Choose risk-first compliance that’s always on, built for you.
Go back to blogs
Crafting a robust NIST disaster recovery policy and template
Last updated on
April 9, 2024
12
min. read

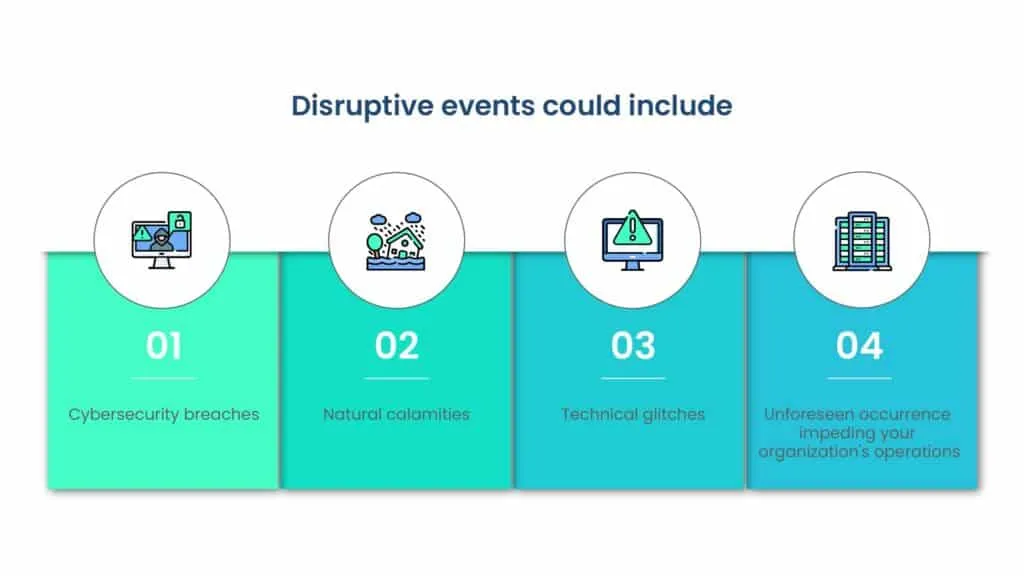
Prioritizing risk management is paramount as cyber threats continue to become more sophisticated and unpredictable. Whether it’s malware, ransomware, or other cyberattacks, the potential damage to an organization’s infrastructure and reputation is substantial.
However, it’s not just cyber threats; natural calamities, technical failures, and unexpected outages also pose significant risks that can severely disrupt operations.
To address these challenges effectively, organizations must prioritize risk management and bolster their defenses with comprehensive business continuity and disaster recovery plans. This proactive approach aligns with the SEC’s new guidelines for cybersecurity management and incident disclosure, underscoring the importance of robust risk mitigation strategies in safeguarding organizational resilience and reputation.
This guide delves into the process of developing an effective Disaster Recovery Plan (DRP) guided by the principles of the National Institute of Standards and Technology (NIST), providing organizations with the tools and knowledge to withstand and thrive in the face of potential disasters.
What is a NIST-guided Disaster Recovery Plan (DRP)?
A Disaster Recovery Plan (DRP), as outlined by the National Institute of Standards and Technology (NIST), serves as your organization’s strategic blueprint for restoring data and critical functions post a disruptive event.
By adhering to NIST guidelines, your DRP integrates industry-standard best practices for risk management and recovery. NIST’s Special Publication 800-34, “Contingency Planning Guide for Federal Information Systems,” furnishes a comprehensive framework for devising and executing effective recovery strategies, serving as a vital tool in shaping your organizational approach.
Why is a NIST-aligned DRP important?
Your NIST-aligned DRP complements your Business Continuity Plan (BCP), which concentrates on maintaining essential functions during disruptions.

While the BCP addresses immediate needs, the DRP is dedicated to restoring your organization’s systems and operations to their pre-disaster state. This dual strategy not only safeguards data and systems but also expedites a return to normalcy.
Implementing a NIST-informed DRP is imperative for several reasons:
- Offers a structured and methodical recovery approach
- Ensures every facet of your organization’s response is deliberate and efficient
- Minimizes downtime
- Safeguards data integrity
- Upholds customer trust
- Ensures regulatory compliance
- Equips your organization with the requisite tools and knowledge to navigate post-incident challenges.
How to formulate a NIST-informed DRP?
- Evaluate potential disaster risks and conduct a business impact analysis for critical applications.
- Delineate the steps required to reinstate these crucial operations in the event of a sudden cessation.
