Choose risk-first compliance that’s always on, built for you.
Go back to blogs
Navigating risk: Critical vs. high-risk vendor dynamics
Last updated on
January 18, 2024
14
min. read

In today’s complex business environment, effective vendor management is paramount for ensuring the smooth functioning of operations.
As businesses increasingly rely on external partners to deliver goods and services, the distinction between critical and high-risk vendors becomes crucial.
By understanding these distinctions, businesses can develop targeted strategies to navigate potential challenges and optimize their vendor ecosystems.
This blog aims to unravel the intricacies of vendor relationships, shedding light on the differences between vendors classified as critical and those deemed high-risk.
Foundational elements of risk
Let’s begin by delving into the foundational elements of risk, focusing on two primary characteristics:
Criticality
Criticality centers on the business impact a vendor may have. This classification distinguishes vendors based on their potential to significantly affect your organization or its customers in the event of a business interruption or failure.
Every vendor is categorized as critical or non-critical. Critical vendors demand inclusion in your business continuity and disaster recovery planning, mandating appropriate insurance coverage and a well-defined exit plan in case termination or replacement becomes necessary.
Inherent Risk
Inherent risk assesses the level of risk inherent in the relationship, gauging the types of risks associated with the provided product or service.
Typically categorized as high, moderate, or low, inherent risk ratings measure risk before any risk mitigation tools, processes, or techniques are applied. These ratings aid in determining the extent of activities required for effective risk identification and management in the vendor relationship.
Inherent risk evaluation encompasses various risk types, including compliance, financial, information security, privacy, reputational, and geopolitical risks, each contributing to an overall understanding of risk exposure.
Defining critical vendors
Critical vendors are the backbone of a company’s daily operations, providing goods or services that are integral to its core functions. These vendors have a direct impact on the organization’s ability to meet its objectives and maintain operational efficiency.
Examples of critical vendors may include key suppliers, technology providers, or service partners whose contributions are vital to the overall success of the business.
Recognizing the significance of critical vendors lays the foundation for implementing specific risk management strategies tailored to their unique role in the business ecosystem.
Characteristics that categorize vendors as critical risk
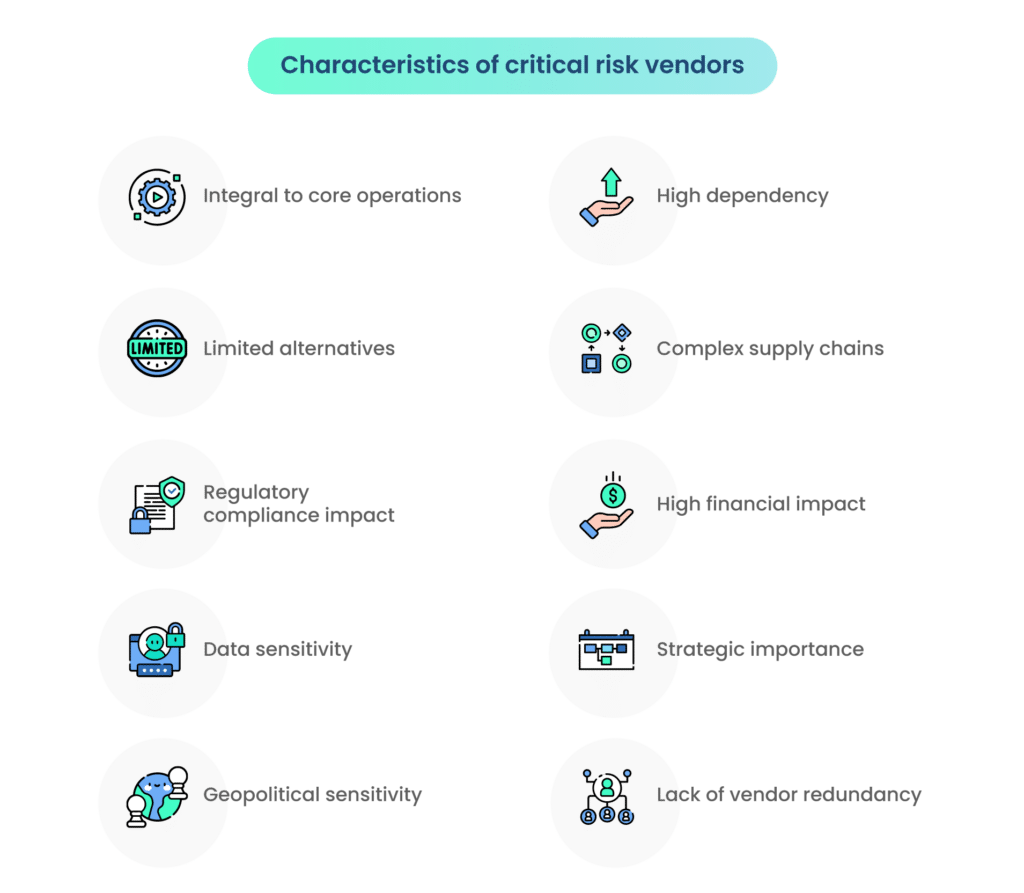
Vendors categorized as critical risk possess specific characteristics that signify their potential to significantly impact an organization if their operations face disruptions. These characteristics include:
- Integral to core operations: Critical risk vendors play a fundamental role in an organization’s core operations, providing goods or services that are essential for daily functioning.
