In today’s ever-evolving digital landscape, the importance of robust risk management in ensuring the security of organizations cannot be overstated. Cyber threats continue to grow in sophistication, making it crucial for businesses to proactively identify, assess, and mitigate risks. Risk management provides a systematic approach to understanding potential vulnerabilities, anticipating potential threats, and developing strategies to safeguard critical assets and sensitive data.
While risk management is a critical aspect of cybersecurity, the traditional manual approach can be time-consuming, resource-intensive, and prone to human errors. As organizations face increasingly complex and numerous risks, there arises a need for a more efficient and scalable solution. This is where automation comes into play. Automating risk management processes can significantly enhance the efficiency and accuracy of risk assessment, response, and mitigation.
In this blog, we will delve into the world of automating risk management and explore how organizations can leverage technology to bolster their security posture.
What is risk management?
Risk management is a systematic process of identifying, assessing, and mitigating potential risks that could impact an organization’s objectives or projects. It involves the identification of threats and vulnerabilities, evaluating their potential impact, and taking appropriate measures to minimize or eliminate their negative consequences.
In the context of cybersecurity and information security, risk management focuses on understanding and addressing the risks related to the confidentiality, integrity, and availability of an organization’s sensitive data, critical assets, and IT infrastructure.
What are the key components of risk management?
The risk management process typically involves the following key steps:
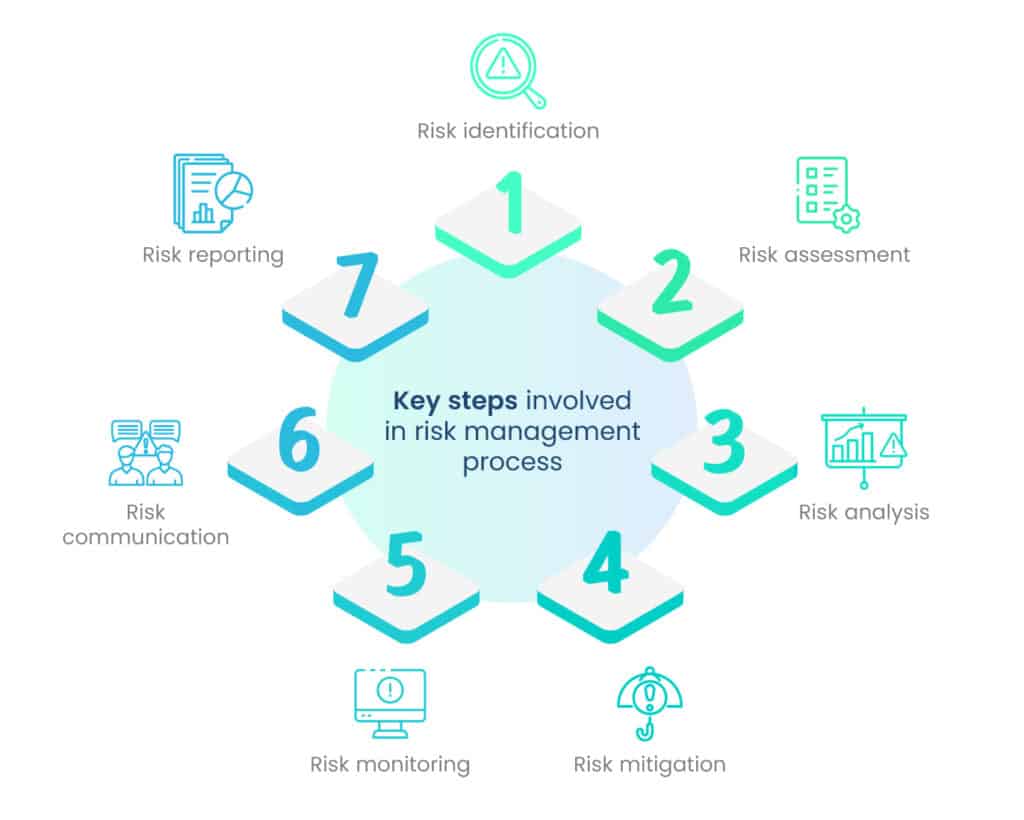
A. Risk identification
This step involves identifying and documenting potential risks that could affect the organization’s assets, operations, or objectives. It includes understanding the internal and external factors that could pose threats.
B. Risk assessment
Once risks are identified, they are assessed based on their likelihood of occurrence and the potential impact they could have on the organization. This step helps prioritize risks and allocate resources more effectively.
