Choose risk-first compliance that’s always on, built for you.
Go back to blogs
What is SOC 2 Type 2? Benefits, Audit Process, Compliance and Certification in 2025
Last updated on
min. read

In our highly connected digital world, protecting sensitive data is more important than ever. SOC 2 Type 2 compliance helps organizations meet the growing demands for data security and privacy. It not only shows an organization's dedication to safeguarding information but also proves that its systems and controls can handle thorough evaluations. SOC 2 Type 2 certification isn't just about following rules; it's about earning and keeping the trust of clients, partners, and stakeholders.
This guide is aimed at organizations and professionals who seek to understand and navigate the complexities of SOC 2 Type 2 compliance. Whether you are an IT manager, a compliance officer, a business owner, or a consultant, this comprehensive resource will help you grasp the fundamentals and implementation strategies of SOC 2 Type 2 compliance.
What is the difference between SOC 2 Type 1 and Type 2 compliance?
AspectSOC 2 Type 1SOC 2 Type 2ObjectiveAssesses controls at a specific point in time to provide assurance about their design and implementation.Assesses controls over a period (typically 6-12 months) to provide assurance about their design, implementation, and effectiveness.TimeframeSnapshot assessment, usually for a single date.Continuous assessment over a defined period, typically months.SOC 2 Type 2 report contentProvides an opinion on the suitability of control design as of a specific date.Provides an opinion on the suitability of control design, implementation, and operating effectiveness over a specified period.FocusEmphasizes control design and whether controls are in place.Emphasizes control design, implementation, and how controls operate over time.Use casesTypically used for initial assessments or when a client or partner wants to evaluate control design.Often used when ongoing monitoring and assurance are required, especially for critical services or sensitive data handling.FrequencyTypically conducted annually or as needed.Conducted at least annually but can cover a more extended period for a deeper evaluation.Assurance levelLower level of assurance, as it doesn't assess control effectiveness.Higher level of assurance, as it assesses control design, implementation, and effectiveness.Cost and effortGenerally less costly and less time-consuming than Type 2.Requires more effort, resources, and time due to the continuous assessment.Client confidenceProvides some level of assurance but may not be sufficient for clients with stringent security requirements.Provides a higher level of assurance and is often preferred by clients with strict security demands.Continuous improvementLimited insights into ongoing control effectiveness.Provides valuable insights for continuous improvement by identifying control weaknesses and trends.
Both SOC 2 Type 1 and Type 2 reports serve important purposes, but the choice between them depends on the specific needs of the organization and its clients or partners. SOC 2 Type 2 certification is generally considered more comprehensive and valuable for organizations that handle sensitive data or offer critical services, as it assesses the effectiveness of controls over time.
For a deeper understanding of difference between SOC 2 Type 1 and Type 2 certificates, please refer to our blog “Choosing the right SOC 2 certification: Type I or Type IIâ€
What are the criteria for SOC 2 Type 2 compliance?
SOC 2 compliance is based on five trust service principles (TSPs). Let's break them down for better understanding and see how each principle relates to SOC 2 Type 2 compliance:
1. Security
Security involves protecting against unauthorized access, both physical and logical, to an organization's systems, data, and facilities. It encompasses measures such as access controls, encryption, and intrusion detection systems to prevent and detect security breaches.
Above all, SOC 2 Type 2 compliance requires organizations to establish and maintain effective security controls and practices over an extended period. This ensures that data and systems remain secure and protected from potential threats and vulnerabilities.
2. Availability
Availability focuses on ensuring that systems and services are available and operational when needed by authorized users. This principle addresses factors like system uptime, disaster recovery, and business continuity planning to minimize downtime and service interruptions.
Moreover, continuous monitoring of availability controls is essential to demonstrate that systems and services are consistently accessible. This is especially crucial for organizations offering critical services where downtime can have significant consequences.
3. Processing integrity
Processing integrity pertains to the accuracy, completeness, and reliability of data processing. It ensures that data is processed correctly, without errors, omissions, or unauthorized alterations. Validation checks, data reconciliation, and error handling are crucial components.
