Choose risk-first compliance that’s always on, built for you.
Go back to blogs
How to Choose Governance, risk and compliance (GRC) Solutions/Tools in 2025?
Last updated on
March 19, 2025
22
min. read

A GRC platform helps you implement your InfoSec program conveniently. Otherwise, you would constantly be juggling between multiple spreadsheets.
There are hundreds of GRC tools available in the market, and it can become an issue on where to start.
If you have already shortlisted a few GRC tools, the next step is to select one.
In case you are still searching for what GRC options are available in the market, check this list of top GRC tools.
Once you have shortlisted a few GRC tools, let’s proceed on to choose one.
In this article, we will show you how to evaluate the capabilities of a GRC platform.
How to Select a GRC Software?
Though GRC tools vary in use cases, the following features are present in most GRC applications:
- Implementing policies
- Vendor risk management
- Employee security awareness
- Cloud security monitoring
- Risk management
- Compliance management
While choosing a GRC software, you must consider your company’s size, pain points, budget, deployment complexity, and other unique requirements.
It also provides different workflows with processes and procedures to manage policies in your organization which streamlines your organization’s regulations and compliance.
First things first…
… determine your goals and assess your needs.
Before going into the market looking for a GRC solution, you must know why you need it.
- Do you want to renew your compliance with existing frameworks?
- Do you want to get compliant with new frameworks?
- Do you want to strengthen your risk and compliance posture?
- Do you want to implement a GRC program from scratch or automate your existing GRC programs?
Choosing a GRC tool starts with understanding your organization’s objectives. Depending on your objective, you can outline your requirements and assess your governance, risk management, and compliance needs.
You should collaborate and discuss the GRC requirements with all internal stakeholders in order to get a comprehensive assessment. You can have various departments that determine collective needs.
Factors to Consider While Evaluating the GRC Tools
Consider the GRC platform along these factors.
1. Evaluate the Workflow Automation Capability
A GRC tool should provide such automation capabilities that increase the efficiency of the GRC program.
It helps you do certain things which otherwise would be very time-consuming. For example, sending reminders to those employees who have not completed their security awareness training.
Apart from the automatic reminders, a GRC tool with a large number of integrations can help in automating:
- Collection of evidence
- Detection of misconfigurations
- Mapping policies and controls with different frameworks
- Sending alerts for compliance deviations
- Employee training
- Risk management
- Vendor risk assessment
- Quick launch of policies
- Task management
Apart from this, they can smoothen your audit process.
GRC should be capable of extending application capabilities for employees to access libraries, upload compliance evidence, and file and archive documents to avoid any compliance mistakes.
Evidence collection is a time-consuming, repetitive, and manual process.
The automation capabilities from an evidence-collection perspective largely depend on the number of integrations the GRC platform has with other tools. Integrations enable you to automate different tasks in your GRC program.
Now, let us understand this with the example of smartGRC—our own GRC platform—that helps GRC teams efficiently manage their workflows.
Scrut smartGRC
Scrut smartGRC helps you to reduce manual effort by up to 75% and increases accountability and pace of InfoSec task completion. You can automate and streamline the monotonous audits-related tasks, from preparation to analysis to effective collaboration with the auditors.
All this can be done through one single window using Scrut smartGRC.

- Scrut smartGRC keeps you informed about the overall status of your GRC program.
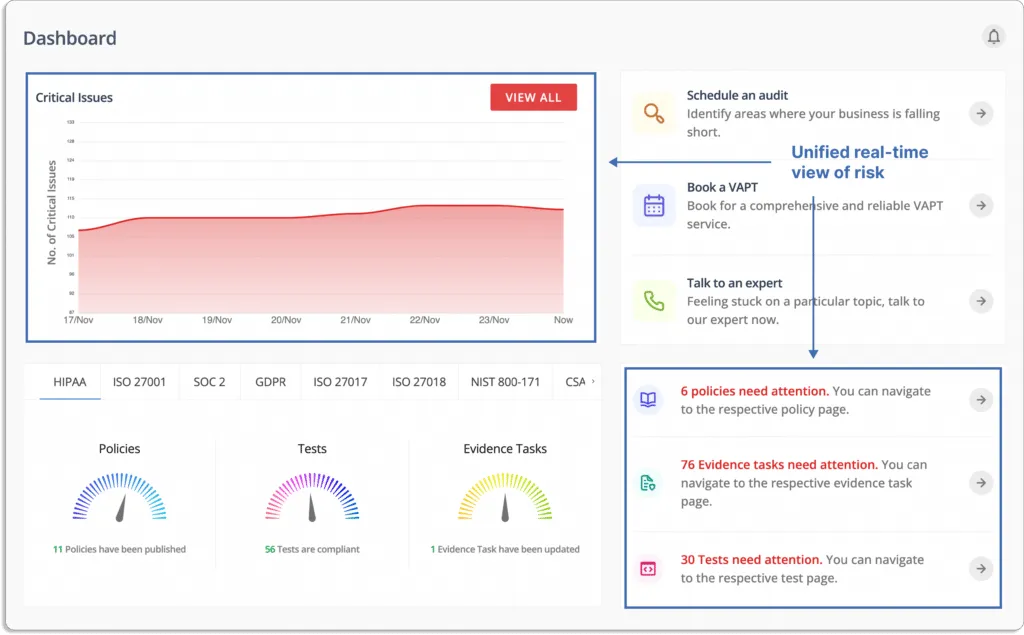
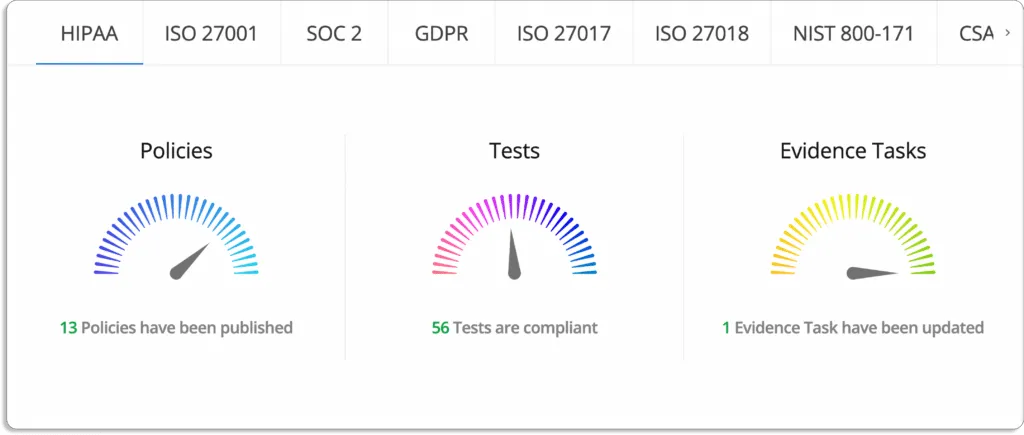
- Scrut smartGRC reduces the burden of evidence collection with integrations. It integrates across application landscapes such as HRMS, endpoint management, and other tools to automate the manual evidence collection process.
Scrut offers over 70+ integrations.

Check the complete list of integrations.
- Scrut smartGRC allows you to collaborate with your team members. You can assign tasks to your team members as well as be updated on the different task statuses. The platform sends reminders for pending tasks to ensure no one misses the deadlines.
- Semi-automate audits: Invite your auditors directly to the platform. Scrut allows smooth collaboration with your auditors. You can directly communicate with them on the platform.
Auditors from Scrut’s partner network are well-versed in the platform. They can quickly finish the audit—as all the required policies, controls, and evidence are in one place.
This eases the whole audit process and reduces the audit time to about a few hours (2-4 hours) from 1 week via the traditional way

- Eliminate duplication of efforts with automatic mapping of artifacts to multiple frameworks:
When going through multiple standards and regulations, you can avoid duplication of efforts. Scrut automatically maps artifacts to all the standards you want to comply with.
Suppose you create the Password Policy for ISO 27001, it’ll automatically get mapped to relevant frameworks, PCI DSS and SOC 2 in this case.