C. Risk analysis
During this stage, the identified risks are analyzed to understand their root causes, vulnerabilities, and potential consequences. This analysis aids in developing appropriate risk mitigation strategies.
D. Risk mitigation
Risk mitigation involves developing and implementing measures to reduce the likelihood of a risk occurring or minimize its impact if it does occur. Mitigation strategies can include implementing security controls, redundancy, training, and more.
E. Risk monitoring
Risk management is an ongoing process, and risks need to be continuously monitored to identify changes in their likelihood or impact. This allows for timely adjustments to risk mitigation strategies as needed.
F. Risk communication
Effective risk management requires clear communication of risks and mitigation efforts to stakeholders, including management, employees, and external partners. Transparent communication ensures a shared understanding of the risks faced and the organization’s approach to managing them.
G. Risk reporting
Regular reporting on risk management activities and their outcomes helps stakeholders stay informed about the current risk landscape and the effectiveness of mitigation efforts.
By implementing a structured risk management process, organizations can make informed decisions to protect their assets, enhance resilience, and ensure continuity in the face of potential threats and uncertainties.
What are the common challenges in traditional risk management approaches?
Traditional risk management approaches, while essential, can also face several challenges that hinder their effectiveness in addressing the ever-evolving cybersecurity landscape. Some common challenges include:
- Manual and time-consuming processes
- Lack of real-time insights
- Incomplete risk visibility
- Difficulty in quantifying risks
- Siloed risk management
- Inadequate resources and budget
- Reactive approach rather than proactive
- Inconsistent risk appetite
- Rapid technological advancements
- Compliance complexity
What are the advantages of automating risk management?
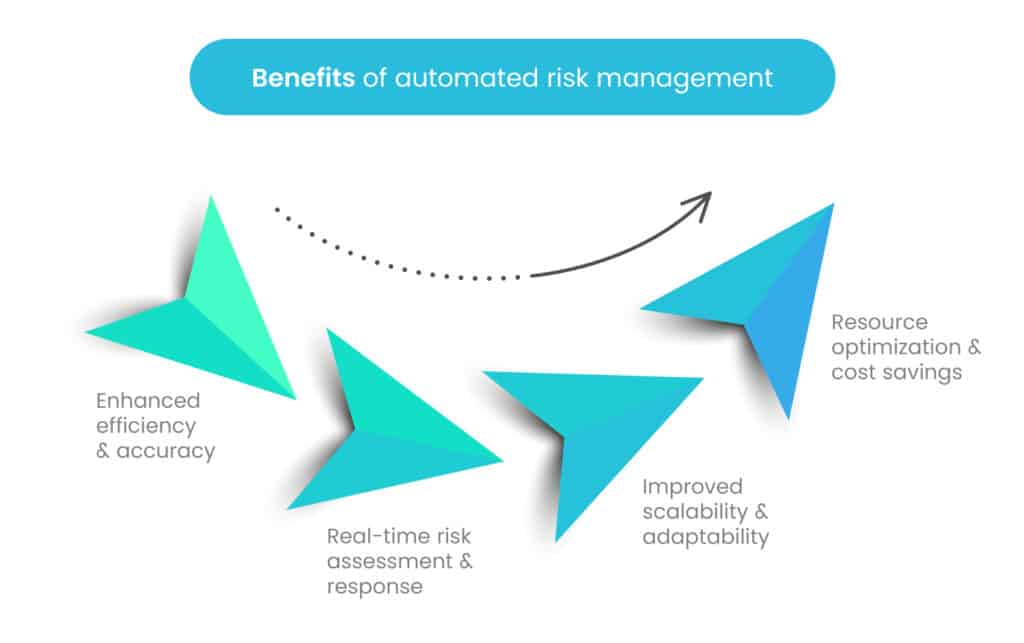
Some of the benefits of automated risk management include:
A. Enhanced efficiency and accuracy
Automating risk management processes can significantly improve efficiency and accuracy compared to manual methods. By utilizing automated tools, data collection, risk assessments, and analysis can be streamlined, reducing the time and effort required. Automation also minimizes the chances of human errors and biases, ensuring a more reliable risk evaluation.
B. Real-time risk assessment and response
One of the most significant benefits of automation is the ability to perform real-time risk assessment. Automated systems continuously monitor and analyze security data, promptly detecting potential threats as they emerge. This allows organizations to respond swiftly to cyber incidents, minimizing their impact and preventing further escalation.
