Choose risk-first compliance that’s always on, built for you.
Go back to blogs
SOC 2 vs SOC 3: Key differences
Last updated on
June 24, 2025
min. read

If you run a SaaS business or offer cloud services, keeping your security strong isn't just important it's key to earning trust and driving sign-ups. Along with putting the right security measures in place, you also need compliance certifications to show customers, investors, and prospects that you take security seriously. One of the most recognized reporting frameworks for this is SOC (Service Organization Controls).
Created by the American Institute of Certified Public Accountants (AICPA), SOC includes different types of frameworks SOC 1, SOC 2, and SOC 3 that help businesses manage customer data securely.
But figuring out which SOC report your business needs can be tricky. In this blog, we'll break down the differences between SOC 2 and SOC 3 to help you decide which one is right for you.
SOC 2 vs SOC 3 at a glance
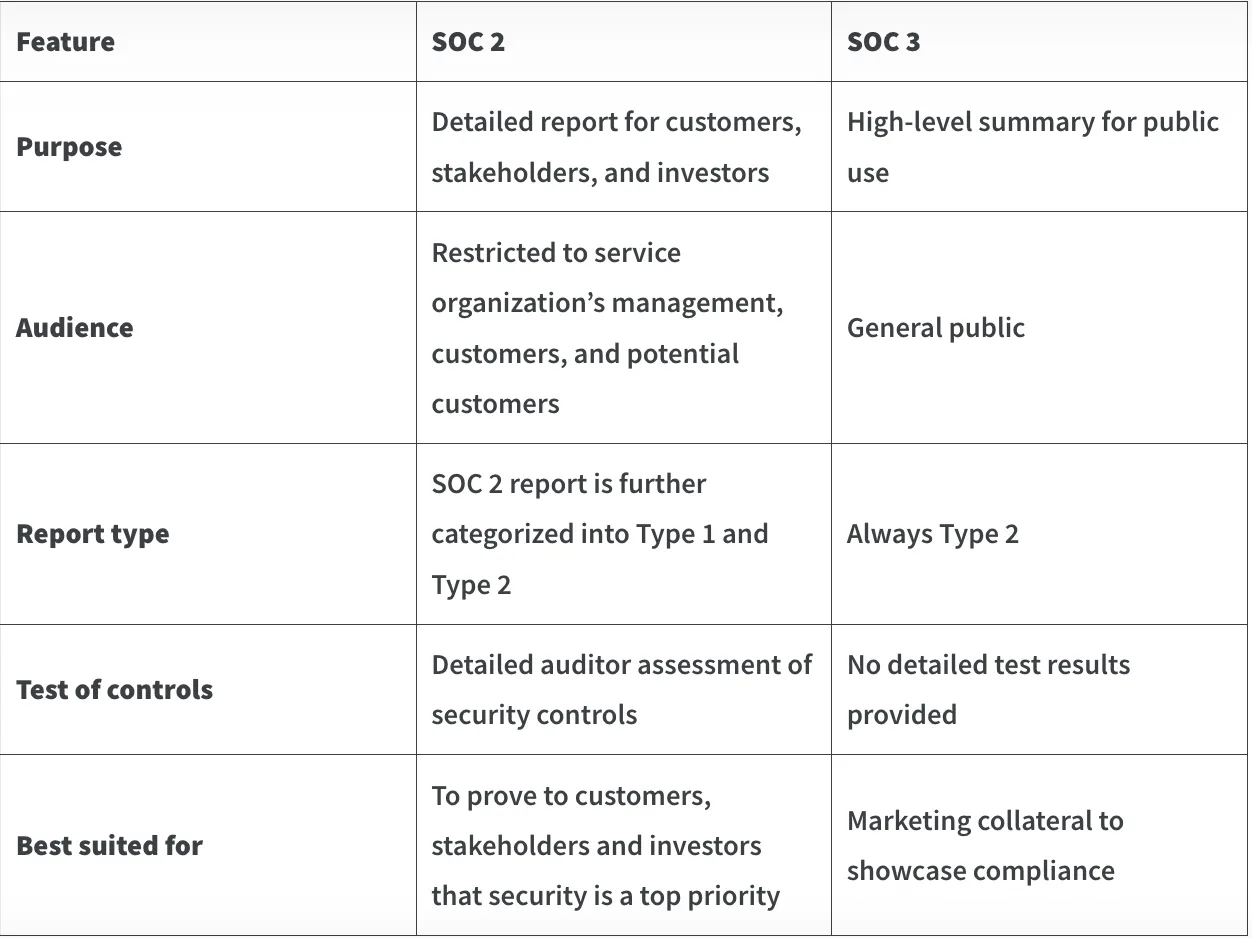
What is SOC 2?