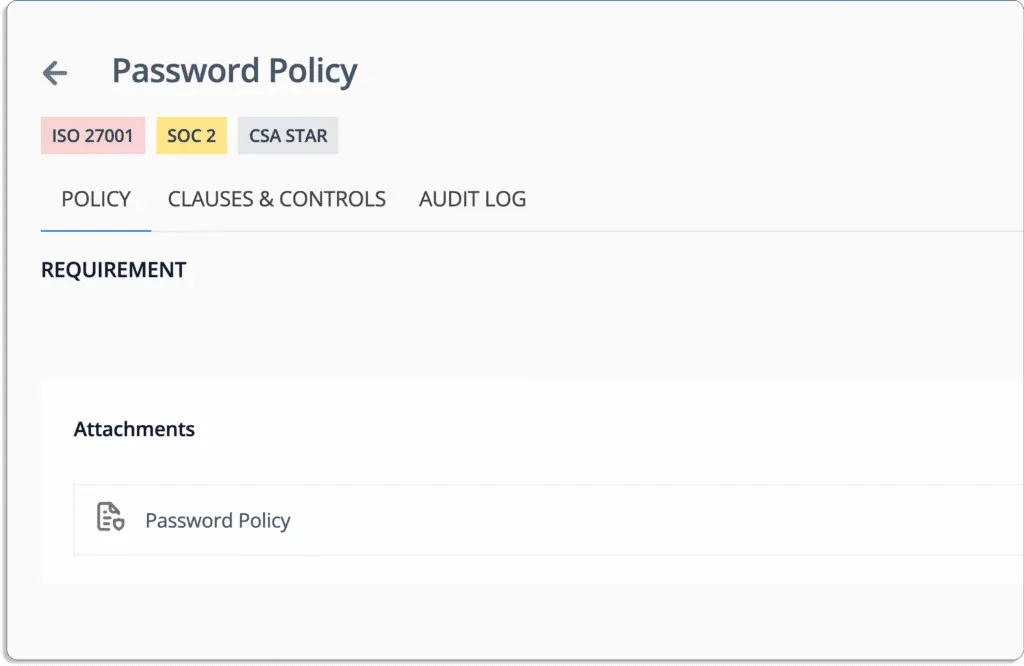
This means that you can do the work once and need not worry about creating and mapping the policy thrice for all the standards separately.
Scrut smartGRC helps you get compliant with 20+ frameworks off-the-shelf. This includes all popular frameworks: SOC 2, ISO 27001, GDPR, CCPA, HIPAA, and PCI DSS.
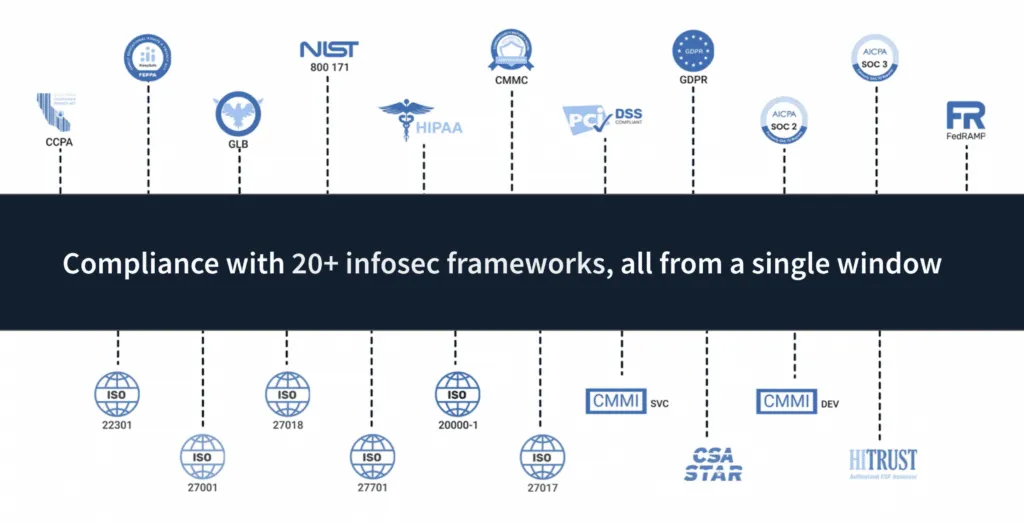
And we set this up very swiftly. For one of our customers that works with US federal agencies, it took us 3 business days to set up 11 frameworks.
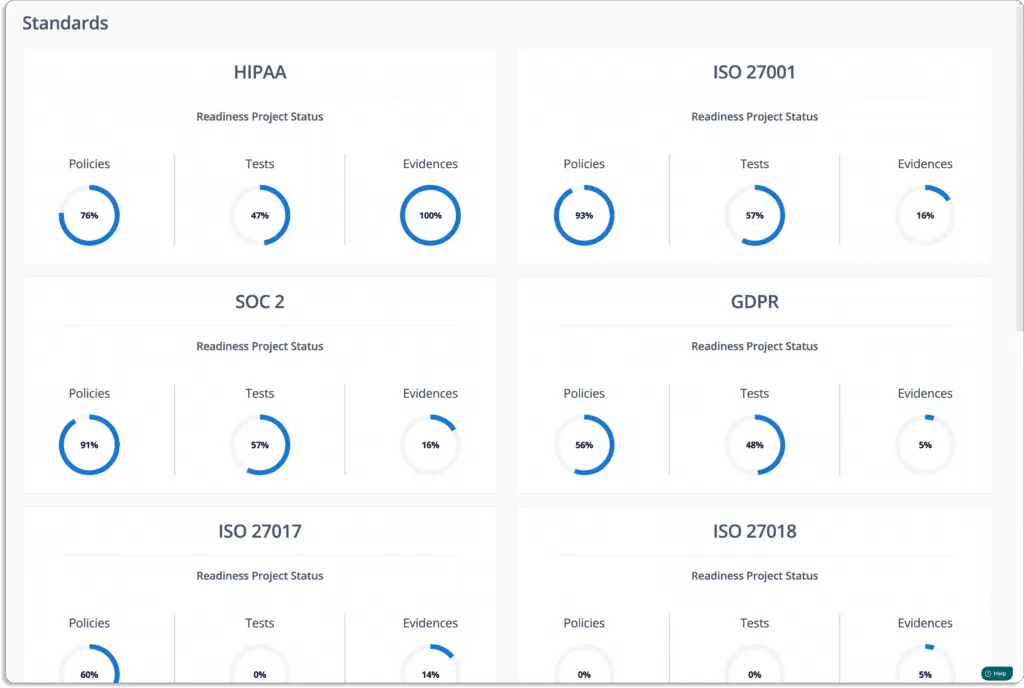
2. Understand the Cloud Monitoring Capability
Now, most companies that go for standards like SOC 2, ISO 27001, FedRAMP, and GDPR, sell some sort of cloud-based software.
To build trust among your customers, vendors, investors, and government authorities, you must stay compliant with the security and privacy frameworks. These are implemented via policies and controls as a way to show that you take security and privacy seriously.
Thus, if you use any cloud platform, like AWS, GCP, Azure, etc., then your GRC platform must have cloud monitoring capabilities.
An effective GRC platform should provide continuous CIS benchmarking. The Center for Internet Security (CIS) Foundations Benchmarks cover identity management, logging, monitoring, networking, access management, etc., and are available for most cloud providers, like AWS, GCP, Azure, Oracle, and IBM Cloud.
Scrut smartGRC does continuous cloud security monitoring to help you stay compliant and proactively fix cloud misconfigurations. The tool ensures your cloud accounts don’t drift out of compliance.
Scrut Cloud Security monitors over 200 cloud controls across popular cloud service providers (AWS, GCP, Azure, and Oracle).
Scrut helps you to implement the best security policies consistently across your hybrid and multi-cloud infrastructure. This establishes full-stack security for all your cloud-native deployments across compute instances, databases, containers, and serverless.
Scrut continuously monitors your cloud accounts and detects misconfigurations.