C. Improved scalability and adaptability
As organizations grow and evolve, their risk management needs change. Manual risk management approaches can become cumbersome to scale, but automation provides the flexibility and scalability to adapt to changing requirements. Automated systems can handle larger datasets and adjust to new risks and technologies seamlessly.
D. Resource optimization and cost savings
Automating risk management can lead to resource optimization and cost savings. By reducing the manual workload, organizations can allocate their skilled personnel to higher-value tasks and strategic initiatives. Additionally, automation helps in identifying cost-effective risk mitigation strategies, making better use of available resources.
Steps to automate the risk management process?
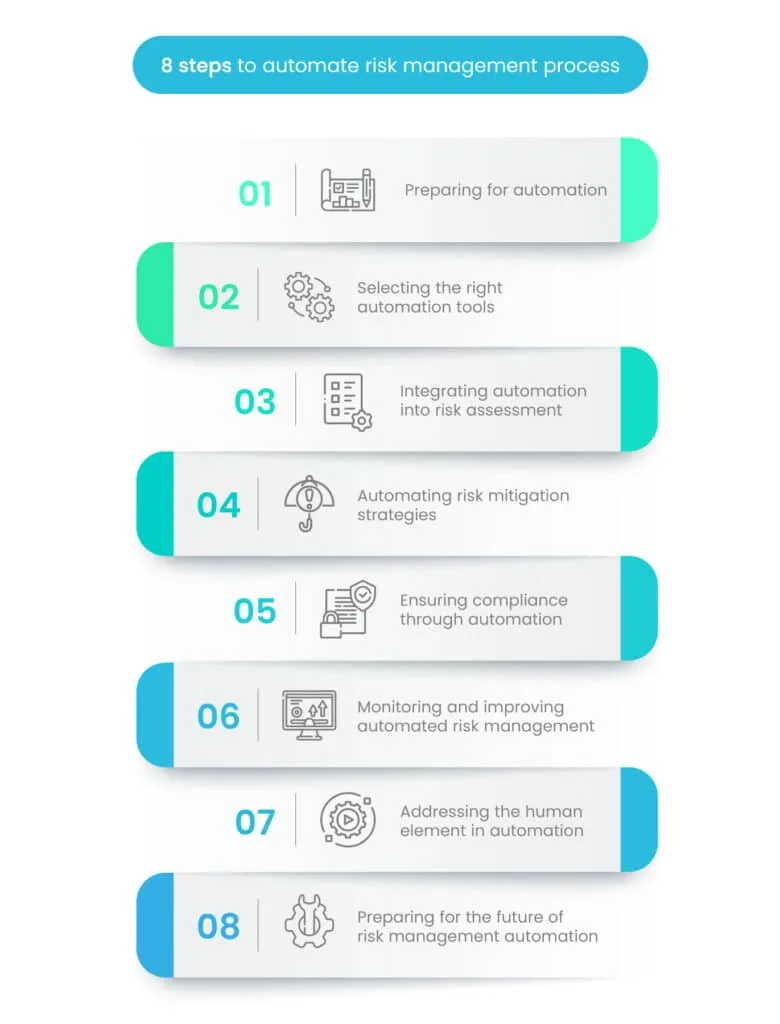
Let’s discuss the steps to automate the risk management process:
Step 1: Preparing for automation
There are several sub-steps when it comes to preparing for the automation of the risk management process.
1. Building a strong risk management foundation
- Define risk management policies, procedures, and governance structures.
- Align risk management with organizational objectives and risk appetite.
- Establish a clear understanding of risk management principles and best practices.
2. Identifying critical assets and data
- Conduct a comprehensive asset inventory and data classification exercise.
- Prioritize assets and data based on their value and importance to the organization.
- Focus on protecting the most critical and sensitive assets and data.
3. Establishing risk tolerance and priorities
- Define the organization’s risk tolerance levels for different types of risks.
- Prioritize risks based on their potential impact on the organization.
- Tailor risk mitigation strategies to align with established risk priorities.
4. Engaging stakeholders and building a team
- Involve key decision-makers, IT teams, security professionals, legal, and compliance personnel.
- Build a diverse and knowledgeable team to ensure a holistic approach to risk management.
- Gain buy-in and support from stakeholders for the successful adoption of automation.
