Vendor Risk Management - The Ultimate Guide
.webp)
endors are a vital part of most business operations. They provide services and products that some organizations cannot do without and constitute an indispensable part of their supply chain.
Outsourcing helps organizations increase efficiency and focus on their core business functions. But it also opens doors to new vulnerabilities. When an organization uses a vendor, the vendor becomes an extension of itself and increases its attack surface.
It is extremely important to choose vendors wisely. All it takes is one bad apple to spoil a bunch, and one bad vendor to disrupt an entire supply chain by making it vulnerable to security risks.
It is crucial for companies to ensure that their vendors employ adequate cybersecurity practices in order to prevent the risk of cyber attacks as a result of their association. This makes vendor risk management a critical process for any organization.
Vendor risk management can be defined as the process of ensuring that the employment of a vendor does not pose any risks to the security of an organization or come in the way of its business performance.
This blog explores how vendor risk management can strengthen the infosec posture of an organization and suggests ways to help devise an efficient vendor risk management strategy.
What are vendors?
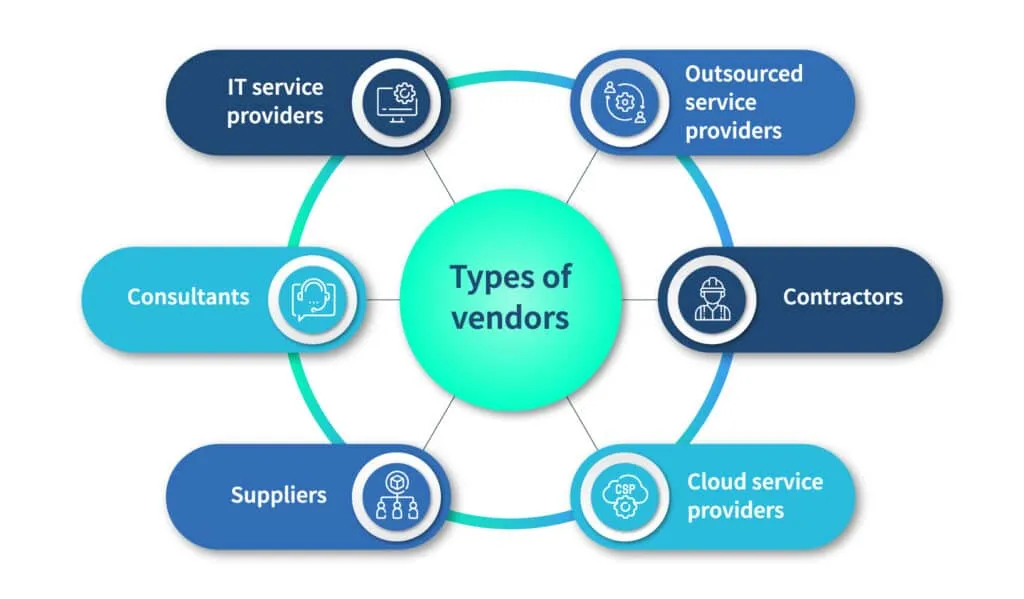
A vendor is an external party that provides services, goods, or support to an organization when it outsources its business-related tasks. Vendors work independently and are employed by organizations to fulfill specific requirements.
Name an industry, and you will find that there are multiple third-party vendors that cater to it. From healthcare to customer support, vendors offer specialized services and resources that organizations across sectors can make use of.
Some examples of third-party vendors are listed below.
IT service providers
Services such as software development, network infrastructure management, cloud computing, cybersecurity, data storage, and technical support are offered by IT service providers.
Consultants
Organizations hire management consulting firms, financial consultants, legal consultants, or subject matter experts to provide specialized services.
Suppliers
Suppliers include manufacturers, wholesalers, retailers, and distributors that provide raw materials, components, equipment, or finished goods that an organization uses for its operations.
Outsourced service providers
It is not uncommon for organizations to outsource some of their functions or processes to specialized vendors. Processes such as customer support, marketing, or accounting services can be outsourced to improve an organization's efficiency.
Contractors
Organizations may hire contractors to fulfill specific requirements that they do not have the time or skill to take on. Examples of contractors include construction companies or maintenance services.