Type 2 compliance assesses not only the design and implementation of processing controls but also their ongoing effectiveness. This helps guarantee the accuracy and reliability of data processing over time, reducing the risk of errors or fraud.
4. Confidentiality
Confidentiality centers on protecting sensitive information from unauthorized disclosure. This includes safeguarding sensitive data through encryption, access controls, data classification, and employee training to prevent data leaks or unauthorized access.
Ongoing control effectiveness assessments under Type 2 compliance confirm that confidential data remains protected from unauthorized access or disclosure. This is vital for maintaining client trust and regulatory compliance.
5. Privacy
Privacy relates to how personal information is collected, used, retained, disclosed, and disposed of in accordance with privacy policies and regulations. It involves obtaining consent, maintaining data subject rights, and ensuring compliance with privacy laws like GDPR or CCPA.
Type 2 compliance ensures that privacy controls are not only in place but also operational and effective. Besides, organizations handling personal data must continuously uphold data privacy standards and comply with relevant privacy regulations.
What is the importance of controls and criteria in SOC 2 Type 2 compliance?
Controls and criteria are the foundation of SOC 2 Type 2 compliance for each of the TSPs. They serve several crucial purposes:
1. Risk mitigation
Controls mitigate risks associated with each trust service principle. By continually evaluating their effectiveness, organizations can proactively address emerging threats and vulnerabilities.
2. Regulatory compliance
Many industries are subject to regulations that require specific controls. SOC 2 Type 2 compliance helps organizations maintain compliance with these regulations by ensuring that controls are consistently in place and effective.
3. Client assurance
Clients and partners often require evidence of control effectiveness to trust that their data is secure and that services meet their needs. Type 2 compliance provides this assurance.
4. Continuous improvement
Regular assessments of controls and criteria enable organizations to identify weaknesses and opportunities for improvement. This leads to a stronger security posture and better overall performance.
In summary, controls and criteria are the backbone of SOC 2 Type 2 compliance, ensuring that organizations meet the trust service principles consistently over time. By emphasizing the ongoing effectiveness of controls, organizations can reduce risks, maintain compliance, build trust, and continuously improve their security and privacy practices.
How to prepare for SOC 2 Type 2 audit?
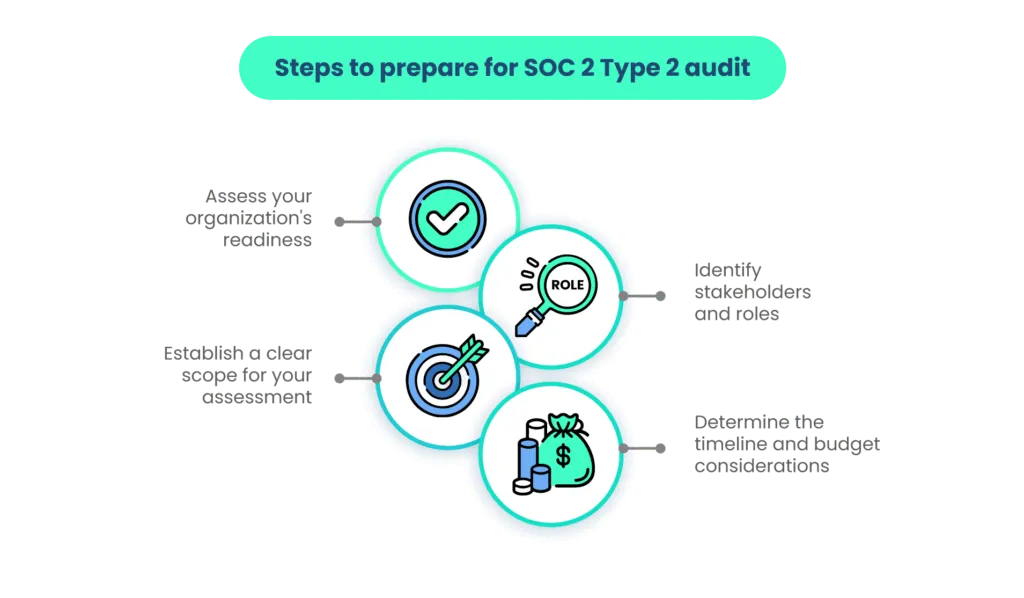
Take the following steps to prepare for the SOC 2 Type 2 audit.
