Choose risk-first compliance that’s always on, built for you.
Go back to blogs
SOC 2 vs HIPAA: Key Differences Explained
Last updated on
June 24, 2025
min. read
.webp)
In today’s data-driven economy, many companies handle a mix of sensitive customer information and patient health data. Industries such as healthcare, technology, and financial services increasingly require both SOC 2 and HIPAA to meet their legal, contractual, and security obligations.
SOC 2 compliance demonstrates effective data security practices, while HIPAA compliance ensures protected health information (PHI) is safeguarded according to U.S. healthcare regulations. Organizations must understand how these frameworks overlap and complement one another.
This blog will offer a comparison of SOC 2 and HIPAA by exploring their focus areas and applicability. By the end, CEOs will gain a clear picture of the different roles SOC 2 and HIPAA play in their operations and when adopting both frameworks may be the best approach.
The purpose and scope of SOC 2
SOC 2 is designed primarily for service-based organizations that manage customer data, especially those operating outside the healthcare space. It is relevant to companies such as SaaS providers, data processors, cloud infrastructure providers, and outsourced IT service providers. These organizations often handle sensitive business data on behalf of clients and must demonstrate that they can maintain robust security and operational controls.
Scope:
SOC 2 focuses on the Trust Services Criteria (TSC), which encompass the following five core areas:
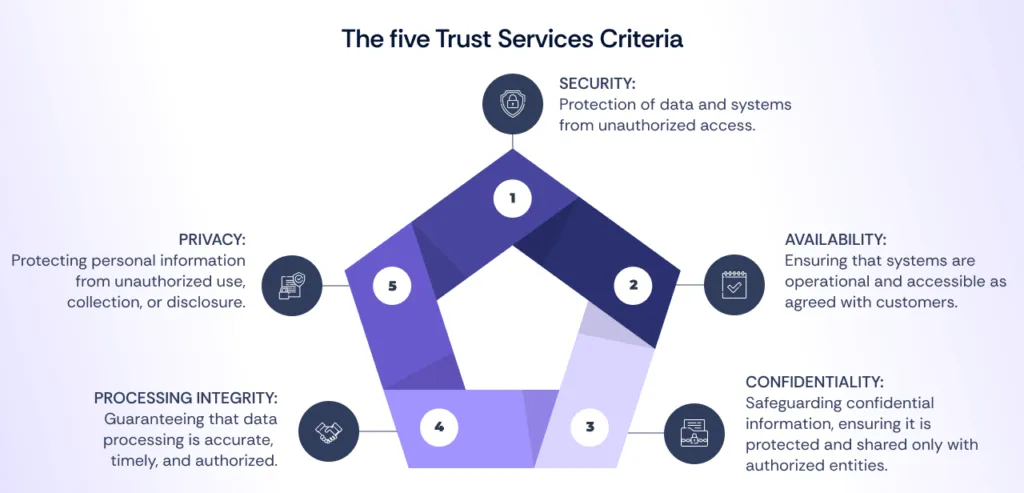
Organizations can customize their SOC 2 report by selecting the specific Trust Services Criteria relevant to their operations and business needs.
Purpose:
The main goal of SOC 2 is to provide assurance to customers that their data is managed securely and responsibly. For companies offering cloud services or outsourcing operations, it signals to clients that internal controls meet industry standards for data protection.
While SOC 2 is not mandated by law, many companies seek certification to build trust with customers, satisfy contractual obligations, and gain a competitive edge in the marketplace.
By focusing on the security and integrity of customer data across various sectors, SOC 2 plays a crucial role in reducing operational risks for service providers and their clients.
Read also: SOC 2 compliance: Top 10 challenges and strategies to solve them
The purpose and scope of HIPAA compliance
HIPAA compliance is aimed at organizations in the healthcare sector and their partners who handle PHI. These entities fall into two categories:
- Covered entities: Organizations directly involved in healthcare, such as hospitals, clinics, insurers, and pharmacies.
- Business associates: Vendors and service providers that process or store PHI on behalf of covered entities, including IT service providers, billing companies, and cloud storage providers.
Both categories are legally required to comply with HIPAA regulations to ensure PHI is properly protected.
Scope:
HIPAA compliance covers three primary rules to protect patient data:
These rules work together to ensure that patient health information is handled securely and disclosed only when necessary.
