Choose risk-first compliance that’s always on, built for you.
Go back to blogs
How to distinguish between SCRM, TPRM, and VRM
Last updated on
August 10, 2023
11
min. read
As organizations scale and grow, their dependency on external vendors to fulfill certain tasks increases. Though this boosts efficiency and productivity, it also opens doors to security risks posed by their vendors.
This has resulted in vendor risk management being indispensable for organizations that engage multiple vendors.
Vendor risk management (VRM) is often confused with Third-Party Risk Management (TPRM) and Supply Chain Risk Management (SCRM).
Though VRM, TRPM, and SCRM have the same ultimate goal—protecting the data of an organization—they have some key differences.
In this blog, we will shed light on all three terms and explore their differences by understanding how they approach external risks and what their objectives are.
Common terms associated with VRM
Before we dive into the differences between VRM, TRPM, and SCRM, let’s take a look at some terms that help understand the inner and outer circles of an organization.
First party
The term first party refers to your organization and all its systems and resources.
Second party
The second party is formed by your customers and their information systems.
Third party
The third party comprises people, organizations, and information systems that have access to your company’s data, excluding the first party and second party. These include the vendors that your organization uses.
Fourth party
Fourth parties or n-parties refers to people, organizations, and information systems that do not have access to your data and are indirectly associated with your organization through the third parties it associates with. In other words, they are the third-party associates of your third-party associates.
What is VRM?
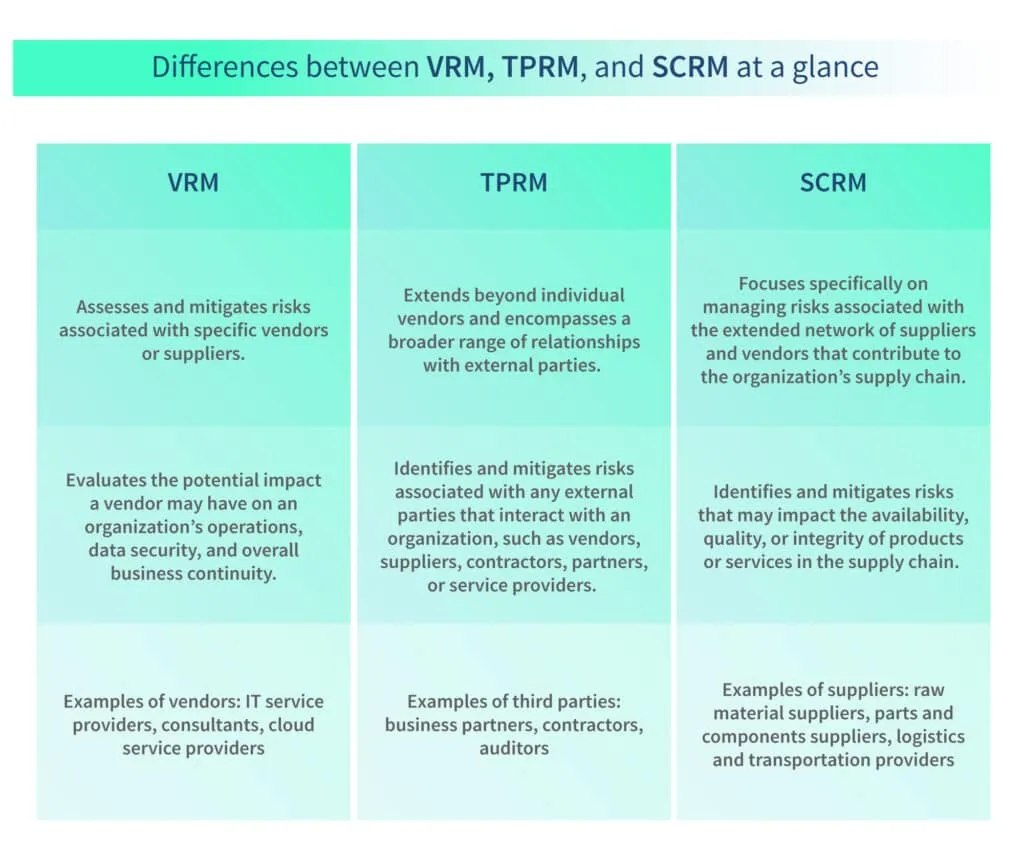
Vendor Risk Management focuses on assessing and mitigating risks associated with specific vendors or suppliers. It involves evaluating the potential impact a vendor may have on an organization’s operations, data security, and overall business continuity.