1. Assess your organization's readiness
Before embarking on the SOC 2 Type 2 compliance journey, it's crucial to evaluate your organization's readiness. This assessment involves:
- Understanding your business processes: Identify the services, systems, and processes that will be subject to the SOC 2 Type 2 audit.
- Existing controls: Evaluate your existing security and privacy controls to identify strengths and weaknesses.
- Documentation: Determine the extent and quality of your documentation related to controls, policies, and procedures.
- Resources: Assess whether you have the necessary human and financial resources to support the compliance effort.
2. Identify stakeholders and roles
Clearly define the key stakeholders and their roles in the SOC 2 Type 2 audit process:
- Executive sponsor: A senior leader who champions the compliance effort and allocates necessary resources.
- Project manager: Responsible for overseeing the compliance project, including planning, execution, and communication.
- Compliance team: Identify individuals responsible for implementing and maintaining controls and documenting compliance efforts.
- External auditor: If you engage an external auditor, establish a relationship and communication plan with them.
3. Establish a clear scope for your assessment
Define the scope of your SOC 2 Type 2 audit to ensure that it aligns with your business objectives and compliance needs. Consider the following:
- In-scope services: Specify the services, systems, and processes that will be assessed for compliance.
- Trust service principles (TSPs): Determine which of the five TSPs (security, availability, processing integrity, confidentiality, and privacy) are relevant to your scope.
- Geographic locations: If your organization operates in multiple locations, clarify which sites or data centers are included.
- Third-party relationships: Identify any third-party vendors or service providers that are part of your scope.
4. Determine the timeline and budget considerations
Establish a realistic timeline and budget for your SOC 2 Type 2 compliance project:
- Timeline: Define key milestones, deadlines, and the expected duration of the assessment process. Consider the complexity of your organization and the availability of resources.
- Budget: Estimate the costs associated with compliance, including auditing fees, technology investments, staff training, and documentation expenses.
- Resource allocation: Allocate human and financial resources according to the established budget and timeline.
- Risk management: Identify potential risks that could impact the project timeline or budget and develop contingency plans.
All in all, by addressing these key preparatory steps, your organization will be better equipped to embark on the SOC 2 Type 2 compliance journey with a clear understanding of its readiness, roles and responsibilities, scope, and resource requirements. This preparation lays the foundation for a successful compliance effort and ensures that you can meet the trust service principles effectively.
What is the SOC 2 Type 2 compliance process?

Steps involved in achieving SOC 2 Type 2 compliance, along with the best practices for each stage, are given below:
1. Planning and scoping
In the initial phase of SOC 2 Type 2 compliance, known as planning and scoping, several critical steps are taken to lay the foundation for a successful compliance journey:
- Define scope: Clearly define the scope of your SOC 2 Type 2 compliance assessment, specifying the systems, services, and locations to be assessed.
- Select TSPs: Determine which trust service principles (TSPs) are applicable to your organization's services.
- Engage stakeholders: Involve key stakeholders, including an executive sponsor, compliance team, and external auditor, if necessary.
Best practices:
- Involve all relevant stakeholders early to ensure alignment on scope and objectives.
- Document the scope and TSPs clearly for reference throughout the compliance process.
2. Risk assessment
In the Risk assessment phase of SOC 2 Type 2 compliance, the focus shifts towards identifying, prioritizing, and mitigating risks associated with the trust service principles within the defined scope, adhering to best practices to ensure robust security measures.
- Identify risks: Conduct a thorough risk assessment to identify potential threats and vulnerabilities related to the TSPs in your scope.
- Prioritize risks: Prioritize identified risks based on their potential impact and likelihood.
- Risk mitigation: Develop strategies and controls to mitigate identified risks.
Best practices:
- Utilize industry-standard risk assessment methodologies.
