Choose risk-first compliance that’s always on, built for you.
Go back to blogs
Update: NIST CSF 2.0 vs 1.1: What's new and why it matters for your cybersecurity program
Last updated on
April 21, 2025
min. read

Ten years is a long time to wait for an update. But when one finally arrives, you can bet it won’t be minor.
That’s exactly what happened with NIST’s Cybersecurity Framework. After years of feedback, industry shifts, and security wake-up calls, NIST CSF got its first major overhaul in 2024.
This isn’t just a touch-up. Version 2.0 reflects how cybersecurity has evolved — wider risks, deeper responsibilities, and a need for clearer guidance.
If you’ve been relying on CSF 1.1 or are new to the framework altogether, this is the perfect time to understand what’s changed, what stayed, and how to make the shift to NIST 2.0.
What is NIST CSF?
The NIST Cybersecurity Framework (CSF) is a high-level framework designed to help organizations understand, manage, and reduce cybersecurity risk. It provides a structured yet flexible approach to strengthening cybersecurity programs across sectors.
First released in 2014, and later updated as version 1.1 in April 2018, the framework gained widespread adoption—especially among U.S. critical infrastructure sectors. Over time, it also found traction across global enterprises, startups, and government entities.
However, the cybersecurity environment changed rapidly. The rise of ransomware, remote work, supply chain threats, and cloud-native systems exposed new kinds of risks, and CSF 1.1 was no longer enough.
In response, NIST kicked off the revision process in February 2022. Over the next two years, they conducted public workshops, released drafts, and invited feedback—ultimately receiving more than 2,500 public comments.
This collaborative effort resulted in the release of CSF 2.0 in February 2024—a more modern, inclusive framework built for today’s security realities.
How NIST CSF differs from other NIST publications
NIST publishes several cybersecurity resources, and they often get grouped together. But each serves a distinct purpose.
- CSF is strategic. It outlines what organizations should aim to achieve in terms of cybersecurity outcomes.
- SP 800-53 is tactical. It provides detailed security and privacy controls that help organizations implement those outcomes.
- SP 800-52 is technical. It provides guidance on configuring Transport Layer Security (TLS) to protect data in transit.
In simple terms:
- CSF helps you identify risks and set priorities.
- SP 800-53 helps you implement and enforce security controls.
- SP 800-52 helps you secure communications using up-to-date encryption practices.
Together, these publications create a layered and practical roadmap—from setting cybersecurity goals to deploying secure, standards-aligned infrastructure.
Why use NIST CSF?
There are several compelling reasons organizations adopt the NIST CSF:
- Great flexibility – It’s technology-neutral and scalable, suitable for both startups and large enterprises.
- Widely recognized – It’s referenced in many industry and regulatory standards, from executive orders to sector-specific guidelines.
- Helps align teams – The CSF’s structure makes it easier for security leaders to communicate with executive stakeholders using a common language.
- Improves resilience – By covering everything from asset identification to incident recovery, the CSF ensures you’re building a full-spectrum cybersecurity program by covering everything from asset identification to incident recovery.
Organizations don’t need to implement everything at once. The CSF is modular, so you can start small and evolve as your capabilities grow.
