Choose risk-first compliance that’s always on, built for you.
Go back to blogs
Risk Management in Cloud Computing
Last updated on
September 27, 2023
min. read

The organization is vulnerable to various threats that jeopardize operational efficiency and regulatory compliance. To stay ahead of these risks, simple awareness is insufficient. This is where enterprise risk management (ERM) comes into the picture. It assists you in managing, minimizing, and in some cases eliminating risks in order to keep your organization safe and operational.
A risk is the possibility of losing, damaging, or destroying your assets or data due to a threat. It refers to events or actions that jeopardize the organization’s goals.
Enterprise risk management (ERM) is a comprehensive and disciplined approach to identifying, addressing, and managing organizational risks. ERM is a top-down strategy aimed at identifying, assessing, and preparing for potential losses, dangers, and hazards that may disrupt an organization’s operations. It addresses an organization’s risks by breaking down silos within each business unit.
Cloud computing is a model that allows a company to access its resources and applications from any location with an internet connection. Technology has advanced rapidly in recent years, providing numerous benefits to businesses and individuals.
Organizations are increasingly investing in cloud deployment infrastructure rather than on-premise infrastructure. However, rapid cloud computing development has created numerous issues, such as compliance risks, cybersecurity risks, cloud vendor risks, malicious insiders, data security risks, etc. As technology is mobilized, new risks are introduced associated with cloud computing, which must be considered with foresight. Organizations are more vulnerable to security threats due to cloud computing. Because the cloud introduces more third-party risks, effective risk management becomes critical. Organizations must ensure that their cloud provider maintains the appropriate data security and regulatory compliance measures to meet their specific needs. The risk management plan in cloud computing assists in identifying appropriate cloud service providers and develops better budgeting plans.
Example of a data breach – Capital One, for example, experienced a data breach of 109 million financial records in 2019 due to an attacker exploiting the cloud-based storage provider Capital One used.
Example of data loss – In 2015, a severe lightning strike that hit a facility four consecutive times permanently damaged Google servers at a cloud storage system in Belgium.
Types of Risks in Cloud
Below are some of the types of enterprise risks in cloud computing.
- Compliance risk – Compliance risks arise from failing to adhere to the standards of several industry rules, such as HIPAA, SOC 2, GLBA, GDPR, etc. The cloud service provider may not follow the external audit process, exposing the end user to compliance risks. While most leading cloud providers have progressed toward certification with widely used cybersecurity frameworks, organizations must still verify that their processes and systems are compliant.
- Data breach – The risk of data leakage increases in the cloud due to shared infrastructure between service providers and their clients. A data breach occurs when a third party gains unauthorized access to an organization’s confidential data. In cloud computing, the organization’s data is stored outside the premise at the endpoint of the cloud service provider. As a result, any attack on data stored on CSP servers may affect all its users.
- Cloud vendor security risk – An association with a vendor or leverage can lead to vendor risk. Every organization uses cloud services provided by different cloud vendors. The cloud vendors’ inability to provide data security and risk mitigation directly affects the organization’s growth. Defamation of third-party vendors, bankruptcy, regulatory investigations, and even lawsuits can significantly impact an organization’s reputation.
- Misconfiguration – Incorrectly configured cloud security settings are a major cause of cloud data breaches. Misconfiguration of your cloud environment refers to any flaws, gaps, or errors that could expose your environment to risk.
Cloud Computing Risk Management Best Practices
An enterprise risk management tool assists organizations in developing procedures to prevent potential threats and reduce their impact if they occur. We have listed some of the important factors for implementing enterprise risk management.
Determine your business goals
Before deciding whether a risk should be accepted or rejected, you must consider your business objectives. Understanding organizational objectives before risk assessment increases the value of the risk mitigation process.
Some key questions you need to ask:
- What kind of data do cloud users access, store, and transmit?
- What is your risk appetite?
- What is your organization’s primary need?
- What new areas of risk could emerge?
- Do you have authority over the security of access devices?
Risk identification
The identification of risks is the first step in risk management. Identifying the scope and nature of your organization’s risks is critical for risk management. Identifying risks involves reviewing IT assets such as systems, devices, data, software, networks, and vendors.
Now, let’s understand this with the example of our Scrut platform.
Scrut automatically identifies risks in your ecosystem by scanning the code base, infrastructure, applications, vendors, employees, access, and more. The platform allows you to create a risk register in minutes. You can use Scrut’s pre-mapped risk library.
