In today’s increasingly data-driven world, understanding the nuances between different types of sensitive information is crucial for maintaining compliance and safeguarding privacy. For CEOs and top executives, a solid grasp of Protected Health Information (PHI) and Personally Identifiable Information (PII) is a legal obligation and a strategic imperative.
This blog aims to clarify the distinctions between PHI and PII for CEOs, especially in the context of Health Insurance Portability and Accountability Act (HIPAA) compliance. This will help executives grasp how they impact data protection strategies and regulatory adherence.
This clarity is crucial for CEOs to effectively oversee compliance efforts, implement robust data security measures, and mitigate risks associated with sensitive information. Understanding these distinctions will empower leaders to make informed decisions and foster a culture of compliance within their organizations.
Understanding PHI and PII
In this section, we’ll explore the definitions of PII and PHI, their scope, and their significance.
What is PHI?
PHI refers to any health information that can be used to identify an individual and is maintained or transmitted by a covered entity or its business associate in any form—whether electronic, paper, or oral.
Under the HIPAA, PHI encompasses a wide range of personal health data, including but not limited to:
- Medical records: Detailed information about a patient’s medical history, treatments, and diagnoses.
- Test results: Laboratory results and other diagnostic information.
- Health insurance information: Details about a patient’s health insurance coverage and claims.
- Patient IDs: Unique identifiers assigned to individuals within a healthcare system.
The importance of PHI lies in its sensitive nature; unauthorized access or disclosure of this information can lead to privacy violations, financial penalties, and damage to an organization’s reputation.
For startups in the healthcare or health-tech sectors, protecting PHI is not just about compliance but also about maintaining trust with patients and clients. These startups often handle substantial amounts of PHI, making them prime targets for breaches and emphasizing the need for stringent security measures.
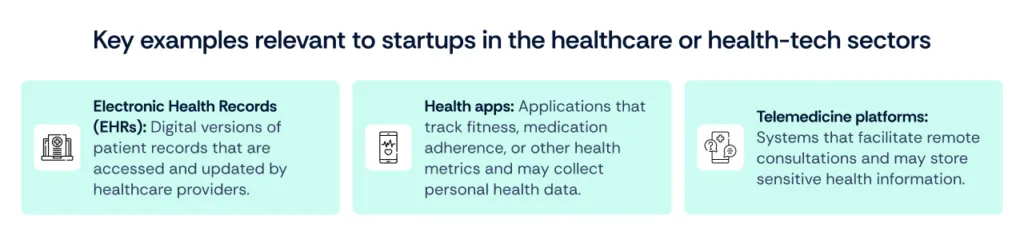
What is PII?
PII is any data that can be used to identify an individual, either on its own or when combined with other information. While PII is broader than PHI and includes various types of personal data, it is not necessarily health-related.
Key elements of PII include:
- Names: Full names or aliases.
- Addresses: Home addresses, email addresses, or phone numbers.
- Social security numbers: Unique identifiers issued by the government.
- Financial information: Credit card numbers, bank account details, and financial records.
The importance of PII lies in its potential for misuse if compromised.
Identity theft, financial fraud, and privacy invasions are just a few risks associated with the unauthorized access or exposure of PII.
For various business sectors—whether retail, finance, or technology—protecting PII is crucial to maintaining customer trust and ensuring compliance with regulations like the GDPR or CCPA.
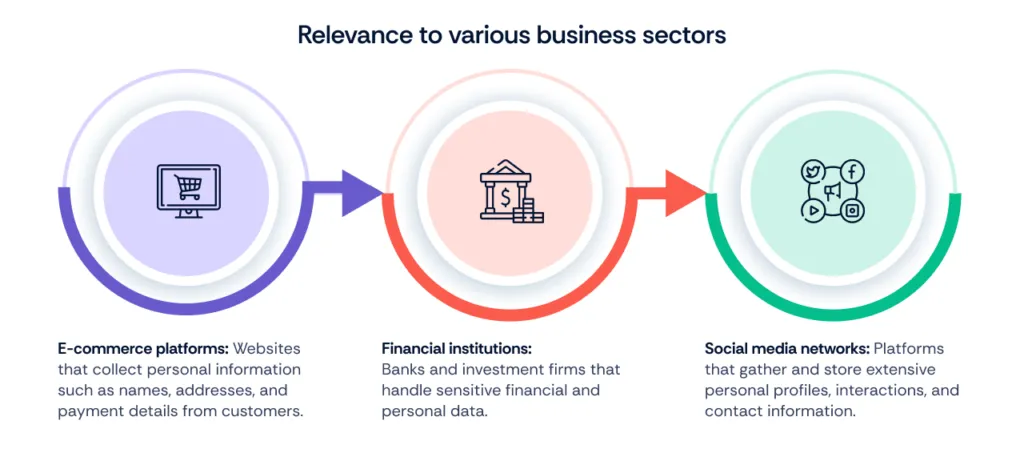
Understanding both PII and PHI is essential for CEOs to oversee comprehensive data protection strategies, ensure compliance with applicable laws, and safeguard their organizations against the risks associated with sensitive information.