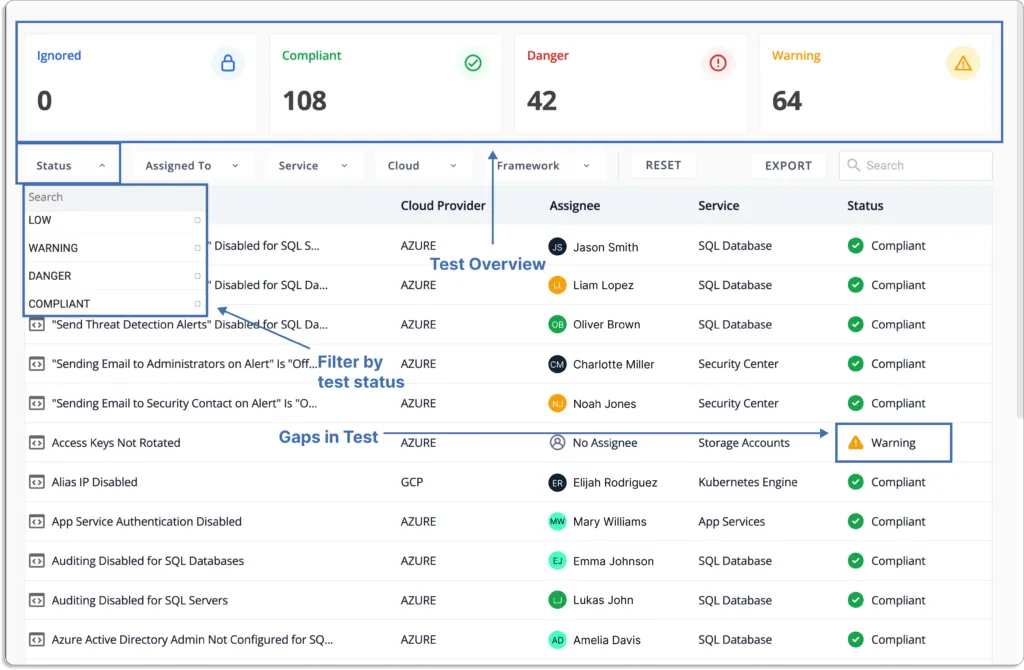
It also provides actionable items for remediation to help you fix issues faster.
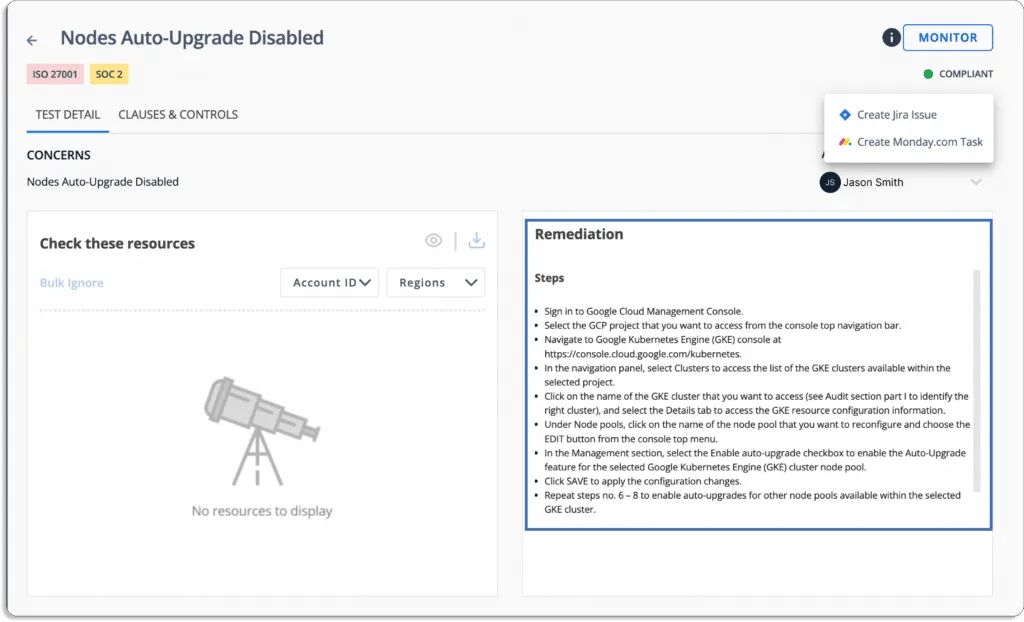

Businesses frequently deploy various cloud security measures, threat monitoring tools, vulnerability scanners, and other technologies to manage their risks.
Furthermore, Scrut integrates with SIEM tools—Datadog and Splunk, as well as XDR tools like Crowdstrike. It integrates with Qualys, AWS Inspector, and Tenable for vulnerability management. Scrut also complements this with human offensive testers (pentesters) who are permanent members of our team.
3. Security awareness training for employees
Security is always a concern for organizations. They want to remain safe from unauthorized access to systems.
Phishing, malware, and ransomware are some of the issues that organizations face. Data breaches are largely caused by employee mistakes. Thus, employees should know how to avoid these things to be more secure from leaving any loophole during accessing organizational tools.
The best way to avoid this is to guide your employee’s standard security practices by adhering to basic guidelines for any security measures.
GRC platforms can ease this out for you in different ways. GRC platforms, like Scrut, offer pre-built courses for employee information security training. Most of the time, these are made by industry experts, so you don’t need to do the heavy lifting of training all the employees yourself.
You can just add them to the GRC platform and they can go through the training materials and acknowledge the security policies of the company.
This self-serve model enables employees to get well-versed with all they need to understand potential risks and avoid making mistakes (like clicking on phishing emails).
Let’s see the workflow of Scrut.
As you onboard an employee, they get an email asking them to sign on to the platform for training.
Once they log in, they see a dashboard like this with all the policies.
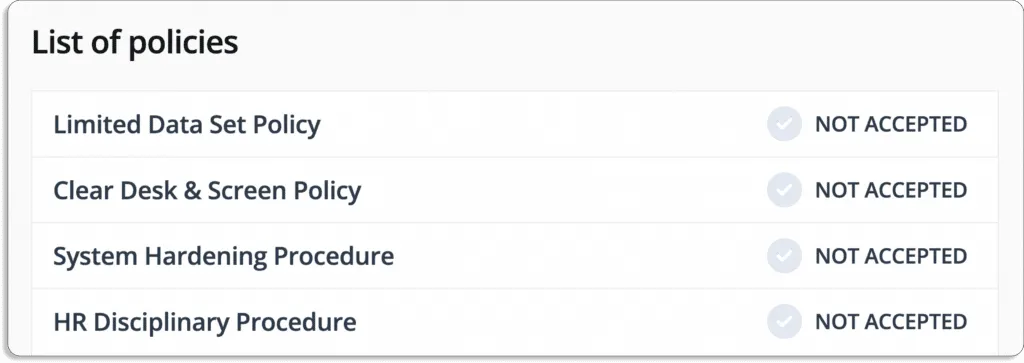
Employees can go through policy by policy and acknowledge the same and the overall status with change.
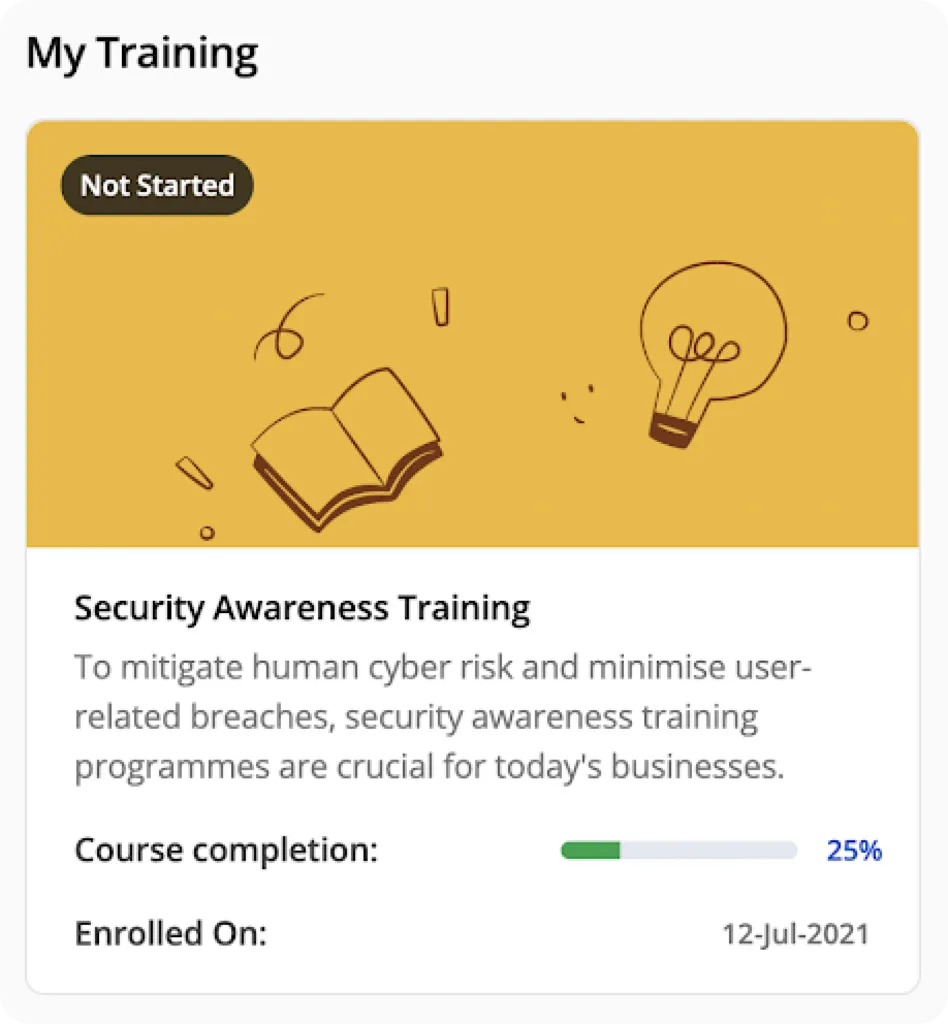
As an admin, you’re always aware of the overall aspects of employees’ training programs. You can conduct quizzes at the end, to make sure they have actually understood the policies, not just skimmed through them.