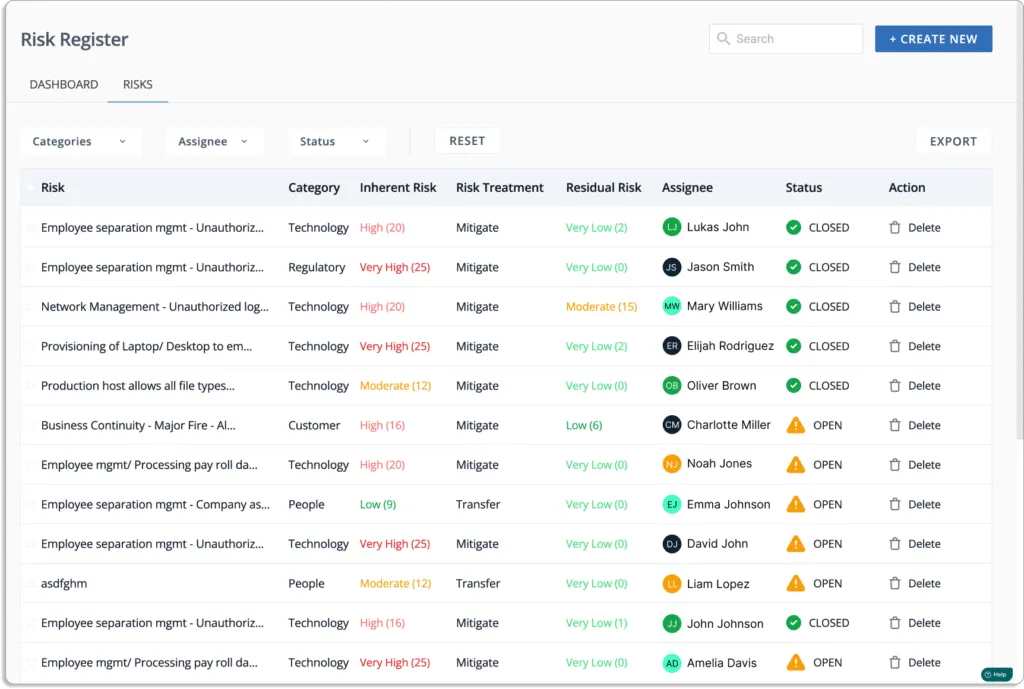
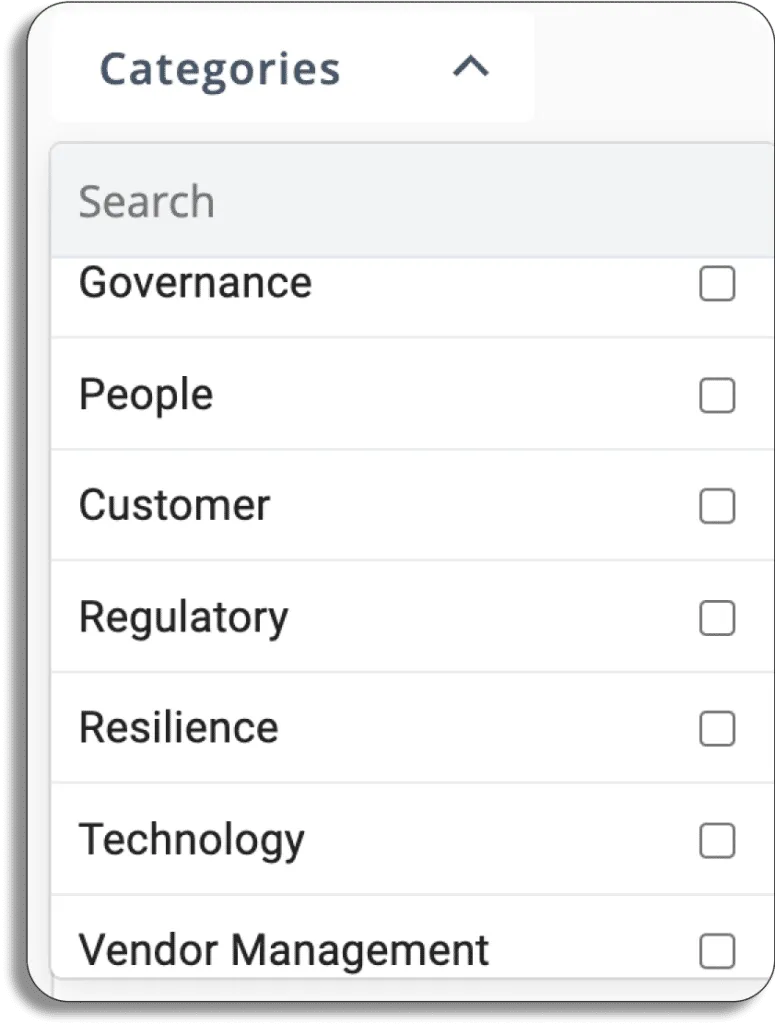
It allows you to choose from seven risk categories. You can filter types based on your needs.
