Comparative Analysis of Top 10 Drata Alternatives & Competitors in 2025

Compliance and risk management are overwhelming for businesses, specifically in heavily regulated financial services and healthcare industries. These challenges are amplified in early and growth-stage companies, which are under increasing pressure to manage compliance as the scope and complexity increase. To respond to these challenges, companies adopt automated solutions that enable them to streamline compliance tasks, reduce risks, and simplify audits.
While Drata has established itself as a leading compliance automation platform, SMBs find it less flexible and expensive. Early-stage and growth-stage midsize businesses need affordable, adaptable solutions that offer comprehensive compliance coverage. As a result, many seek Drata alternatives for broader compliance coverage, more customizable workflows, and cost-effective solutions.
This article examines the top 10 Drata alternatives in 2025, highlighting key features and capabilities to help you choose the right solution. Discover which Drata alternative can best meet your compliance and risk management needs.
Drata’s Key Features
Drata automates security compliance by providing continuous control monitoring, automated evidence collection, and workflow optimization. It enables companies to maintain compliance across various frameworks and ensures they are audit-ready.
1. Compliance monitoring
The platform supports compliance with data regulations such as the General Data Protection Regulation (GDPR), the Health Insurance Portability and Accountability Act (HIPAA), and other standards.
2. Risk assessment
The platform continuously evaluates risks and sends notifications, alerts, and reminders for policy violations, control failures, or missing evidence, enabling teams to take swift actions to mitigate risks.
3. Multiple framework support
Drata supports over 20 pre-built compliance frameworks, including SOC 2, ISO 27001, HIPAA, GDPR, and PCI DSS. It also helps organizations create custom frameworks and controls.
4. Integrations
The platform integrates with multiple tools, including cloud services providers, identity management platforms, version control systems, and more.
5. Security
The platform monitors user activities and detects anomalies. It analyzes denied entries and policy enforcement-related data to provide valuable insights for enhancing authentication and security protocol implementation.
Besides, Drata’s real-time reporting dashboard provides an updated view of compliance status.
What is Drata’s pricing model?
Drata offers a tiered subscription-based pricing model for businesses of varying sizes and compliance needs. The differentiating factors in the three pricing models are the number of users, framework access, custom control capabilities, open API availability, risk management functionality, and other factors.
The basic plan, “Essential,” is limited to 50 FTEs, while the “Foundation” and “Advanced” plans include unlimited FTEs. Each plan includes features to meet an organization’s compliance requirements at different stages.
Why consider alternatives to Drata?
If you need a compliance solution that meets your industry needs, auditing support, and affordable pricing, you must consider Drata alternatives, as it may not be the best fit.
If you are an early and growth-stage company, Drata may be expensive and lack the necessary features and customization options to meet your unique requirements. Drata alternatives such as Scrut Automation offer extensive features without extra costs, flexibility to customize the platform, supportive customer service, and more.
Although Drata is a strong compliance platform, you must consider Drata’s alternatives for the following reasons.
- Limited framework options
While Drata provides 20 pre-mapped frameworks, custom frameworks come at an additional cost, and pre-built policy templates are limited to 20. This limitation may hinder organizations with specific or evolving compliance needs. - Auditing support gap
The platform connects users with auditors but leaves them to navigate the audit process independently, unlike platforms which guide customers through every stage of the audit process. - Inflexible risk register
The risk register in Drata is characterized by a cookie-cutter approach, restricting risk scoring to a simplistic “Impact x Likelihood” formula. This inflexibility may not align with organizations seeking a more nuanced and tailored risk assessment process. - Inadequate security-focused cloud controls
Drata monitors over 80 controls, but these are primarily tailored for specific compliance requirements, neglecting a broader range of key controls essential for an organization’s overall security posture. - Basic security training
Drata’s security training offerings lack customization based on campaigns and events. This one-size-fits-all approach may not adequately address the diverse training needs of organizations with varying security requirements. - Unrealistic pricing model
The standard package does not include critical components such as the Trust vault and risk management module, which are locked behind an upgrade plan. Additionally, charges are applied separately for auditors and pen-testers, potentially adding to the overall cost. The high costs of Drata for essential compliance and risk management modules make it unaffordable for small businesses. - Limited customer support
Though Drata offers pre-built policy templates, there is an apparent lack of support for policy reviews, edits, or customizations. This lack of flexibility may impede organizations seeking tailored policy solutions. Some users have voiced concerns over delayed responses to their queries and solutions that did not work.