Cloud service providers
Vendors that offer cloud-based services such as infrastructure as a service (IaaS), platform as a service (PaaS), and software as a service (SaaS) are also commonly hired by organizations to boost their business operations.
What is vendor risk management?
Vendor risk management refers to the management and monitoring of risks associated with external parties, consultants, agencies, contractors, freelancers, and other IT service providers.
Third-party vendors have the potential to introduce cybersecurity risks to an organization. Implementing a vendor risk management program equips an organization to identify potential threats posed by vendors. Assessing the security controls and practices of vendors, evaluating their data protection measures, and ensuring that they adhere to industry best practices and standards are some of the ways in which vendor risk management protects an organization from third-party dangers.
It evaluates the potential risks and benefits of working with specific vendors, implements strategies to minimize or eliminate identified risks, and continuously monitors and manages vendor relationships throughout their lifecycle. It also works to avoid legal liabilities and reputational damage that could arise as a result of associating with a less-than-diligent vendor.
From due diligence to continuous monitoring, vendor risk management is not a one-and-done process it requires constant effort to prevent and mitigate vendor risks. The process is essential for mitigating potential risks and ensuring a secure and reliable relationship with vendors and promoting business continuity.
What are the risks associated with vendors?
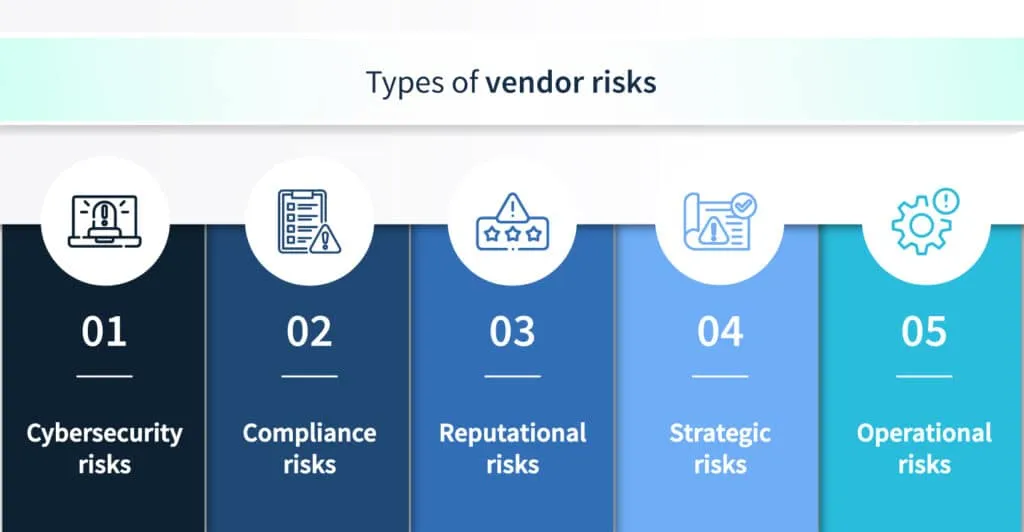
Vendors help make operations easier, but they also carry the unnerving possibility of exposing organizations to multiple risks. Just the prospect of doing business with a third party requires organizations to brace themselves against numerous dangers.
Here are some of the risks associated with hiring vendors.
