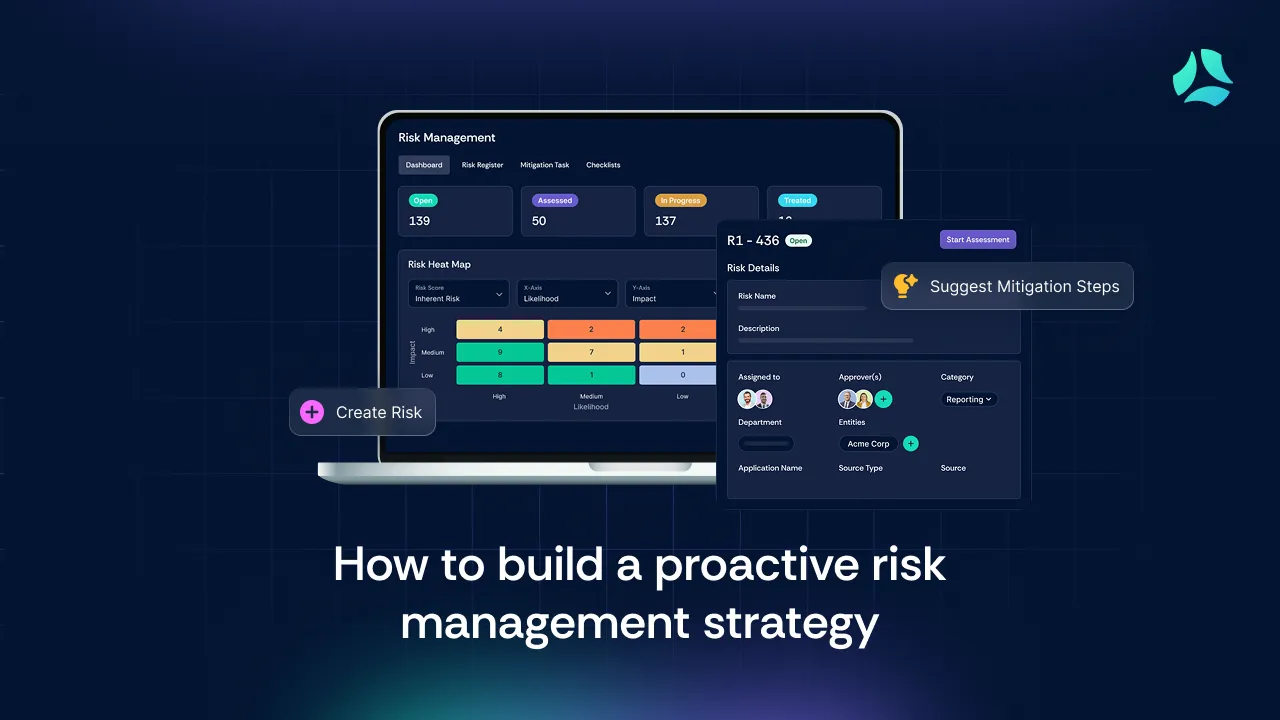
Risk is not a future problem; it’s a current reality. But many teams treat it as a second thought.
In 2024, an Accenture survey found that only 14.5% of organizations had truly advanced risk capabilities, like tech-driven analytics and data-connected workflows. That means more than 85% of firms are potentially missing early warning signs.
Meanwhile, the Government Enterprise Risk Management 2024 Survey Results, researched by the Association for Federal Enterprise Risk Management (AFERM), show that 85% of organizations have a formal Enterprise Risk Management (ERM) program, but the bulk of these are basic setups with limited visibility and manual controls.
What does that gap look like in action? Just 57% of risk leaders say they’re prioritizing investments in new tools or skills to boost their capabilities (Accenture). That’s good, but not nearly enough when the landscape keeps shifting daily.
Here’s the truth: if most companies are not equipped with advanced tools, deep visibility, or ongoing investment, they’re simply too slow to catch emerging threats, and those threats quickly escalate.
In this blog, you’ll discover an actionable blueprint for modern risk management: how to identify and assess risks clearly, respond confidently, monitor continuously, and embed resilience into everyday operations. You’ll learn to move from reactive chaos to proactive strength and, more importantly, stay there.
