In today’s complex and interconnected business arena, organizations rely on various vendors to support their operations for software solutions, logistics, financial services, and other critical functions. While these vendor relationships bring significant advantages in terms of cost savings and expertise, they also introduce risks.
These risks encompass a range of challenges, including data breaches, compliance violations, and the financial instability of vendors. Without a robust vendor risk assessment process, organizations risk operational disruptions, damage to their reputation, and the compromise of sensitive data.
Identifying and mitigating these risks becomes paramount for sustaining a resilient and secure business ecosystem. An efficient vendor risk assessment process is essential to safeguarding an organization’s operations, reputation, and sensitive data.
In this blog, we’ll delve into the strategies and tips that can help organizations streamline their vendor risk assessment procedures, ensuring compliance and enhancing the overall security of their business operations.
What is vendor risk assessment?
Vendor risk assessment is a crucial process that organizations undertake to evaluate and manage the potential risks associated with their third-party vendors and suppliers. It involves a systematic analysis of various factors, including contractual terms, compliance with regulations, data security practices, financial stability, and more, to determine the level of risk a vendor may pose to the organization.
The objective of vendor risk assessment is to identify and mitigate risks that could impact an organization’s operations, reputation, or sensitive data.
By thoroughly assessing and monitoring vendors, organizations can make informed decisions, enhance their risk management strategies, and ensure that their business relationships with vendors remain secure and compliant with applicable regulations.
Why is vendor risk assessment important?
Vendor risk assessment is of paramount importance because it safeguards an organization’s operations, data, and reputation.
By systematically evaluating the risks associated with third-party vendors and suppliers, organizations can identify vulnerabilities and proactively mitigate potential threats, such as data breaches, compliance violations, or financial instability. It ensures that the organization’s business relationships are secure, align with regulatory requirements, and maintain the highest standards of data security.
In an interconnected business environment where reliance on external partners is commonplace, vendor risk assessment serves as a critical tool to prevent disruptions, protect sensitive information, and maintain the trust of customers and stakeholders.
Key factors in vendor risk assessment
When conducting efficient vendor risk assessments, organizations must focus on specific key factors that impact the risk profile of their vendors. These factors guide the assessment process and help organizations identify and mitigate potential risks effectively.

1. Data security
Data security is a paramount consideration. Vendors often have access to an organization’s sensitive data, and a security breach can have severe consequences. Assessing a vendor’s data security practices, including encryption, access controls, and data handling procedures, is crucial to understanding and mitigating data security risks.
2. Regulatory compliance
Regulatory compliance is another critical factor. Organizations must ensure that their vendors adhere to industry-specific regulations and standards. Non-compliance can lead to legal and financial ramifications, making it essential to evaluate a vendor’s regulatory posture.
3. Financial stability
Financial stability is vital to assessing a vendor’s ability to fulfill its obligations. A financially unstable vendor may pose a risk to the continuity of the services or products they provide. Evaluating a vendor’s financial health helps organizations make informed decisions about their vendor relationships.
4. Contractual terms
Vendor contracts play a significant role in risk assessment. Organizations should thoroughly review contract terms to understand their liability, data ownership, dispute resolution procedures, and the vendor’s responsibilities related to data security and compliance.
5. Vendor reputation
Assessing a vendor’s reputation in the industry is valuable. Seeking references from existing clients and conducting research on a vendor’s track record can provide insights into their performance, reliability, and trustworthiness.
Key challenges in vendor management risk assessment
Vendor risk assessment, while vital, is not without its challenges. Organizations often encounter several common obstacles when conducting these assessments. Understanding these challenges is the first step in addressing them effectively.