Purpose:
HIPAA’s primary objective is to establish legal obligations for safeguarding PHI and ensuring patient privacy. Unlike SOC 2, which is voluntary, HIPAA is a federal regulation in the United States, with non-compliance resulting in penalties, fines, and legal action.
The purpose is not only to prevent data breaches but also to promote trust between healthcare providers and patients by ensuring that personal health data is protected.
Organizations subject to HIPAA must implement rigorous controls and processes to prevent unauthorized access to PHI, minimize data breaches, and comply with audit and reporting requirements. HIPAA compliance helps healthcare entities avoid reputational and financial risks while fostering a secure healthcare ecosystem.
Read also: Guardians of healthcare data: Mastering HIPAA audit trail requirements
Key differences between SOC 2 vs HIPAA
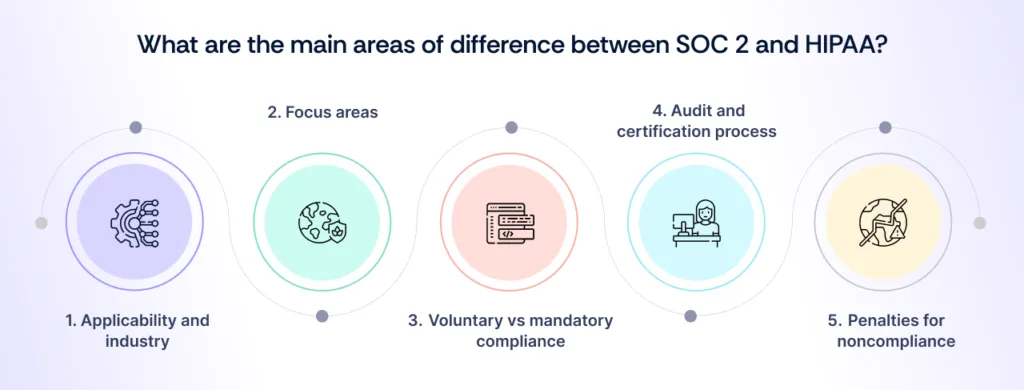
SOC 2 vs HIPAA highlights the distinct compliance needs and industry focus of these two frameworks. SOC 2 emphasizes data security practices across various sectors, serving service providers like SaaS and IT companies, while HIPAA is mandatory for healthcare entities handling PHI.
Understanding the key differences between SOC 2 and HIPAA helps organizations align their security efforts with the appropriate standards.
Applicability and industry focus in SOC 2 vs HIPAA:
Focus areas in SOC 2 vs HIPAA:
Voluntary vs. mandatory compliance:
Audit and certification process in SOC 2 vs HIPAA:
Penalties for non-compliance in HIPAA vs SOC 2:
Also Read : Understanding SOC 2 Report: A Comprehensive Guide
Where SOC 2 and HIPAA overlap
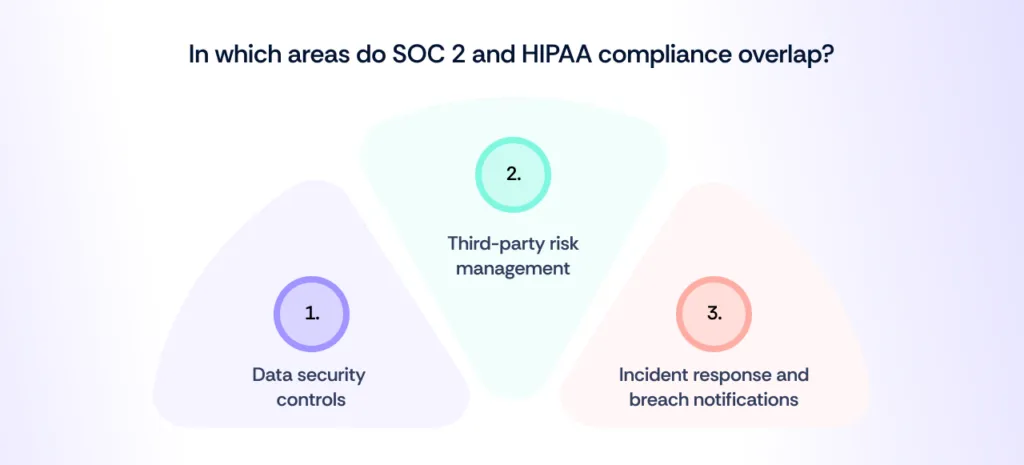
Although SOC 2 and HIPAA serve different industries and have distinct objectives, there are areas where their requirements align. This overlap benefits organizations that must comply with both frameworks, allowing them to streamline security efforts and leverage shared controls. Below are the key areas where SOC 2 and HIPAA intersect:
1. Data security controls
Both SOC 2 and HIPAA require the implementation of robust security measures to protect sensitive data from unauthorized access, breaches, or misuse.