Also read: Which entities are covered under HIPAA?
Key similarities: PHI vs PII
While pii and phi overlap in aspects such as data sensitivity, privacy and security measures, and regulatory compliance, they require distinct handling.
Key differences: PHI vs PII
Understanding the key differences between pii and phi is crucial for ensuring proper data protection and compliance with relevant regulations. Here’s how the two differ.
Also read: How to map HIPAA to ISO 27001?
Practical implications for CEOs

1. Risk management
Mishandling pii and phi exposes organizations to serious risks, including substantial legal penalties, financial losses, and significant damage to their reputation.
Key risks include:
- Data breaches: Unauthorized access to or disclosure of sensitive information can result in significant financial and legal consequences. Data breaches often lead to legal actions, customer lawsuits, and costly remediation efforts.
- Non-compliance fines: Failing to comply with regulations such as HIPAA for PHI or GDPR and CCPA for PII can lead to hefty fines and sanctions. Non-compliance can also trigger audits and investigations by regulatory bodies, compounding financial and operational impacts.
- Erosion of customer trust: Mishandling personal data undermines trust and damages relationships with customers. Once trust is lost, it is difficult to regain, leading to potential loss of business and negative public perception.
To effectively manage these risks, CEOs should:
- Implement robust data protection measures: Deploy advanced security technologies such as encryption, multi-factor authentication, and secure data storage solutions. Ensure that access to sensitive data is restricted and monitored to prevent unauthorized access.
- Conduct regular risk assessments: Continuously evaluate potential risks and vulnerabilities through regular risk assessments and security audits. Identify areas where your data protection measures may be lacking and address them promptly.
- Ensure comprehensive employee training: Provide ongoing training for employees on data privacy and security best practices. Employees should be aware of the importance of safeguarding sensitive information and understand their role in maintaining data protection.
- Continuously evaluate and update protocols: Data protection is an evolving field, and new threats emerge regularly. Regularly review and update your security protocols and practices to adapt to new risks and technological advancements. This proactive approach helps ensure that your organization remains resilient against evolving threats.
By focusing on these aspects of risk management, CEOs can better protect their organizations from the significant consequences of mishandling pii and phi, ensuring both compliance and the security of sensitive data.

2. Organizational policies
Developing and enforcing comprehensive policies is crucial for safeguarding PHI and PII. This involves creating detailed procedures for data handling, establishing access controls, and implementing incident response plans.
Regularly reviewing and updating these policies is essential to ensure they remain effective in the face of evolving regulations and emerging threats. Clear and enforceable policies help ensure compliance and protect sensitive data from unauthorized access or breaches.
3. Strategic focus
Incorporating pii and phi protection into your startup’s strategy is vital. This means prioritizing data security and regulatory compliance in all operational decisions.
Allocate resources to invest in necessary technologies, such as encryption and secure storage solutions, and provide ongoing training for staff on data privacy best practices.
By embedding data protection into the core of your business strategy, you create a culture of privacy awareness and build a strong foundation for trust with your customers.

PII and PHI in the context of HIPAA
How do PHI and PII differ in the context of HIPAA regulations?
PHI includes medical records and personal health information under HIPAA, whereas PII generally refers to personal details like names and addresses.
A key difference is that PHI is protected under HIPAA, while PII may not be, depending on the context. To delve deeper, consider how each type of data is ultimately safeguarded or utilized in various sectors.
Startups must familiarize themselves with core HIPAA requirements, including safeguarding PHI through secure handling, storage, and transmission.
To meet HIPAA standards, implement practical measures such as encryption, access controls, and employee training on data privacy and security.
Regularly monitor compliance through internal audits and maintain ongoing vigilance to ensure adherence to HIPAA standards and address any issues promptly.
