees. By prioritizing cyber awareness and investing in training, policies, and a vigilant workforce, organizations can better protect themselves from cyber threats and maintain the trust of their stakeholders.
Wrapping up
Cultivating a security mindset is an ongoing process that requires unwavering commitment from an organization. By fostering a culture where cybersecurity is embedded in the organizational DNA, organizations can significantly mitigate cybersecurity risk and ensure the safety of sensitive data.
In an era where cyber threats are ever-looming, developing good cybersecurity habits and actively nurturing a cybersecurity culture is not an option but a necessity.
In doing so, you empower your workforce to be the first line of defense against cyber adversaries, bolster your cybersecurity risk management strategies, and fortify your organization’s cybersecurity posture.
Scrut can help you with aspects of cybersecurity like employee awareness and risk management. Schedule a demo today to see how it works!
Frequently Asked Questions
1. What is a cybersecurity culture, and why is it essential for organizations?
A cybersecurity culture refers to the shared values, attitudes, and behaviors within an organization that prioritize and promote cybersecurity awareness and best practices. It is essential because it empowers employees to actively participate in protecting the organization from cyber threats.
2. What are the key components of a cybersecurity culture?
The key components include employee training and awareness, leadership commitment, clear policies and procedures, and effective communication and reporting mechanisms. These elements collectively contribute to a strong culture of cyberawareness.
3. How can organizations raise cybersecurity awareness among employees and leadership?
Organizations can raise awareness through continuous training and education programs tailored to different roles. Leadership plays a crucial role by actively supporting cybersecurity initiatives and demonstrating their commitment to a secure environment.
4. What challenges and common pitfalls should organizations be aware of when building a cybersecurity culture?
Common challenges include resistance to cybersecurity initiatives, addressing the human element in security risks, and maintaining a culture of cyber awareness over time. Organizations should be aware of these challenges to effectively address them.
5. What metrics and examples can be used to measure the success of a cybersecurity culture?
Measuring success can involve tracking metrics like phishing resilience, incident reporting rates, policy adherence, and response times. Real-world examples of companies with strong cybersecurity cultures, such as Microsoft and Google, can serve as inspiration for organizations aiming to achieve similar success.





