Key common controls include:
- Access controls:
- Both frameworks emphasize the importance of restricting access to sensitive data based on job roles and responsibilities. This includes the use of multi-factor authentication (MFA) and role-based access controls (RBAC).
- Organizations must regularly review and update access privileges to prevent unauthorized access to data or systems.
- Encryption:
- Both SOC 2 and HIPAA require encryption of data at rest and in transit to protect sensitive information, such as customer data or PHI, from interception or unauthorized disclosure.
- SOC 2 organizations focus on encryption to protect customer information, while HIPAA emphasizes encrypting PHI to minimize breach risks.
- Incident management procedures:
- Both frameworks require organizations to develop and maintain incident response plans to detect, respond to, and mitigate the impact of security incidents.
- These procedures must include logging, monitoring, and investigation of potential security breaches to ensure timely identification and resolution.
2. Third-party risk management
Both SOC 2 and HIPAA place significant emphasis on managing third-party risks, as vendors and service providers can introduce vulnerabilities if their security practices are inadequate.
- SOC 2:
- Organizations must evaluate the security posture of third-party vendors and ensure they meet relevant Trust Services Criteria. Vendors with access to sensitive systems or data are expected to comply with contractual obligations that align with SOC 2 requirements.
- HIPAA:
- HIPAA mandates that organizations enter into Business Associate Agreements (BAAs) with all vendors who handle PHI on their behalf. These agreements define the vendor’s obligations to safeguard PHI and outline responsibilities in the event of a breach.
- HIPAA-regulated entities must monitor their business associates and ensure they remain compliant with HIPAA’s privacy and security standards.
- Shared focus:
- Both frameworks require due diligence during vendor onboarding and periodic assessments to ensure third parties maintain adequate security practices. A vendor’s non-compliance can lead to financial and reputational risks for the contracting organization.
3. Incident response and breach notifications
While both SOC 2 and HIPAA emphasize the importance of managing and reporting security incidents, HIPAA outlines more prescriptive legal requirements for breach notification.
- SOC 2:
- SOC 2 encourages organizations to establish incident response plans that include timely communication with clients and partners about potential security issues. Although SOC 2 does not mandate a specific notification timeline, organizations are expected to act transparently and notify stakeholders promptly.
- HIPAA:
- HIPAA’s Breach Notification Rule establishes strict requirements for notifying affected individuals, regulators, and, in some cases, the media, following a PHI breach.
- The notification must occur within 60 days of discovering the breach, with the specifics depending on the number of affected individuals and the nature of the incident. Failure to report breaches within the required timeline can lead to hefty penalties.
- Shared focus:
- Both SOC 2 and HIPAA stress the importance of being proactive in responding to incidents, ensuring that organizations can contain breaches quickly, minimize damage, and restore operations.
- Incident management practices in both frameworks aim to reduce risks and improve future security postures through post-incident analysis and remediation.
Read also: HIPAA vs HITRUST: A practical comparison for making compliance decisions
Do you need both SOC 2 and HIPAA compliance?
Organizations operating in industries where healthcare and technology intersect often find that they need to comply with both SOC 2 and HIPAA. Although maintaining compliance with both frameworks can be resource-intensive, it provides strategic advantages that far outweigh the costs, ensuring both customer trust and regulatory protection.
Are you a hybrid organization?
Many hybrid organizations operate at the crossroads of healthcare and technology, such as:
- Cloud providers or data hosting companies serving hospitals, clinics, or insurers.
- SaaS providers developing software for electronic health records (EHRs) or telehealth platforms.
- Business process outsourcing (BPO) firms managing healthcare claims and billing on behalf of insurers.
These organizations often handle both customer data and PHI, making it essential to comply with SOC 2 and HIPAA to meet clients’ expectations and avoid regulatory penalties.
For such companies, dual compliance ensures they meet the needs of healthcare providers while also positioning themselves to serve customers in non-healthcare industries that prioritize security and operational transparency.