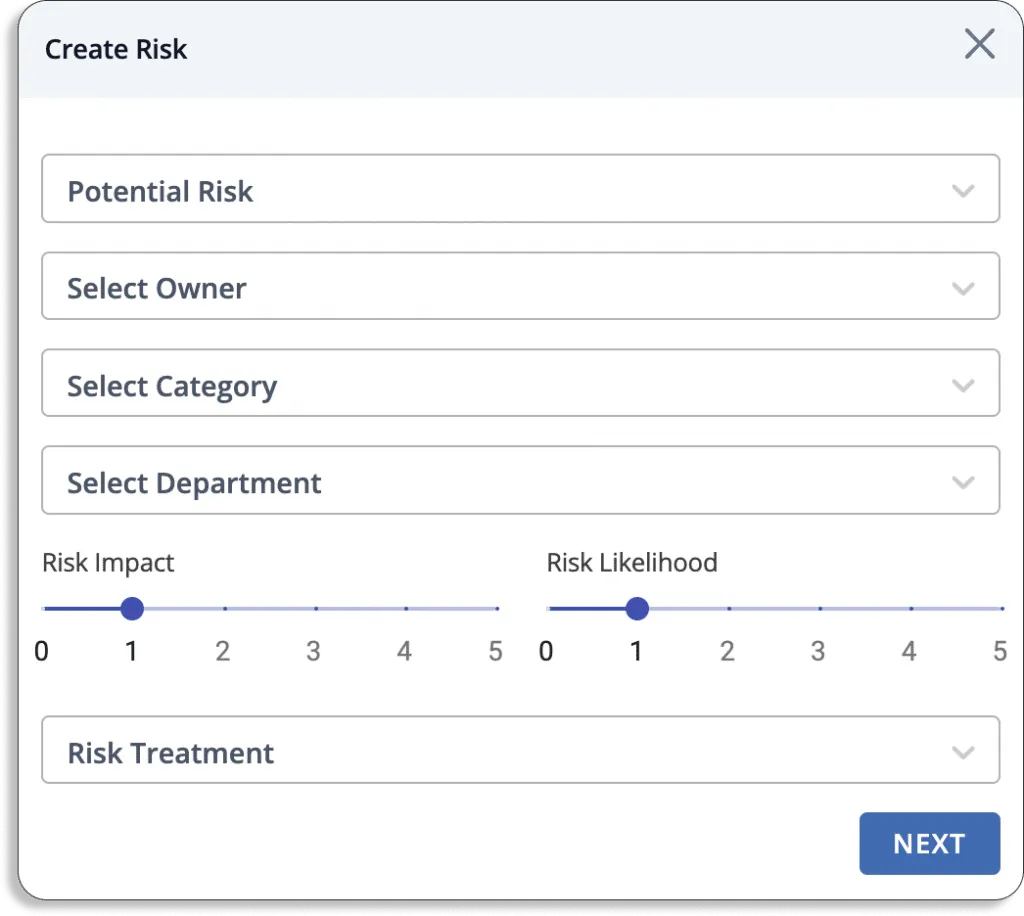
Scrut also lets you create custom risks, as shown in the screenshot below.
Risk assessment
Following risk identification, the risk must be assessed. In this step, the likelihood and consequences of the risks are determined. The risks are further classified (high, moderate, or low) based on the severity of the impact they have on information security and the likelihood of occurring.
Scrut allows you to evaluate your risk profile using automated risk scoring. The platform generates risk scores based on the likelihood and impact of events.
- Likelihood – the probability of occurrence of the risk.
- Impact – the potential impact of a risk event on the business.
Let’s take an example of change management risk, as shown in the screenshot below.
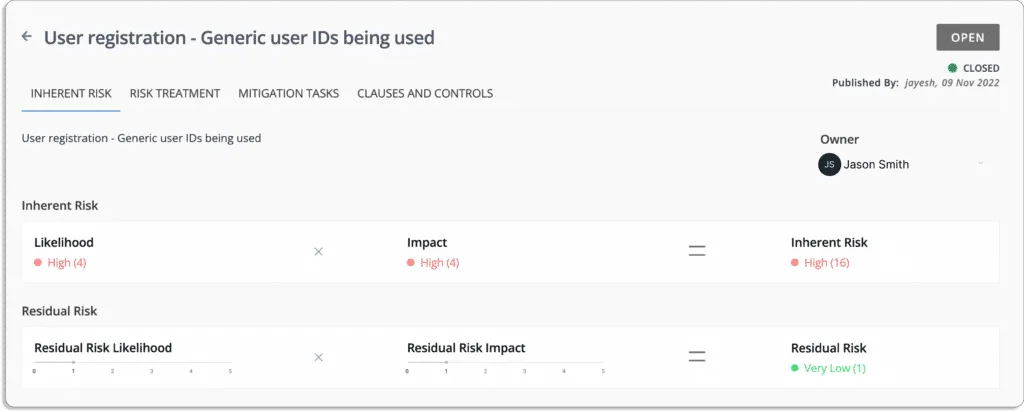
The likelihood of this event = 5 (very high)
The impact in case the event occurs = 4 (high)
Thus, the inherent risk associated with this event = 20 (high)
Risk = Likelihood * Impact
Risk = 5 * 4 = 20
The final score lies between 0 – 25.