- Consider both internal and external risks.
- Regularly review and update your risk assessment to account for changes in your environment.
3. Control implementation
The control implementation phase of SOC 2 Type 2 compliance involves selecting, implementing, and training employees on controls and policies that are carefully chosen to address identified risks while adhering to best practices for customization, gradual implementation, and maintaining a comprehensive inventory.
- Select controls: Choose appropriate controls and policies to address the identified risks and meet the TSPs' SOC 2 Type 2 requirements.
- Implement controls: Put in place the selected controls, ensuring that they are well-documented and consistently applied.
- Employee training: Train employees on control procedures and security best practices.
Best practices:
- Choose controls that are both relevant to your scope and tailored to your organization's specific risks.
- Implement controls gradually, ensuring that they align with business processes.
- Maintain an updated inventory of all implemented controls.
4. Testing and evaluation
The testing and evaluation phase of SOC 2 Type 2 compliance involves control testing, documentation review, and internal audits to ensure effectiveness, with best practices emphasizing regular assessments and automated tools.
- Control testing: Conduct testing and assessments of implemented controls to ensure their effectiveness.
- Documentation review: Review and update the documentation to reflect control implementations accurately.
- Internal audit: Perform internal audits or assessments to identify areas needing improvement.
Best practices:
- Conduct regular testing and assessments of controls, not just during the audit phase.
- Document testing procedures, results, and any deviations or exceptions.
- Use automated tools where applicable to streamline testing processes.
5. Remediation
In the remediation phase of SOC 2 Type 2 compliance, we correct deficiencies promptly, update documentation, and foster a culture of continuous improvement, following best practices.
- Correct deficiencies: Address any control deficiencies or issues identified during testing and internal audits.
- Documentation updates: Update documentation to reflect improvements and changes.
- Continuous improvement: Use this stage to continuously enhance control effectiveness.
Best practices:
- Prioritize and address control deficiencies promptly.
- Document corrective actions taken and their effectiveness.
- Maintain a culture of continuous improvement to prevent future deficiencies.
6. Independent audit
In the independent audit phase of SOC 2 Type 2 compliance, organizations engage an experienced auditor, conduct a pre-audit review, undergo the audit process, and promptly address audit findings, following best practices for success.
- Engage auditor: Select an independent auditor experienced in SOC 2 assessments if required.
- Pre-audit review: Conduct a pre-audit review to ensure readiness for the official audit.
- Audit execution: Undergo the SOC 2 Type 2 audit, which includes on-site visits, interviews, and document reviews.
- Audit report: Receive the audit report detailing findings and compliance status.
Best practices:
- Select an experienced and reputable auditor with expertise in your industry.
- Be transparent and cooperative during the audit process.
- Review and address any findings or recommendations in the audit report promptly.
How can organizations maintain SOC 2 Type 2 compliance?

The following steps must be followed by the organization for continuous SOC 2 Type 2 compliance:
1. The importance of ongoing monitoring and reporting
Ongoing monitoring and reporting are crucial to provide clients with confidence in the long-term security and reliability of our services.
- Continuous assurance: Ongoing monitoring is vital for maintaining SOC 2 Type 2 compliance. It ensures that the controls and practices you've implemented remain effective over time.
- Client trust: Consistent monitoring and reporting provide clients and partners with the assurance that their data and services continue to be secure and reliable.
- Risk management: Regularly assessing control effectiveness helps identify and mitigate emerging risks, reducing the likelihood of security incidents or compliance breaches.
2. Continuous improvement and adapting to changes
Continuous improvement is essential as it allows us to adapt our controls to evolving threats and technological advancements, ensuring our compliance remains effective.
- Evolving threat landscape: The cybersecurity landscape is dynamic. Continuous improvement allows you to adapt controls to new threats and vulnerabilities.
- Technology changes: As technology evolves, your organization's systems and processes may change. Regular assessments help ensure that controls remain aligned with these changes.
- Regulatory updates: Privacy and security regulations can change. Ongoing monitoring helps you stay compliant with evolving legal SOC 2 Type 2 requirements.