- High dependency: The organization has a high dependency on critical risk vendors, and any disruption in their services could lead to severe operational or financial consequences.
- Limited alternatives: There are limited or no readily available alternatives for the goods or services provided by critical risk vendors, making it challenging to replace them swiftly in case of disruptions.
- Complex supply chains: Critical risk vendors are often part of complex supply chains, and their failure could have cascading effects on various interconnected processes within the organization.
- Regulatory compliance impact: Non-compliance by critical risk vendors could lead to severe consequences, including legal and regulatory repercussions, affecting the organization’s overall compliance status.
- High financial impact: Financial stability is a critical factor. If a critical risk vendor faces financial instability or insolvency, it could result in significant financial losses for the organization.
- Data sensitivity: Vendors handling sensitive data or intellectual property are often categorized as critical risk, as any compromise in data security could have far-reaching consequences for the organization.
- Strategic importance: Critical risk vendors align strategically with the organization’s objectives, and their uninterrupted performance is vital for achieving key business goals.
- Geopolitical sensitivity: Vendors operating in geopolitically sensitive regions or countries may pose additional risks, especially if political or economic instability could impact their ability to deliver goods or services.
- Lack of vendor redundancy: Critical risk vendors may lack redundancy in their operations, meaning there are no backup plans or alternative vendors readily available to step in during disruptions.
Defining high-risk vendors
In contrast to critical vendors, high-risk vendors pose potential threats that may not manifest immediately but could lead to significant problems if not managed carefully.
Vendors are often classified as high-risk based on a combination of characteristics and factors that signal potential challenges and vulnerabilities.
Understanding these characteristics and contributing factors allows businesses to proactively assess and manage the risks associated with vendors, enabling effective vendor risk management strategies and mitigating potential disruptions.