Also read: HIPAA Audit Trail Requirements
Checklist to prioritize focus on data protection and compliance
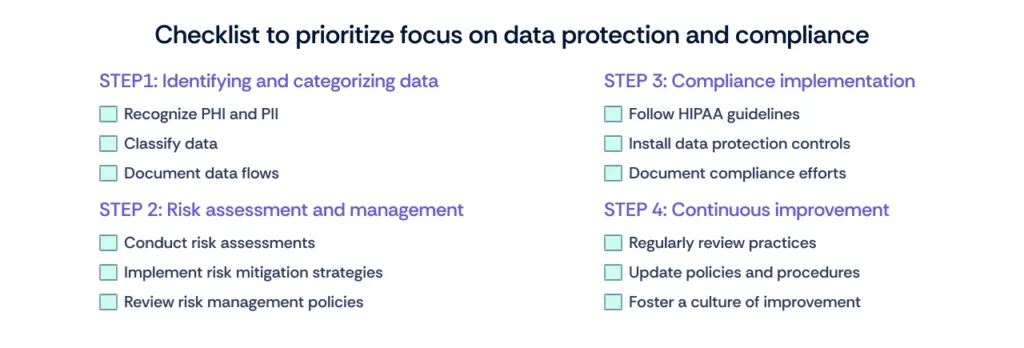
1. Identifying and categorizing data
- Recognize PHI and PII: Identify all types of data that fall under PHI and PII within your organization.
- Classify data: Categorize data based on sensitivity and regulatory requirements to determine appropriate handling and protection measures.
- Document data flows: Track how pii and phi move through your systems to ensure proper oversight and security.
2. Risk assessment and management
- Conduct risk assessments: Regularly evaluate risks associated with PHI and PII, including potential vulnerabilities and threats.
- Implement risk mitigation strategies: Develop and apply strategies to address identified risks, such as enhancing security measures or revising procedures.
- Review risk management policies: Continuously update risk management policies to adapt to new threats and changes in data handling practices.
3. Compliance implementation
- Follow HIPAA guidelines: Ensure all HIPAA compliance measures are implemented, including secure data handling and employee training.
- Install data protection controls: Implement technical and administrative controls to protect PHI, such as encryption and access restrictions.
- Document compliance efforts: Keep thorough records of compliance activities and controls for audits and regulatory reviews.
4. Continuous improvement
- Regularly review practices: Periodically assess and refine data protection practices to address emerging risks and regulatory changes.
- Update policies and procedures: Modify data protection policies and procedures as needed based on feedback, audit results, and evolving best practices.
- Foster a culture of improvement: Encourage ongoing education and awareness among staff about data protection and compliance to support continuous improvement.
Also read: Who enforces HIPAA?
Wrapping up
In summary, understanding the differences between PHI and PII, adhering to their respective compliance requirements, and implementing best practices are crucial for safeguarding sensitive data. It’s essential to stay proactive about data protection to mitigate risks and ensure compliance.
For expert guidance on HIPAA and related requirements, contact Scrut. We can offer you comprehensive support and solutions.
Frequently Asked Questions
1. What are the key differences between PHI and PII?
PHI (Protected Health Information) refers specifically to health-related data protected under HIPAA, including medical records and personal health details.
PII (Personally Identifiable Information) is a broader category that includes any information that can identify an individual, such as names, addresses, and Social Security numbers.
PHI is a subset of PII, focused on health information, whereas PII encompasses a wider range of personal data.
2. How do compliance requirements for PHI differ from those for PII?
Compliance with PHI is governed by HIPAA (Health Insurance Portability and Accountability Act), which sets strict standards for safeguarding health information. PII compliance varies by jurisdiction and regulation, such as GDPR (General Data Protection Regulation) in the EU and CCPA (California Consumer Privacy Act) in California, each with its own requirements for data protection and privacy.
3. What are the best practices for managing PHI and PII in a startup?
Best practices include implementing robust data protection measures such as encryption and access controls, conducting regular risk assessments, ensuring comprehensive employee training on data privacy, and maintaining clear, updated privacy policies. Additionally, startups should regularly review and update their security protocols to adapt to new threats.
4. How can a startup effectively mitigate risks associated with mishandling pii and phi?
To mitigate risks, startups should adopt strong data protection measures, such as encryption and secure data storage, and implement strict access controls. Regularly conducting risk assessments and internal audits helps identify and address vulnerabilities. Ensuring that employees are well-trained in data privacy practices is also crucial. Staying proactive and updating security measures based on evolving threats is essential for effective risk management.
5. What should be included in a checklist for prioritizing PHI and PII protection?
A checklist for PHI and PII protection should include identifying and categorizing sensitive data, conducting regular risk assessments, implementing compliance measures specific to PHI and PII, and establishing data protection controls. It should also include continuous monitoring and auditing practices to ensure ongoing compliance and improvement.





