Top Drata Alternatives You Should Try in 2025
1. Scrut Automation
Scrut Automation provides compliance and risk automation solutions for cloud-native companies. The compliance management platform integrates various frameworks for organizations. It automates evidence collection through seamless integration with multiple third-party platforms and solutions that enterprises commonly use. The company focuses on the compliance needs of mid-market businesses, specifically in regulated industries such as financial services, healthcare, and others.
Scrut enables organizations to comply with industry and security regulations, manage risks, and enhance security posture.
Platform at a Glance
- Unified Governance Risk and Compliance (GRC)
Scrut centralizes risk management, control monitoring, and audits. It offers real-time risk monitoring across infrastructure and applications and ensures compliance with over 50 frameworks.
The platform integrates numerous tools, enabling automatic data collection for evidence gathering. The collaborative workflow enhances teamwork among internal and external stakeholders, while intuitive dashboards provide valuable insights, enabling data-driven decisions. Scrut is ideal for organizations looking to automate compliance and enhance operational efficiency without requiring extensive in-house resources. - Efficient risk and compliance management
An integrated risk assessment, compliance management, and continuous monitoring platform enable organizations to proactively and efficiently manage their security posture. The user-friendly interface and intuitive features allow companies of all sizes to streamline their security processes without requiring extensive resources.
The platform automates routine compliance tasks using AI and machine learning, reducing manual effort and human errors in security audits. - Best-fit solution for regulated industries and SMEs
Scrut is suited for small and medium-sized enterprises looking to enhance their information security programs with limited resources. Companies in highly regulated industries such as healthcare, finance, and SaaS businesses with complex cyber asset footprints that need to comply with multiple standards like ISO 27001, SOC 2, GDPR, and NIST can benefit from the Scrut integrated platform. Enterprises experiencing multiple security audits can leverage Scrut to streamline compliance processes and minimize duplicate efforts.
Features
- Pre-built policy library
The library contains 75+ policies mapped to popular industry frameworks like SOC 2, ISO 27001, and more, which enables enterprises to start their InfoSec program quickly. Organizations can use built-in inline editors to customize these policies to their unique business needs.
- Automated evidence collection
The platform integrates with multiple third-party platforms and solutions that automate evidence collection, reducing manual efforts and improving efficiency.
- Task and workflow management
You can use automated workflows to create, assign, and monitor tasks to control your InfoSec posture firmly. This enables you to enhance collaboration with your internal team members by automatically posting tasks, monitoring them, and sending alerts and notifications.
- Seamless collaboration with auditors
The platform simplifies audits by allowing you to invite auditors to the platform, share artifacts, and monitor status in real time for seamless and efficient audits.
- Customized risk management
Scrut offers an actionable risk register that stands out for its flexibility. You can create custom fields tailored to your organization’s needs and develop risk-scoring formulas. The flexibility ensures a dynamic and tailored risk management approach for your organization.
The platform enables you to integrate preferred messaging services and/or email providers to receive alerts and instant notifications about compliance issues.
Pros
- User-friendly with fast deployment, making it suitable for companies scaling quickly.
- A unified dashboard offers a comprehensive view of compliance with actionable insights.
- 75+ pre-built, customizable policies to set up your compliance program.
- Automates over 80% of the evidence-collection process across your application and infrastructure landscapes.