What is risk management?
Risk management is the process of figuring out what could go wrong, how bad it could be, and what to do about it, before it actually happens.
It’s not just about security or compliance. Risk comes in many forms: a cloud outage, a third-party vulnerability, a regulatory change, or even a missed renewal in a critical tool. And when risks aren’t managed, they don’t just cause disruptions; they slow down launches, break customer trust, and drain resources.
That’s why risk management is necessary. It gives your team a clear picture of where things could go off track and the power to act before they do. It shifts your organization from reactive firefighting to proactive decision-making. In a world where a single misstep can snowball into reputational damage or financial loss, risk management isn’t optional; it’s a core part of staying resilient and competitive. And behind every effective risk management process are specific techniques — practical methods that help you identify, assess, respond to, and monitor risks with clarity and consistency.
What is a risk management technique?
A risk management technique is a structured method used to carry out one of the four core risk management steps: identify, assess, respond, and monitor. These techniques help organizations break down complex risks into manageable actions, like using a risk matrix to prioritize threats or automated tools to detect vulnerabilities. The right technique improves visibility, strengthens decisions, and makes risk management repeatable across teams.
But a process is only as strong as the techniques behind it. Each stage of risk management — from spotting risks early to responding effectively — relies on specific, proven techniques. These methods turn broad strategy into day-to-day execution, helping your team move from uncertainty to control.
Techniques to identify risks
To spot risks effectively, you need visibility into your systems, people, vendors, and workflows. These techniques help uncover hidden vulnerabilities, dependencies, and blind spots before they turn into incidents.
1. Asset inventorying
Asset inventorying is the starting point for identifying risk. It means building a clear, up-to-date list of all systems, applications, devices, data stores, and cloud resources your organization uses. Without this visibility, you’re operating blind; you can’t secure what you don’t know exists.
2. Threat modelling
Using frameworks like STRIDE or PASTA, teams map out systems, data flows, and access points, then brainstorm how those could be exploited. This uncovers not just technical bugs but design flaws or trust assumptions. It’s best done early in system design or planning.
3. Vulnerability scans
Scanners like Qualys or Nessus can automatically flag outdated software, misconfigurations, and unpatched systems. The key is to not just scan, but act on findings quickly.
4. Vendor risk assessments
Review third-party certifications, send due diligence questionnaires, and assess contract terms — especially for high-risk vendors handling sensitive data or having access to your systems.
5. Employee interviews or workshops
These uncover risks tools often miss, like inconsistent processes or undocumented workarounds. They also build a culture where people feel responsible for risk awareness.
Techniques to assess risks
Once you’ve identified risks, the next step is understanding which ones need attention and why. These techniques help you evaluate risks based on their likelihood, impact, and alignment with your organization’s tolerance.
1. Risk matrix
Plots risks on a grid of likelihood vs. impact.
Example: A data breach with high impact and high likelihood gets top priority; a low-likelihood system timeout may be accepted or monitored passively.
2. FAIR model
A quantitative method that estimates potential loss in dollar terms.
Example: A risk with a $1 million impact but low frequency may still justify an investment in controls if exposure is too high to ignore.
3. Heat maps and scoring
Visual grids and numeric models to rank and compare large numbers of risks quickly. Ideal for exec reporting.
4. Define risk appetite
Sets clear thresholds for which risks are tolerable and which need action.
Example: “Any risk with a projected loss over $50,000 must have a mitigation plan.”
Techniques to respond to risks
Not all risks need to be fixed, but all need a decision. These strategies help you decide how to handle each risk.
1. Avoid
Walk away from risky activities altogether.
Example: A startup avoids handling financial data by outsourcing all payment processing to Stripe.
2. Reduce
Apply controls or improve processes to lower risk.
Example: Enable multi-factor authentication, encrypt sensitive data, or add real-time monitoring to reduce the impact of breaches.
3. Transfer
Shift risk to a third party.
Example: Purchase cyber insurance or include liability clauses in vendor contracts.
4. Accept
Deliberately choose to tolerate a risk.
Example: A non-critical bug is left unresolved because fixing it would cost more than its potential impact.