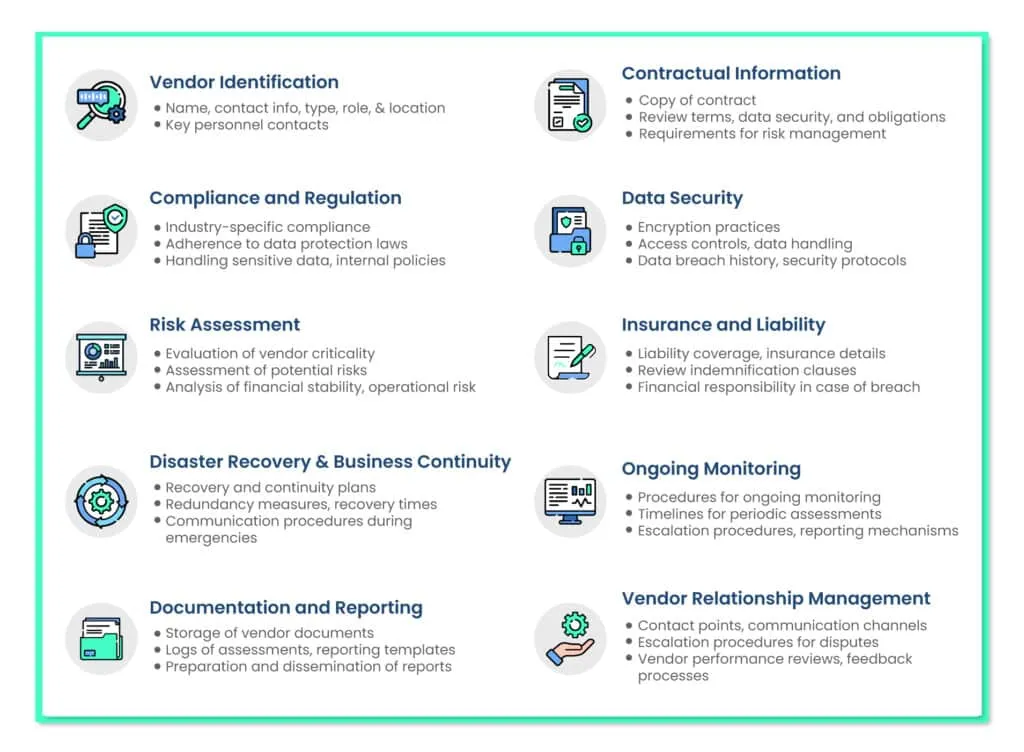
Vendor risk assessment checklist
To ensure you’re tackling all challenges efficiently, here’s a 10-step checklist:
Best practices for efficient vendor risk assessment
Vendor risk assessment is a dynamic process that must adapt to evolving risks and technologies as organizations become increasingly interconnected.
Organizations should adopt best practices, prioritize regular updates, education, technology adoption, thorough evaluations, and collaboration with industry peers.
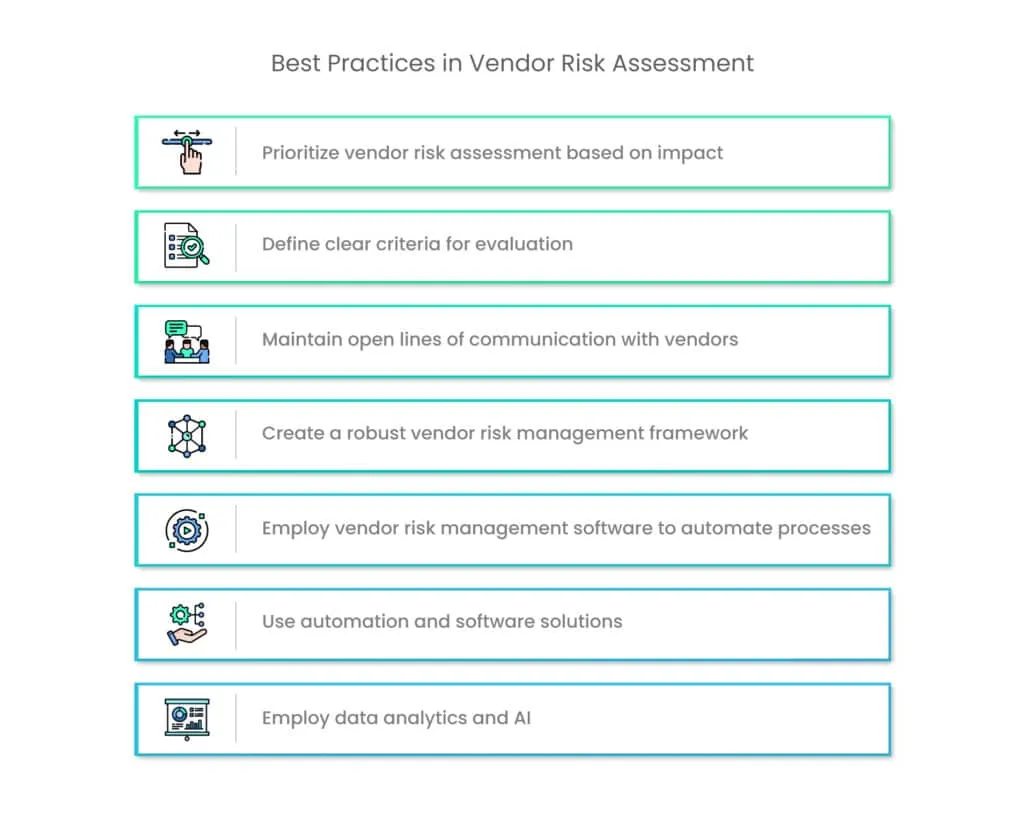
By implementing these best practices, organizations can navigate the complexities of vendor risk assessment more effectively:
1. Prioritize vendor risk assessment based on impact
Not all vendors pose the same level of risk to an organization. To optimize resource allocation and focus, prioritize vendor risk assessments based on criticality and impact. Consider the following factors when setting priority levels:
Criticality of the vendor: Assess how essential the vendor’s products or services are to your operations. Vendors providing core services may require more in-depth assessments.