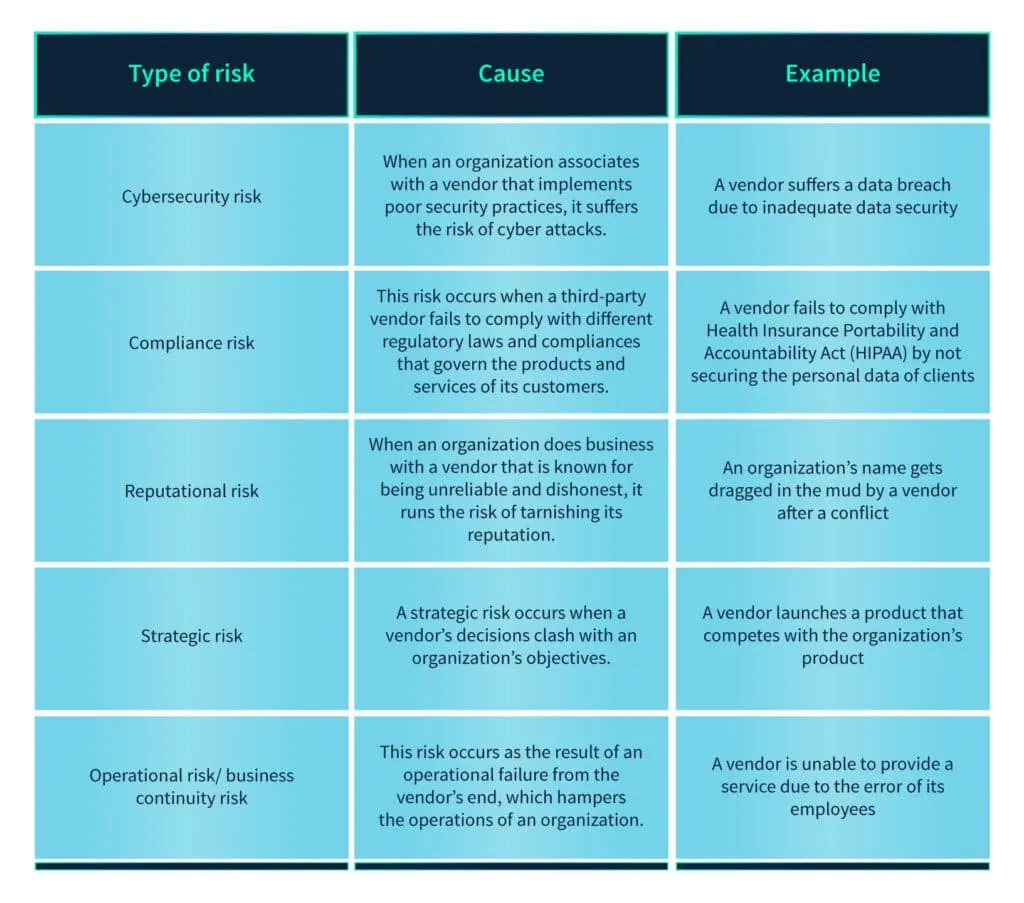
Cybersecurity risks
Though a vendor is a separate entity, when an organization utilizes its services, it becomes an extension of the company. This means that no matter how secure an organization is, if any one of its vendors does not enforce adequate cybersecurity measures, it becomes vulnerable to cyber attacks and disruptions in services. Vulnerabilities in systems or applications, weak security practices, inadequate access controls, or poor data protection measures from the vendor's end have the potential to endanger an organization's cybersecurity.
Compliance risks
When an organization associates with a vendor that does not comply with laws, regulations, or industry standards, it becomes vulnerable to compliance risks. This could result in organizations being slapped with legal consequences, reputational damage, or financial penalties.
Reputational risks
Associating with vendors who have a poor reputation could result in an organization harming its own reputation. It becomes guilty by association if its vendor practices poor security measures or violates regulations. A fallout with a vendor could lead to the organization being badmouthed by the vendor. All these risks could lead to customers, partners, and stakeholders losing trust in the organization.
Strategic risks
When a vendor's strategies clash with the objectives of an organization it has the potential to hamper the organization's business outcomes. For instance, if the vendor launches a product that competes with the organization's product, it negatively impacts the organization's sales.
Operational risks/business continuity risks
An organization's operations may be disrupted when its vendor suffers operational challenges. For instance, if the vendor's employees go on a strike or if the vendor faces a power outage. This results in the organization's productivity taking a hit.
What is the importance of vendor risk management?
In today's complicated threat landscape, every decision an organization makes has to be viewed from a security standpoint, and the possible risk that every resource carries should be assessed and monitored. Even the employees of an organization should be considered potential threats to its security.
In such a scenario, external parties, such as vendors, have to be handled with even more care. When an organization outsources operational tasks, sharing access to some of its confidential data with a vendor is inevitable. This increases the risk of data being leaked or misused.