Do you know the strategic value of dual compliance?
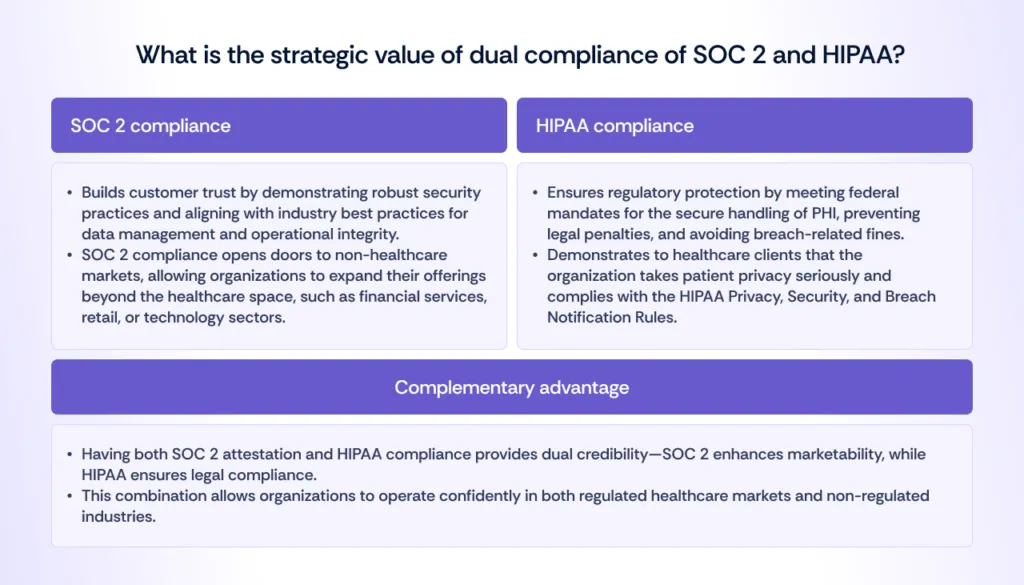
Have to compare the cost vs benefit of dual compliance?
1. Resource-intensive compliance:
Maintaining compliance with both SOC 2 and HIPAA requires significant investment in resources, including time, personnel, and financial costs for audits, risk assessments, and monitoring tools.
For example, organizations must develop policies, procedures, and technical controls that satisfy both frameworks while also conducting vendor risk assessments and incident response planning.
2. Reducing redundancy through overlap:
The overlap between SOC 2 and HIPAA security controls offers opportunities to integrate compliance efforts, reducing redundancy and streamlining processes. For instance:
- Access control measures and encryption standards required by both frameworks can be implemented simultaneously.
- Incident response plans can address both HIPAA’s breach notification requirements and SOC 2’s expectations for incident management.
3. Long-term savings and risk mitigation:
While the initial investment may be high, integrating security efforts across both standards results in long-term cost savings by reducing the need for separate audits and minimizing the risks of data breaches and regulatory fines.
Read also: How to turn SOC 2 compliance into a growth strategy?
How to choose the right compliance path?
Choosing the right compliance path depends on the industry, business model, and type of data your organization handles. While SOC 2 and HIPAA serve distinct purposes, understanding when to pursue one or both is essential for strategic growth and regulatory protection. CEOs must carefully evaluate target markets, client expectations, and operational priorities to determine which path best aligns with their long-term business goals.
1. For healthcare organizations or vendors handling PHI
1. HIPAA compliance is non-negotiable:
Healthcare organizations—such as hospitals, clinics, pharmacies, and insurers—and their business associates must comply with HIPAA to meet federal regulations and avoid significant financial penalties. HIPAA compliance ensures that PHI is properly secured and only disclosed under appropriate circumstances.
2. SOC 2 as an added assurance for clients and partners:
While HIPAA compliance is mandatory, obtaining a SOC 2 report offers additional business value. SOC 2 provides transparency about your organization’s security practices beyond the healthcare-specific scope of HIPAA, reassuring business partners, vendors, and non-healthcare clients about your overall security posture.
Example: A billing service handling PHI for hospitals may pursue both HIPAA compliance and SOC 2 attestation to meet healthcare regulations and simultaneously build trust with non-healthcare business partners.