Sensitivity of handled data: Evaluate the type of data the vendor handles. Vendors managing sensitive customer data demand more scrutiny.
Potential impact: Analyze the potential consequences of a risk event with the vendor. High-impact scenarios require a more comprehensive assessment.
By categorizing vendors based on these criteria, organizations can allocate resources appropriately, ensuring that the most critical and high-risk vendors receive more extensive evaluations while lower-risk vendors undergo streamlined assessments.
2. Define clear criteria for evaluation
A fundamental aspect of efficient vendor risk assessment is the definition of clear, standardized criteria for evaluation. Having a well-defined set of criteria ensures that assessments are conducted consistently and objectively across all vendors.
These criteria should encompass various aspects of risk assessment, including data security, regulatory compliance, financial stability, vendor reputation, and contractual terms.
3. Maintain open lines of communication with vendors
Maintaining open lines of communication with vendors is a critical component of efficient vendor risk assessment. Transparency and collaboration between your organization and your vendors can lead to better risk management and stronger vendor relationships.
Effective communication includes:
Feedback and recommendations: Share risk assessment findings with vendors and provide constructive feedback. If risks are identified, collaborate on strategies and actions for risk mitigation.
Compliance and remediation: If a vendor is not compliant with specific regulations or standards, communicate the necessary remediation steps and timelines.
Information sharing: Exchange information on emerging risks and vulnerabilities, enabling proactive risk mitigation and strengthening data security practices.
4. Create a robust vendor risk management framework
Creating a robust vendor risk management framework is a strategic approach to efficient vendor risk assessment. This framework should integrate risk assessment as an integral part of the vendor lifecycle, from vendor selection to ongoing monitoring.
Key elements of this framework include:
Defined processes: Clearly outline the processes and steps involved in vendor risk assessment. These processes should cover vendor onboarding, periodic assessments, risk scoring, and ongoing monitoring.
Assigned responsibilities: Specify the roles and responsibilities of individuals or teams involved in vendor risk assessment. This includes defining who is responsible for data collection, analysis, communication, and risk mitigation.
Timelines and milestones: Establish timelines and milestones for assessments, reviews, and audits. This ensures that assessments are conducted consistently and on schedule.
Continuous improvement: Incorporate mechanisms for continuous improvement and feedback, allowing the framework to evolve based on lessons learned and changing risk landscapes.
5. Employ vendor risk management software to automate processes
Vendor Risk Management (VRM) software solutions empower professionals in vendor management, risk assessment, security, and procurement to efficiently oversee the assessment of third parties and vendors throughout their entire relationship lifecycle.
Further, they prove invaluable in aiding compliance management efforts. These tools are adept at gathering and consolidating a wide spectrum of risk-related data from vendors, third-party entities, and external sources, aligning seamlessly with regulatory vendor risk mandates and internal vendor engagement policies. Scrut can help with suitable vendor risk management software solutions.
Automation and VRM software solutions can help with:
- Maintaining comprehensive vendor oversight: Store all your contracts, documents, and vendor data within a centralized platform. Utilize integrated tools for managing, assessing, tracking, and reporting on your vendor relationships, enhancing the overall health and oversight of these partnerships.
- Streamlining vendor assessment with questionnaires: Benefit from user-friendly, built-in tools designed for risk assessment, vendor criticality, and risk scoring. Employ preconfigured or customized questionnaires, sending them directly to vendors for gathering relevant information. All responses are conveniently centralized and readily accessible for decision-makers.
- Efficient collaboration with internal and vendor stakeholders: Once you’ve reviewed a vendor’s security questionnaire responses and identified actions needed for added assurance, the platform allows you to assign tasks directly to the vendor or internal stakeholders. These tasks can be tailored based on vendor criticality and questionnaire responses. Additionally, the platform offers task automation, alerts, and reminders, facilitating stakeholder task management.
- Establishing a robust project management system: A robust project and task management system for vendor risk management significantly bolsters security. Such a system ensures critical security tasks, like testing access controls and other protocols, are not overlooked. Preventing vulnerabilities from being exploited is essential to safeguard customer data and prevent potentially costly security breaches.
- Mitigating vendor risks: Implement controls to mitigate specific risks and gauge the residual risk associated with vendors. Visual reports provide visibility into residual risk for each vendor, highlighting those requiring questionnaire completion or responses to follow-up queries. This simplifies the identification of vendors and tasks necessitating attention, enabling effective risk reduction.