When an organization engages vendors who implement poor security practices, it makes its own security posture vulnerable.
The rise in regulatory expectations around third-party risk management processes also calls for organizations to continuously monitor and manage the potential risks of their vendors. Information security frameworks such as Payment Card Industry Data Security Standard (PCI DSS) and ISO 27001 enforce risk management policies that concern third-party vendors.
All these reasons make third party vendor risk management a dire need when it comes to doing business with vendors.
What are the benefits of vendor risk management?
An effective vendor risk management program makes all the difference when it comes to reaping the benefits of vendor services without the hassle of vendor risks.
It can mitigate the impact of events that could disrupt an organization's supply chain and also improve the company's security posture. It enables organizations to track the evolution of their supplier relationships, identify new risks, and assess supplier performance. On the whole, it helps organizations fulfill their agendas efficiently without any hindrance caused by vendors.
Here are some of the many benefits that a good vendor risk management program can offer to an organization.
Mitigates risks
Vendor risk management helps organizations identify vulnerabilities, security gaps, or compliance issues through risk assessments and due diligence, and helps in mitigating these risks through the implementation of necessary controls and remediation measures. This reduces the likelihood of disruptions, security incidents, or regulatory non-compliance caused by vendor risks.
Boosts security
Since third-party vendors could potentially harm the security of an organization, vendor risk management focuses on assessing and mitigating their potential risks. It does this by evaluating the security practices, controls, and data protection measures of vendors. By ensuring that vendors meet the organization's security requirements, vendor risk management helps in reducing the risk of data breaches, unauthorized access, and other security incidents.
Maintains compliance
If a vendor does not adhere to data privacy regulations, financial regulations, or industry-specific standards, it exposes the organization that uses its services to compliance risks. Vendor risk management helps in determining if vendors comply with applicable regulations to save organizations from the horrors of reputational damage, penalties, and loss of customer trust.
Ensures business continuity
Disruptions in a vendor's operations can negatively impact an organization's operations. Vendor risk management helps in zeroing in on potential vulnerabilities in the vendor's operations. It implements appropriate risk mitigation strategies so that the organization can address these risks and reduce disruptions caused by vendor-related issues, ensuring business continuity.
Saves costs and increases efficiency
A good vendor risk management program can help in saving costs and increasing efficiency. Conducting thorough vendor assessments and due diligence helps organizations select vendors that meet their requirements and align with their business objectives. This does away with the unwanted loss of money and time that comes as a result of engaging unreliable vendors. Establishing clear contractual terms, service level agreements, and performance monitoring mechanisms helps in ensuring that vendors meet or exceed expectations and optimizes cost and resource allocation.
Protects reputation
Vendor risk management assesses the reputation and track record of vendors before entering into a contract with them. It monitors vendor activities and puts in place incident response plans that help in protecting the organization's reputation and maintain the trust of its customers and stakeholders.
What is vendor risk management policy?
A vendor risk management policy identifies and sets apart vendors who pose a risk to an organization's operations. This includes vendors who collect sensitive data, have access to internal networks, or perform critical functions.
The vendor risk management policy helps an organization reduce risk and adhere to compliance frameworks such as Service Organization Control Type 2 (SOC 2), HIPAA, and General Data Protection Regulation (GDPR) by establishing certain controls.
How to build a vendor risk management policy
Here are 4 steps you can follow to build an effective vendor risk management policy.
Identify high-risk vendors and audit their access
Start by identifying vendors that pose a high risk to your organization based on factors such as the necessity of their services, the sensitivity of the data they handle, or the possible impact of their actions on your operations. Conducting a thorough vendor assessment helps in determining the level of risk they pose. Their financial stability, reputation, security practices, compliance with regulations, and past security incidents should also be taken into account during the assessment.
It is very important to audit the access of vendors. They should only be given access to the systems, data, or facilities that they require for their services. It is crucial to review and validate their access rights to prevent unauthorized activities or data breaches.
Assign a risk score to each vendor and establish various levels of risk
Assigning a risk score to each vendor helps in planning the focus of risk management efforts and allocating resources accordingly. The risk-scoring methodology should take into account factors such as the criticality of services, sensitivity of data shared, security controls, regulatory compliance, and incident response capabilities.