Cons
- Scrut is a GRC solution designed to integrate with your security stack rather than replace it. Companies expecting an all-in-one, advanced security solution may still need additional tools.
Ratings
Scrut Automation has received positive feedback. Users rated it 4.9 out of 5 at popular review site G2, highlighting its user-friendly interface and responsive customer support.
Pricing
Scrut offers customizable pricing. Contact the team for more information.
Why choose Scrut over Drata?
2. Sprinto
Sprinto is an end-to-end compliance automation, management, and tracking solution for cloud-hosted enterprises. It offers pre-approved, auditor-grade compliance programs supporting frameworks like SOC 2, ISO 27001, GDPR, HIPAA, NIST, and more.
Features
- Adaptive automation capabilities go beyond task outlining, consistently organizing, nudging, and capturing corrective actions against each task in an audit-friendly manner.
- Allows the assignment of tasks in tiers, organized according to compliance priorities.
- Offers pre-built, auditor-friendly compliance programs with the auditor customizable dashboard enabling users to collect, edit, and view evidence.
- Compliance and audit experts collaborate with you from the beginning to ensure the implementation of the proper controls and practices for your business.
Pros
- Handles policy documentation, vendor risk assessment, SOA, and other compliance requirements comprehensively.
- Provides a real-time overview of control statuses, highlighting areas of compliance and potential gaps.
Cons
- Response time to queries can be delayed at times.
- Expensive, especially when pursuing multiple compliance certifications.
- A lack of assessment criteria to evaluate employees’ security training is noted.
Ratings
Sprinto has received a 4.8 out of 5 on G2 for its user-friendly platform that simplifies compliance processes through seamless integrations and intuitive interfaces.
Pricing
Sprinto’s price ranges between $4,000 for one framework (10 – 50 employees). Each additional framework adds another $1,000 extra.
3. Vanta
Vanta is a robust security and compliance automation platform, empowering businesses to streamline security procedures and automate compliance with industry-leading standards, including SOC 2, ISO 27001, PCI DSS, GDPR, HIPAA, and CCPA.
Features
- Excels in automating up to 90% of the effort required for security audits, eliminating the hassles of time-consuming manual security checks.
- Continuous monitoring ensures that your organization remains safe and compliant around the clock.
- Facilitates the active sharing of Trust Reports with customers and prospects, bolstering confidence in your company and showcasing your commitment to security.
Pros
- Controls, dashboards, and alarms prove highly useful in keeping users attentive and preventing a surge in workload as an audit approaches.
- Offers excellent integration capabilities with tools such as Rippling, Addigy, AlexisHR and others.
- Simplifies the process of gathering and organizing required information in one centralized location.
Cons
- Lacks support for essential integrations.
- Tracking requirements like encryption frequently encounter issues on Linux machines.
Pricing
Vanta offers three plans suitable for early-stage, growth-stage and mature companies. You must contact the company to get pricing details for each plan.
4. Hyperproof
Hyperproof’s GRC solution injects efficiency into your compliance and risk management processes. The platform organizes, automates, and unifies your risk management and compliance activities.
It is an all-in-one solution, providing clarity on compliance requirements, managing internal controls, defining optimal compliance processes, automating manual tasks, and continuously monitoring compliance posture.
Features
- Risk management module facilitates the documentation, assessment, and management of all risks.
- Consolidates program requirements, internal controls, and proof in a single, accessible location.
- Integration capability spans various services, ranging from cloud storage to project management, communications, cloud infrastructure, devops, security, and business applications.
Pros
- Offers a seamless workflow for linking controls to numerous frameworks.
- Exceptionally straightforward to set up and use.
Cons
- With Hyperproof, maintaining a seamless continuous monitoring posture can be challenging.
Pricing
Hyperproof has 3 pricing editions. You need to contact the company for details.