Characteristics that categorize vendors as high-risk
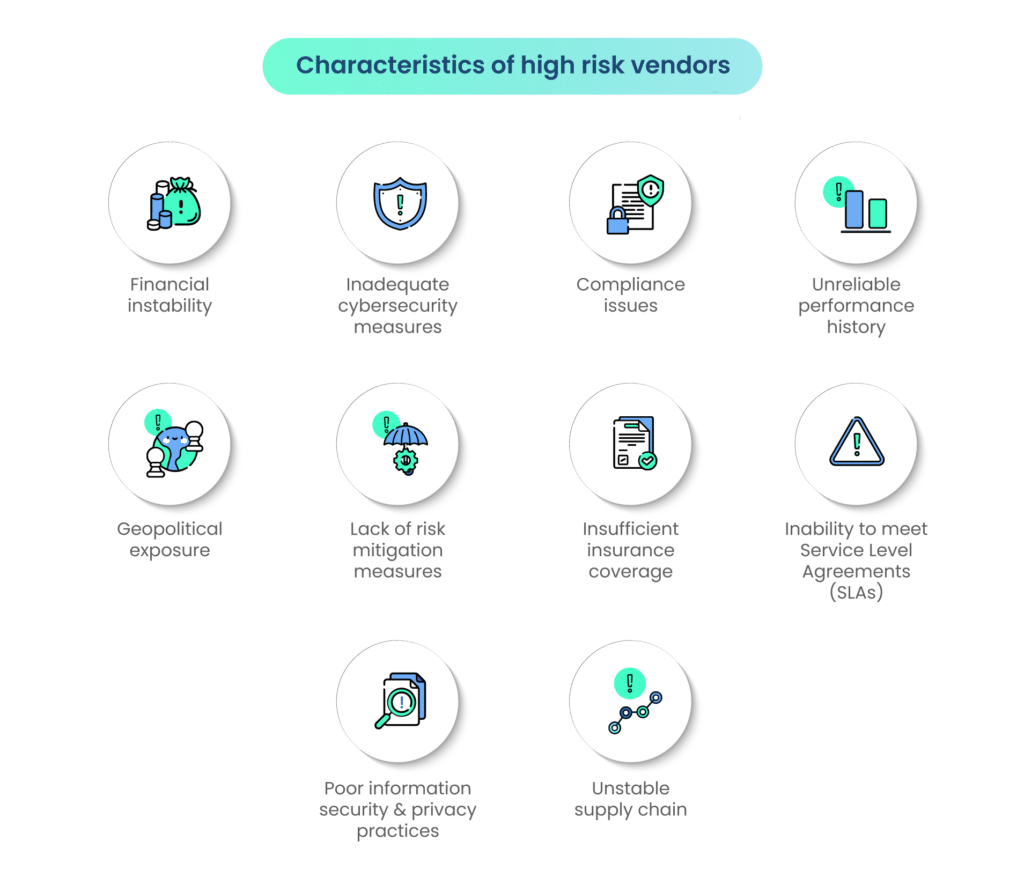
The high-risk definition in vendor management is designated for vendors whose characteristics are as follows:
- Financial instability: Vendors with uncertain financial health, including issues such as insolvency, bankruptcy, or unstable cash flow, are often deemed high-risk.
- Inadequate cybersecurity measures: Vendors lacking robust cybersecurity protocols, leading to vulnerabilities in data protection, are considered high-risk, especially in an era where cyber threats are prevalent.
- Compliance issues: Vendors failing to meet regulatory requirements or industry standards face a high-risk classification, as non-compliance can result in legal repercussions and operational disruptions.
- Unreliable performance history: Vendors with a track record of inconsistent or unreliable performance may be categorized as high-risk due to the potential impact on business operations.
- Geopolitical exposure: Vendors operating in regions with geopolitical instability may introduce higher risks due to factors such as political unrest, economic volatility, or legal uncertainties.
- Lack of risk mitigation measures: Failure to implement adequate risk mitigation measures, such as contingency plans or disaster recovery protocols, contributes to a vendor’s high-risk status.
- Insufficient insurance coverage: The inability to provide suitable types and amounts of insurance coverage may contribute to the vendor’s high-risk classification, especially in situations where insurance is crucial for risk transfer.
- Inability to meet Service Level Agreements (SLAs): Vendors consistently falling short of agreed-upon SLAs contribute to a perception of high risk, as it implies unreliability and potential disruptions to business operations.
- Poor information security and privacy practices: Vendors lacking robust information security and privacy practices expose businesses to heightened cybersecurity risks, contributing to their high-risk designation.
- Unstable supply chain: Vendors dependent on an unstable or unreliable supply chain may pose risks related to the timely delivery of goods or services, impacting the overall stability of operations.
Differences between critical vendors and high-risk vendors
Risk mitigation strategies for critical and high-risk vendors
Effectively managing a diverse vendor ecosystem involves strategic prioritization to address the unique challenges posed by both critical and high-risk vendors.
A risk-based assessment approach serves as the linchpin of this strategy, allowing organizations to categorize vendors based on their impact and potential risks.
The implementation of a robust high-risk liability vendor approval policy is paramount to safeguarding the organization against potential disruptions and ensuring that vendors adhere to stringent risk mitigation measures.