Step 2: Selecting the right automation tools
The best way to automate risk management is by using risk management software. Risk management software assists you in identifying, assessing, and documenting risks associated with various business processes and efficiently managing risk mitigation tasks.
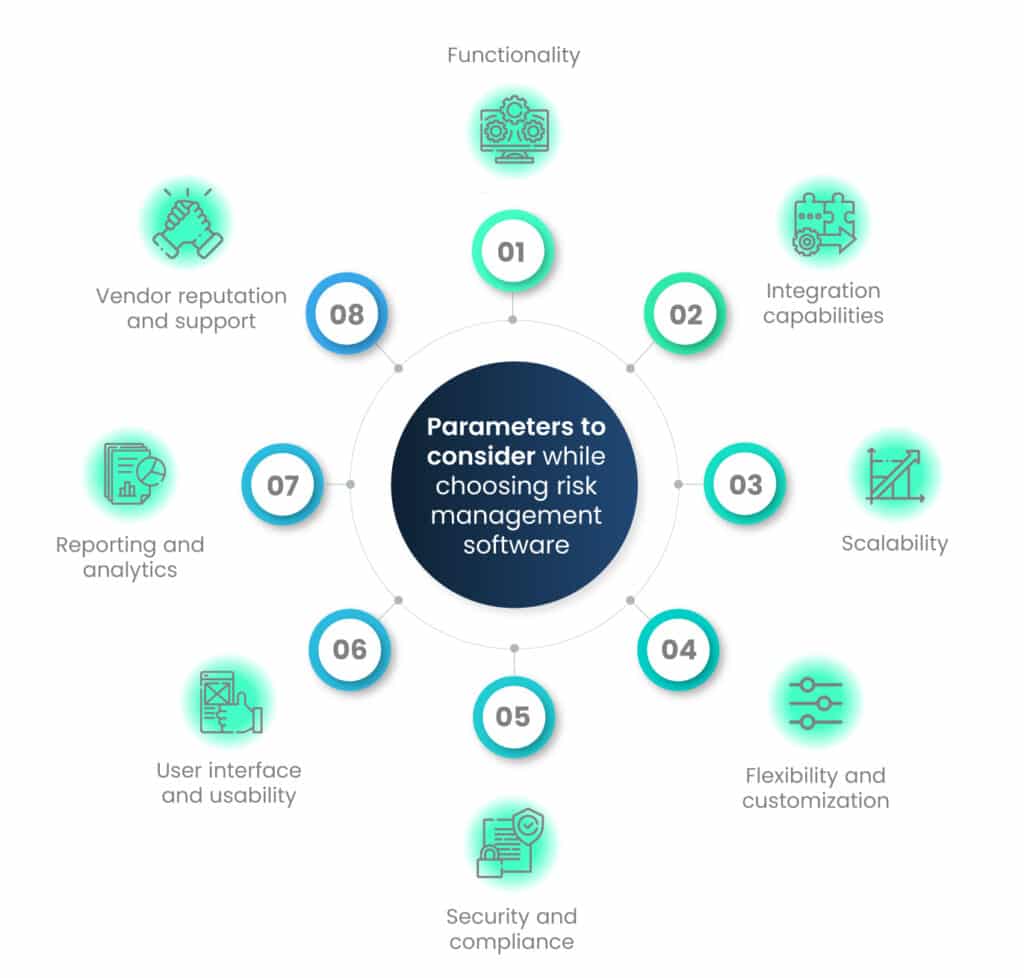
The parameters that you should consider when choosing risk management software are listed below:
1. Functionality
Assess whether the tool covers essential risk management processes, such as risk assessment, incident response, and compliance monitoring.
2. Integration capabilities
Ensure that the automation tool can integrate with existing security infrastructure and third-party solutions to avoid disruptions and enable seamless data sharing.
3. Scalability
Verify that the tool can handle the organization’s current data volume and scale to accommodate future growth and increasing automation demands.
4. Flexibility and customization
Determine whether the tool allows customization to match the organization’s unique risk management requirements and workflows.
5. Security and compliance
Prioritize tools that adhere to industry security standards and regulatory compliance requirements to maintain data confidentiality and integrity.
6. User interface and usability
Evaluate the tool’s user-friendliness and accessibility to ensure that security teams can easily operate and manage it effectively.
7. Reporting and analytics
Look for tools that provide comprehensive reporting and analytics capabilities to gain insights into risk trends and security performance.