- Detail strategies aimed at mitigating the repercussions of a disaster.
- Incorporate “Recovery Point Objectives” (RPOs) into your plan. These represent the operational states that you aim to return to during the data recovery process and help determine the acceptable data loss limits during recovery.
- Establish “Recovery Time Objectives” (RTOs) to define the timeframe within which normal operations should be restored after a disaster. RTOs establish the timeframe within which you aim to restore normal operations. For example, set objectives such as, “We endeavor to resume regular operations within four hours of the incident.”

Incident response, business continuity, and disaster recovery
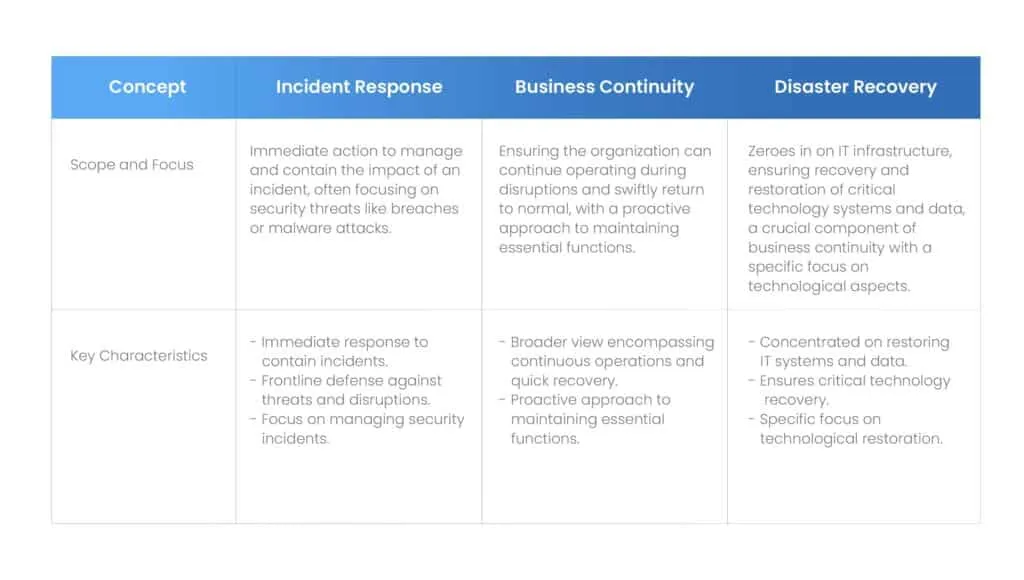
Within the domain of organizational resilience and risk management, three fundamental concepts—incident response, business continuity, and disaster recovery—hold significant importance.
Although they are interrelated and frequently intersect, each serves a unique function in the endeavor to sustain, recover, and safeguard business operations. Grasping their differences is essential for crafting a resilient organizational structure capable of navigating and responding to unforeseen disturbances effectively.
1. Incident Response
Incident response is an immediate reaction to unexpected events or threats to prevent further damage to operations, assets, or individuals.
It involves these steps:
- Preparation: Developing an incident response plan including roles and communication strategies.
- Detection and Analysis: Identifying and assessing the nature and impact of the incident.
- Containment, Eradication, and Recovery: Taking steps to contain the incident, eliminate the threat, and restore operations.
- Post-Incident Review: Analyzing the response to improve future readiness.
2. Business Continuity
Ensuring continuous business operations during and after incidents or disruptions is vital.
Its key components are:
- Business Impact Analysis (BIA): Identifying critical functions, resources, and potential impact of disruptions.
- Continuity strategies: Developing plans to maintain or resume critical operations after an incident.
- Plan development and implementation: Creating comprehensive continuity plans embedded within the organization.
- Training and testing: Regularly testing plans and training employees for preparedness.
3. Disaster Recovery
Disaster recovery focuses on restoring IT infrastructure and operations after catastrophic events.
Its key components include:
- Technology Recovery Strategies: Identifying critical IT assets and services and establishing recovery methods.
- Data Backup Solutions: Implementing protocols to restore critical data after a disaster.
- Recovery Site Arrangements: Establishing alternate processing sites to quickly bring IT systems back online.
- Testing and Plan Updates: Regularly testing recovery procedures and updating plans to reflect technological and process changes.
A comprehensive organizational resilience strategy integrates incident response, business continuity, and disaster recovery, ensuring seamless alignment and mutual support.