- Feedback loop: Create a feedback loop for lessons learned from incidents, audits, or control assessments. Use this feedback to refine and enhance your controls continuously.
3. Addressing common challenges and pitfalls
To maintain SOC 2 Type 2 compliance successfully, we must proactively tackle challenges such as resource constraints, compliance fatigue, and the risk of scope creep while also fostering clear communication among teams.
- Resource constraints: Lack of resources, both human and financial, can hinder compliance efforts. Allocate adequate resources and consider automation to streamline processes.
- Compliance fatigue: Compliance efforts can be taxing on employees. Maintain a culture of compliance and provide ongoing training and awareness programs.
- Scope creep: Expanding services or systems without adjusting controls can lead to compliance gaps. Regularly review and update your scope to reflect changes.
- Documentation neglect: Inadequate documentation can lead to compliance failures. Maintain up-to-date documentation for all controls, policies, and procedures.
- Third-party risks: Third-party vendors may introduce security and compliance risks. Continuously assess and monitor third-party relationships to ensure they meet your standards.
- Audit preparedness: Organizations often struggle with staying audit-ready at all times. Conduct periodic internal audits or assessments to identify and correct issues proactively.
- Communication breakdown: Poor communication among teams can lead to control failures. Establish clear communication channels to ensure everyone is aware of their roles and responsibilities.
What are the benefits of SOC 2 Type 2 compliance?
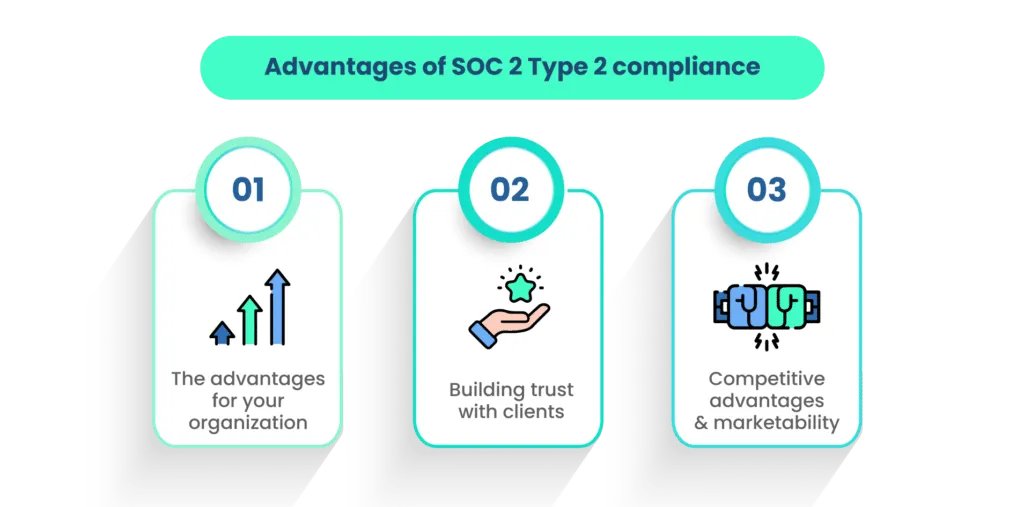
There are three faceted advantages to SOC 2 Type 2 compliance:
1. The advantages for your organization
SOC 2 Type 2 compliance brings enhanced data security, operational efficiency, and client retention, safeguarding our reputation and bottom line.
- Enhanced data security: SOC 2 Type 2 compliance ensures that our data security measures are robust and effective, reducing the risk of data breaches and their associated costs.
- Operational efficiency: Compliance requires well-defined processes and controls, leading to increased operational efficiency and reduced downtime.
- Client retention: SOC 2 Type 2 compliance reassures existing clients that their data is in safe hands, promoting client retention and loyalty.
2. Building trust with clients
By undergoing independent audits and transparently reporting control effectiveness, SOC 2 Type 2 compliance assures clients that their data is secure, fostering trust and long-term partnerships.
