Choose risk-first compliance that’s always on, built for you.
Go back to blogs
What are SOC 2 Trust Services Criteria and why do they matter?
Last updated on
min. read

As a CEO looking to navigate the complex world of data security, you've likely heard about SOC 2 (System and Organization Controls 2) compliance and Trust Services Criteria (TSC). However, you might still wonder what they truly mean for your business.
In today's fast-paced digital world, safeguarding sensitive information isn't just a technical responsibility—it's a strategic imperative. Clients, vendors, and stakeholders expect your organization, especially if you're in SaaS or tech, to have rock-solid security measures in place. SOC 2 compliance is one of the most recognized ways to show you're serious about data protection. But where do the Trust Services Criteria fit in?
Think of the Trust Services Criteria as the foundation for your SOC 2 compliance. These criteria represent the pillars that uphold your company's security, privacy, and operational integrity. They are essential because they guide the entire compliance process and ensure you cover all critical aspects of data protection.
In short, understanding and implementing the TSC is how you demonstrate to the world that your business is prepared to handle data securely and responsibly.
One of the most recognized ways to prove this is through a SOC 2 report. But what exactly is SOC 2, and why should you care about the Trust Services Criteria (TSC) it involves?
Let's dive in.
What are the SOC 2 Trust Services Criteria?
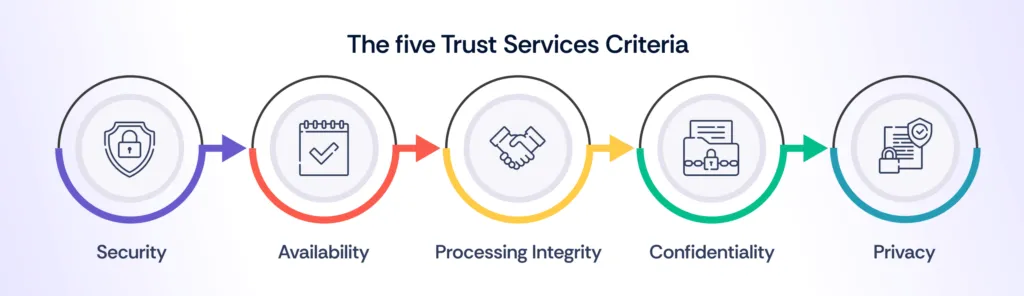
SOC 2 is a framework established by the American Institute of Certified Public Accountants (AICPA) designed to evaluate how well an organization manages data based on five key principles.
Originally known as the SOC 2 Trust Services Principles (TSP), these 5 trust services criteria for SOC 2 are now referred to as Trust Services Criteria (TSC) and are used to assess the effectiveness of controls related to data security and privacy.
Why are SOC 2 TSCs important?
The scope of SOC 2 compliance is vast and companies need not tick every box in the checklist to be SOC 2 compliant for their respective industry. The SOC 2 Trust Services Criteria (TSCs) provide a framework for businesses across different industries to choose the most suitable path towards compliance.
Do note that apart from the Security TSC, all others are not mandatory.
1. Security
The Security Trust Criteria are fundamental to any SOC 2 report. Among the five, Security is a mandatory criterion for every SOC 2 audit. This criterion focuses on protecting information throughout its lifecycle, ensuring appropriate controls are in place to safeguard against unauthorized access, data breaches, and system failures.
It provides guidelines for control environments, risk assessment, and monitoring, ensuring that systems are protected from misuse, theft, or unauthorized alterations.
All SOC 2 audits must include Security to demonstrate protection against data breaches and unauthorized access.
2. Availability
Availability is concerned with whether information and systems are consistently accessible as needed to meet the organization's objectives. This criterion is particularly relevant for businesses that provide data centers, SaaS, or hosting services.
If your platform supports continuous delivery or is critical to client operations, addressing Availability in your SOC 2 report is crucial. This ensures that any downtime or service interruptions are managed and communicated effectively, often involving Service Level Agreements (SLAs) to reassure clients of your operational reliability.
- For companies requiring 24/7 uptime, such as cloud service providers.
3. Processing integrity
Processing Integrity focuses on the accuracy and completeness of data processing. It ensures that your systems perform without errors, omissions, or delays. This criterion is important for businesses that handle transactions or data processing, such as e-commerce platforms or service providers managing client transactions.
By adhering to this criterion, you demonstrate that your systems operate correctly and reliably, providing confidence in your data processing capabilities.