For instance, an efficient incident response can mitigate incident impacts, thereby alleviating the strain on business continuity procedures. Likewise, a resilient business continuity plan incorporates disaster recovery strategies tailored for IT systems.
Together, they forge a holistic approach to organizational resilience, fortifying against diverse disruptions and guaranteeing the organization’s ability to endure, respond to, and recuperate from unforeseen events.
Best practices for disaster recovery
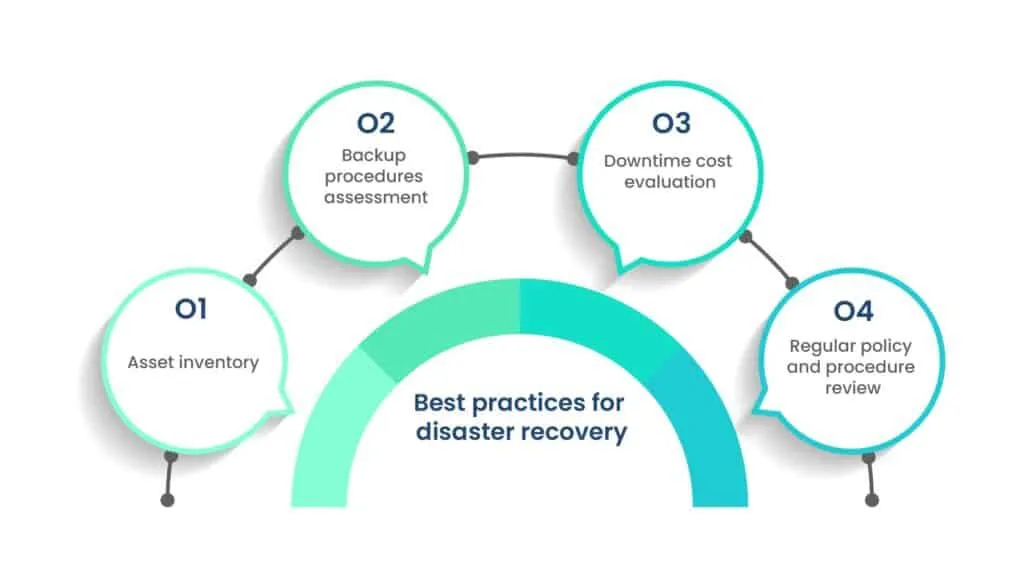
Disaster recovery protocols may differ across businesses, but they should adhere to the following best practices:
1. Asset inventory
- Identify all critical systems, including software, data, and hardware essential for your company’s operations.
- Assess servers, data centers, on-premises, and cloud-based virtual machines (VMs), as well as endpoint equipment like desktops, laptops, and Internet-connected devices.
- Pay close attention to network and server configurations that require resetting post-disaster.
2. Backup procedures assessment
- Ensure every critical system has a functional backup system in place.
- Regularly backup data and test procedures for restoring critical systems from these backups.
- Evaluate the likelihood of systems not recovering from backup and develop appropriate replacement strategies.
3. Downtime cost evaluation
- Understand the financial impact of potential downtime on production, revenue, brand reputation, and legal or regulatory compliance.
- Determine the value of preventive measures based on the estimated cost of downtime.
4. Regular policy and procedure review
- Continuously reassess contingency plans to adapt to changes in business operations, IT infrastructure, data collection, etc.
- Implement updates and revisions to policies and procedures as needed to ensure the plan remains current and effective.
- Review and revise the plan annually or biennially, or following significant changes in the business environment.
Compliance obligations and disaster recovery planning
Compliance obligations and disaster recovery planning intersect significantly, as many laws and regulations necessitate organizations to uphold effective disaster recovery and business continuity strategies.
Specific requirements vary, dictating what and how swiftly recovery must occur. For instance:
- The Sarbanes-Oxley Act (SOX) imposes liability on corporate officers of publicly traded firms for ensuring the presence of business continuity and disaster recovery plans.
- The Consumer Credit Protection Act (CCPA) mandates diligence concerning data availability in electronic funds transfers, including post-disaster at the point of sale.
- The Health Insurance Portability & Accountability Act (HIPAA) necessitates businesses handling protected health information (PHI) to maintain data backup, disaster recovery, and emergency mode operations plans.
- The Federal Information Security Management Act (FISMA) obliges federal government agencies and their contractors to ensure electronic data availability during crises.
- The NIST 800-53 cybersecurity standard offers comprehensive guidelines covering policy, procedures, plans, training, testing, and updating of disaster recovery plans.