By adopting a tiered approach to vendor management, businesses can allocate resources judiciously. It allows for a nuanced and dynamic response to the distinct risks associated with each vendor category, enhancing overall resilience and fortifying the vendor ecosystem against potential disruptions.
Risk mitigation strategies for critical vendors
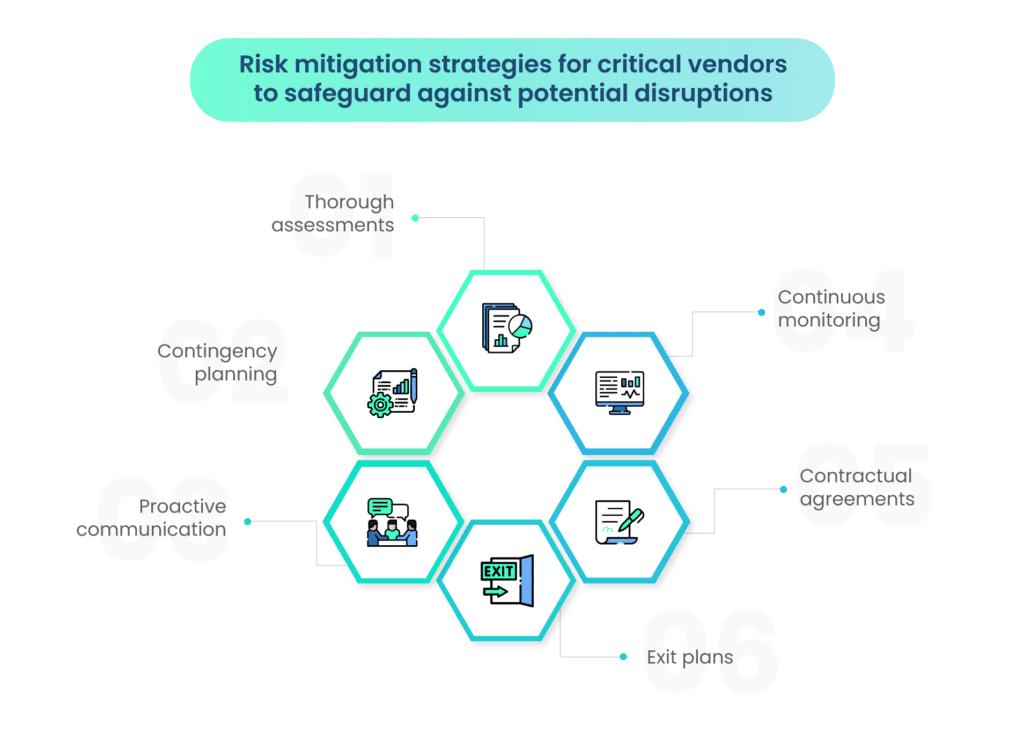
Critical vendors, given their pivotal role in daily operations, require tailored risk mitigation strategies to safeguard the business against potential disruptions.
- Thorough assessments: A fundamental aspect of managing critical vendors is conducting thorough assessments. This involves evaluating the financial stability of the vendor, analyzing their performance history, and assessing their ability to meet contractual obligations.
- Contingency planning: Establishing contingency plans is crucial for mitigating unforeseen challenges, ensuring that the business can respond promptly to any disruptions caused by critical vendors.
- Proactive communication: Transparent communication channels, both upstream and downstream, facilitate a proactive approach to problem-solving.
- Continuous monitoring: Regular monitoring of critical vendor activities allows for early detection of issues, enabling businesses to address concerns before they escalate.
- Contractual agreements: Robust contractual agreements, outlining expectations and responsibilities, serve as a legal framework to protect the interests of both parties.
- Exit plans: Develop dynamic exit plans for critical vendors. These plans should be specific, actionable, and consider various scenarios. Having a well-defined exit strategy enhances the organization’s ability to terminate or replace a vendor if necessary without significant disruptions.
Risk mitigation strategies for high-risk vendors
Mitigating risks associated with high-risk vendors requires a multifaceted approach.
Proactive risk mitigation strategies are paramount, involving regular monitoring, stringent audits, and the establishment of contingency plans. The goal is to identify and address potential risks before they escalate, mitigating the likelihood of disruptions.