Types of Vendors
Here are some types of vendors that organizations commonly hire:
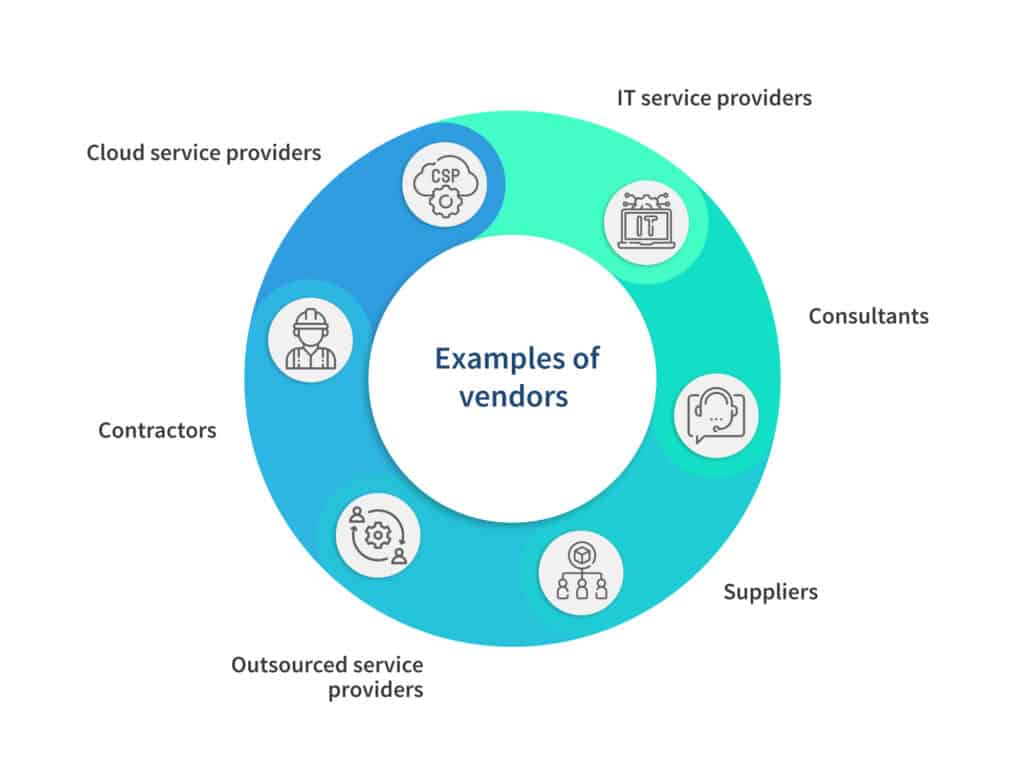
1. IT service providers
These providers offer services such as software development, network infrastructure management, cloud computing, cybersecurity, data storage, and technical support.
2. Consultants
Organizations hire management consulting firms, financial consultants, legal consultants, or subject matter experts to provide specialized services and advice.
3. Suppliers
Suppliers encompass manufacturers, wholesalers, retailers, and distributors that provide raw materials, components, equipment, or finished goods used by an organization for its operations.
4. Outsourced service providers
Organizations often outsource certain functions or processes to specialized vendors, such as customer support, marketing, or accounting services, to improve efficiency.
5. Contractors
Organizations hire contractors to fulfill specific requirements that they may not have the time or expertise to handle, such as construction companies or maintenance services.
6. Cloud service providers
Vendors offering cloud-based services like Infrastructure as a Service (IaaS), Platform as a Service (PaaS), and Software as a Service (SaaS) are commonly hired by organizations to enhance their business operations.
What does VRM entail?
VRM is a comprehensive process that effectively manages an organization’s relationships with its vendors. Here are some of its key processes:
1. Vendor assessment
Organizations assess potential vendors based on various criteria such as financial stability, reputation, track record, compliance with regulations, and adherence to industry standards.
This assessment helps determine the suitability of vendors and their alignment with the organization’s values and requirements.
2. Risk identification
VRM identifies and assesses potential vendor risks. Data breaches, service disruptions, compliance violations, or any other risks that may arise from the vendor’s operations or relationship with the organization are what it watches out for.
3. Due diligence
This step involves conducting thorough due diligence on selected vendors. It includes background checks, reviewing vendor contracts, and evaluating security controls and practices.
The organization should ensure that vendors meet the necessary risk and security requirements and can provide the expected level of service and protection.
Assessing the vendors’ SOC 2 reports can help in evaluating the risks they pose.
4. Ongoing monitoring
VRM is not a one-time activity. It requires continuous monitoring of vendor performance.
This monitoring helps identify any changes in vendor risk levels, performance issues, or emerging concerns that need to be addressed. Using vendor risk management software helps in this pursuit.
What is TPRM?
All vendors are third parties, but all third parties are not vendors. Third-Party Risk Management extends beyond individual vendors and encompasses a broader range of relationships with external entities.
Apart from dealing with paid vendors, third-party risk management also manages risks posed by unpaid parties such as development partners and open-source software providers. It is harder to exert control over them since they are not paid for their services.