Essential elements of a Disaster Recovery Plan
A Disaster Recovery Plan (DRP) is a vital component of an organization’s broader business continuity strategy, focusing specifically on the restoration of IT systems and operations following a catastrophic event.
A study by FEMA found that 20% of companies have no disaster recovery planning in place and 40 to 60% of small companies do not survive a major disaster.
A well-designed DRP encompasses more than just technology; it aims to enable the organization to swiftly rebound from disruptions, thereby minimizing downtime and losses.
Below are the key components that should be incorporated into an effective Disaster Recovery Plan, based on NIST guidelines:
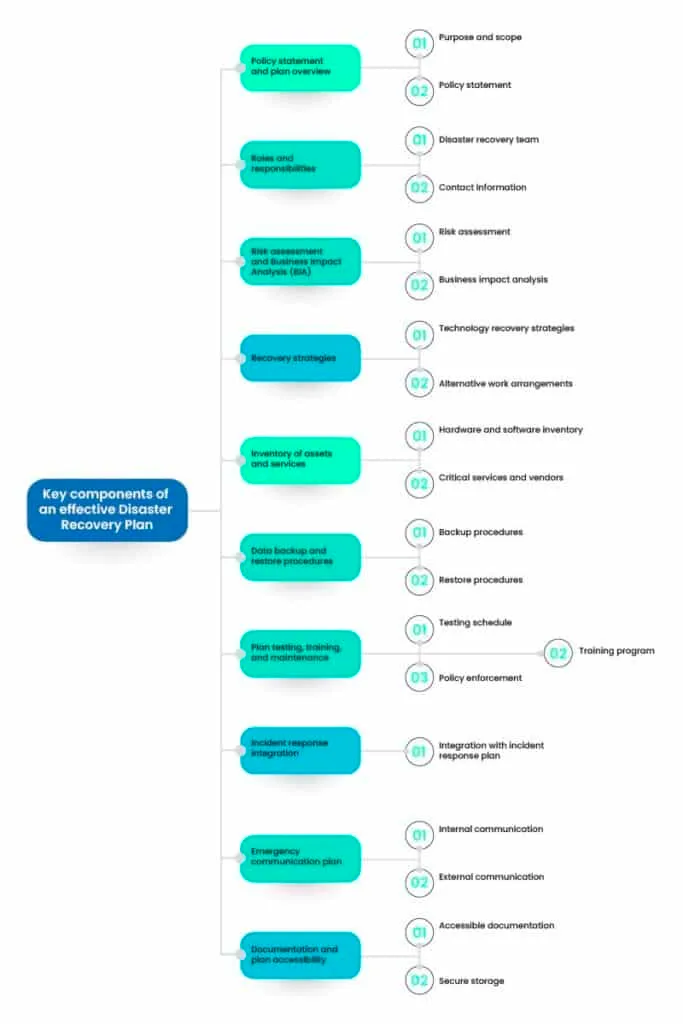
1. Policy statement and plan overview
- Purpose and scope: Clearly define the purpose, scope, and objectives of the disaster recovery plan, specifying the systems, processes, and functions it covers.
- Policy statement: Outline the guiding policy and principles governing the disaster recovery efforts, demonstrating management commitment.
2. Roles and responsibilities
- Disaster recovery team: Identify members of the disaster recovery team and delineate their roles and responsibilities, encompassing IT staff, management, and other key personnel.
- Contact information: Provide updated contact details for all team members and external contacts (vendors, emergency services, etc.) critical to the recovery process.
3. Risk assessment and Business Impact Analysis (BIA)
- Risk assessment: Identify potential threats and vulnerabilities leading to disasters, assessing their likelihood and impact.
- Business impact analysis: Determine critical business functions and their disruption impact, specifying the maximum acceptable downtime for each function.
4. Recovery strategies
- Technology recovery strategies: Develop strategies for restoring IT systems, applications, and data, encompassing off-site backups, cloud solutions, and redundancy measures.
- Alternative work arrangements: Plan alternative work setups in case the primary workplace is unavailable, such as remote work or a secondary location.
5. Inventory of assets and services
- Hardware and software inventory: Maintain an up-to-date inventory of all hardware and software, including versions, configurations, and dependencies.
- Critical services and vendors: List critical services and vendors, along with contact details and alternative options.
6. Data backup and restore procedures
- Backup procedures: Detail data backup procedures, specifying frequency, method, and storage locations.
- Restore procedures: Outline steps for restoring data from backups, ensuring quick recovery of critical systems.