8. Vendor reputation and support
Research the vendor’s reputation, customer reviews, and the level of technical support they offer to ensure a positive experience.
Step 3: Integrating automation into risk assessment
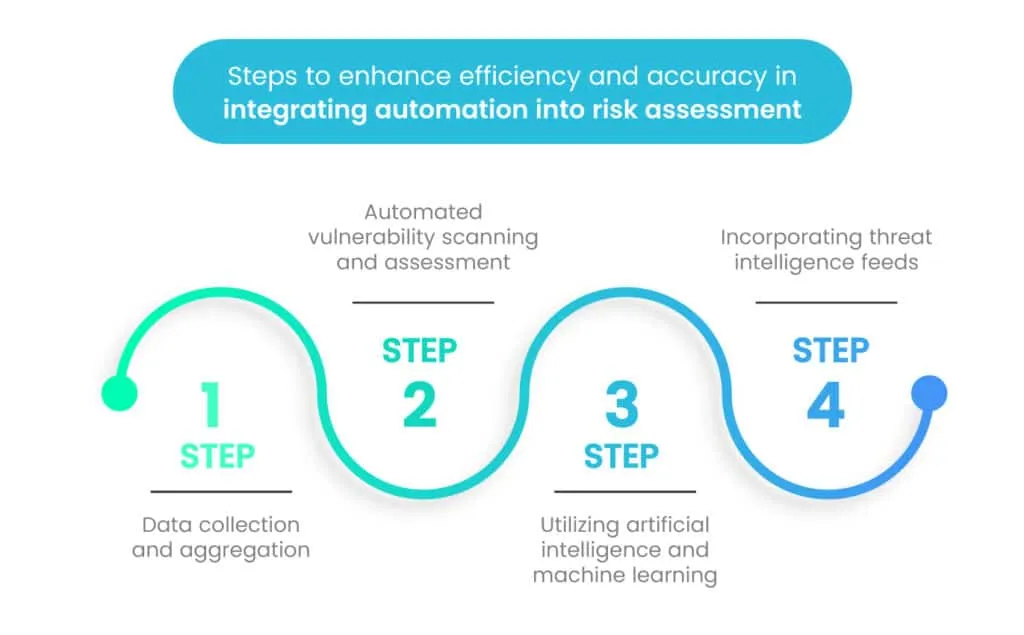
Integrating automation into risk assessment involves several crucial sub-steps to enhance efficiency and accuracy.
1. Data collection and aggregation
The first sub-step is Data Collection and Aggregation, where relevant data is automatically gathered from various sources, including system logs, network traffic, and application logs. This data is then aggregated into a centralized repository to facilitate further analysis.
2. Automated vulnerability scanning and assessment
In this phase, organizations employ automated vulnerability scanning tools to identify weaknesses and security flaws in their systems, applications, and infrastructure. These tools generate comprehensive reports on the identified vulnerabilities, which are then prioritized based on their severity.
3. Utilizing artificial intelligence and machine learning
To further bolster risk assessment capabilities, organizations can leverage Artificial Intelligence and Machine Learning in their processes. By implementing AI and machine learning algorithms, they can analyze large datasets and identify patterns that may indicate potential risks and threats. AI-driven anomaly detection helps in identifying abnormal behaviors that might signify security incidents.
4. Incorporating threat intelligence feeds
Finally, Incorporating Threat Intelligence Feeds is a crucial aspect of automation in risk assessment. Organizations integrate threat intelligence feeds from reputable sources to stay updated with the latest known threats and attack vectors. By automating the process of matching this threat intelligence with the organization’s assets, they can identify potential areas of concern more effectively.
Step 4: Automating risk mitigation strategies
Automating risk mitigation strategies plays a crucial role in strengthening an organization’s cybersecurity posture and reducing response time to potential threats.