Core functions of NIST CSF
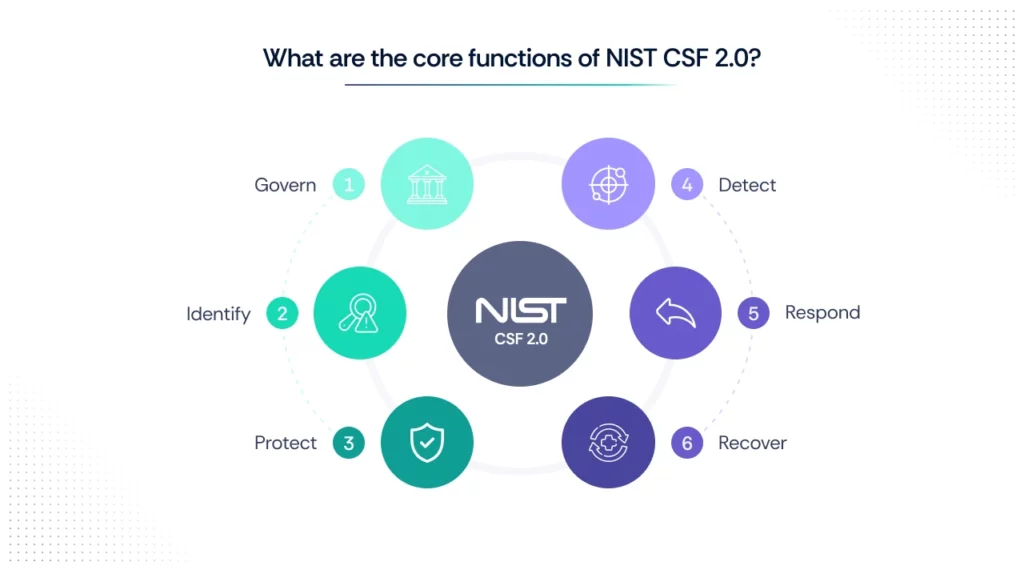
At the heart of NIST CSF are its six core functions, which act as pillars for any cybersecurity program:
- Govern – Establish and monitor the organization’s cybersecurity risk management strategy, policies, and roles.
- Identify – Understand your organizational context, assets, risks, and supply chain dependencies.
- Protect – Safeguard data and systems through appropriate controls, such as access management and employee training.
- Detect – Develop systems and processes to discover anomalies and security events in real time.
- Respond – Build and execute incident response plans to manage and mitigate cybersecurity incidents.
- Recover – Ensure you can restore operations and services and learn from incidents to improve future resilience.
These core functions are further broken down into categories and subcategories describing specific outcomes organizations should aim for.
Implementation tiers
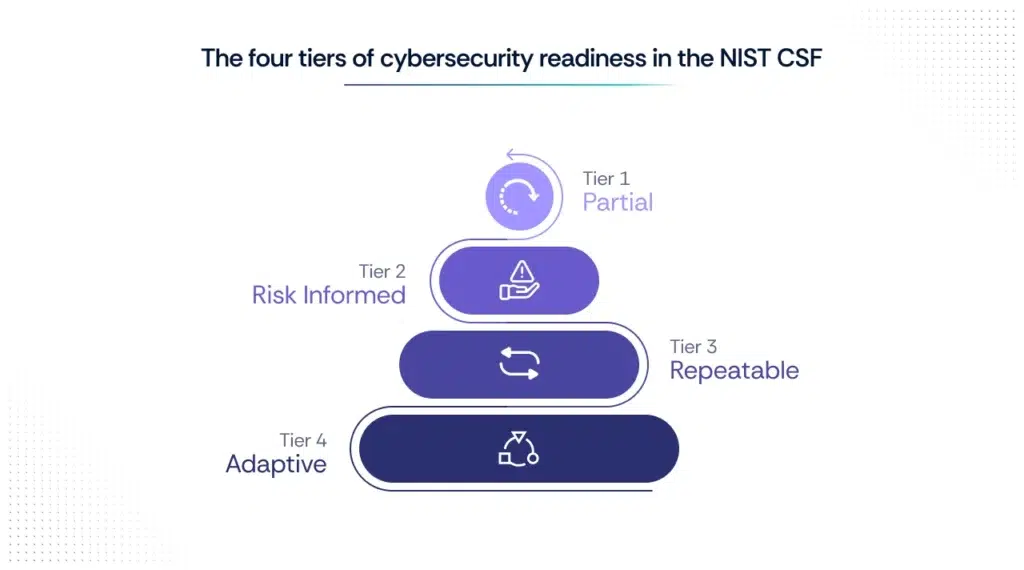
The CSF includes four implementation tiers that describe how an organization manages cybersecurity risk — from informal practices to adaptive, risk-informed strategies:
- Tier 1: Partial – Cybersecurity activities are reactive and ad hoc.
- Tier 2: Risk Informed – Risk management is approved but not yet organization-wide.