A minimum threshold score guarantees that your employees are informed and prepared to handle threats.
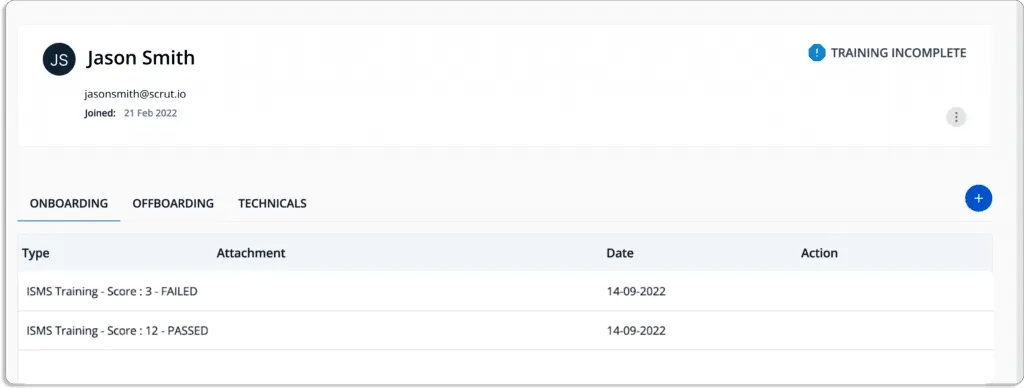
See the score of an employee who first failed, then went through the training, and finally passed.
4. Risk management capability
One of the major use cases of GRC software is risk management. Without proper risk management, you cannot establish governance in your organization or stay compliant.
Organizations face many risks, which include thefts, business downturns, accidental data loss, lawsuits, or data breaches.
A GRC tool helps implement different control measures to deal with these risks. It provides continuous monitoring of the risks associated with the system environments. Generally, a GRC tool can help you with
- Risk identification: The risk identification process documents the risk that could disturb an organization’s streamlined flow. This is the first step in the risk management process, where the organization identifies and understands potential risks.
Identify and understand under which category risks fall. These risks can be related to geopolitical, operational, legal, financial, environmental, cyber, and more.
At the end of this step, you build your risk register with all the risks associated with your business documented in one place, along with their categories.
Once you do this, you need to see their impact.
- Risk assessment: Once you identify a risk, the next step is understanding how it affects your organization.
The risk assessment includes analyzing and evaluating the risk associated with the event for its likelihood and the severity of damage caused in case the event takes place.
Risk = Likelihood * Impact
Risk assessment is a must for passing the audits for standards like SOC 2, ISO 27001, etc.
We have seen companies not using any GRC platforms facing issues like:
- Not understanding how to conduct a risk assessment
- Submitting an incomplete risk assessment report to their auditors, causing issues in audits
- Doing risk assessments at the last minute
The process doesn’t end at risk assessment, which brings us to our last step.
- Risk remediation: After the risk assessment process, you should work on the risks. Not managing the risks that can result in negative consequences, like an actual data breach or reputation loss.
An efficient GRC platform automatically informs you on risk treatment, thus saving a lot of time in researching how to deal with these risks.
Furthermore, a GRC tool keeps you updated on your risk posture.
Now, let us continue with our Scrut example.
Scrut Risk Management provides actionable insights in the context of your business processes to assist you in effectively identifying, assessing, and treatments of IT and cyber risks.
Scrut Risk Management dashboard gives you a birds-eye view of your risk posture.
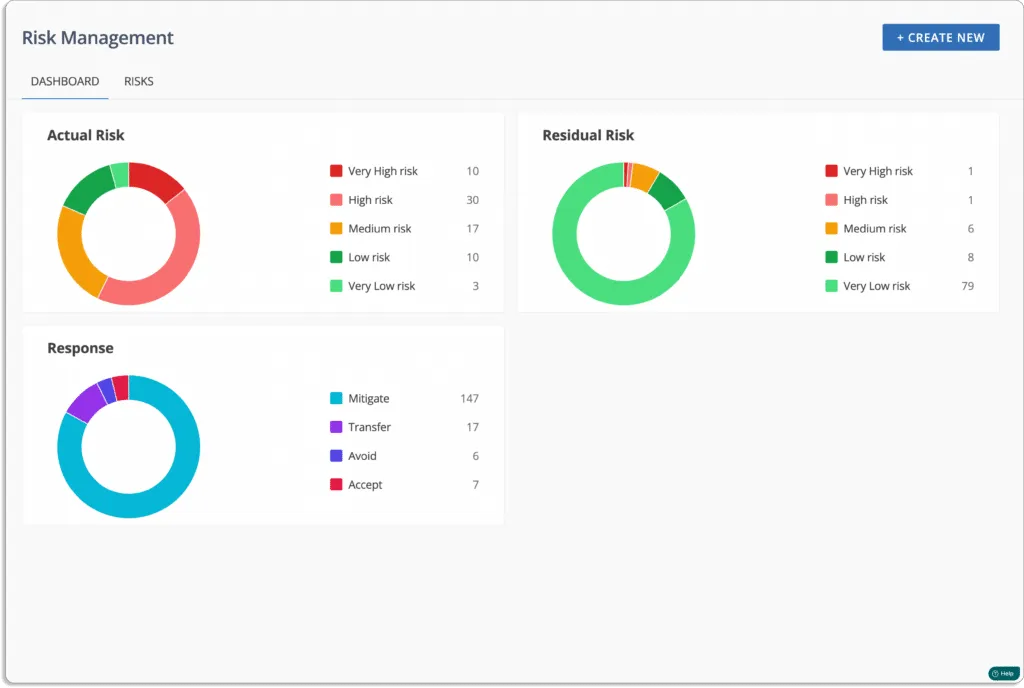
To automate your risk identification, Scrut scans your ecosystem to identify risks across the code base, infrastructure, applications, vendors, employees, and access.
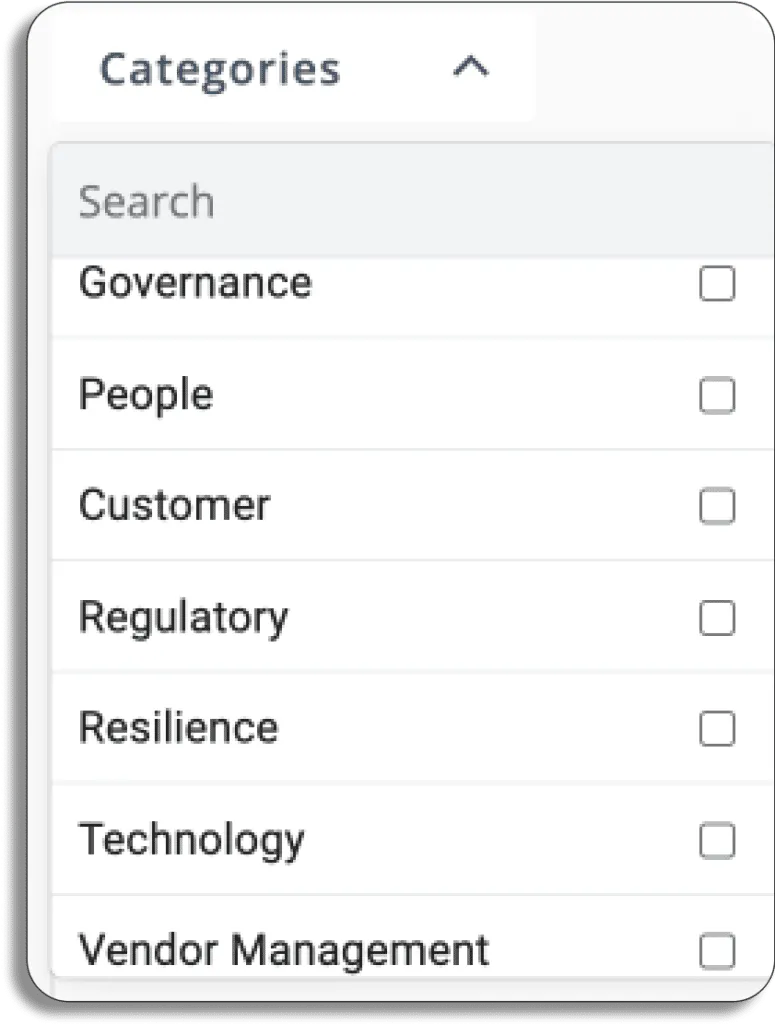
Then, you can choose from Scrut’s library of the most common risks across seven categories.