- Seamless integration with compliance efforts: Link all vendor management activities, including questionnaire responses and remediation project tasks, to pre-existing risk factors, controls, security standards, or regulatory requirements within the software. VRM software serves as the central hub for comprehensive compliance management. By leveraging this platform for vendor risk and aligning your security program with industry standards, you can swiftly access proof of vendor due diligence activities for audit purposes.
Organizations can utilize dedicated software solutions and platforms designed to automate key aspects of the assessment process.
By quickly and accurately detecting, assessing, and keeping track of vendor risks, Scrut can support your company’s security assessment initiatives.
6. Employ data analytics and AI
Data analytics and artificial intelligence (AI) are powerful tools for vendor risk assessment. These technologies can process large volumes of data to identify patterns and anomalies, which can reveal potential risks.
For example, data analytics can uncover financial irregularities or trends in vendor performance that may not be apparent through manual analysis.
AI can enhance predictive analytics, helping organizations forecast vendor performance and potential risks. It can also provide insights into emerging risks and vulnerabilities in the vendor landscape.
Wrapping up: The imperative of efficient vendor risk assessment
In the fast-paced world of business and technology, efficient vendor risk assessment is no longer a luxury—it’s an imperative. Organizations cannot afford to overlook the critical task of assessing and managing the risks posed by their third-party vendors.
The efficiency of this process ensures compliance and strengthens the overall security of business operations and the protection of sensitive data. Efficient vendor risk assessment is not just a measure of compliance; it’s a strategic pillar that supports the long-term success and resilience of modern businesses in a dynamic and interconnected world.
By adopting the best practices, technology, and a proactive approach to an evolving risk landscape, organizations can safeguard their interests, maintain strong vendor relationships, and make informed decisions in vendor management.
Scrut offers a comprehensive approach to vendor risk management, ensuring your operations remain secure, compliant, and resilient in evolving vendor landscapes. Get in touch to find out more.
Frequently Asked Questions
1. What is vendor risk assessment, and why is it important for businesses?
Vendor risk assessment is the process of evaluating and managing the risks associated with third-party vendors or suppliers that an organization engages with. It involves assessing factors such as financial stability, data security, compliance with regulations, and the vendor’s ability to deliver products or services. Vendor risk assessment is crucial for businesses to mitigate potential risks, safeguard their operations, protect sensitive data, and ensure the reliability and security of their supply chain.
2. What are the common challenges organizations face when conducting vendor risk assessments?
Common challenges in vendor risk assessments include the complexity of managing multiple vendors, limited resources and expertise, inconsistent data sources, and rapidly changing vendor risk profiles. Additionally, organizations may struggle with evaluating the risks associated with emerging technologies or assessing the security of vendors’ third-party relationships. Addressing these challenges requires comprehensive risk assessment strategies and efficient processes.
3. How can technology and automation help improve the efficiency of vendor risk assessments?
Technology and automation play a critical role in enhancing the efficiency of vendor risk assessments. Software tools and platforms can automate data collection, risk scoring, and monitoring of vendors. They provide real-time insights into a vendor’s risk profile, reducing manual efforts and improving accuracy. Additionally, technology can help identify high-risk vendors more quickly, allowing organizations to allocate resources effectively for in-depth assessments where they matter most.
4. What key factors should organizations consider when selecting and evaluating vendors in terms of risk?
Organizations should consider several key factors when assessing vendor risk, including:
– Data Security: Assess the vendor’s data protection practices, especially if they handle sensitive customer data.
– Regulatory Compliance: Ensure the vendor complies with industry-specific regulations and standards relevant to your business.
– Financial Stability: Evaluate the vendor’s financial health and stability to ensure they can deliver on their commitments.
– Contractual Terms: Carefully review vendor contracts to understand liability, data ownership, and dispute resolution procedures.
– Reputation: Investigate the vendor’s reputation in the industry and seek references from existing clients to gauge their performance and reliability.
5. What are some best practices and tips for ensuring an efficient and thorough vendor risk assessment process?
To ensure an efficient and thorough vendor risk assessment process, organizations should:
– Prioritize vendors based on risk and criticality.
– Define clear risk assessment criteria and methodologies.
– Leverage technology and automation for data collection and monitoring.
– Conduct periodic risk assessments and continuously monitor vendor risk profiles.
– Foster strong communication with vendors to address and mitigate identified risks.
– Establish a robust vendor management framework that includes risk assessment as an integral part of the vendor lifecycle.
– Efficient vendor risk assessment helps organizations make informed decisions, enhance vendor relationships, and protect their operations and reputation.





