- Tier 3: Repeatable – Policies are formalized and consistently followed.
- Tier 4: Adaptive – Cybersecurity practices are continuously improved and embedded in organizational culture.
These tiers help organizations assess where they are and map a path to maturity.
Who does the NIST Cybersecurity Framework affect?
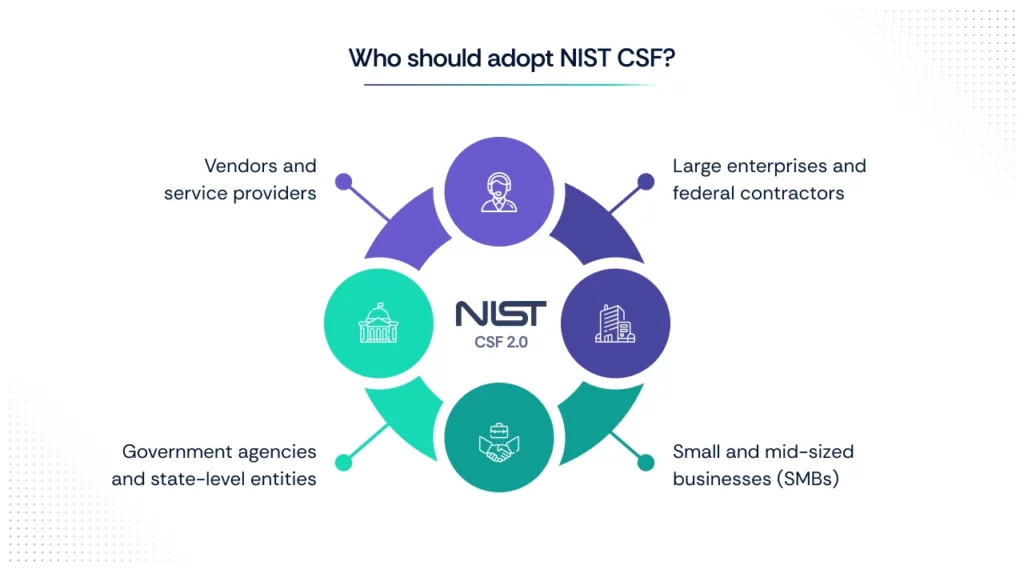
The NIST Cybersecurity Framework (CSF) is designed for any organization—public or private—that manages cybersecurity risks to its systems, assets, and data. While it was initially developed for U.S. critical infrastructure sectors (like energy, healthcare, and finance), its flexible, industry-agnostic structure has made it a go-to standard worldwide.
Here’s who typically adopts NIST CSF:
- Large enterprises and federal contractors: Many use it to mature their cybersecurity programs, meet federal expectations, and align with supply chain requirements.
- Small and mid-sized businesses (SMBs): The CSF offers a practical starting point for resource-constrained teams to structure their cybersecurity priorities.
- Government agencies and state-level entities: The framework is often referenced in executive orders and government guidance for improving national cyber resilience.
- Vendors and service providers: Organizations working with federal agencies or regulated industries often use NIST CSF to demonstrate alignment and readiness.
Even though NIST CSF is voluntary, it’s frequently cited in RFPs, audits, and vendor assessments — making it effectively de facto mandatory in many industries.
CSF 2.0 vs CSF 1.1: What’s actually different?
The transition from CSF 1.1 to 2.0 marks a significant evolution — not just in terminology, but in how cybersecurity programs are expected to function across sectors.