Contingency planning ensures that the business has a roadmap to navigate challenges swiftly, reducing the impact of any unforeseen issues.
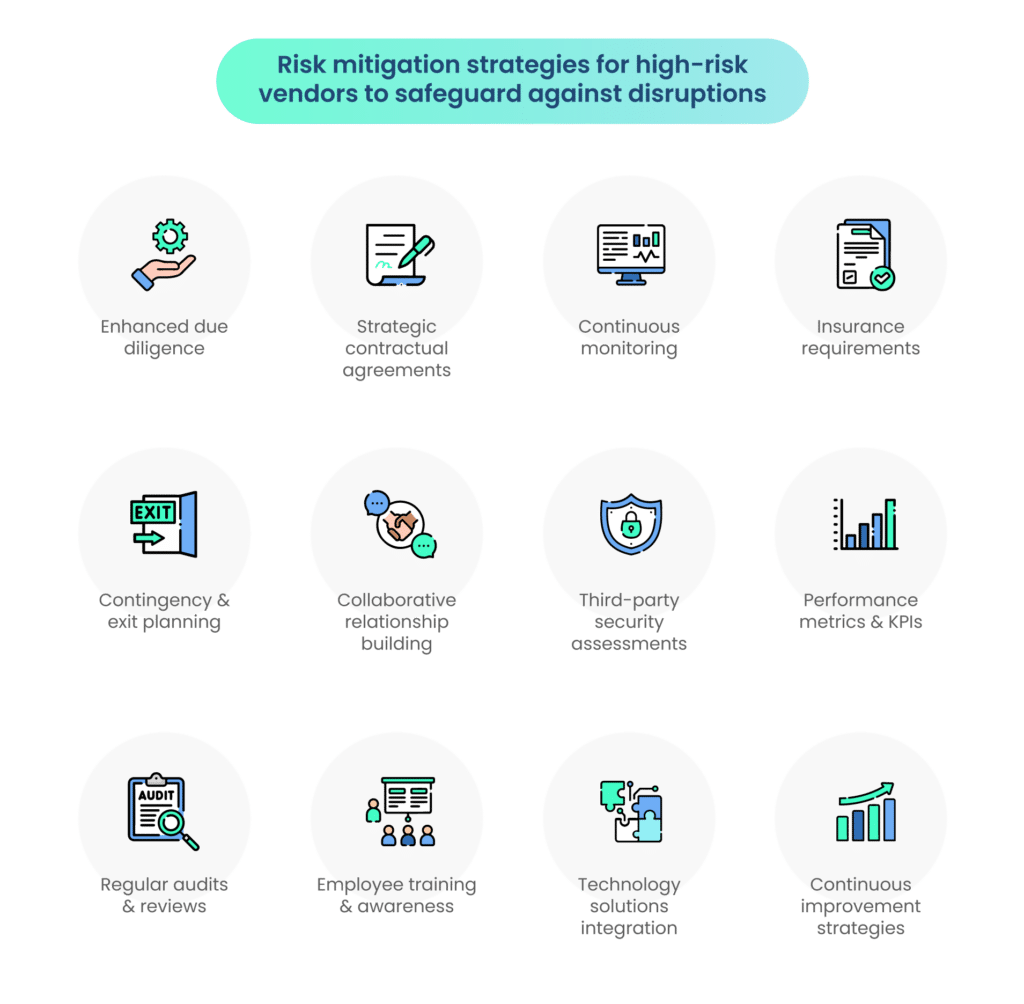
Here are key risk mitigation strategies for high-risk vendors:
- Enhanced due diligence: Conduct thorough due diligence to gain comprehensive insights into the vendor’s financial stability, operational capabilities, and compliance with industry standards.
- Strategic contractual agreements: Implement detailed contractual agreements that clearly outline expectations, responsibilities, and stringent risk mitigation measures. Specify compliance standards, data protection protocols, and consequences for breaches.
- Continuous monitoring: Establish ongoing monitoring mechanisms to track the vendor’s performance, adherence to contractual obligations, and changes in risk posture. Real-time monitoring facilitates proactive responses to emerging risks.
- Insurance requirements: Mandate suitable types and amounts of insurance coverage from high-risk vendors. This ensures financial protection for the organization in case of unforeseen events impacting the vendor’s ability to deliver.