Risk Remediation
The next step after a risk assessment is to work on the risk. The highest-ranked risks are treated in this step to eliminate or modify them to an acceptable level. The security controls are implemented in the cloud system and evaluated using proper procedures to determine whether the controls are effective in producing the desired outcome.
Continuing with Scrut, as an example– you can select your risk treatment plan as accept, mitigate, transfer or avoid.
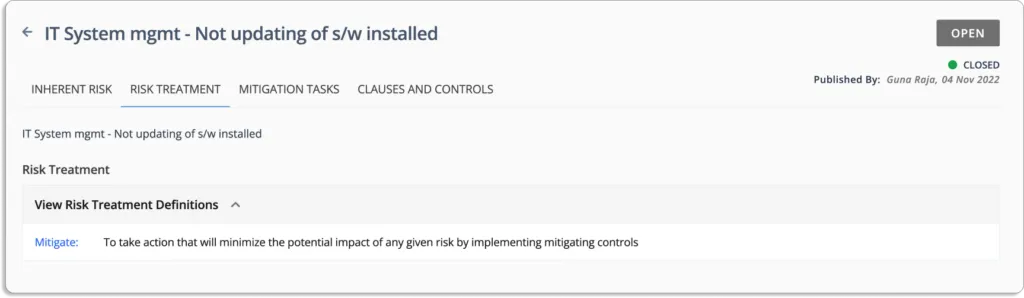
Scrut offers four options for dealing with the risk. Each risk can be ignored, accepted, transferred, or mitigated.
- Risk Remediation – eliminate the risk.
- Risk Mitigation – minimize the impact or likelihood of the risk.
- Risk Transfer – transfer the risk to another party.
- Risk Acceptance – accept the risk.
As shown in the screenshot below, you can also create mitigation tasks.
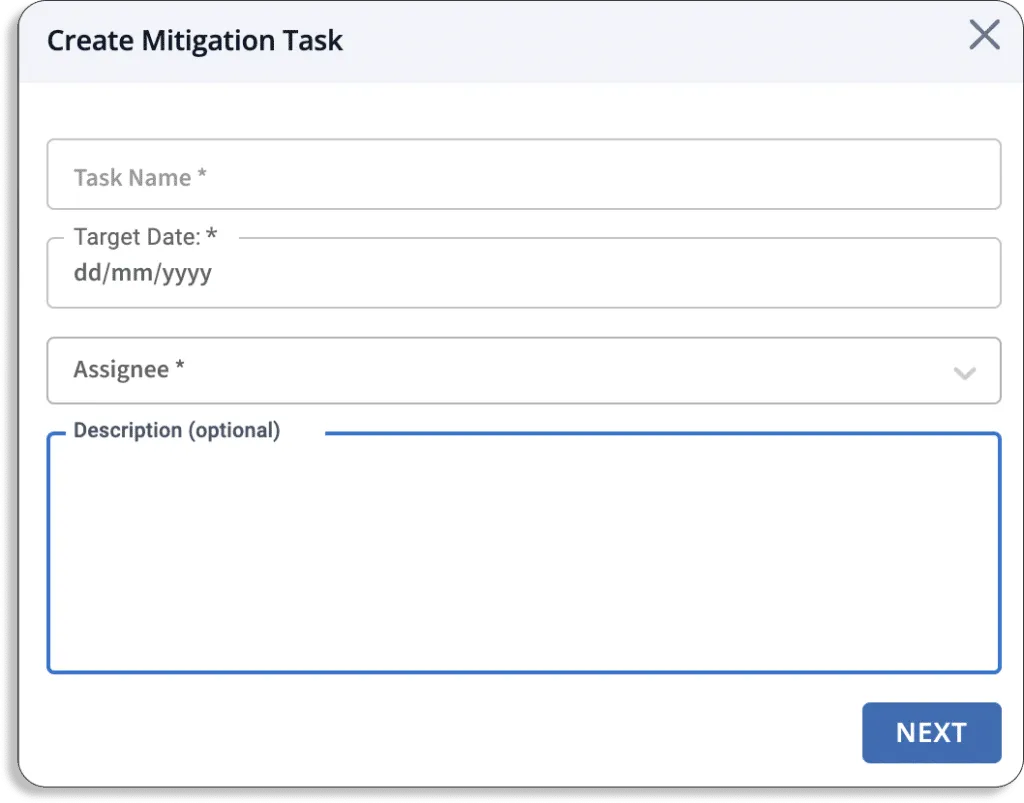
With Scrut, you can also assign risks to the team members for risk treatment.