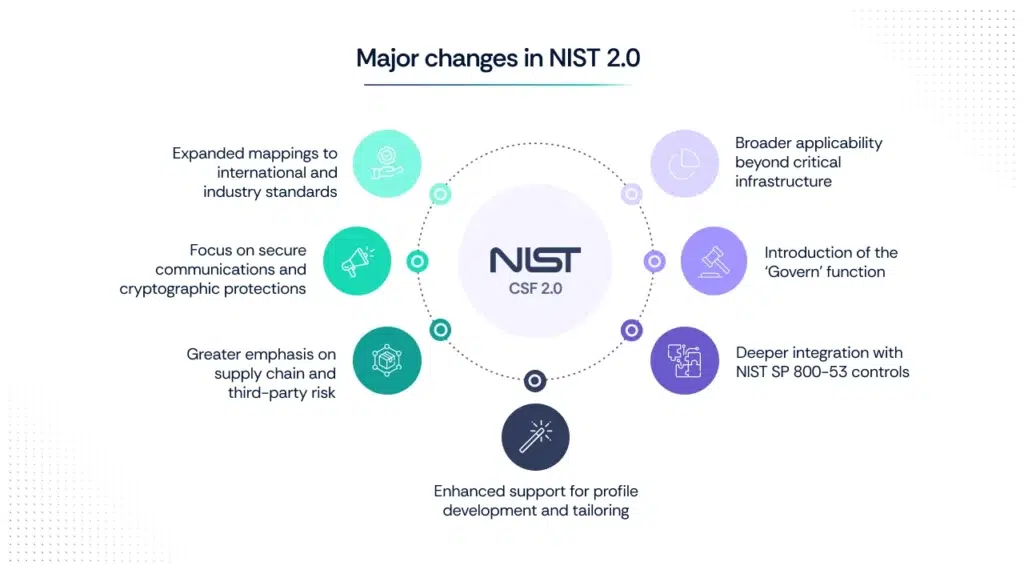
Here’s a breakdown of the most impactful changes introduced in CSF 2.0.
1. Broader applicability beyond critical infrastructure
CSF 1.1 was originally designed with critical infrastructure in mind. CSF 2.0 expands this focus to include all sectors — public and private, large enterprises and small businesses alike.
By removing sector-specific language, NIST has made it clear that the framework is intended to support any organization seeking to improve its cybersecurity posture.
2. Introduction of the ‘Govern’ function
A major structural enhancement in CSF 2.0 is the addition of a sixth core function: Govern.
This function formalizes the role of governance in cybersecurity, emphasizing organizational oversight, defined responsibilities, and risk management strategy.
It brings executive accountability into sharper focus and helps ensure cybersecurity is treated as a business risk — not just an IT issue.
3. Deeper integration with NIST SP 800-53 controls
CSF 2.0 strengthens its connection with NIST SP 800-53 Revision 5, offering updated mappings between CSF subcategories and specific security and privacy controls.
This alignment significantly reduces the implementation gap. Organizations can now move more seamlessly from high-level framework objectives to detailed technical execution.
For instance, if the Govern function calls for establishing cybersecurity roles and responsibilities, 800-53 offers concrete guidance through controls such as PM-3 (Information Security Resources) and PM-10 (Security Authorization Process).
This deeper alignment also helps organizations unify compliance efforts, as SP 800-53 is commonly referenced in frameworks like FISMA, FedRAMP, and increasingly even in private sector benchmarks.
4. Enhanced support for profile development and tailoring
While CSF 1.1 introduced the concept of profiles, CSF 2.0 took it further by offering improved examples and clearer guidance.
Organizations are encouraged to define both current profiles (where they stand) and target profiles (where they want to be), and then use the framework to close the gap.
This is especially valuable when paired with SP 800-53, as the control catalog can be selectively tailored to match the organization’s unique risk context, sector, and maturity.
5. Greater emphasis on supply chain and third-party risk
Supply chain attacks and vendor-related breaches have become more common and more damaging.
CSF 2.0 responds by adding new categories under the Govern and Protect functions that explicitly address third-party oversight, contractual obligations, and external risk monitoring.
Here too, SP 800-53 offers actionable support — especially through control families like SR (Supply Chain Risk Management), which now play a key role in operationalizing CSF 2.0’s expanded scope.
6. Focus on secure communications and cryptographic protections
While CSF has always addressed data protection, version 2.0 puts more weight on securing data in transit — particularly under the Protect and Detect functions.
This is where NIST SP 800-52 Rev. 2 becomes especially relevant. It offers guidance for configuring Transport Layer Security (TLS) to ensure secure, standards-based encryption between systems.