2. For other SaaS providers and IT services
1. Primary focus on SOC 2:
SaaS companies and IT service providers that do not work exclusively within healthcare should prioritize SOC 2 compliance. SOC 2 provides a broad framework for demonstrating data security and operational reliability, which is critical for building trust with enterprise customers across industries.
SOC 2 attestation signals to partners and clients that your organization follows industry best practices for securing customer data, making it easier to win contracts in highly competitive sectors such as financial services, retail, and technology.
2. Prepare for HIPAA if targeting healthcare clients:
If your SaaS platform or IT service intends to serve healthcare providers, insurers, or other entities that handle PHI, you must be prepared for HIPAA compliance.
Even though SOC 2 is not required by healthcare entities, having HIPAA compliance demonstrates that your organization understands and respects the legal requirements surrounding PHI. Pursuing HIPAA compliance in advance can expand your market potential in the healthcare industry.
Example: A cloud hosting company that provides storage solutions to hospitals or EHR providers may need to ensure both SOC 2 and HIPAA compliance to satisfy regulatory and contractual obligations.

How can you balance resources and business goals?
A streamlined approach can minimize costs and time while ensuring compliance with both frameworks. Following are some of the suggestions that can help you balance resources and business goals.
1. Align compliance with business strategy:
CEOs must ensure that compliance efforts align with their business goals. If your organization aims to expand into multiple sectors (e.g., healthcare and non-healthcare), it is crucial to determine how much focus and investment each compliance framework requires.
2. Efficient resource allocation:
Since compliance efforts are resource-intensive, it is essential to carefully balance time, budget, and personnel. A risk-based approach can help allocate resources based on the criticality of each framework to the business.
For example, if most clients require SOC 2 compliance but a small subset deals with PHI, HIPAA efforts might be scaled down to meet minimum regulatory requirements.
3. Leverage overlap to reduce costs:
Organizations can reduce redundancy by integrating overlapping security controls and compliance efforts between HIPAA vs SOC 2. For instance:
- Implement access control policies that meet the requirements of both frameworks.
- A single incident response plan should be used to satisfy both HIPAA breach notification rules and SOC 2 incident management criteria.
Read also: Streamlining compliance with Scrut Automation
How Scrut can help achieve SOC 2 and HIPAA compliance
Scrut simplifies the path to SOC 2 and HIPAA compliance by automating critical processes, reducing redundancy, and providing continuous monitoring. With an integrated platform, Scrut helps organizations implement shared controls—such as access management, encryption, and incident response—aligning with both SOC 2’s Trust Services Criteria and HIPAA’s regulatory requirements.
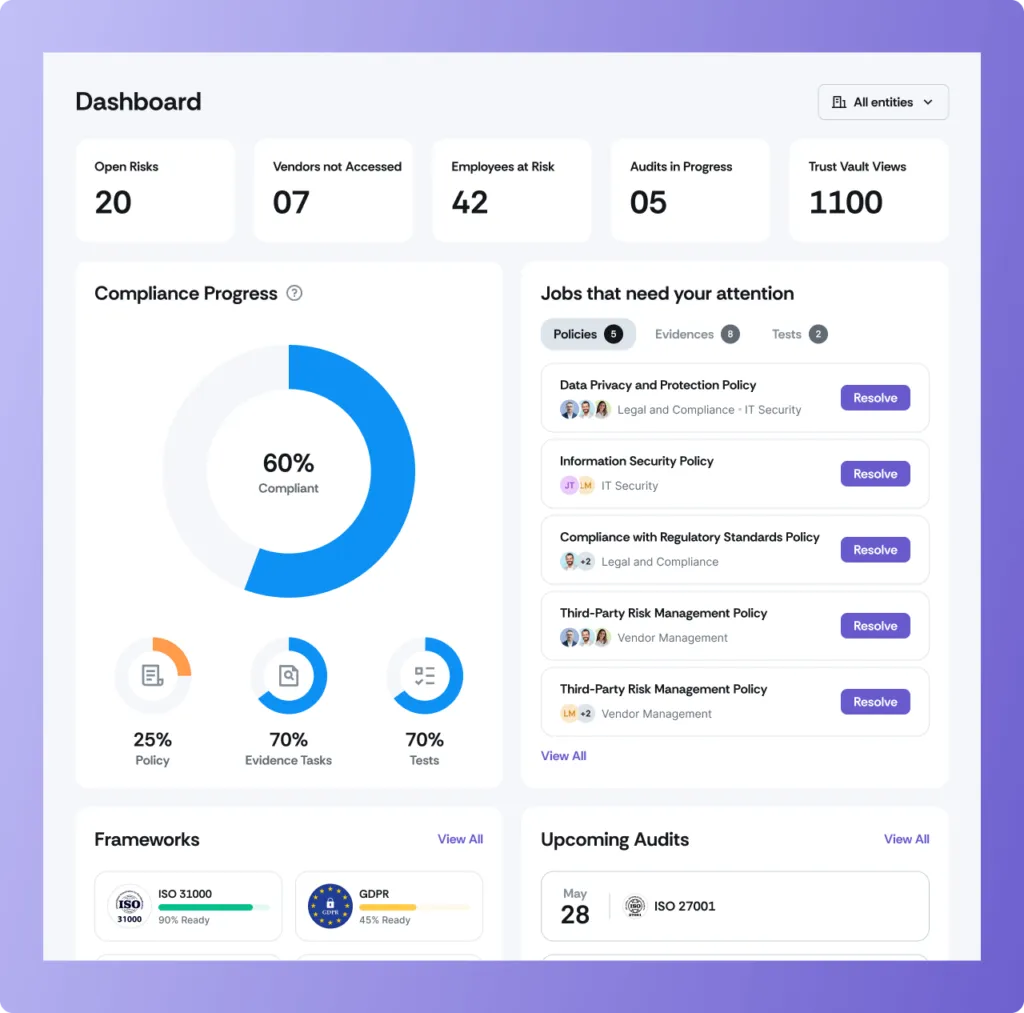