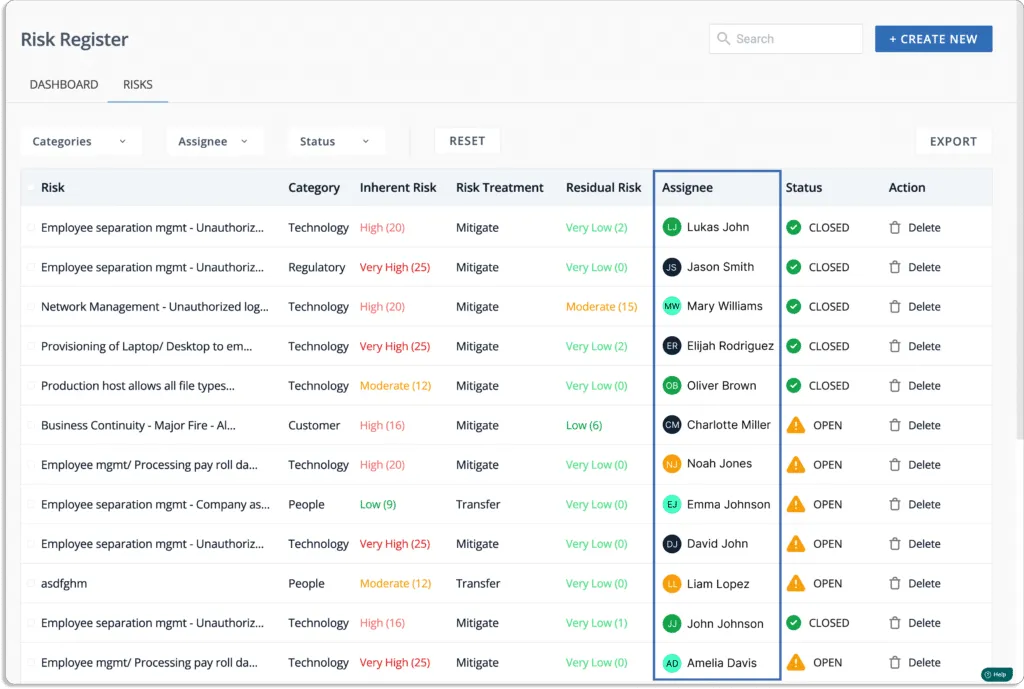
Cloud monitoring capability
Risk management extends beyond the initial deployment of cloud services. During the operational phase of cloud services, you must ensure that tools for continuous monitoring are in place. An effective enterprise risk management tool should provide continuous CIS benchmarking. The Center for Internet Security Foundations Benchmarks covers access control, identity management, logging, monitoring, networking, and other topics. Scrut not only assists you in becoming compliant, but it also assists you in remaining compliant. Scrut automatically compares your cloud configurations to 200+ cloud control across CIS benchmarks to ensure a strong information security posture.
As shown in the screenshot below, our platform detects gaps and critical issues in real time.
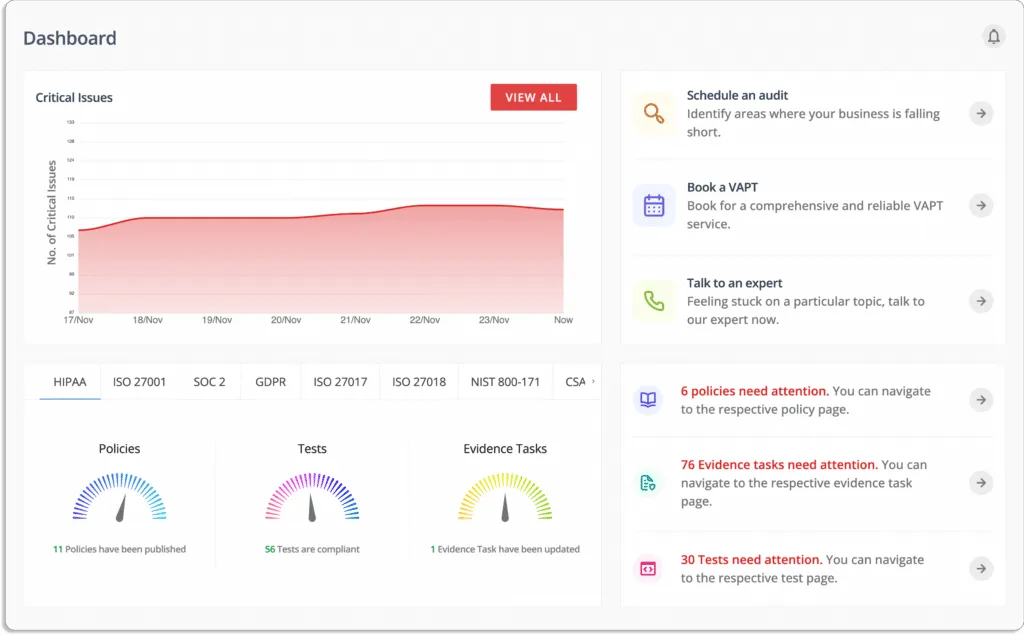
Scrut cloud security regularly audits your cloud accounts for security risks, misconfigurations, and control threats across hundreds of configuration settings. It reduces your exposure to risk and compliance across all public cloud accounts. You can efficiently prioritize your work with Scrut’s automated status classification, as shown in the screenshot below.