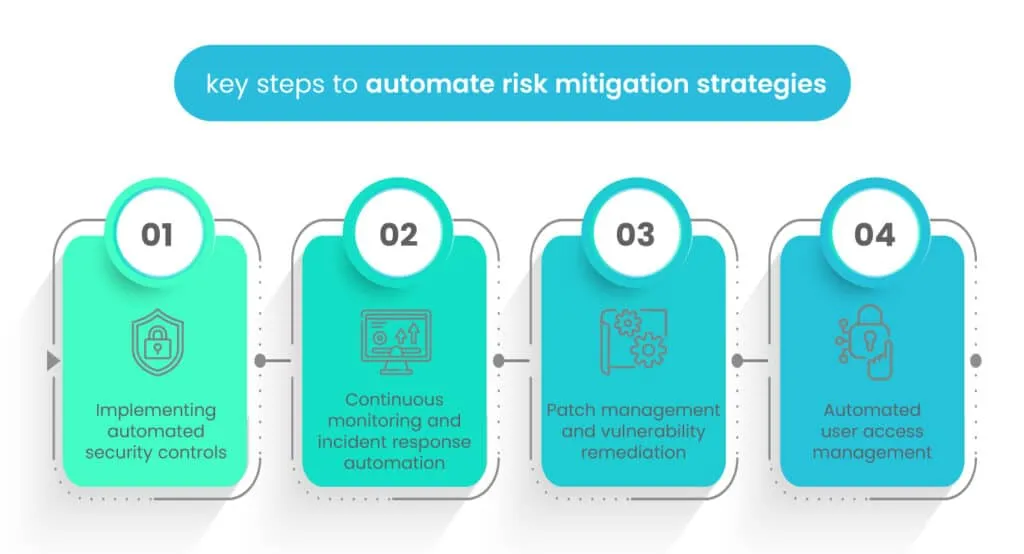
Here are the key steps to automating risk mitigation:
1. Implementing automated security controls
Automated security controls involve setting up security measures that can autonomously detect and respond to security threats in real time. These controls can include Intrusion Detection Systems (IDS), firewalls, and Security Information and Event Management (SIEM) systems. By implementing automated security controls, organizations can proactively safeguard their networks and systems from various cyber threats.
2. Continuous monitoring and incident response automation
Continuous monitoring involves the real-time monitoring of an organization’s IT environment to identify any suspicious activities or potential security incidents. Incident response automation allows for the automatic execution of predefined incident response actions when a security event is detected. This can include isolating affected systems, blocking malicious IP addresses, or notifying relevant personnel. Automated incident response helps to swiftly contain and mitigate security incidents, reducing the overall impact on the organization.
3. Patch management and vulnerability remediation
Automating patch management involves deploying software updates and security patches to systems and applications promptly. Vulnerability remediation involves automatically addressing identified vulnerabilities to prevent potential exploitation. Automated patch management and vulnerability remediation processes help ensure that systems remain up-to-date and secure against known vulnerabilities and exploits.
4. Automated user access management
Automated user access management involves using Identity and Access Management (IAM) systems to handle user privileges and access rights automatically. These systems can streamline user provisioning, de-provisioning, and access reviews, ensuring that users have appropriate access levels and that access is revoked promptly when users change roles or leave the organization. This minimizes the risk of unauthorized access and potential insider threats.
Step 5: Ensuring compliance through automation
Ensuring compliance through automation is essential for organizations to meet regulatory requirements and maintain a strong governance framework.
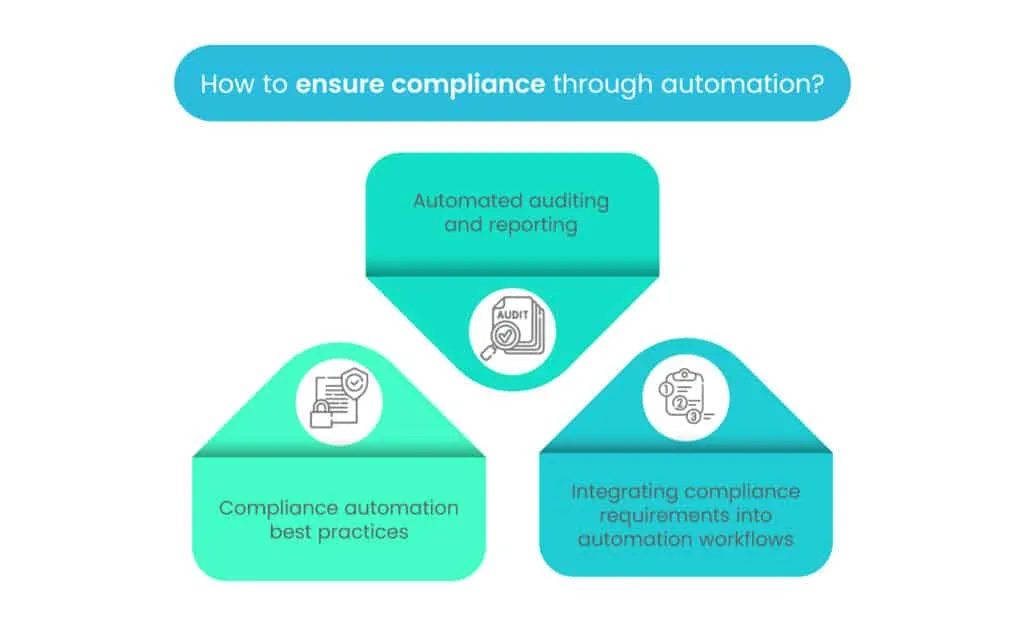
Here are the key steps to achieve compliance through automation:
1. Compliance automation best practices
Implementing compliance automation best practices involves creating a structured approach to automate compliance processes effectively. This includes identifying relevant regulatory requirements, establishing internal policies and controls, and mapping them to automated workflows. Organizations should also prioritize regular updates to the compliance automation tools and procedures to adapt to changing regulations and security threats.