Through real-time dashboards, risk assessments, and automated policy tracking, Scrut ensures organizations stay compliant, avoid audit fatigue, and meet evolving standards. Whether you operate in healthcare, SaaS, or IT services, Scrut streamlines dual compliance, enabling you to focus on business growth while ensuring robust data security and regulatory adherence.
Scrut’s intuitive dashboard provides real-time visibility into your compliance status, tracking progress across both SOC 2 and HIPAA frameworks. It offers actionable insights, automated alerts, and centralized control, ensuring you stay audit-ready and address potential risks proactively.
SOC 2 vs HIPAA: A balancing act
Achieving both SOC 2 and HIPAA compliance offers a powerful blend of trust and legal assurance for organizations that handle sensitive data. By aligning with both frameworks, companies not only meet essential regulatory requirements but also build credibility across various sectors and minimize operational risks.
Dual compliance goes beyond fulfilling obligations—it’s a strategic investment that strengthens client trust, reinforces security practices, and enables expansion into new markets. With the right tools and a proactive approach, your organization can confidently meet these compliance standards, supporting sustainable growth and resilience in today’s competitive environment.

Ready to simplify your SOC 2 and HIPAA compliance journey?
Partner with Scrut to streamline your journey with automation, integrated controls, and continuous monitoring. Stay ahead of risks, reduce redundancy, and focus on scaling—Scrut ensures you meet all regulatory needs.
Get started with Scrut today and turn compliance from a challenge into a strategic advantage!
FAQs
1. What is the difference between confidentiality and privacy in SOC 2?
In SOC 2, confidentiality protects sensitive business information from unauthorized access, while privacy focuses on the proper handling of personal data, ensuring compliance with privacy laws and respecting individuals’ data rights.
2. What does SOC 2 compliance mean?
SOC 2 compliance indicates that an organization has undergone an independent audit to verify that its controls align with the Trust Services Criteria (TSC). It ensures that the company has implemented appropriate processes to safeguard data security, availability, confidentiality, processing integrity, and privacy, building trust with customers and partners.
3. What is the difference between privacy and security in information security?
Privacy in information security focuses on controlling who can access personal data and ensuring it is handled in compliance with regulations and individuals’ rights. It involves policies and practices that govern data collection, storage, and sharing to protect individuals’ privacy.
Security, however, is broader, aiming to protect all types of data—personal and non-personal—from unauthorized access, breaches, and cyber threats. Security encompasses technical measures like encryption, access controls, and monitoring to ensure data confidentiality, integrity, and availability.
In essence, privacy is about managing who can access personal data and how it’s used, while security is about safeguarding all data from external and internal threats.
Table of contents


