- Essential for businesses managing financial transactions or e-commerce to ensure accurate data processing.
4. Confidentiality
One of the trust principles SOC 2 addresses is confidentiality.
Confidentiality addresses how organizations protect sensitive information by restricting access, storage, and usage to authorized individuals only.
This criterion is essential if your organization handles confidential data like personal information, financial records, or proprietary business information.
Implementing robust confidentiality controls helps safeguard against unauthorized access and ensures that sensitive information remains secure.
- Important for sectors handling sensitive personal or proprietary data, such as healthcare and financial services.
5. Privacy
Privacy is closely related to Confidentiality but focuses specifically on how organizations handle personally identifiable information (PII). This criterion evaluates how your organization collects, uses, and shares PII, ensuring that personal data is protected according to legal and regulatory requirements.
If your organization directly manages customer data, including details such as names, addresses, and purchase histories, incorporating Privacy into your SOC 2 report is crucial.
- Important for sectors handling sensitive personal or proprietary data, such as healthcare and financial services.
Also read: Remote SOC 2 Audits: A Comprehensive Guide
Prioritizing Trust Services Criteria based on industry needs
Different industries have varying priorities when it comes to SOC 2 Trust Services Criteria (TSC). Recognizing which criteria to emphasize allows businesses to align their compliance efforts with industry-specific needs and regulatory requirements.
Industry-Specific Prioritization:
IndustryKey CriteriaFocusHow does it affect revenue?SaaS and TechnologySecurity, AvailabilityProtect client data and ensure platform uptime. Security safeguards sensitive information, while Availability ensures the service remains operational, impacting reputation and customer trust.- 99.99% Uptime is the industry standard for many SaaS providers.- The average cost of a data breach for technology companies is $5.04 million (IBM, 2023).Financial ServicesPrivacy, ConfidentialityProtect sensitive personal and financial data to comply with regulations (e.g., GDPR, CCPA) and maintain client trust. Privacy and Confidentiality are crucial for safeguarding financial information.- 70% of financial services firms have experienced a cybersecurity incident in the past year.- Average breach cost for financial institutions: $5.85 million (IBM, 2023).HealthcareConfidentiality, Privacy, AvailabilitySecure Patient Health Information (PHI) in compliance with HIPAA, and ensure system uptime to support continuous patient care and operational efficiency.- 60% of healthcare organizations experienced a data breach in the last year.- Healthcare breaches cost an average of $10.93 million per incident (IBM, 2023).E-Commerce and RetailProcessing Integrity, SecurityEnsure accurate transaction processing and protect payment information. Processing Integrity is vital for order accuracy, while Security defends against breaches and fraud.- The average cart abandonment rate is 69.8%, often due to system downtime or slow performance.- Cost of e-commerce data breaches: $3.28 million (IBM, 2023).
By tailoring your SOC 2 report to highlight the most relevant criteria for your industry, you can effectively address operational risks, regulatory compliance, and customer trust. This approach not only aligns with your business's specific needs but also demonstrates a commitment to data protection across critical areas.
Also read: SOC 1 vs SOC 2 vs SOC 3: A walkthrough
How the Trust Services Criteria relate to other frameworks
Many organizations find themselves needing to comply with multiple standards, such as GDPR, HIPAA, or ISO 27001, alongside SOC 2. Fortunately, the Trust Services Criteria can align with these frameworks, allowing organizations to streamline their compliance efforts.
For instance:
- Security in SOC 2 often overlaps with ISO 27001's Information Security Management System (ISMS) controls, which both aim to protect the confidentiality, integrity, and availability of information.
- Privacy in SOC 2 closely mirrors GDPR's requirements regarding the protection of personal data. By incorporating SOC 2 Privacy controls, organizations can simultaneously work toward GDPR compliance.
- For organizations in the healthcare industry, SOC 2's Confidentiality criterion complements HIPAA's requirements for protecting patient health information.
By recognizing the parallels between SOC 2 Trust Services Criteria and other widely adopted frameworks, organizations can avoid duplication of effort and build a more cohesive compliance strategy.
However, spotting these overlaps without the relevant expertise can be time-consuming and costly. This is where leveraging compliance automation software, like Scrut's Compliance Automation, becomes invaluable.
It streamlines the entire process, helping you integrate various frameworks while saving time and money, ensuring audits are both efficient and comprehensive.