High-risk vendors would require stricter controls and monitoring, while lower-risk vendors would require less effort.
Create procedures and policies for each risk level
Procedures and policies should be tailored to each risk level. High-risk vendors require stringent due diligence, contract negotiations, and ongoing monitoring. Policies and controls should cover data protection, encryption, security assessments, business continuity plans, incident response protocols, and regulatory compliance.
Lower-risk vendors require less stringent procedures and policies, and standard contracts can be used for them, without the need for special provisions.
Update and monitor risk management policies regularly
Vendor risk management policies should evolve with the vendor landscape and its associated risks. This makes it important to review and update policies regularly. Being aware of emerging threats, regulatory changes, and industry best practices helps in making necessary changes.
What is a vendor risk management framework?
A vendor risk management framework consists of processes that help organizations effectively manage their supplier relationships, optimize their operations and reduce risk across their supply chains.
An effective vendor risk management framework will cover the entire lifecycle of third-party vendor risk management, starting from vendor selection to the continuous monitoring and risk assessment of the vendor. It streamlines the entire vendor risk management process.
How to create a vendor risk management framework
Below are some steps you can follow while creating a vendor risk management framework for your organization.
Identify and outline challenges associated with vendors
It's important to identify and outline the specific challenges and risks associated with hiring vendors. Conducting a thorough assessment of the vendor ecosystem and identifying potential vulnerabilities, security risks, compliance issues, or operational challenges that may arise from vendor relationships can help organizations develop strategies to address and mitigate them effectively.
Make sure that all employees are on the same page when it comes to vendor management
Effective vendor risk management is a combined effort that requires commitment from all employees involved in the vendor management process such as personnel from procurement, legal, IT, security, and other relevant departments. It is necessary to create clear policies, procedures, and guidelines for vendor management, and ensure that employees receive training and awareness about their roles and responsibilities in managing vendor risks. Proper communication between different departments is crucial for consistent vendor risk management efforts.
Ensure that vendors conduct internal audits of their infosec programs
It's important to request vendors to conduct internal audits of their information security programs to assess their security posture. Evaluating their security controls, policies, incident response capabilities, and compliance with relevant standards or frameworks will help in gauging how effective their infosec program is. Vendors should be asked to submit the results of their internal audits for review. This will help in gaining insights into their security practices, identifying any gaps or areas of concern, and working collaboratively with the vendor to address the issues.
Establish how and when monitoring takes place and how risks are identified and avoided
Monitoring vendors is an essential part of vendor risk management. It is necessary to establish clear processes and mechanisms for ongoing monitoring of vendor activities, performance, and compliance. Regular assessments, audits, or reviews of vendors will ensure that they consistently meet the organization's requirements and adhere to its terms.
Defining key performance indicators (KPIs) or metrics that help track and measure vendor performance and compliance will also help in ensuring that vendors deliver what is required while adhering to relevant regulations. Implementing a system for identifying and escalating risks associated with vendors in a timely manner will help mitigate risks and reduce their negative impact on the organization.
What is a vendor risk management maturity model?

A vendor risk management maturity model (VRMMM) is a useful tool for evaluating the maturity of a third-party risk management program by assessing its cybersecurity and business resilience.
It helps organizations to develop a strategy to make their vendor management program robust. A good VRMMM will assess the overall vendor risk management framework by reviewing how risk is being managed and provide guidelines on how to further reduce risks.
VRMMM is one of the best risk management tools for risk managers, as it lets them evaluate their program against a comprehensive set of best practices. It uses governance as its basis and identifies the best steps for effective vendor management risk assessment.
Its practices are adaptable across industries. The tool also helps companies figure out how much resources to allocate to the program. It can be used to determine the level of maturity of the current or future state of an organization's risk management program.
The maturity levels are as follows:
- Initial visioning: No processes are defined at this level.
- Approved roadmap: Processes are defined in this stage.
- Determined and established: The processes are well-defined and established.
- Fully implemented and operational: Compliance measures are carried out and plans for monitoring and governance are defined.