System and Organization Controls 2 (SOC 2) is an audit report that evaluates an organization's controls based on five Trust Services Criteria: security, availability, processing integrity, confidentiality, and privacy. Developed by AICPA in 2010, the report evaluates how well a service organization safeguards customer data.
The reporting framework is widely adopted by technology companies, particularly those offering cloud-based services, to demonstrate their commitment to data protection.
SOC 2 compliance is not a legal requirement, but it has become an industry standard. Many businesses, particularly in sectors like SaaS, financial services, and healthcare, require their vendors to undergo SOC 2 audits before entering into partnerships. While failing to obtain a SOC 2 report does not result in regulatory penalties, the absence of compliance can lead to lost business opportunities and diminished customer trust.
How to get SOC 2 certification?
The timeline for obtaining SOC 2 certification depends on the type of audit. A SOC 2 Type 1 audit, which assesses the design of controls at a specific point in time, typically takes a few weeks to a couple of months to complete. In contrast, a SOC 2 Type 2 audit evaluates both the design and operational effectiveness of controls over a period usually ranging from three to twelve months making it a longer and more comprehensive process.
The cost of a SOC 2 audit varies based on factors like company size, complexity, and the audit firm. A SOC 2 Type 1 audit generally costs between $15,000 and $40,000, while a SOC 2 Type 2 audit, given its extended evaluation period, ranges from $30,000 to $80,000. Additional expenses may include readiness assessments, security tools, and ongoing compliance management.
Once achieved, SOC 2 certification remains valid as long as an organization continues to meet the requirements. However, since SOC 2 reports assess controls at a given point or over a defined period, companies must undergo regular audits typically annually to maintain compliance and demonstrate ongoing security and trustworthiness to customers and partners.
Who needs SOC 2?
SOC 2 is widely adopted by companies handling customer data, particularly in cloud-based services. While not legally required, it helps meet contractual obligations and build trust, especially in regions with strict data security regulations. It is most relevant for technology companies like SaaS and cloud service providers but is also valuable for financial institutions, healthcare organizations, and any business managing sensitive data. However, in healthcare and finance, SOC 2 is more of an additional requirement alongside HIPAA and GLBA, respectively.
What are the requirements of SOC 2?
SOC 2 compliance is based on the Trust Services Criteria established by the AICPA, which outlines key areas organizations can address to protect customer data by designing their own controls. The requirements include:
Security: Implementing controls to protect systems and data from unauthorized access, with security being the mandatory and foundational Trust Services criterion.
Availability: Ensuring systems are operational and accessible as agreed in service commitments.
Processing integrity: Ensuring data processing is accurate, timely, authorized, and maintains completeness and validity.
Confidentiality: Protecting sensitive information from unauthorized disclosure.
Privacy: Managing personal data in accordance with privacy policies and its own privacy commitments and applicable laws.
Advantages of SOC 2
- Enhanced security: SOC 2 evaluates whether a company's security controls align with the relevant Trust Services Criteria, indicating its commitment to protecting sensitive information and reducing the risk of data breaches.
- Stronger customer trust: By undergoing an independent audit to validate their security controls, organizations can reassure customers and stakeholders that their data is handled securely.
- Business growth: Achieving SOC 2 compliance can open doors to new business opportunities by demonstrating a commitment to security and compliance.
Disadvantages of SOC 2
- High cost: Achieving and maintaining SOC 2 compliance can be expensive, particularly for smaller businesses, due to audit fees and the cost of implementing necessary security controls.
- Resource-intensive process: Preparing for a SOC 2 audit requires significant time and effort, as organizations must document policies, implement procedures, and continuously monitor controls.
- Limited scope: While SOC 2 focuses on data security and privacy, it may not cover all aspects of cybersecurity, leaving certain risks unaddressed. Additionally, it does not prescribe specific security controls, allowing organizations to design their own based on the chosen Trust Services Criteria.
What is SOC 3?