5. Thoropass
Thoropass, formerly Laika, is a compliance and audit platform combining compliance automation with a tech-enabled audit firm. It enables businesses to implement, monitor, and manage compliance, accelerate audits, and reduce risks. It facilitates continuous monitoring to maintain compliance with InfoSec and privacy frameworks.
Features
- Offers continuous oversight of compliance status, alerting users to potential issues as they arise, ensuring proactive management.
- Streamlines compliance by automatically gathering necessary documentation from integrated systems, reducing manual effort.
- Risk Register provides a comprehensive view of an organization’s risk landscape for efficiently tracking, evaluating, and remediating risk.
Pros
- Offers a holistic approach to compliance, integrating various tools and features to effectively manage risk assessments, policy management, and audit preparations.
- Supportive customer service team actively engages with customers to answer compliance questions and review evidence, enabling them to implement the solution easily.
- Users find Thoropass intuitive and user-friendly, simplifying the complex process of maintaining compliance.
Cons
- Integration options are limited, which makes it challenging for organizations with niche integration requirements.
- Pre-built templates can be overwhelming for small businesses.
- Some users have reported a lack of clarity in certain platform aspects, leading to confusion during the compliance process.
Pricing
The company offers custom prices based on organization compliance requirements.
6. OneTrust
OneTrust is a comprehensive GRC platform that provides enterprises with an integrated risk solution, including IT and security risk management, vendor risk management, incident and breach documentation, audit management, and more.
OneTrust acquired Tugboat Logic in 2021 to enhance its risk and compliance capabilities, particularly in automating information security assurance and audit readiness. This acquisition helps organizations manage security and compliance across various frameworks, such as ISO 27001, SOC 2, CMMC, HIPAA, and PCI DSS, thereby complementing OneTrust’s existing data privacy management functionalities for regulations like GDPR and CCPA.
Features
- Automates privacy impact assessments, aiding in identifying and mitigating risks associated with data processing activities.
- Boasts a pre-built policy library featuring over 40 policies, aiding users in rapidly developing credible InfoSec policies.
- Enhances vendor management by enabling assessment and rating of vendors, including the capability to review fourth and fifth parties extensively.
Pros
- Users can leverage machine learning-suggested responses to repurpose previously answered queries.
- Provides outlined actions necessary to achieve compliance with frameworks such as SOC 2, GDPR, ISO 27001, etc.
- Facilitates assessment automation (PIA, DPIA) and data mapping.
- Streamlines the auditing process, simplifying collaboration with auditors.
Cons
- Custom pricing can be expensive, especially for smaller companies.
- Reporting features are not comprehensive, and lack of customization limits the data that can be displayed.
- Requires significant manual effort to unlink related rules and procedures, leading to duplication and mapping challenges.
Pricing
The company offers customized pricing; you need to contact them to get the details.
7. Secureframe
Secureframe stands out as a robust platform, providing seamless support for maintaining security, privacy, and compliance. This powerful solution offers automated compliance and security features tailored to the needs of growing businesses.
Moreover, with Secureframe, organizations can achieve audit readiness within weeks, streamlining the compliance process.
Features
- Leverage automatic reporting and notifications to maintain compliance effortlessly.
- Foster collaboration with in-house subject matter experts (SMEs) to ensure the Secureframe knowledge base remains consistently up-to-date.
- Benefit from support provided by compliance experts and former auditors.
Pros
- Offers AI-powered text revisions, version controls, and automated framework updates among other features in its policy building.
- Secureframe provides a guided flow for executing standards such as SOC 2, HIPAA, PCI DSS, ISO 27001, simplifying the initial setup process and aiding auditors.
Cons
- Bugs are occasionally encountered during information syncing, requiring manual data entry.
- The tool may generate errors with limited information on resolution steps, lacking specificity in identifying affected components.
Pricing
Secureframe offers two pricing packages, Fundamentals and Complete, each with a defined set of features and prices.