CSF 2.0 does not detail specific encryption mechanisms, but by pointing to documents like SP 800-52, it gives implementers the clarity they need to enforce stronger cryptographic protections — aligned with federal best practices.
Whether you’re encrypting internal APIs or securing third-party integrations, SP 800-52 ensures TLS is configured correctly, using modern cipher suites and protocol versions.
7. Expanded mappings to international and industry standards
NIST CSF 2.0 enhances its utility by incorporating mappings to a broader range of standards and frameworks, facilitating organizations in harmonizing their cybersecurity practices with globally recognized guidelines. Notable mappings include:
- ISO/IEC 27001:2022: Aligns with international information security management standards, aiding global organizations in streamlining compliance efforts.
- Center for Internet Security (CIS) Controls Version 8: Maps to prioritize cybersecurity best practices, assisting organizations in implementing effective security measures.
- Cloud Security Alliance (CSA) Cloud Controls Matrix (CCM): Aligns with cloud-specific security controls, supporting organizations in securing cloud environments.
- General Data Protection Regulation (GDPR): While GDPR focuses on data protection and privacy for individuals within the European Union, aligning NIST CSF’s core functions — such as Identify, Protect, Detect, Respond, and Recover — with GDPR requirements can enhance data security measures and support compliance efforts.
- Health Insurance Portability and Accountability Act (HIPAA): Organizations handling protected health information can map NIST CSF controls to HIPAA’s Security Rule requirements, facilitating the implementation of robust security measures to protect sensitive health data.
- Payment Card Industry Data Security Standard (PCI DSS): Businesses involved in payment card processing can align NIST CSF with PCI DSS requirements to strengthen payment data security and streamline compliance efforts.
These expanded mappings enable organizations to integrate diverse regulatory requirements into their cybersecurity strategies, promoting a unified and efficient approach to risk management.
What hasn’t changed (and why that’s important)
While CSF 2.0 brings several key updates, much of its foundational structure remains intact. This continuity ensures that organizations already using CSF 1.1 do not need to start from scratch.
1. The core structure still revolves around five core functions
The five original functions — Identify, Protect, Detect, Respond, and Recover — remain central to the framework. These continue to provide a logical, lifecycle-based approach to managing cybersecurity risk.
The new Govern function complements rather than replaces them, elevating strategy and oversight without disrupting the overall structure.
2. Risk-based, outcomes-focused approach
CSF 2.0 continues to emphasize a risk-based approach. It helps organizations prioritize efforts based on their unique threat landscape, business objectives, and regulatory requirements.
The framework still avoids prescribing exact tools or solutions. Instead, it focuses on the outcomes organizations should strive to achieve.
3. Use of tiers and profiles
The Implementation Tiers — ranging from Partial (Tier 1) to Adaptive (Tier 4) — are still in place. These tiers help organizations evaluate the maturity of their cybersecurity practices in terms of risk management sophistication and integration with enterprise goals.
Similarly, the Profile model is retained and enhanced. Organizations can still use Current and Target Profiles to build tailored roadmaps, now with better guidance and mapping support from NIST.
4. Interoperability with other frameworks
CSF 2.0, like its predecessor, is designed to work in harmony with other standards and regulations. It continues to serve as a bridge between high-level governance and detailed technical guidance — especially when used alongside NIST SP 800-53 for controls and SP 800-52 for secure communication practices.
This allows organizations to adopt CSF as a unifying framework without abandoning existing compliance or control models.
Where SP 800-52 fits into CSF 2.0: Securing data in transit
CSF 2.0 puts greater emphasis on securing data in transit — especially under the Protect and Detect functions. That’s where NIST SP 800-52 comes in.
This special publication outlines how to configure Transport Layer Security (TLS) properly. It covers recommended protocol versions, cipher suites, and certificate practices to ensure communications remain confidential and tamper-proof.
When applied within the CSF framework, SP 800-52 strengthens both internal and external communications — whether across APIs, cloud systems, or third-party integrations.