2. Automated auditing and reporting
Automating the auditing and reporting processes streamlines the collection and analysis of data required for compliance assessments. By employing automated tools, organizations can continuously monitor their systems and infrastructure for compliance violations, security incidents, and other relevant events. These tools generate comprehensive reports, allowing for easier review and verification of compliance status.
3. Integrating compliance requirements into automation workflows
Organizations should integrate compliance requirements into their existing automation workflows and systems. This involves designing automated processes that incorporate compliance checks at various stages of operation. For example, automated workflows could include checks for user access rights, data encryption, or software versioning to ensure compliance with relevant regulations.
Step 6: Monitoring and improving automated risk management
Monitoring and improving automated risk management processes are crucial to ensure their effectiveness and alignment with organizational objectives.
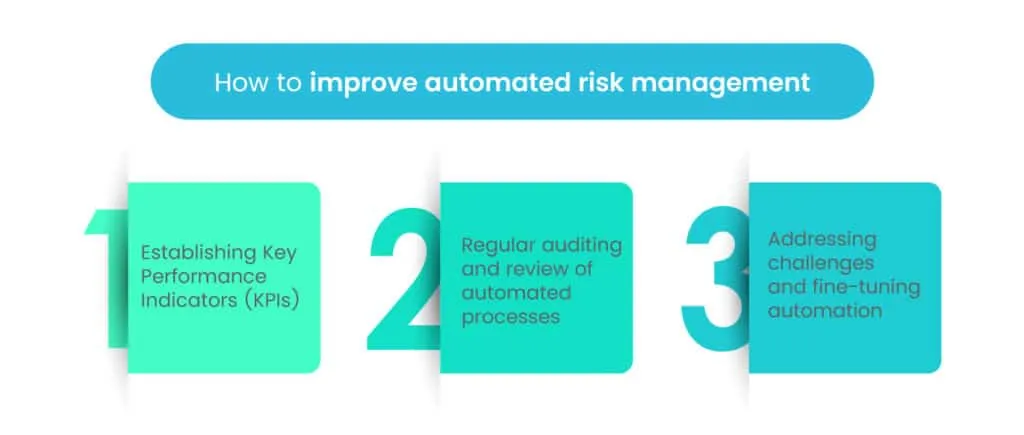
Here are the key steps for monitoring and improving automated risk management:
1. Establishing Key Performance Indicators (KPIs)
To gauge the success of automated risk management, organizations should establish KPIs that align with their risk management goals. These KPIs can include metrics related to the number of identified risks, risk response times, the accuracy of risk assessments, and the effectiveness of risk mitigation strategies. By regularly measuring and analyzing these KPIs, organizations can identify areas for improvement and track progress over time.
2. Regular auditing and review of automated processes
Conducting regular audits and reviews of automated risk management processes is essential to identify any potential weaknesses, errors, or gaps in the system. Audits help ensure that automated processes are functioning as intended and they comply with relevant policies and regulatory requirements. Through reviews, organizations can gain insights into the overall performance of the automated risk management system and make necessary adjustments.
3. Addressing challenges and fine-tuning automation
Challenges may arise during the implementation and operation of automated risk management systems. These challenges could include false positives or negatives in risk assessments, integration issues with existing systems, or changes in regulatory requirements. It is crucial to address these challenges promptly and fine-tune the automation to optimize its performance. This may involve adjusting algorithms, updating data sources, or refining the automation workflows.
Step 7: Addressing the human element in automation
Addressing the human element in automation is critical to ensure that automated processes are effectively managed and aligned with organizational objectives.