8. Scytale
Scytale helps SaaS companies adhere to security frameworks such as SOC 2, ISO 27001, HIPAA, GDPR, and PCI-DSS. It provides automated evidence collection, continuous monitoring, and centralized task management to streamline audit readiness. Additionally, the platform offers personalized guidance from compliance experts to assist with compliance implementation and audit.
Features
- Real-time monitoring of compliance controls, promptly alerting users to any deviations or issues.
- Supports multiple compliance frameworks, including SOC 2, ISO 27001, HIPAA, GDPR, and PCI DSS, enabling organizations to manage various compliance requirements from a single platform.
- Automates compliance evidence collection, reducing manual effort and ensuring accuracy.
Pros
- Personalized guidance from Scytale’s compliance experts is highly valued.
- Pre-built policy templates enable organizations to establish a strong compliance foundation swiftly.
- Integration with numerous third-party tools and applications facilitates automated evidence collection and streamlines compliance workflow.
Cons
- The platform is frequently updated, requiring users to adapt quickly to new features and workflows.
- Limitations in manipulating evidence within the platform could be a concern for certain compliance audits.
Pricing
Scytale offers three pricing packages, and you need to contact companies for details.
9. AuditBoard
AuditBoard emerges as a connected risk platform, seamlessly unifying standards such as SOC 2, ISO 27001, NIST, CMMC, PCI DSS, and more across organizations. This platform empowers users to forge connections between people, risks, and insights, aligning with contemporary expectations and fortifying organizational resilience.
Features
- Connected risk platform provides real-time visibility into emerging issues, risk trends, and critical indicators, enabling users to stay ahead in today’s dynamic risk environment.
- Designed to automate procedures and enhance execution, fostering a collaborative approach to evidence gathering, control certification, risk assessments, and other tasks that unite teams and stakeholders.
- Enhance job efficiency and deliver more strategic value across all auditing processes.
Pros
- Minimal training is required for auditors and process owners to utilize the platform effectively.
- User-customizable project management dashboards simplify updates for leaders and help users stay on track.
- The platform’s features expedite the documentation process while improving the quality of audit work papers.
- Establishing and managing projects is straightforward for control owners.
Cons
- Administrators may encounter initial challenges when starting with new controls, users, etc.
- Tracking audit plan progress separately in spreadsheets is a notable drawback.
Pricing
The company offers custom prices; you need to contact them for details.
10. Anecdotes
Anecdotes offer a data-driven compliance platform to manage compliance frameworks, policies, risks, and user access reviews and monitoring. The platform features proprietary integrations, continuous monitoring, and a Trust Center for sharing compliance and security information with stakeholders.
Its customized controls and frameworks enable companies to meet internal and external audits seamlessly and have visibility, flexibility, and intelligence to scale their compliance programs as they grow.
Features
- Anecdotes’s GRC applications leverage data extensively to manage compliance frameworks, policies, risks, and user access reviews and monitoring.
- Continuous monitoring of compliance data ensures real-time visibility into compliance status and facilitates proactive management of potential issues.
- Trust Center allows companies to share compliance and security information with stakeholders, streamlining the security review process and accelerating the sales cycle.
Pros
- A navigable, user-friendly interface simplifies the setup of control frameworks, policy writing, risk assessments, and evidence collection.
- Pre-built frameworks and templates for various compliance standards, such as SOC 2 and ISO, provide a structured approach to compliance management risk assessments.
- Extensive integrations serve as the building blocks for control requirements that can then be easily mapped to applicable frameworks such as SOC 2, HIPAA, PCI, ISO27001, etc.
Cons
- The platform lacks certain compliance features and integration options.
- Limited customization options and the platform lacks complete automation, requiring manual efforts for some tasks.
- Anecdotes does not have security awareness training built into its platform.
Pricing
The company offers customized pricing.
How Scrut stands out among Drata alternatives?