- Contingency and exit planning: Develop robust contingency plans outlining procedures to follow in case of disruptions caused by high-risk vendors. Additionally, establish clear exit strategies for swift termination or replacement if necessary.
- Collaborative relationship building: Foster transparent communication and collaboration with high-risk vendors. An open dialogue allows for early identification and resolution of potential issues, reducing the likelihood of disruptions.
- Third-party security assessments: engage third-party experts to conduct security assessments of high-risk vendors, evaluating their cybersecurity practices and identifying vulnerabilities that need immediate attention.
- Performance metrics and KPIs: Define and track performance metrics and key performance indicators (KPIs) to measure the ongoing effectiveness of high-risk vendor relationships. Regular assessments ensure continuous alignment with organizational objectives.
- Regular audits and reviews: Conduct regular audits and reviews of high-risk vendors’ operations, focusing on areas of concern identified during due diligence. Audits provide additional layers of assurance and can uncover potential risks.
- Employee training and awareness: Educate internal stakeholders involved in vendor management about the specific risks associated with high-risk vendors. Training enhances awareness and ensures that employees follow risk mitigation protocols.
- Technology solutions integration: Leverage technology solutions, such as automated risk management platforms, to streamline and enhance the efficiency of risk mitigation processes. Automation allows for real-time monitoring and quick response to potential threats.
- Continuous improvement strategies: Implement a culture of continuous improvement, regularly reviewing and updating risk mitigation strategies based on evolving risks, industry changes, and lessons learned from past incidents.
Critical components of vendor risk management
Critical components of Vendor Risk management (VRM) encompass a comprehensive set of strategies and processes aimed at identifying, assessing, and mitigating potential risks associated with third-party vendors. These components are essential for ensuring a resilient and secure vendor ecosystem.
By integrating these critical components into their Vendor Risk Management framework, organizations can establish a proactive, adaptive, and comprehensive approach to mitigating the complexities and challenges associated with third-party vendor relationships.
Wrapping up
In conclusion, mastering the nuances between critical and high-risk vendors is pivotal for any organization aiming to fortify its business ecosystem.
Critical vendors form the bedrock of daily operations, demanding meticulous assessments and proactive risk management strategies. Simultaneously, understanding and mitigating the potential threats posed by high-risk vendors are paramount to avoiding disruptions.
By adopting a tiered approach to vendor management, businesses can strategically allocate resources, ensuring resilience and responsiveness. A well-crafted vendor management strategy is not just a risk mitigation measure but a catalyst for sustained success in a dynamic business arena.
Scrut can help your organization automate the vendor management process. To know more, get in touch today!
Frequently Asked Questions
1. What defines a vendor as critical in a business ecosystem?
Critical vendors are those whose products or services are integral to a company’s operations, often having a direct impact on its core functions and success. These vendors are essential for maintaining the business’s day-to-day activities.
2. How do high-risk vendors differ from critical vendors, and what factors contribute to their classification?
High-risk vendors pose a potential threat due to factors like financial instability, cybersecurity vulnerabilities, or regulatory compliance issues. Unlike critical vendors, their impact may not be immediate but could lead to significant problems if not managed carefully.
3. What strategies can businesses employ to assess and mitigate risks associated with critical vendors?
To manage risks with critical vendors, businesses should conduct thorough assessments, establish contingency plans, and maintain transparent communication. Regular monitoring, contractual agreements, and diversification of critical vendors are also effective risk mitigation strategies.
4. Are there specific industries or sectors where the distinction between critical and high-risk vendors becomes more pronounced?
Yes, industries with stringent regulatory requirements, such as finance or healthcare, often have a more pronounced distinction between critical and high-risk vendors. The impact of vendor failure or security breaches can be more severe in these sectors.
5. In practical terms, how can organizations prioritize their focus on managing both critical and high-risk vendors concurrently?
Organizations can employ risk-based assessments to prioritize efforts. Critical vendors may undergo more frequent and comprehensive evaluations, while high-risk vendors require proactive risk mitigation strategies. Implementing a tiered approach ensures efficient resource allocation based on the level of risk each vendor presents.
Table of contents