The Scrut’s risk categories are Governance, People, Customer, Regulatory, Resilience, Technology, and Vendor Management.
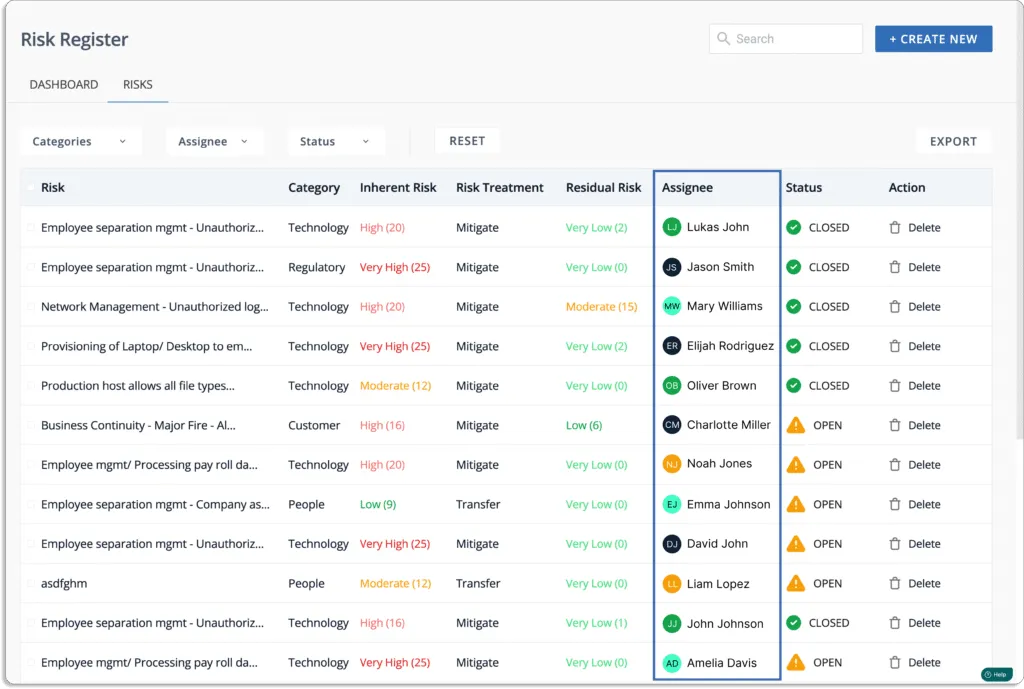
This helps to build your risk register in a few minutes.
Likewise, you can begin your risk assessment in a few minutes by cutting out the numerous hours spent developing and mapping risks, threats, controls, and related tasks.
You can choose the likelihood and impact on a scale of 0 to 5.
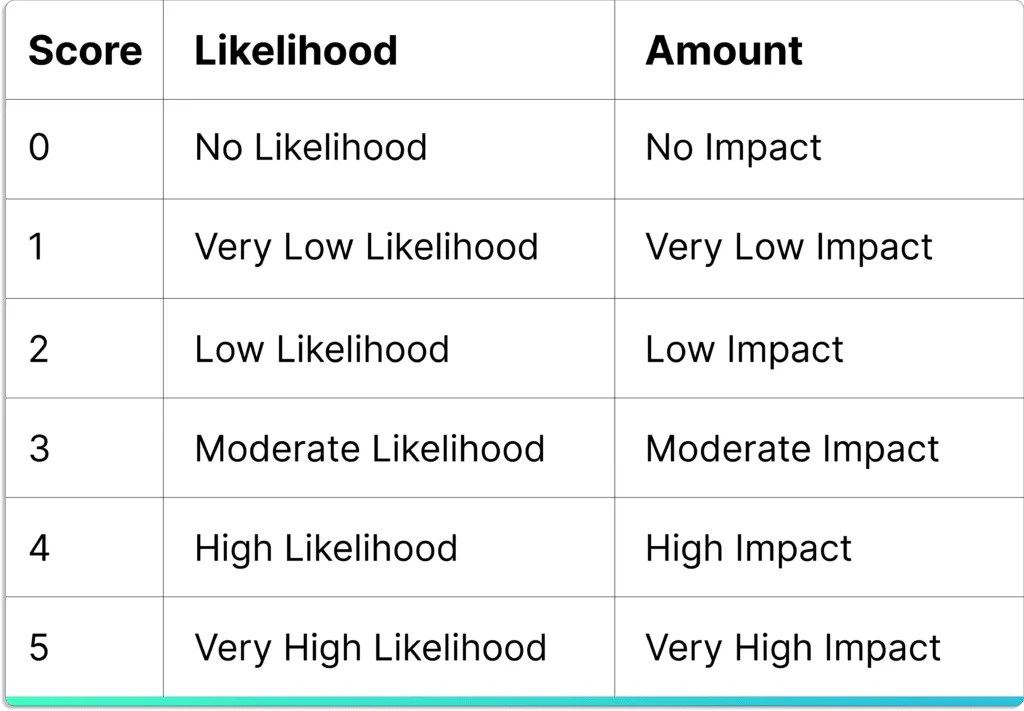
Risk scoring of events based on likelihood and impact.
Then, you get the inherent risk of the event as a multiplication of these two factors.
The final score lies between 0 – 25.