Scrut Automation distinguishes itself from Drata and other compliance automation platforms through several key factors:
Affordable pricing
Scrut offers a pricing model that includes all platform modules, auditors, and pen-testers. Businesses can use multiple frameworks (SOC 2, ISO 27001, HIPAA, GDPR, etc.) without worrying about add-on charges or inflating the cost.
Businesses get access to Scrut’s in-house compliance experts and a broad network of auditors and pen-testers at pre-negotiated rates and guaranteed SLAs, providing a high return on investment (ROI).
Extensive integration capabilities
Scrut integrates with multiple platforms, including but not limited to:
- Cloud Services – AWS, GCP, Azure
- Identity & Access Management – Okta, Google Workspace, Azure AD
- MDM Solutions – Kandji, Jamf, Intune
- Project Management – Jira, ClickUp, Asana
- Version Control – GitHub, GitLab, Bitbucket
The extensive integration ecosystem makes Scrut more than any Drata alternatives, ensuring seamless compliance automation.
Customizable workflows
Scrut allows businesses to tailor compliance workflows, generate custom reports, and automate evidence collection. Its control framework eliminates redundant efforts within controls and streamlines compliance processes.
Automation reduces manual efforts more than its competitors
Automated evidence gathering across multiple integrations reduces manual efforts by 80%, a policy builder with 50+ pre-built templates and built-in workflows, improves productivity and cost efficiency.
Robust risk and security posture
Scrut provides continuous cloud monitoring across 200+ controls covering Centre for Internet Security(CIS) benchmarks mapped to industry-leading frameworks. It also offers in-built security training and a dynamic risk register. Scrut offers real-time compliance tracking with automated alerts on control deviations. It helps businesses proactively fix security gaps before audits, reducing last-minute compliance workloads.
4 steps to choose the right Drata alternative for your business
You must diligently follow a systematic approach to select the Drata alternative that best fits your business and technical requirements. Some key evaluation criteria for choosing the right Drata alternative are as follows.
Define your compliance and security needs
You must assess your compliance needs by identifying the frameworks (SOC 2, ISO 27001, HIPAA, etc.) you must comply with and the controls you need to establish. You must also determine whether you require continuous monitoring, automated evidence collection, auditor access, and other requirements.
After identifying your compliance requirements, you can refer to benchmark budgets to finalize the price range for purchasing the right Drata alternative for your organization.
Establish evaluation criteria
Create an evaluation framework classifying criteria and sub-criteria and assigning weights based on their relevance. The evaluation criteria should include both quantitative and qualitative criteria.
Identify and assess options
Create a long list of vendors based on their rankings in popular review platforms and inclusion in analyst research reports by Forrester and Gartner.
Make an informed decision
Evaluate each vendor using the evaluation framework to identify the top three vendors that meet most of your requirements. Schedule a demo and use product trials to choose the best-fit option.
Still not sure? Explore Scrut for streamlined compliance
Choosing the right compliance automation platform is critical for ensuring security, regulatory adherence, and operational efficiency. With so many options available, the decision can feel overwhelming. While Drata may have been on your radar, its high cost, limited features, and lack of flexibility might make it a less-than-ideal fit for your needs.
Compliance automation platforms all have similar capabilities, but it is not one size fits all. If you are an early or growth-stage company, you may find some of Drata’s alternatives overwhelming and complicated, as they have been designed for large enterprises. Others may lack features and functionalities to meet your industry-specific requirements.
Scrut Automation stands out among Drata alternatives as the best compliance automation solution for businesses seeking a cost-effective, scalable, and feature-rich compliance solution. With transparent single pricing, continuous control monitoring, built-in risk and vendor management, and, Scrut provides a comprehensive approach to compliance without hidden costs. The dedicated compliance experts ensure a smooth audit process, making compliance management easier and more efficient.
Scrut offers end-to-end compliance automation, risk management, and customizable workflows. Schedule a demo to learn more.