Here are the key steps for addressing the human element in automation:
1. Human oversight and decision-making
While automation can greatly enhance efficiency, human oversight is essential to maintain control over critical decisions and actions. Organizations should ensure that there are designated personnel responsible for overseeing automated processes and intervening when necessary. Human decision-makers play a vital role in assessing the context of certain situations that automated systems may not fully grasp. This human intervention helps prevent errors, reduce false positives, and avoid potential negative consequences resulting from over-reliance on automation.
2. Training and upskilling the security team
To effectively manage and interact with automated systems, the security team should receive adequate training and upskilling. Training should cover various aspects, including how to interpret and act upon automated risk assessments, understanding the limitations and potential biases of the automation tools, and effectively collaborating with automated systems. Upskilling the security team ensures that they are equipped to make informed decisions and optimize the benefits of automation.
3. Communication and collaboration in automated workflows
Automation can sometimes create silos between different teams or functions within an organization. To address this, it is crucial to establish effective communication and collaboration channels in automated workflows. This involves fostering a culture of information-sharing and cross-functional teamwork. Different teams, such as IT, security, and compliance, must communicate and coordinate effectively to ensure that automated risk management processes align with broader organizational goals.
Step 8: Preparing for the future of risk management automation
Preparing for the future of risk management automation requires organizations to stay ahead of emerging technologies and trends while also addressing ethical considerations. Integrating automation with security orchestration is another crucial aspect of future-proofing risk management.
Here are the key steps to prepare for the future of risk management automation:
1. Emerging technologies and trends in security automation
To stay at the forefront of risk management automation, organizations must continuously monitor and adopt emerging technologies and trends in the cybersecurity landscape. This includes exploring advancements in artificial intelligence, machine learning, and data analytics for improved risk assessment and threat detection. Additionally, keeping an eye on new automation tools and platforms can help organizations enhance their risk management capabilities and adapt to evolving threats.
2. Ethical considerations and avoiding bias in automation
As automation becomes more pervasive in risk management, organizations must be vigilant about ethical considerations and the potential for bias in automated systems. Bias can inadvertently be introduced through algorithms, data selection, or the way automation is implemented. It is crucial to regularly review and audit automated risk management processes to identify and mitigate any biases that may arise. Ensuring fairness, transparency, and accountability in automation can help maintain trust and credibility in risk management practices.
3. Integrating automation with security orchestration
Security orchestration involves the seamless integration of different security tools, processes, and teams to create a cohesive defense against cyber threats. Integrating automation with security orchestration allows for the streamlined management of security incidents, faster response times, and better coordination among different security functions. This integration can enhance overall risk management effectiveness and ensure a more proactive and unified approach to cybersecurity.
To wrap up
In conclusion, automating risk management processes offers numerous benefits to organizations in today’s dynamic digital landscape. By leveraging automation, businesses can enhance efficiency, accuracy, and scalability in identifying, assessing, and mitigating potential risks. Real-time insights and continuous monitoring enable swift responses to emerging threats, bolstering the organization’s security posture. Furthermore, automation optimizes resource allocation, reduces costs, and frees up skilled personnel to focus on strategic initiatives. Integrating automation into risk mitigation strategies empowers organizations to implement security controls and incident response measures promptly, minimizing the impact of cyber incidents.
However, it is essential to address the human element in automation to ensure effective risk management. Human oversight remains critical to make critical decisions and prevent unintended consequences. Proper training and upskilling of the security team facilitate seamless interaction with automated systems and better utilization of automation’s capabilities. By embracing automation and refining its integration, organizations can proactively protect their assets, navigate emerging risks, and strengthen their overall security posture in an ever-evolving digital landscape.
FAQs
What is risk management?
Risk management is a systematic process of identifying, assessing, and mitigating potential risks that could impact an organization’s objectives or projects. It involves understanding threats and vulnerabilities, evaluating their potential impact, and taking appropriate measures to minimize or eliminate their negative consequences.
What are the key components of risk management?
The key components of risk management include risk identification, risk assessment, risk analysis, risk mitigation, risk monitoring, risk communication, and risk reporting.
What are the advantages of automating risk management?
The advantages of automating risk management include enhanced efficiency and accuracy, real-time risk assessment and response, improved scalability and adaptability, resource optimization, and cost savings.





