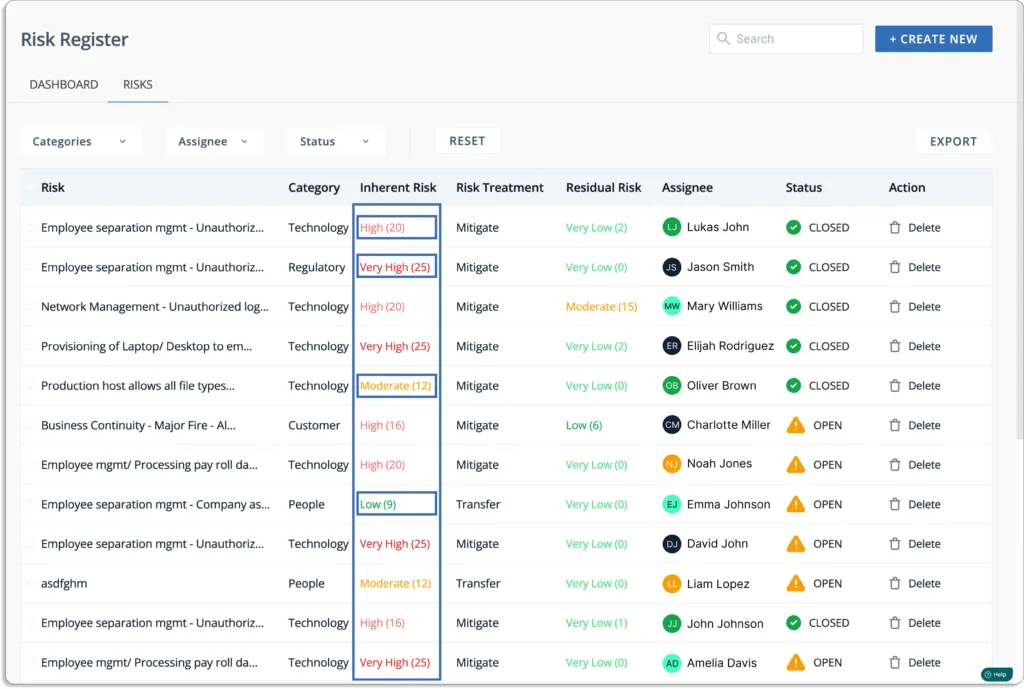
This is how to understand these inherent risk scores:
- 0 – 5 – Very Low
- 6 – 10 – Low
- 11 – 15 – Moderate
- 16 – 20 – High
- 21 – 25 – Very High
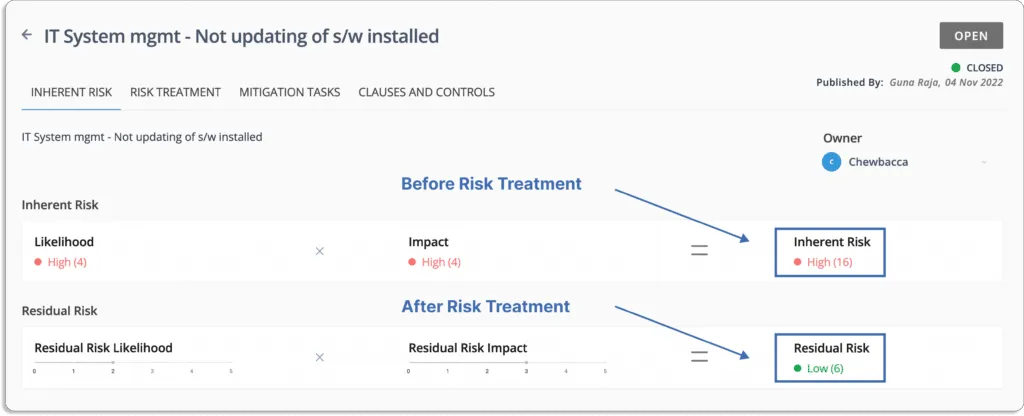
For example, in the screenshot shown below, the risk is outdated software applications.
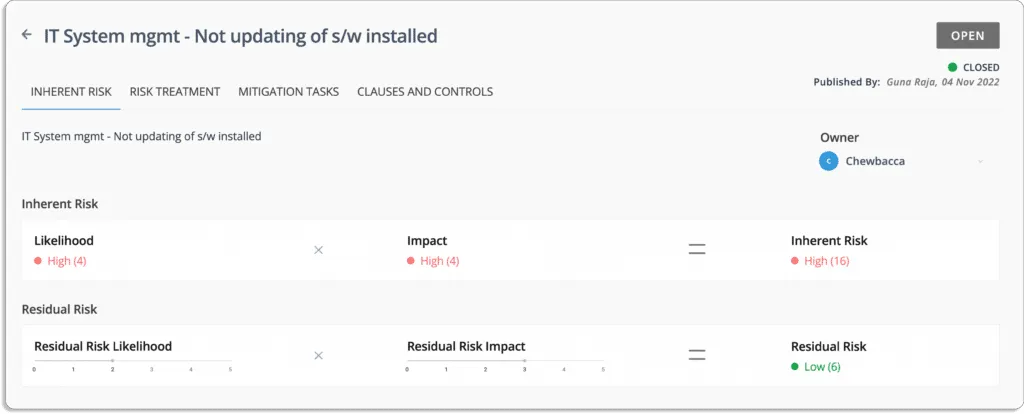
The likelihood of this event = 4 (high)
The impact in case the event occurs = 4 (high)
Thus, the inherent risk associated with this event is also high (score 16= 4*4).
Furthermore, Scrut Risk Management maps all these events to different frameworks and controls automatically.
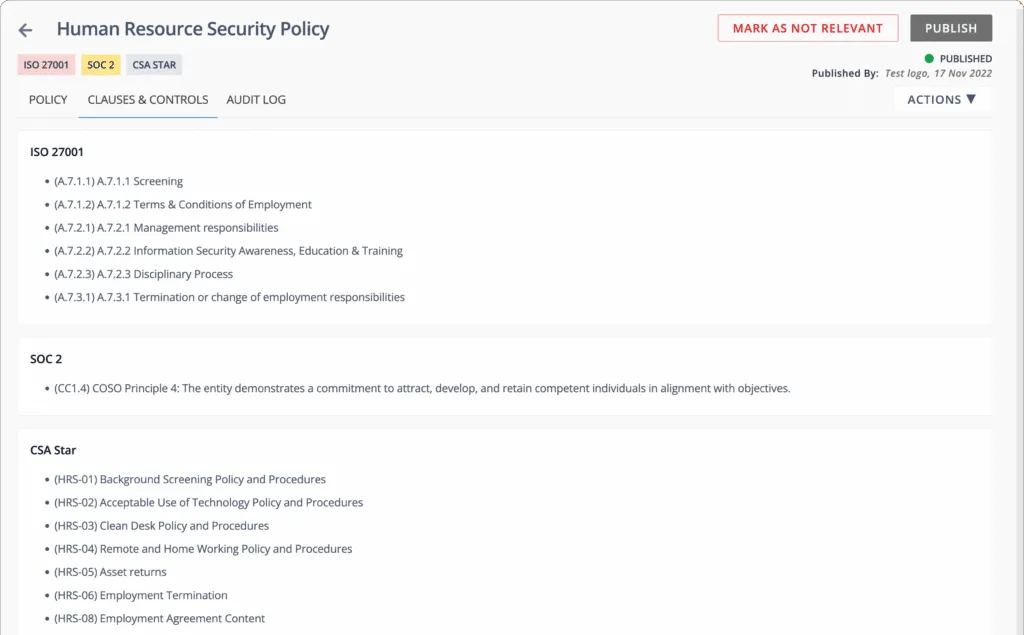
Automated Mapping of Risks with Frameworks and Controls
At this step, you get a visual overview of your risk profile.
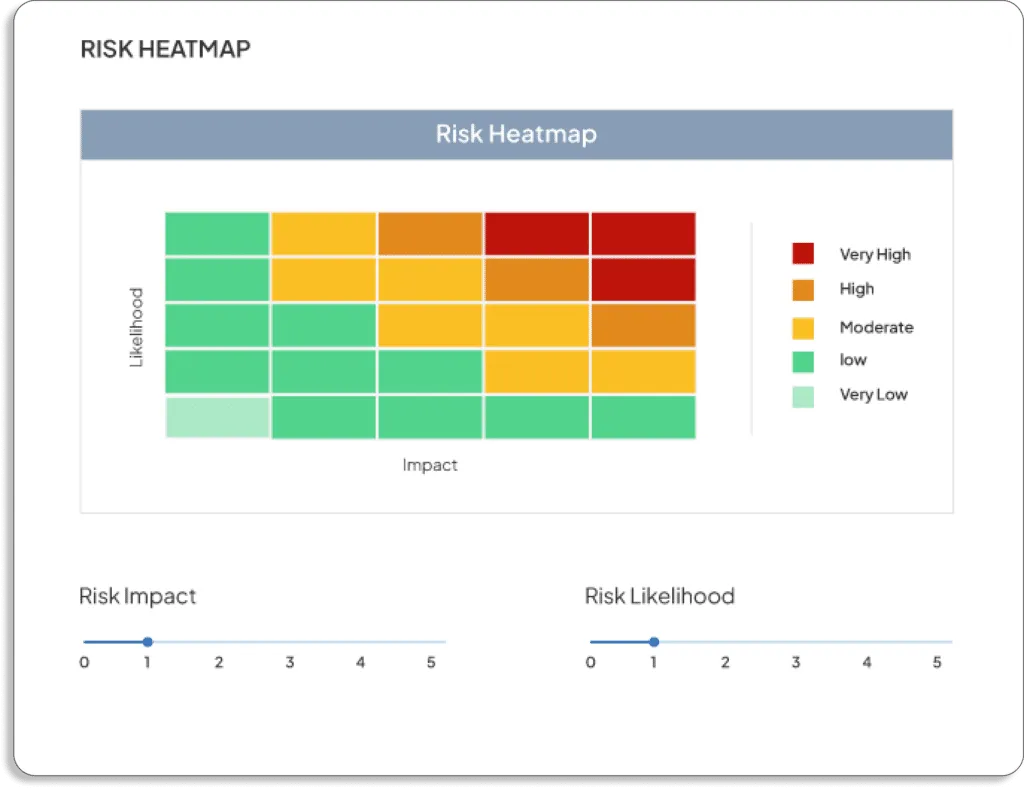
Risk Heat Map
Additionally, Scrut provides you with action items for carrying out risk treatment.