FAQs
Which is better: Drata or Sprinto?
Drata and Sprinto are compliance automation platforms that help businesses comply with standards like SOC 2, ISO 27001, HIPAA, and more and enable them to manage risks effectively. Drata is considered a better fit for large enterprises with complex compliance requirements and more significant automation capabilities requirements.
Sprinto offers advanced automation, extensive integrations, and real-time compliance insights, which are ideal for rapidly growing companies seeking comprehensive compliance management capabilities. Drata is better suited for businesses that don’t require active support through their compliance processes, while Sprinto can be helpful for companies that need assistance throughout their journey.
What is the best Drata alternative for SMBs or mid-market companies?
Scrut Automation is the best Drata alternative for SMBs and mid-market companies. It offers comprehensive compliance management features like continuous monitoring, risk assessment, and automated evidence collection.
Scut’s single-point pricing, including all modules, is affordable for price-conscious and value-driven SMBs and mid-market companies. In contrast, the Drata basic plan includes only limited features, excluding the essential compliance and risk management modules.
For example, vulnerability assessment and penetration testing are crucial to compliance and are included in Scrut’s basic pricing plan. In Drata, you have to pay an additional fee and go through the tedious exercise of finding a trusted partner and negotiating rates, making the platform expensive for SMBs and mid-market companies.
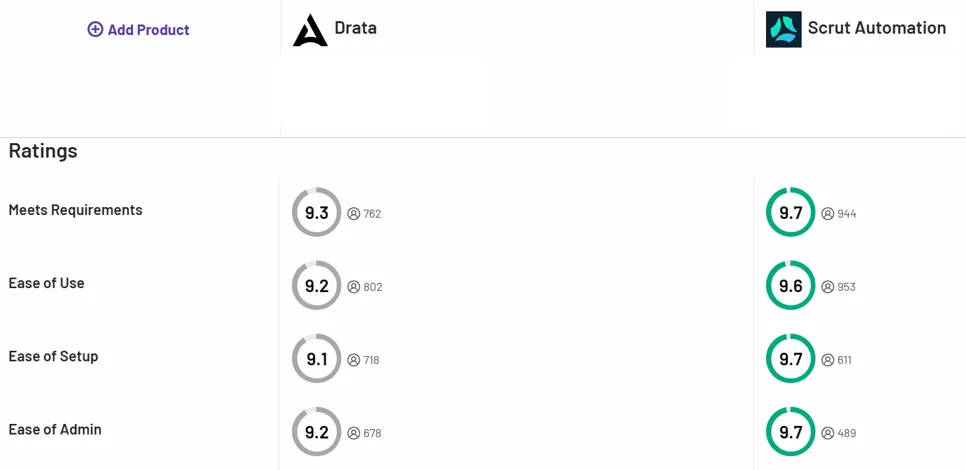
Users have also assigned Scrut higher ratings than Drata across various features. Scrut is highly valued for its ease of setup scoring 9.7 over Drata’s 9.1.
Which Drata alternative offers the best integration capabilities?
Scrut offers extensive integration with multiple platforms and solution providers, including cloud services, identity access management (IAM), single sign-on (SSO), human resource tools, and more.
Similarly, Sprinto offers over 200 native and deep integrations that connect the platform seamlessly with cloud applications and services.
What is the pricing of Drata?
Drata offers tiered pricing plans to meet the compliance needs of businesses of various sizes.
- Essential Plan: This plan includes up to 50 full-time employees (FTEs), one pre-mapped framework, pre-built integrations, a trust center, vendor management, and additional features.
- Foundation Plan: This plan is suitable for growth-stage companies and includes platform access to unlimited FTEs, all features included in the essential plan, and additional capabilities like custom controls, open API, and user access reviews.
- Advanced Plan: The plan is aimed at large enterprises with mature compliance programs and includes all features of the foundation plan and some additional features.


