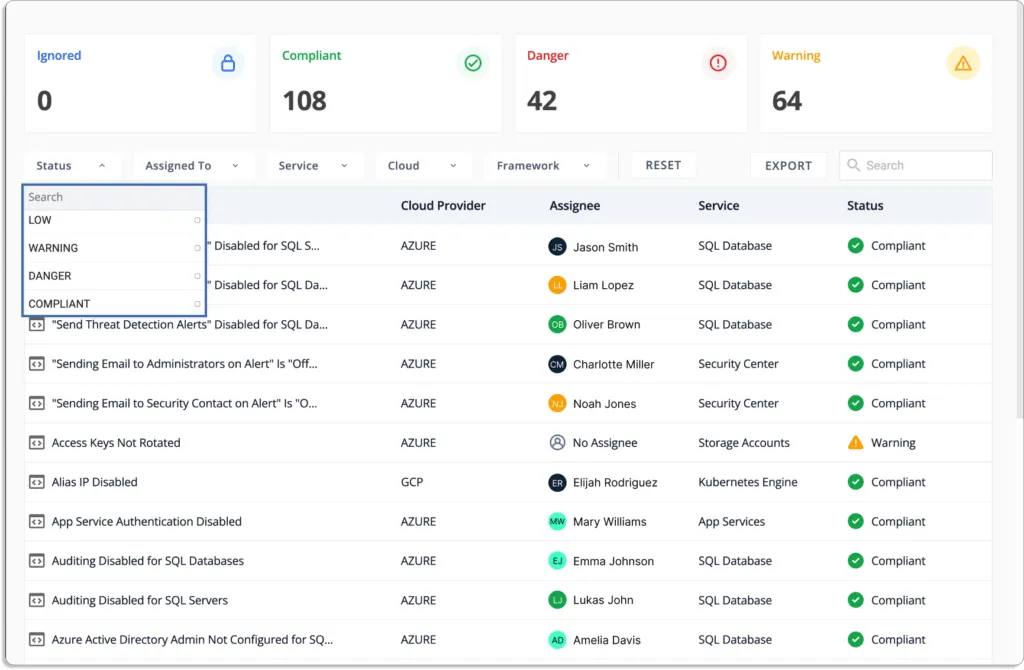
- Danger – The most urgent problems.
- Warning – You can proceed to these after dealing with the problems labeled “danger.”
- Low – These risks are of low importance and can be handled last.
- Ignored – You can override an ignored status.
- Compliant – No problems at all. Nothing needs to be done by you.
Whenever there are any issues in your cloud environment, Scrut provides real-time notifications (email, Slack, etc.). Further, you get tools and guidance within the platform that help you quickly remediate the issues.
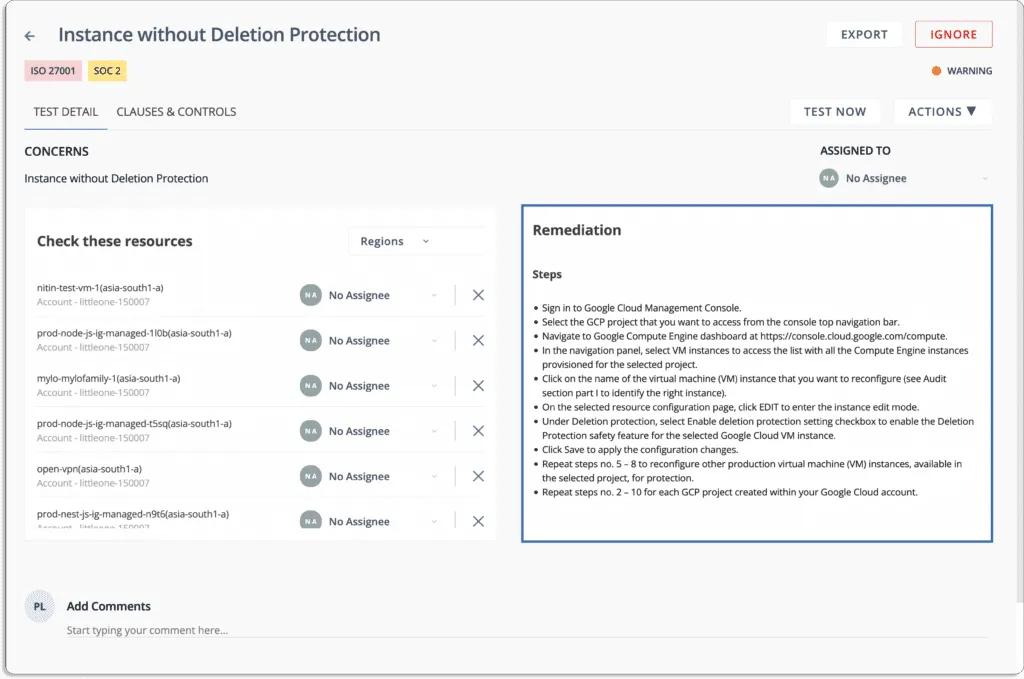
Moreover, you can ensure accountability for fixing these by assigning ownership to different individuals for every task.