Continuous monitoring of Trust Services Criteria
Achieving SOC 2 compliance isn't a one-time event; it requires continuous monitoring to ensure ongoing adherence to the Trust Services Criteria. Businesses must regularly assess their controls and update them as necessary to address evolving risks, changing regulations, and technological advancements.
Continuous monitoring involves tracking system performance, reviewing access logs, and conducting regular vulnerability assessments to identify potential security gaps. Automated tools can help businesses streamline this process by providing real-time alerts, generating compliance reports, and managing security incidents swiftly.
BarRaiser helps organizations standardize interviews using its AI-powered platform, supported by industry experts for a fair and predictive recruitment process. With data on over 70,000 candidates, their platform constantly evolves, making continuous monitoring of their extensive cloud assets essential for maintaining information security.
To ensure a strong security posture, BarRaiser partnered with Scrut Automation, enabling automatic monitoring of their cloud environment, detecting risks and misconfigurations. Scrut's GRC automation has simplified BarRaiser's ability to maintain continuous compliance with ISO 27001, SOC 2, and GDPR.
Ensuring continuous monitoring across various criteria can become a major hassle without the right infrastructure and manpower. For example, maintaining Security demands constant oversight of user access to detect unauthorized activities. Availability requires tracking system uptime and disruptions while Processing Integrity involves ongoing validation of data accuracy.
This is where a plug-and-play solution like Scrut's Compliance Automation Software proves essential. It simplifies continuous monitoring by automating these critical tasks, ensuring seamless tracking and validation without draining your team's resources, ultimately saving time and reducing risks.
By using automation and regular audits to monitor compliance, organizations can ensure they remain aligned with the Trust Services Criteria over time. This proactive approach not only helps maintain compliance but also ensures that the business stays ahead of potential risks and security threats as they arise.
Also read: Why does your company need SOC reports?
What are SOC 2 supplemental criteria?
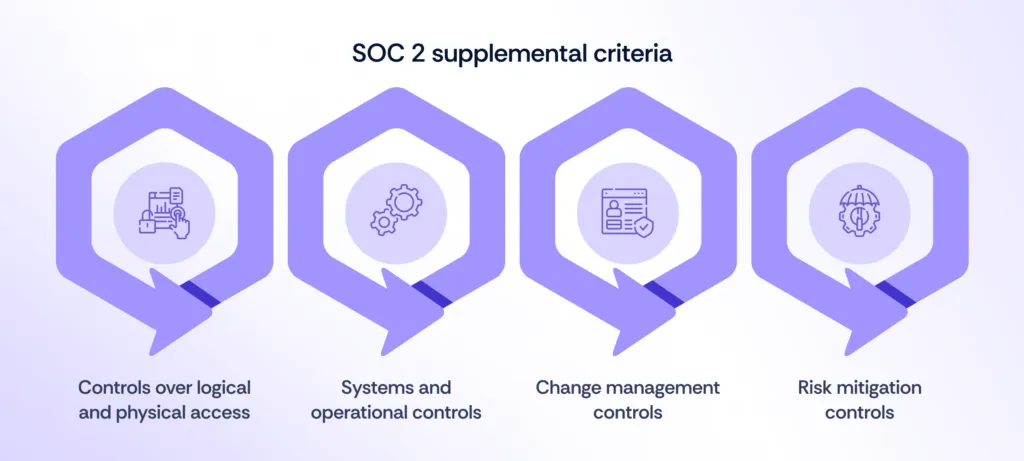
SOC 2 supplemental criteria are additional controls that strengthen the overall effectiveness of internal processes. These criteria are crucial for trust service engagements and cover areas such as logical and physical security, system and operations management, change control, and risk mitigation strategies.
1. Controls over logical and physical access
These controls ensure organizations implement both virtual and physical measures to safeguard data confidentiality, integrity, and privacy. Examples of such controls include restricting access based on roles and responsibilities, securing devices and workstations, and managing credentials effectively. It also involves limiting physical access to facilities and assets containing sensitive data, allowing only authorized personnel.
- Financial services: Strict access controls over sensitive financial information and client data are essential to prevent fraud and meet regulatory standards (e.g., GDPR, CCPA).
- Healthcare: Protecting electronic health records (EHR) and physical access to health information systems is critical for HIPAA compliance.
- Retail and e-commerce: Securing payment processing systems from both physical and digital unauthorized access prevents breaches and fraud in payment gateways.