There are 4 ways of risk treatment:
- Remediation
- Mitigation
- Transference
- Acceptance
To continue with our example, the treatment for the software not being updated is to mitigate it since you cannot entirely eliminate this risk.
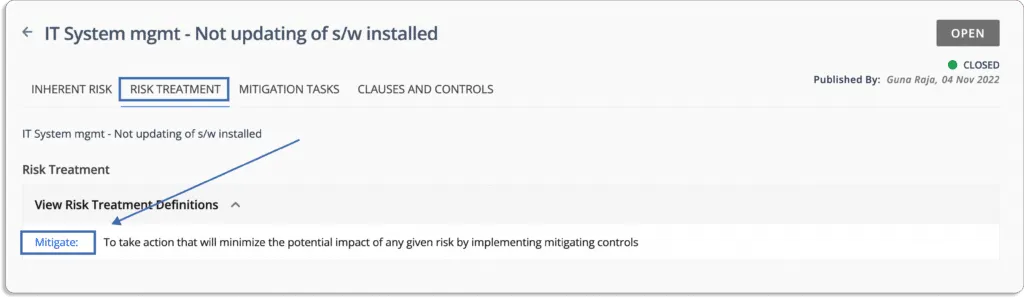
Once you treat the risks, you get the updated score (residual score) for all the risky events at once place.
For risk treatment, you can assign risks to team members. This helps you with easy risk distribution.
When risk mitigation occurs, a risk owner must ensure that required controls are in place to reduce the risk level. Scrut continuously monitors events that may lead to an increase in risk levels and data breaches.
For more details on working on risk management, refer to this post.
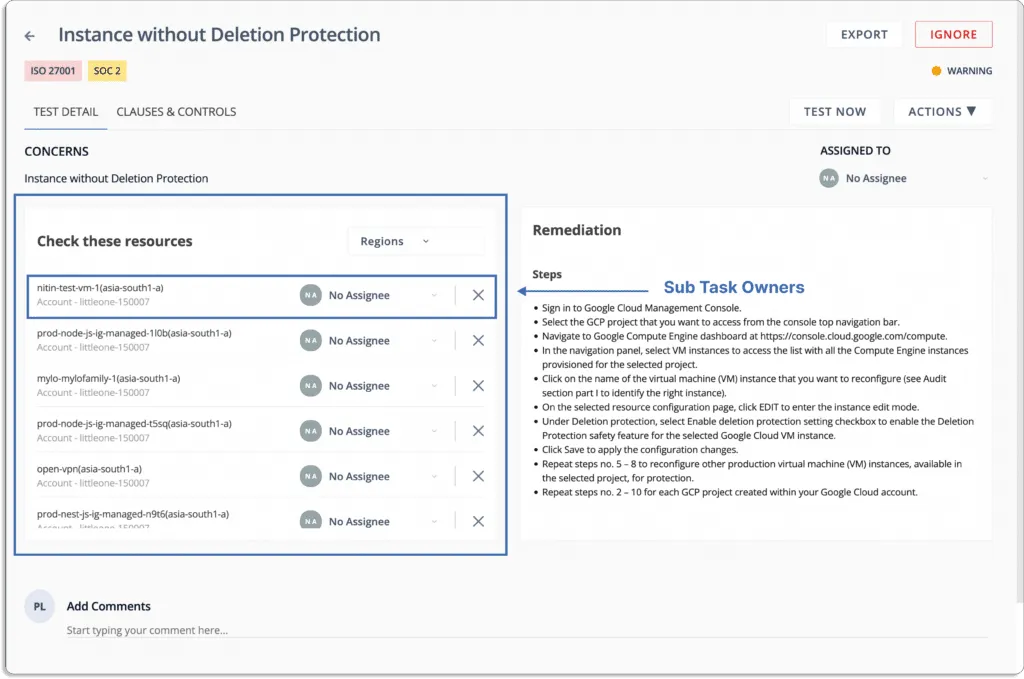
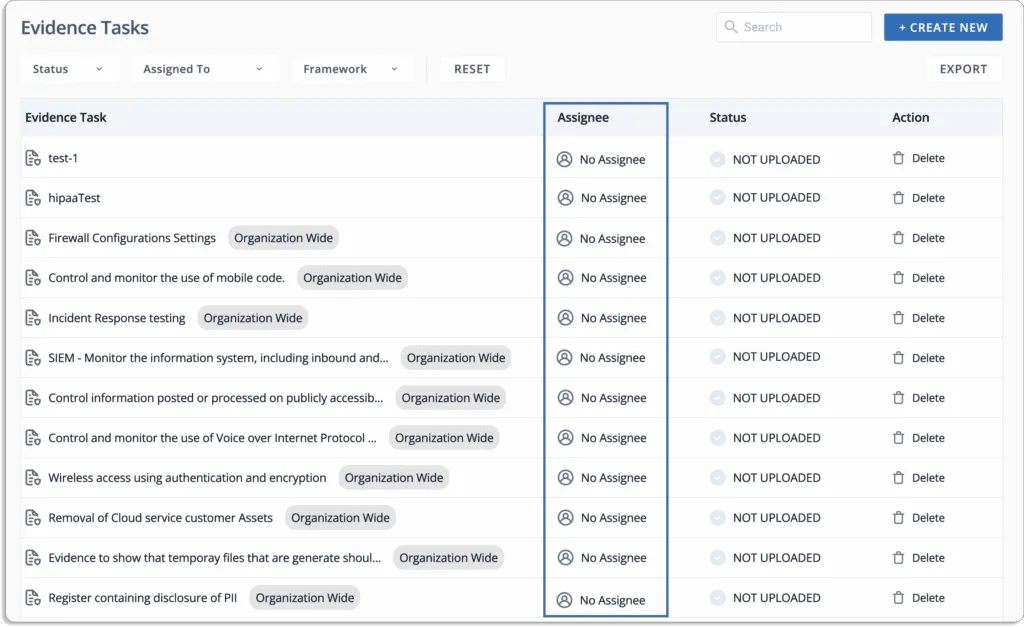
5. Task management (ownership/accountability)
A GRC tool should have a proper system to store, manage, and track your organization’s policies and controls related to security and compliance frameworks.
Many tasks can be assigned to different teams.
This ensures both tasks are done correctly, and someone is accountable to do the same in time.
Almost all the major tasks can be distributed.

6. Vendor risk management
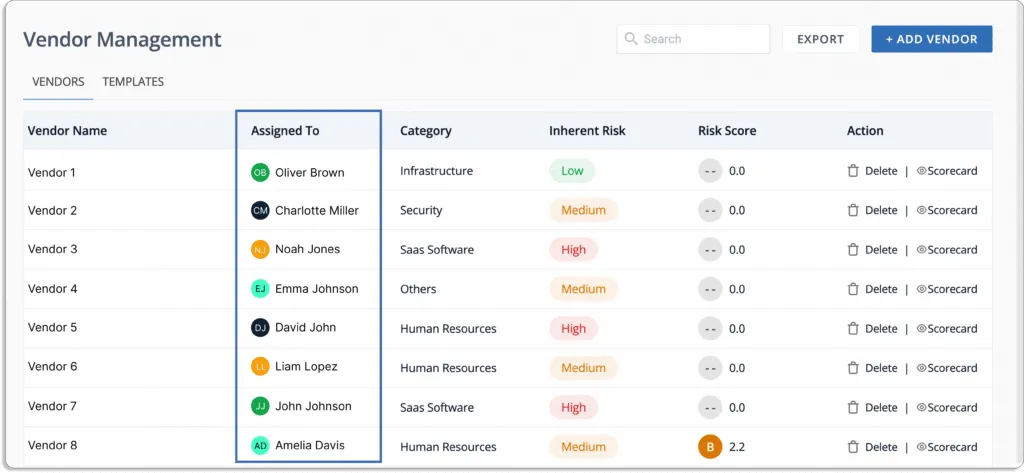
GRC tools help you discover third-party risks associated with vendors, partners, contractors, or service providers.
Vendor risk management is critical for safeguarding an organization, its customers, and all proprietary information. Auditors expect an organization to have information on how secure its vendors are in order to achieve compliance.