Accepted risks must be documented — with justification, ownership, and review dates — to avoid future blind spots.
Techniques to monitor risks
Risks evolve, and so should your approach. These techniques help you continuously track control performance, revisit past decisions, and stay alert to new threats over time.
- Automated control testing: Tools continuously check if controls like MFA or data retention policies are working.
- Dashboards: Provide real-time visibility into risk posture across departments.
- Periodic reviews: Monthly or quarterly reviews help catch outdated assumptions and ensure ownership remains clear. These reviews should be documented consistently to keep your risk history auditable.
- Incident simulations: Tabletop exercises test your response to real-world scenarios and identify gaps in your plan.
- Audit logs: A tamper-proof, queryable record of system activity that helps during investigations or audits.
Key components of using risk management techniques
Techniques alone don’t guarantee success — they need structure. These are the core elements that ensure your techniques work in practice:
1. Clear ownership: Every risk or control should have someone responsible.
2. Defined thresholds: Know when action is needed.
3. Integrated tooling: Reduce manual effort with automation.
4. Strong documentation: Every decision must be traceable.
]5. Consistent review cycles
5. Consistent review cycles: Keep risk posture up to date.
Who should be involved in risk management?
Risk management isn’t just a security or compliance task; it’s a team sport. While GRC teams may lead the process, risks live across systems, vendors, and workflows, so input from every function matters.
- Leadership
- Engineering and IT teams
- Business and operations teams
- Legal and compliance
- Employees
Assigning clear risk owners helps ensure accountability. When everyone understands their role, risk management becomes a shared rhythm, not a one-team responsibility.
What are some risk management tools?
As risks grow across systems and teams, purpose-built tools help you move beyond spreadsheets and stay in control. Here are some commonly used ones:
- Risk registers – Track risks, assign owners, and manage mitigation plans.
- Continuous control monitoring tools – Automatically test key controls in real time.
- Vulnerability scanners – Identify misconfigurations and unpatched systems.
- Vendor risk management tools – Automate due diligence and risk scoring.
- Risk quantification tools – Translate risks into financial terms.
- GRC platforms – Centralize all risk, compliance, and audit workflows.
How Scrut simplifies risk management for your organization
Scrut brings all your risk management techniques into one place — from identifying risks using automated asset discovery and vulnerability scanning, to assessing them with configurable risk matrices and real-time scoring, to tracking responses and continuously monitoring control health. With 100+ integrations, Scrut automates evidence collection, simplifies audits, and gives you real-time visibility into your compliance posture — so you can manage risk without slowing down operations.
Scrut replaces spreadsheets with real-time visibility and audit-ready reporting. Whether you’re managing ISO 27001, SOC 2, or your own risk register, Scrut helps you stay ahead of what could go wrong, without drowning in manual effort.

Typically, the Chief Information Security Officer (CISO), Chief Risk Officer (CRO), or Head of GRC leads the charge. They design the strategy, set priorities, and ensure alignment with frameworks like ISO 27001 or SOC 2.
The risk or compliance team, typically led by a CISO or CRO, oversees overall monitoring. But individual risk owners across teams are responsible for tracking risks in their domain. This role should go to someone with strong risk management skills.
Yes. Compliance risks are a key part of risk management. The same techniques, like risk assessments and control monitoring, are used to identify, manage, and track regulatory and standards-related risks.
Organizations typically manage several types of risks, including: Operational risks – Process failures, human errors, or system breakdowns Security risks – Threats like data breaches, malware, or insider attacks Compliance risks – Violations of laws, regulations, or standards (e.g. GDPR, HIPAA)Strategic risks – Risks tied to business decisions, market shifts, or competition Third-party risks – Risks from vendors, partners, or service providers Financial risks – Budget overruns, fraud, or revenue loss Reputational risks – Negative publicity, loss of customer trust, or brand damage Each of these needs to be identified, assessed, and managed using appropriate techniques, ideally in a unified, ongoing process.
Yes, the core strategies (avoid, reduce, transfer, and accept) are generally enough to manage most types of risk. What matters more is choosing the right strategy for each risk and applying it effectively. The real strength lies in how well these strategies are supported by processes, tools, and clear ownership.