- Third-party validation: SOC 2 Type 2 compliance demonstrates our commitment to security and privacy through an independent third-party audit, building trust with clients.
- Transparency: Compliance involves transparent reporting on control effectiveness, giving clients insight into our commitment to maintaining high standards.
- Data protection: Clients trust us with their sensitive data; SOC 2 Type 2 compliance assures them that we prioritize data protection and privacy.
3. Competitive advantages and marketability
Our SOC 2 Type 2 compliance not only gives us a competitive edge but also expands our client base and mitigates risks, positioning us as a reliable and trustworthy choice in the marketplace.
- Competitive edge: Compliance sets us apart in the marketplace, as many clients prefer working with organizations that adhere to rigorous security and privacy standards.
- Expanded client base: SOC 2 Type 2 compliance opens doors to new clients and partnerships, especially in industries where data security is paramount.
- Risk mitigation: Compliance helps mitigate legal and financial risks associated with data breaches and regulatory non-compliance, reducing potential liabilities.
What is the relevance of SOC 2 Type 2 certification for ongoing monitoring?
SOC 2 Type 2 reports are highly relevant for ongoing monitoring because they provide a comprehensive assessment of an organization's controls, focusing on their design, implementation, and effectiveness over an extended period.

This ongoing evaluation is essential for several reasons:
1. Continuous assurance
Firstly, SOC 2 Type 2 audits offer continuous assurance to stakeholders, demonstrating that controls are not only in place but also operational and effective over time. This is particularly important in dynamic business environments.
2. Risk management
Secondly, ongoing monitoring helps identify and mitigate risks as they evolve. By regularly assessing control effectiveness, organizations can proactively address vulnerabilities and security threats.
3. Regulatory compliance
Many industries are subject to regulatory requirements that necessitate continuous monitoring of security and privacy controls. SOC 2 Type 2 report helps organizations demonstrate compliance with these regulations.
4. Client trust
Clients, customers, and partners often require ongoing assurance that their data is being handled securely. SOC 2 Type 2 reports provide this confidence by showing that controls are consistently maintained.
5. Data-centric sectors
Industries dealing with sensitive data, such as healthcare, finance, and technology, benefit from continuous monitoring. These sectors are more susceptible to data breaches and must demonstrate a sustained commitment to data protection.
6. Service providers
Service organizations, including cloud service providers, data centers, and managed IT service providers, benefit significantly from ongoing monitoring. They can showcase their dedication to delivering secure services to clients.
7. Internal improvement
Lastly, SOC 2 Type 2 audits help organizations internally. By identifying weaknesses or areas for improvement in controls over time, they can enhance their security posture and operational efficiency.
Which industries and organizations benefit from SOC 2 Type 2 audits?
Several industries and organizations benefit from SOC 2 Type 2 compliance due to their reliance on secure data handling and ongoing assurance. These include:
1. Healthcare: Healthcare providers, including hospitals and clinics, must safeguard patient health records and sensitive medical information.
2. Financial services: Banks, credit unions, insurance companies, and fintech firms require robust controls to protect financial data and transactions.
3. Technology: Software-as-a-Service (SaaS) providers, data centers, and IT managed service providers need to assure clients of their data security and operational reliability.
4. Cloud service providers: Organizations offering cloud computing services rely on SOC 2 Type 2 certification to demonstrate the security and availability of their cloud infrastructure.
5. E-commerce: Online retailers and payment processors handling customer payment information benefit from ongoing monitoring to prevent data breaches.
6. Legal services: Law firms handling sensitive client information require stringent controls to maintain confidentiality and data security.
7. Higher education: Universities and colleges need to protect student data and maintain the integrity of their academic systems.
8. Consulting firms: Consulting companies that advise clients on security and compliance often undergo SOC 2 Type 2 audits to demonstrate their expertise.
9. Government contractors: Organizations working with government agencies must meet specific security requirements and often benefit from SOC 2 Type 2 compliance.
10. Data-intensive startups: Emerging technology companies that collect and process large volumes of user data can build trust and credibility through SOC 2 Type 2 reports.
In summary, SOC 2 Ty
Table of contents