- Continuous improvement: The best practices are employed at this level, and it is defined by the use of automation for continuous improvement.
An efficient risk management program will swiftly transition from the initial level to the level of continuous improvement.
How to manage vendor risks effectively through vendor risk management

Comprehensive vendor risk management will help an organization proactively identify, assess, and mitigate the risks associated with engaging third-party vendors. Overall, it will ensure that the organization's security, compliance, and risk posture are effectively managed.
Here is a step-by-step guide on how to manage vendor risks effectively.
1. Create a comprehensive program
The first step to implementing an effective risk management program is to outline its objectives, scope, and responsibilities. The key stakeholders involved in the process, such as procurement, IT, security, legal, and compliance teams should be clearly defined.
2. Categorize and prioritize vendors
Vendors should then be categorized based on their criticality and the level of risk they pose to the organization. Factors such as the nature of the services provided, access to sensitive data, business impact, and regulatory requirements should be taken into account. Prioritizing vendors based on their risk level helps in allocating resources effectively.
3. Conduct due diligence
It is important to conduct thorough due diligence during the vendor selection process. Vendors should be evaluated against predefined criteria, such as financial stability, reputation, security controls, regulatory compliance, and references. It is advisable to document the due diligence process and maintain records for future reference.
4. Assess risks
A comprehensive risk assessment of selected vendors should then be carried out. Their information security controls, data protection practices, vulnerability management, incident response capabilities, and compliance with relevant regulations should be evaluated. Potential risks and vulnerabilities associated with their systems, processes, and access to sensitive data should also be identified.
5. Create comprehensive contracts
Vendor contracts should contain specific clauses and provisions to address risk management. Data protection requirements, security standards, access controls, notification of security incidents, indemnification clauses, liability limitations, termination conditions, and compliance obligations should be included. Legal and procurement teams should be involved to ensure that contracts align with the organization's risk tolerance and compliance requirements.
6. Maintain ongoing monitoring and performance management
A process for ongoing monitoring of vendor performance and compliance should be implemented. Metrics and KPIs to assess vendor adherence to contractual obligations, service level agreements, and security controls should be defined. Vendor performance should be reviewed regularly and periodic audits should be conducted to verify that they are compliant with security and regulatory requirements.
7. Create incident response and business continuity procedures
Incident response procedures that outline the steps to be taken in the event of a security incident or disruption caused by a vendor should be created. Roles and responsibilities, communication channels, incident escalation procedures, and coordination with the vendor during incident response efforts should be defined. Provisions for business continuity planning to safeguard operations in case of vendor-related incidents should also be established.
8. Develop a process for vendor offboarding
Terminating vendor relationships or transitioning to alternate vendors should be carried out carefully. Data transfer or destruction, removal of access rights, and returning or securely disposing of any organization-owned assets in the vendor's possession are crucial steps in the process of severing ties. Exit assessments should be conducted to ensure a smooth transition and to mitigate any risks associated with vendor offboarding.
9. Maintain documentation
It is vital to maintain comprehensive documentation throughout the vendor risk management process. Vendor assessments, risk assessments, contracts, monitoring activities, incident response efforts, and vendor performance evaluations should be documented for future reference. Regular reports for stakeholders, including management, auditors, and regulators, to demonstrate compliance with regulatory requirements and adherence to risk management practices should be maintained.
10. Regularly update the program
The vendor risk management program should be reviewed and updated regularly to address emerging risks, regulatory changes, and findings from risk assessments. Feedback from stakeholders and industry best practices should also be taken into account to increase the effectiveness of the program.