SOC 3 is a publicly available report derived from a SOC 2 report. Issued by an independent auditor, it summarizes an organization's security controls based on the Trust Services Criteria (TSC) established by the AICPA. Unlike the detailed SOC 2 report, which is shared with stakeholders under an NDA, SOC 3 is a high-level, simplified version intended for public distribution.
SOC 3 is not a separate certification or compliance standard. Organizations must first complete a SOC 2 audit to be eligible for a SOC 3 report, as it does not involve additional testing or a separate audit process. It simply presents SOC 2 findings in a format that businesses can use to publicly demonstrate their adherence to security best practices without revealing detailed control assessments.
How to get SOC 3?
There is no separate SOC 3 audit. The SOC 3 report is generated only after an organization has undergone a SOC 2 audit and received a SOC 2 report. Since SOC 3 is a summary, companies that do not have a SOC 2 report are not eligible for SOC 3. The same challenges such as audit costs, resource investment, and ongoing monitoring apply to both.
Who uses SOC 3?
SOC 3 reports are widely used in the United States and internationally by organizations that want to publicly demonstrate their adherence to security best practices. They are particularly useful for SaaS providers, cloud service companies, and any business handling customer data that wants to showcase its commitment to security without sharing detailed SOC 2 findings.
What are the requirements of SOC 3?
SOC 3 does not have separate requirements. It is entirely derived from SOC 2 and includes the same Trust Services Criteria (TSC), which cover:
- Security - Protecting systems and data from unauthorized access.
- Availability - Ensuring systems are operational and accessible as committed.
- Processing integrity - Ensuring data processing is accurate, complete, and timely.
- Confidentiality - Restricting access to sensitive information.
- Privacy - Managing personal data in line with privacy policies and regulations.
Advantages of SOC 3
- Great for marketing: Since SOC 3 reports are designed for public distribution, organizations can use them as marketing collateral to build trust and credibility without disclosing specific controls or audit details.
- Easier to share: Businesses can freely share SOC 3 reports with clients, partners, and prospects without requiring NDAs or additional access permissions.
Disadvantages of SOC 3
- Lacks detailed insights: SOC 3 reports do not include the in-depth findings found in SOC 2, which some clients may require for greater assurance.
- May not meet regulatory requirements: Organizations in highly regulated industries often need more comprehensive security assessments, making SOC 3 insufficient.
- Limited visibility into internal controls: The absence of detailed control evaluations may leave some stakeholders needing more comprehensive information.
How Scrut streamlines your path to compliance
Scrut simplifies and accelerates the SOC 2 audit process, helping organizations implement and monitor security controls efficiently. Scrut enables businesses to streamline their SOC 2 journey ensuring they meet the necessary requirements to obtain both SOC 2 and SOC 3 reports. By automating key compliance tasks and reducing manual effort, Scrut helps organizations maintain continuous adherence to security best practices and effectively demonstrate their commitment to data security.
With Scrut, businesses can:
1. Monitor controls in real time: Continuous monitoring ensures security configurations and policies align with SOC 2 requirements, identifying potential compliance gaps before they become issues.
2. Automate evidence collection: With 70+ integrations, Scrut reduces manual effort by automating over 65% of evidence collection, mapping it directly to SOC 2 controls.
3. Build SOC-2-compliant policies in minutes: Leverage Scrut's policy library with 75+ pre-built policies or upload your own to quickly establish a SOC-2-compliant infosec program. Customize policies with the in-built editor and have them vetted by Scrut's in-house compliance experts.
4. Accelerate the audit process: Scrut enables seamless collaboration with auditors by allowing them to review evidence, track progress, and complete assessments within the platform.
5. Get expert guidance: Access in-house SOC 2 compliance experts and auditors for tailored advice and best practices.

FAQs
Can I replace SOC 2 with SOC 3?
No. A SOC 3 report is simply a summarized version of a SOC 2 report and does not include detailed control assessments. Organizations that do not undergo a SOC 2 audit cannot obtain a SOC 3 report.
What are the similarities between SOC 2 and SOC 3?
- Both are based on the AICPA Trust Services Criteria.
- Both require an independent SOC 2 audit by a CPA firm.
- Both cover security, availability, processing integrity, confidentiality, and privacy.
- SOC 3 is derived from SOC 2, meaning organizations must first complete a SOC 2 audit to obtain a SOC 3 report.
Table of contents


