2. Systems and operational controls
At the core of systems and operational controls is ensuring the efficiency and resilience of your infrastructure. These controls assess how effectively operations can recover after disruptions or incidents.
Common controls include threat detection, incident response, root cause analysis, and compliance management, all of which help maintain operational integrity.
Utilizing Managed Detection and Response (MDR) services can significantly enhance these efforts by providing real-time threat monitoring and rapid response.
3. Change management controls
Change management controls encompass the policies and procedures that organizations must adhere to when modifying processes, software, data, or infrastructure. Implementing scalable patch management solutions is recommended to stay updated with software changes while ensuring security measures remain intact.
These tools help manage software development changes while protecting systems from potential security vulnerabilities.
4. Risk mitigation controls
Risk mitigation controls help identify and address risks associated with growth, location, and security best practices. In addition to assessing risks from vendors and business partners, organizations must conduct internal risk assessments for factors such as leadership transitions, regulatory changes, environmental shifts, and technological advancements.
During the risk assessment process, risks are categorized by likelihood and impact, and appropriate internal controls are implemented to minimize their effects.
Also read: 5 best practices for a successful SOC 2 audit
Final thoughts
While not all organizations need to address all 5 Trust Services Criteria for SOC 2, Security is a mandatory component of every SOC 2 report. The other criteria—Availability, Processing Integrity, Confidentiality, and Privacy—should be included based on the relevance to your services and operations.
Tailoring your SOC 2 report to include the criteria that matter most to your business ensures that you effectively demonstrate your commitment to data security and privacy. Moreover, by identifying overlaps between SOC 2 and other frameworks like ISO 27001, HIPAA, or GDPR, companies can address multiple compliance requirements simultaneously, reducing effort and costs.
For organizations looking to streamline compliance efforts, platforms like Scrut Automation can simplify the process. Scrut helps reduce the manual effort involved in maintaining compliance with SOC 2 and other standards, making governance, risk, and compliance more manageable. Get in touch with us to learn more!
Frequently Asked Questions
1. What are SOC 2 Trust Services Criteria? SOC 2 Trust Services Criteria are a set of standards used to evaluate and ensure that a service organization's controls and processes meet specific requirements related to security, availability, processing integrity, confidentiality, and privacy. These criteria are part of the SOC 2 framework, which is designed to help businesses manage and protect customer data.
2. Why is SOC 2 Trust Services Criteria important for businesses? The SOC 2 Trust Services Criteria are crucial because they provide a framework for assessing and demonstrating how well a company manages and protects customer data. Compliance with these criteria helps build trust with clients, ensures data security and privacy, and can be a key differentiator in competitive markets.
3. How do SOC 2 Trust Services Criteria differ from other security frameworks? SOC 2 Trust Services Criteria are specifically tailored for service organizations and focus on aspects such as security, availability, processing integrity, confidentiality, and privacy. Unlike frameworks like ISO 27001, which provides a broad information security management system, SOC 2 criteria are designed for evaluating service organizations' control environments and are often used to meet client-specific requirements.
4. What are the benefits of achieving SOC 2 compliance? Achieving SOC 2 compliance offers several benefits, including enhanced credibility and trust with clients, improved security practices, and a competitive advantage in the marketplace. It also helps organizations meet regulatory requirements and reduces the risk of data breaches and associated penalties.
5. How often should a SOC 2 report be obtained? SOC 2 reports are typically obtained annually. This annual review ensures that the organization's controls are continuously effective and up-to-date, and it helps maintain ongoing compliance with the Trust Services Criteria. Regular audits also provide clients with assurance of the organization's commitment to data security and privacy.
6. Do I need to address all Trust Services Criteria in my SOC 2 audit? Not necessarily. While Security is mandatory, the other criteria—Availability, Processing Integrity, Confidentiality, and Privacy—are optional and should be included based on their relevance to your services.
7. Are Trust Services Principles (TSP) and Trust Services Criteria (TSC) different? No, they are the same. The term "Trust Services Criteria" replaced "Trust Services Principles" but refers to the same framework and principles.
8. Why is SOC 2 compliance important for my organization? SOC 2 compliance demonstrates your ability to handle data securely, which builds trust with clients and stakeholders, helps meet regulatory requirements, and can give you a competitive edge.
Table of contents


