The benefits of automating vendor risk management
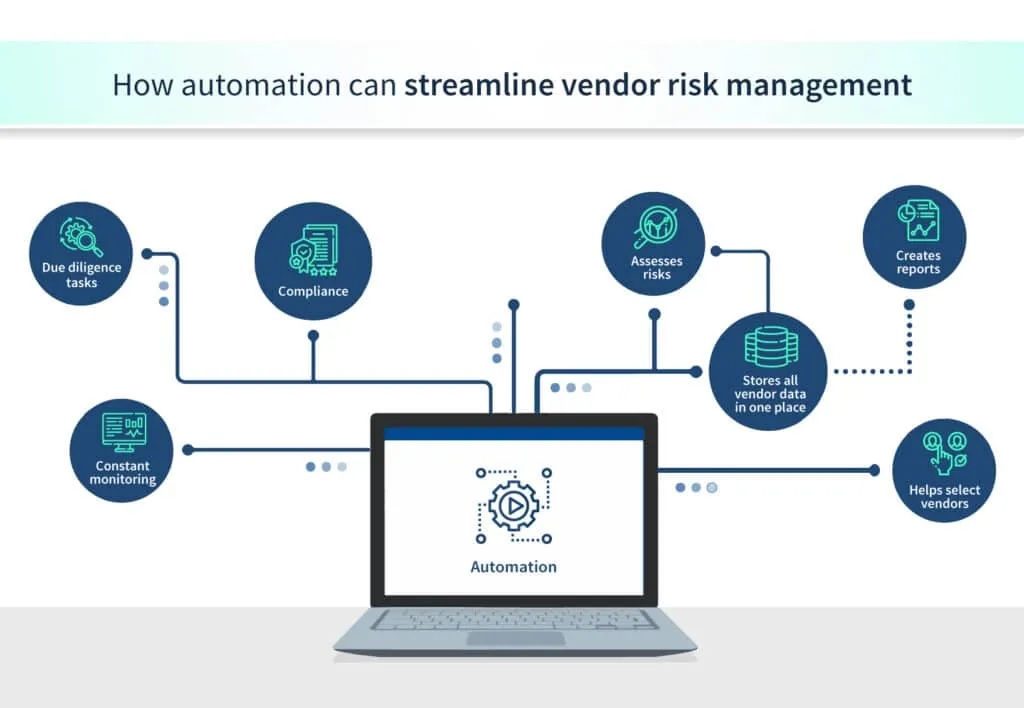
Using vendor risk management software is one of the best ways to streamline and strengthen a vendor risk management program. Such software help in the collection and management of vendor risk data. It safeguards organizations from security incidents caused by the non-compliance of vendors.
Vendor risk management software help in streamlining vendor compliance assessment by storing all the vendors' data in one window and assessing their risk by analyzing security reviews.
A good vendor risk management solution should be scalable, centralized, and consistent to keep up with a dynamic environment.
The key benefits of vendor risk management software are listed below.
Automates processes
A good vendor risk management software automates tasks associated with due diligence and constant monitoring. This reduces the need for manual effort and frees up time for employees to work on other important tasks.
Ensures compliance
Vendor risk management software can help in determining if a vendor is compliant. By screening non-compliant vendors, they help organizations to avoid the payment of fines and penalties and help them protect their reputation.
Creates reports
Reports that address various vendor-risk data points, such as new issues or areas of concern, can be generated by vendor risk management tools with ease. This helps in keeping the vendor risk management program updated.
Choosing a vendor risk management tool
From managing vendor portfolios to calculating risk scores, there is a lot that a good vendor risk management tool can do. It is important to consider the following before zeroing in on software.
- It is necessary to determine if the information security team has the budget and resources to carry out an effective risk management program.
- Ranking the program on the vendor risk management maturity model is important in knowing where the program stands.
- All current vendor issues and risk areas in the vendor risk management lifecycle should be taken into consideration.
How can Scrut help with vendor risk management?
Scrut's vendor risk management tool provides a comprehensive understanding of who an organization's vendors are, how they manage their risks, and the potential effects they have on its business.
It is a rapid, effective, and efficient tool, which evaluates, monitors, and manages vendor risks in a single window. It helps in gaining valuable insights into the vendors' security posture and determines if it aligns with the organization's expectations.
The key features of the tool are listed below.
Automates vendor audit programs
It automates vendor audit programs, saving time and effort while ensuring comprehensive assessments of vendor risk profiles.
Effortless vendor management
It simplifies the vendor management process by developing tailored programs for vendors across different risk levels.
Offers an intuitive dashboard for vendor comparison
It compares vendor responses effort.


