It also supports monitoring efforts under the Detect function, ensuring encrypted traffic doesn’t compromise visibility or incident detection.
By following SP 800-52, organizations align with federal best practices while addressing one of CSF 2.0’s key technical expectations.
Getting started with CSF 2.0: How Scrut helps you put it into action
Adopting the NIST Cybersecurity Framework 2.0 may seem like a daunting task — especially with expanded functions and mappings — but you don’t have to start from scratch. Scrut simplifies your CSF 2.0 journey by breaking it into actionable steps backed by automation and expert guidance.
Here’s how Scrut helps you operationalize CSF 2.0:
1. Pre-mapped controls for faster adoption
Scrut’s platform comes with thousands of pre-mapped controls, including those aligned with NIST CSF 2.0. This allows you to start building your cybersecurity program with controls that are already aligned with the framework’s core functions and categories.
2. Integrated risk assessments
With Scrut, you can conduct guided risk assessments that tie directly into the Identify and Govern functions. The platform helps you identify assets, assess threats, and prioritize risks based on business impact — all within a centralized system.
3. Automated evidence collection
Scrut’s integrations with cloud providers, HR systems, identity management platforms, and ticketing tools automate evidence gathering for many CSF-aligned controls — saving your team hours of manual work and improving audit readiness.
4. Real-time monitoring and alerts
The Protect and Detect functions come to life with Scrut’s continuous monitoring capabilities. Along with comprehensive dashboards, you get real-time alerts for security gaps, misconfigurations, or access violations — so you can take action before issues escalate.
5. Gap analysis and implementation roadmap
Not sure where to begin? Scrut helps you perform a gap analysis against CSF 2.0, highlighting which controls are in place and where improvements are needed. Not just that, we also help you put a plan in place. From there, the platform provides a step-by-step roadmap tailored to your organization’s maturity level.
6. Centralized policy management
Scrut helps you align with CSF’s Govern function by centralizing all security policies, assigning ownership, and tracking review cycles — ensuring accountability across your team. Creation and mapping of CSF 2.0 policies to relevant controls is further simplified by pre-built templates and a unified controls framework.
7. Audit-readiness and collaboration
Scrut’s custom auditor access lets auditors view all audit-related documentation from the platform itself, thereby eliminating the pain of lengthy and cumbersome email threads. Detailed audit logs and reports provide visibility over document trails, and dedicated trackers for requests and findings let auditors collaborate with your team smoothly.
8. Cross-mapping with other frameworks
Scrut allows you to reuse your existing compliance work by automatically cross-mapping overlapping controls from standards like ISO 27001, reporting frameworks like SOC 2, and regulations like the GDPR directly to CSF 2.0. This minimizes duplication and saves your team valuable time. With support for over 50 standards, regulations, and cybersecurity frameworks, Scrut keeps your compliance efforts streamlined—even as new requirements emerge.
Looking to operationalize NIST CSF 2.0 without the manual overhead?
Scrut can help you assess your current posture, map controls to SP 800-53, and manage your cybersecurity program end-to-end—with clarity, accountability, and automation built in.
Talk to our experts to see how Scrut can support your NIST CSF journey.
FAQs
1. How does NIST CSF 2.0 align with other security standards and frameworks?
NIST CSF 2.0 aligns with various security standards and frameworks, including ISO standards, the NIST Privacy Framework, and the NIST Risk Management Framework. This alignment enhances interoperability and streamlines compliance efforts.
2. What challenges might organizations face in implementing NIST CSF 2.0?
Implementing NIST CSF 2.0 may pose challenges such as resource constraints, technical complexity, resistance to change, and the need for adequate knowledge and understanding of the framework and its implications.
3. What are the benefits of implementing NIST CSF 2.0 for organizations?
Implementing NIST CSF 2.0 enables organizations to adopt a risk-based approach to cybersecurity, prioritize continuous improvement, ensure versatility across sectors and sizes, and gain clarity on governance structures, ultimately enhancing their cybersecurity resilience.
Table of contents


