Policies and compliance requirements
All organizations should have policies to prevent and detect unauthorized procurement and use of cloud services. The compliance audit process is difficult due to the lack of visibility in ever-changing cloud environments. You must first determine which standards apply to your industry and which your organization must meet.
Scrut policy library contains 50+ prebuilt policies, as shown in the screenshot below. These policies were developed in collaboration with information security experts and lead auditors.
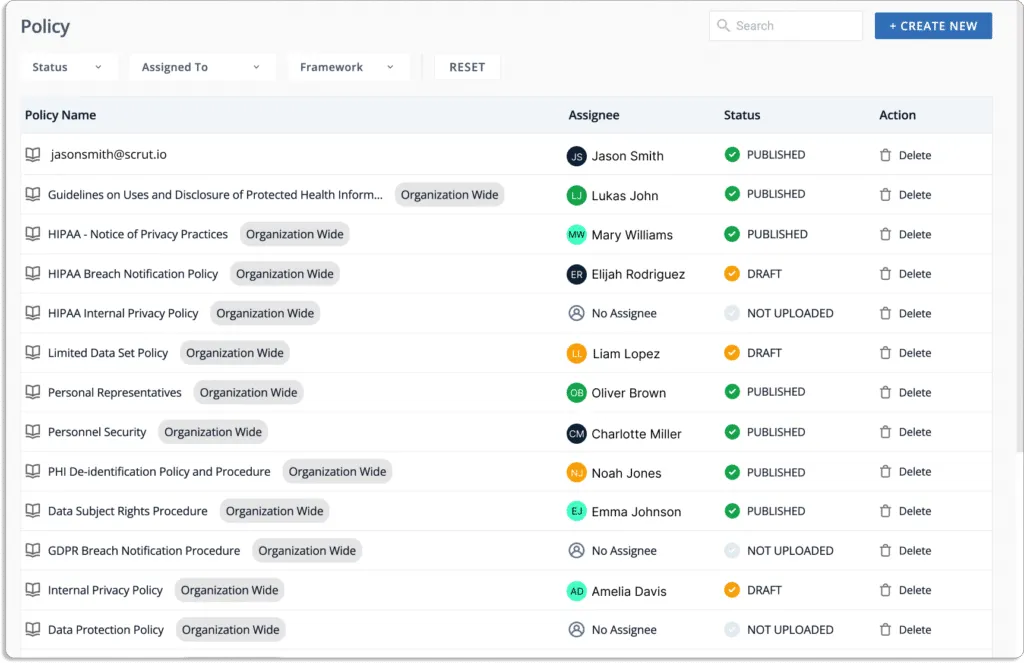
These policies are mapped to different compliance frameworks for your understanding.
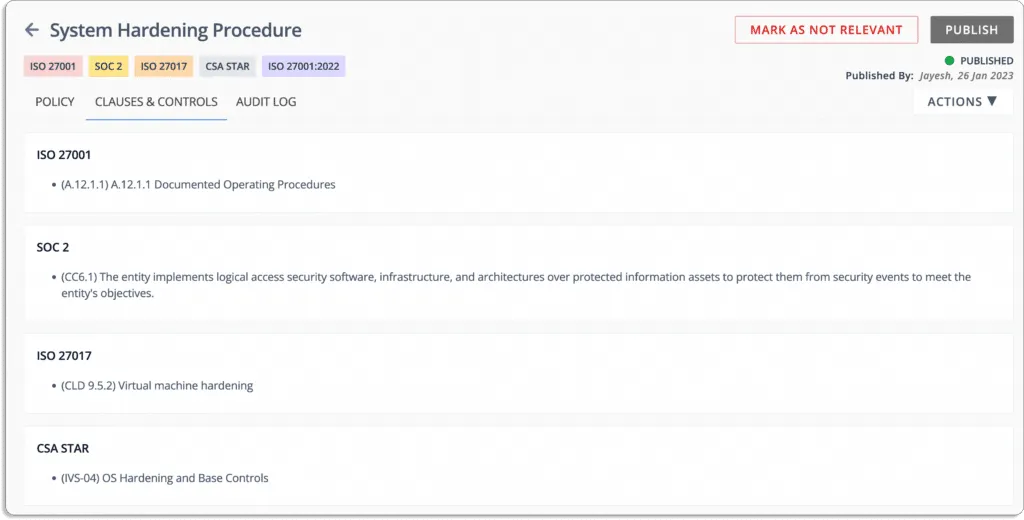
The tool ensures that your compliance posture has no missed checks or misconfigurations. Scrut risk management maps all the risks to compliance frameworks automatically. With Scrut, risks are pre-mapped to controls across popular frameworks such as ISO 27001, HIPPA, SOC 2, and others. You can maintain compliance without having to go through thousands of risk sources.