If your vendor lacks a needed standard assessment for a specific framework, then it will be challenging for your organization to achieve certification against your aspired compliance certifications.
In the absence of vendor risk management, you can expose your organization to risk. For instance, an outage on the vendor’s side can cause a financial/operational impact on your organization.
From vendor onboarding to offboarding, a GRC tool takes care of the security. It identifies the vendors, evaluates and assesses risks associated with the vendor, and mitigates risks.
Moreover, it provides continuous monitoring and, after vendor onboarding, removes every access to secure the environment and eliminate any vulnerabilities that can lead to data breaches.
Now, let’s see how Scrut helps with vendor risk management.
Scrut helps you to evaluate, monitor, and manage risks associated with your vendors. You can understand the security postures of your vendors with the help of Scrut. This enables you to find out whether a vendor fits your compliance needs or not.

Scrut helps you streamline your vendor compliance check with security questions. You can create your own custom questionnaire or use any of our pre-built templates.
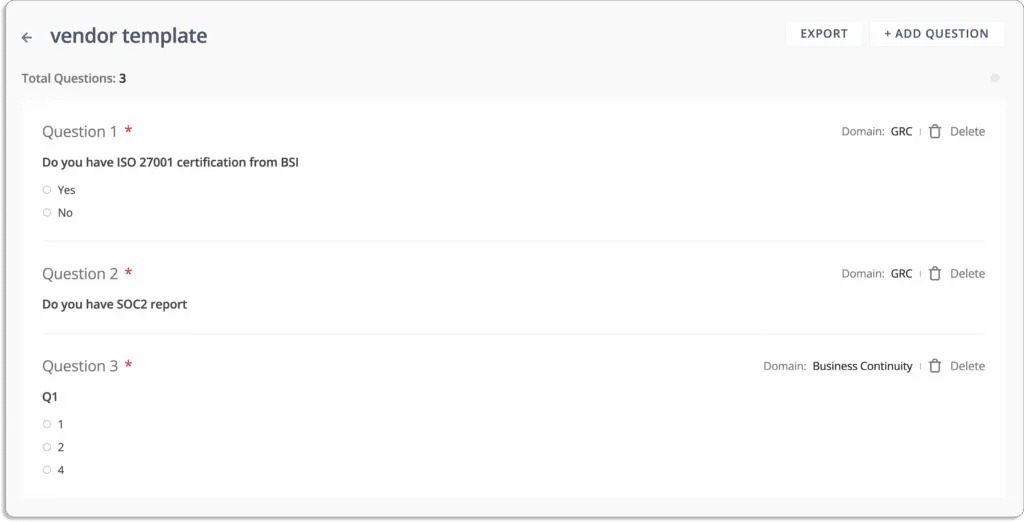
In this way, you can send these questionnaires to your vendors for security reviews and get their responses in one place.
This helps you accelerate vendor security reviews, which in turn helps in quick decision-making.
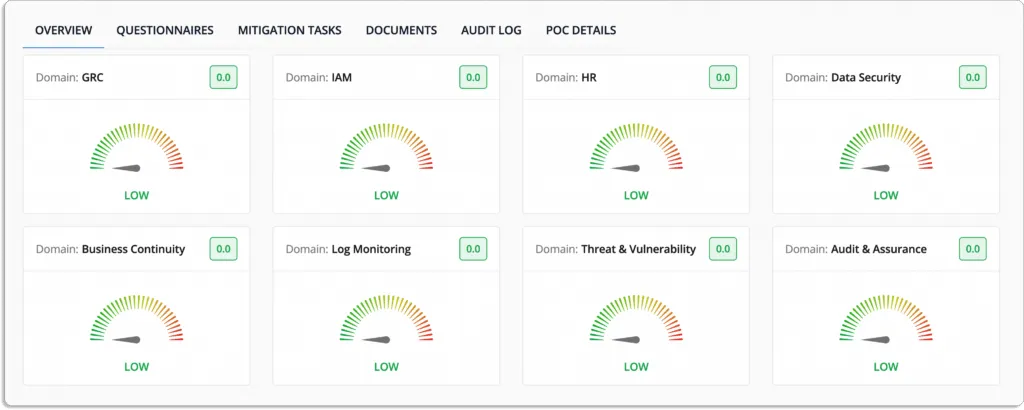
Scrut acts as a central storage system for all information related to vendor security, that includes certificates, vendor audits, and paperwork.
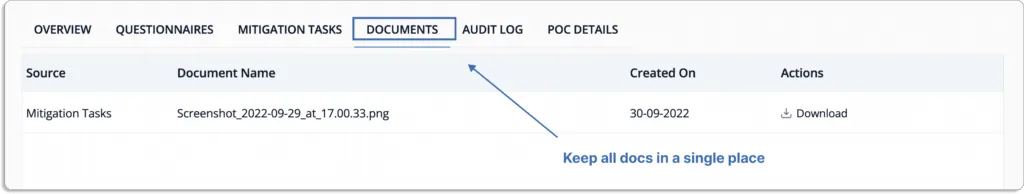
You can share vendors’ responses with customers and auditors seamlessly from the platform. Thus you can assess risks for all your vendors.
At last, Scrut also manages proof of compliance for you. You can directly provide auditors access to the platform to check vendor security reports.
Don’t Stop at the GRC Tool. Go Beyond the Features
GRC software is readily available from different vendors, but you need to analyze and compare vendors to get the best GRC.
Here are two more things to keep in mind while choosing a GRC vendor.
1. How Easy it is to Get Started
Scrut smartGRC has pre-built policies aligned with popular security and privacy frameworks. These policies are made by industry experts.
So you can get started quickly.
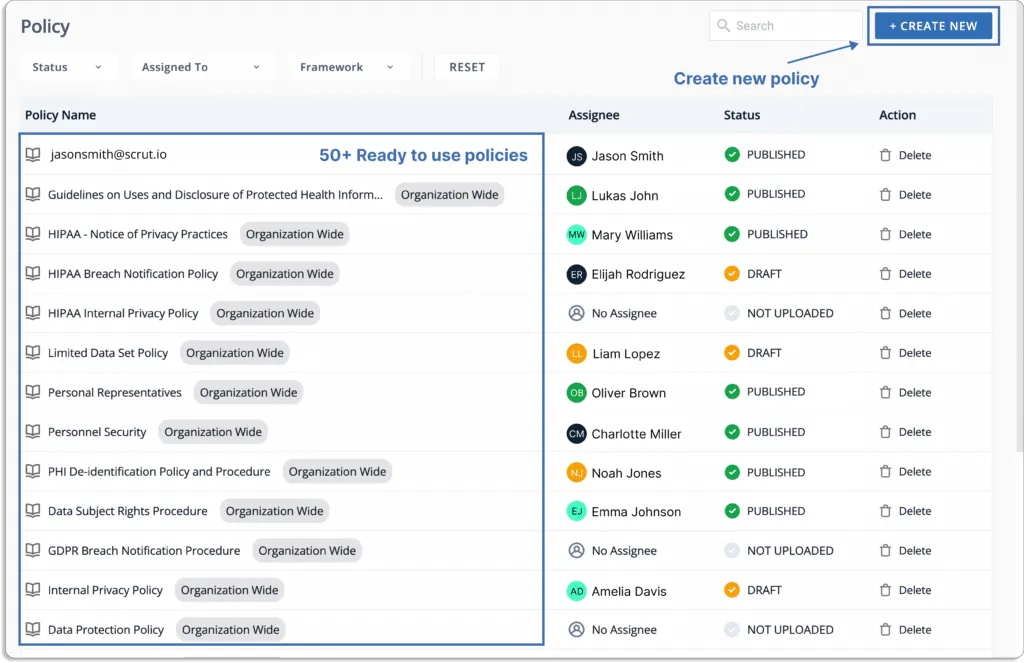
Further, you can customize these policies as per your requirements with Scrut’s built-in inline policy editor.
2. Customer support
Customer support is a vital part of any deal. Most GRC vendors have a customer success team that maintains a relationship with their customers to mitigate any problems that occurs.
You should understand the customer support of your chosen GRC platform. It will ensure if any risk occurs, then you can recover your system immediately.
Scrut has a team of experts to help you with any problem related to GRC. You can schedule meetings and review your systems to detect any GRC-related anomalies at your convenience.
See some of Scrut’s customer reviews on G2.

Table of contents


