7. Plan testing, training, and maintenance
- Testing schedule: Establish a regular testing schedule to ensure the DRP’s effectiveness and identify areas for improvement.
- Training program: Implement a training program for the disaster recovery team and staff to ensure everyone understands their roles and responsibilities.
- Maintenance schedule: Set up a schedule for regularly reviewing and updating the DRP to reflect changes in technology, business processes, and personnel.
8. Incident response integration
- Integration with incident response plan: Ensure seamless coordination between the disaster recovery plan and the broader incident response plan, facilitating a smooth transition from initial response to recovery.
9. Emergency communication plan
- Internal communication: Plan methods for communicating with employees during a disaster, including status updates and instructions.
- External communication: Determine communication channels for external parties, such as customers, suppliers, and the media.
10. Documentation and plan accessibility
- Accessible documentation: Ensure clear documentation of the disaster recovery plan, accessible to all relevant parties even during a disaster.
- Secure storage: Store plan copies in multiple secure locations, both on-site and off-site, to ensure accessibility and resilience.
An exhaustive Disaster Recovery Plan stands as a cornerstone in any organization’s resilience and continuity strategy. By encompassing these essential components, organizations bolster their readiness to respond adeptly to disasters, mitigating the ramifications on operations, reputation, and finances.
Regular testing, updates, and training are imperative to uphold the plan’s efficacy and adaptability within an evolving risk environment.
Through dedicated investment of time and resources into crafting a robust DRP, organizations adeptly navigate the trials of unforeseen disruptions, thereby sustaining their trajectory towards growth and prosperity.
Template for disaster recovery plan
To ensure confidence in the protection of your systems and data during a disaster and the swift restoration of functionality for your business, include the following sections in your recovery plan:
Streamline risk management with Scrut Automation
As your company expands, navigating the increasingly complex risk landscape becomes paramount. Scrut’s SmartGRCTM offers comprehensive solutions to manage your disaster recovery initiatives and ensure compliance with regulatory requirements. Moreover, it extends its support across numerous other programs and compliance standards.
Our compliance templates simplify self-assessments, while our intuitive dashboard provides a centralized overview of all your compliance frameworks. Identify vulnerabilities in your programs effortlessly and access guidance on resolving them.
SmartGRCTM by Scrut efficiently gathers and organizes associated documents, ensuring seamless access during audits. Schedule a demo today to discover how Scrut can enhance your risk management program.
Frequently Asked Questions
1. What is the purpose of developing a disaster recovery policy compliant with NIST guidelines?
Disaster recovery policies compliant with NIST guidelines serve to ensure that organizations have comprehensive plans in place to recover critical systems and data in the event of a disaster. By following NIST standards, organizations can enhance their resilience, minimize downtime, and protect sensitive information from loss or compromise.
2. What are the key components that should be included in a NIST-aligned disaster recovery template?
A NIST-aligned disaster recovery template should include essential components such as risk assessment procedures, recovery objectives, roles and responsibilities, communication protocols, backup and recovery strategies, testing and training plans, and documentation requirements. These components ensure that organizations have a systematic approach to disaster recovery that aligns with NIST guidelines.
3. How does NIST recommend organizations approach risk assessment in the context of disaster recovery planning?
NIST recommends that organizations conduct thorough risk assessments to identify potential threats and vulnerabilities that could impact their operations and data integrity. This involves assessing the likelihood and potential impact of various disaster scenarios, such as natural disasters, cyberattacks, or equipment failures. By understanding their risks, organizations can develop more effective disaster recovery strategies tailored to their specific needs.
4. What are some common challenges organizations face when implementing NIST-compliant disaster recovery policies, and how can they be addressed?
Common challenges organizations face when implementing NIST-compliant disaster recovery policies include resource constraints, lack of expertise, and resistance to change. These challenges can be addressed by securing adequate resources and expertise, conducting comprehensive training and awareness programs, and engaging stakeholders in the planning process. Additionally, organizations can leverage external resources such as consultants or industry best practices to overcome implementation challenges.
5. What are the benefits of aligning disaster recovery efforts with NIST standards, and how can it enhance organizational resilience?
Aligning disaster recovery efforts with NIST standards offers several benefits, including improved preparedness, enhanced compliance, and greater resilience. By following NIST guidelines, organizations can develop more robust and systematic disaster recovery plans that are aligned with industry best practices. This enhances their ability to recover from disruptions quickly and minimize the impact on operations, thereby strengthening organizational resilience in the face of adversity.
Table of contents


