Vendor management
The presence of third-party vendors in cloud business models has raised security concerns. Vendor risk management is essential for protecting an organization’s customers and all proprietary information. With Scrut, you can compare vendors to find the least risky business partner.
As shown in the screenshot below, you can use pre-made templates or create your questionnaire.
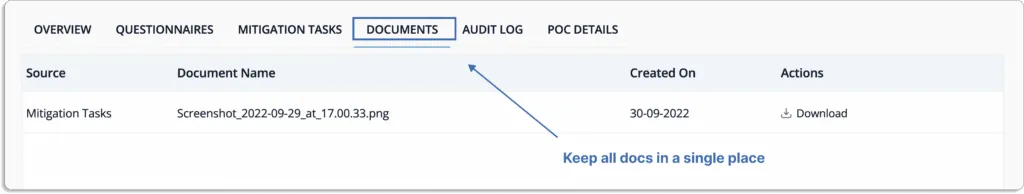
Scrut keeps all vendor security certifications, software vendor audits, and paperwork in one place, as shown in the screenshot below.
Employee training
Security awareness training for employees is one of the major use cases of enterprise risk management. Data breaches, cloud vendor security issues, and misconfiguration are some issues that organizations face. The best way to avoid this is to guide your employees’ standard security practices by following basic security guidelines.
Scrut automates employee information security training with a pre-built 30-minute course designed by industry experts. The tool provides everything your employees need to understand potential risks, avoid slippages, and develop a secure posture.
As shown in the screenshot below, you can always see the status of your security training.
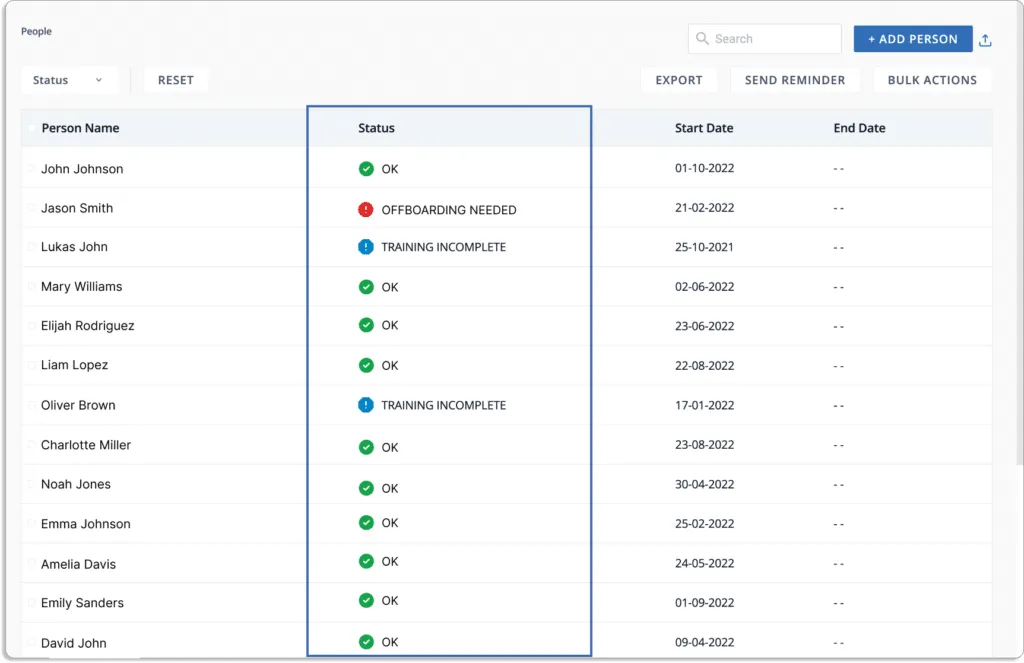
The platform allows you to create alerts, set reminders, and send personalized notifications to employees for them to complete the training.
You can schedule a demo to learn more about Scrut Automation.

Table of contents


