Types of Third Parties
Here is a list of third parties that an organization commonly engages with:
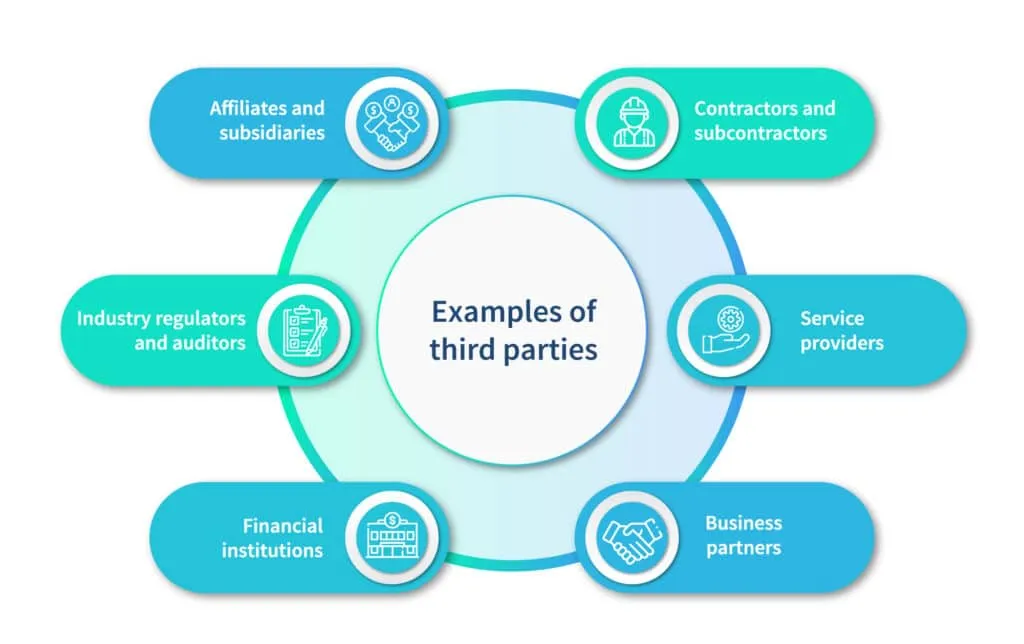
1. Contractors and subcontractors
These third parties may include construction companies, consultants, or freelancers hired for temporary or specialized work.
2. Service providers
They provide outsourced services to support an organization’s operations. This can include IT-managed service providers, cloud service providers, marketing agencies, or legal firms.
3. Business partners
Business partners are parties with whom an organization has established a strategic alliance or partnership. Joint ventures, co-marketing agreements, or collaborations to develop and deliver products or services are examples of such alliances.
4. Affiliates and subsidiaries
Affiliates and subsidiaries are separate legal entities that are related to the organization through ownership or control. They may share resources or have common goals but are still considered third parties for risk management purposes.
5. Industry regulators and auditors
Regulatory bodies, government agencies, and auditors interact with organizations to ensure compliance with industry regulations, standards, or specific legal requirements. They play a role in evaluating an organization’s practices.
6. Data processors
In the context of data privacy and protection, organizations often engage third-party data processors to handle and process personal or sensitive data on their behalf. This can include cloud storage providers, payroll processors, or customer support service providers.
7. Financial institutions
Organizations may have relationships with banks, payment processors, or other financial institutions to manage banking services, handle transactions, or provide financing options.
8. Research and development partners
In research-driven industries, organizations may collaborate with external research institutions, universities, or specialized R&D firms to develop new products, technologies, or intellectual property.
9. Logistics and transportation providers
Third-party logistics (3PL) companies or transportation providers are often engaged to handle the shipping of goods and supply chain logistics.
10. Professional associations and industry groups
Organizations may participate in professional associations or industry groups to gain access to resources, networking opportunities, and shared knowledge within their respective sectors.
What does TPRM entail?
TPRM involves several critical aspects that are vital for mitigating potential risks associated with third parties and ensuring the security of the organization’s operations. Here are the key processes involved in TPRM:
1. Risk assessment
Organizations should perform a comprehensive risk assessment of their third parties to identify and evaluate the potential risks associated with them.
This assessment involves categorizing them based on criticality and assessing the potential impact on the organization’s operations if a security incident were to occur.
2. Due diligence
Thorough due diligence should be conducted on all third parties under consideration. This process involves evaluating their financial stability, compliance with regulations, adherence to industry standards, security controls, and their past performance in relevant areas.
The objective is to gain a clear understanding of the third party’s capabilities, reputation, and potential risk factors.
3. Contractual agreements
Organizations should establish contractual agreements that clearly outline the expectations, responsibilities, and security requirements of third parties.
These agreements must include clauses addressing data protection, confidentiality, liability, compliance, and security controls.
By establishing such agreements, organizations can set clear expectations and ensure that third parties meet the required standards.
4. Ongoing monitoring
Third party vendor risk management calls for the continuous monitoring of third-party performance and security posture. Organizations should establish mechanisms to regularly assess and monitor the activities and security practices of third parties.
This includes conducting audits, periodic reviews, and performance evaluations. Any identified risks or issues should be promptly addressed to mitigate potential impacts on the organization’s operations.
What is SCRM?
Supply chain risk management focuses on managing risks associated with the extended network of suppliers and vendors that contribute to an organization’s supply chain. It involves identifying and mitigating risks that may impact the availability, quality, or integrity of products or services.
Examples of Suppliers
There are numerous suppliers and vendors that contribute to an organization’s supply chain. The specific suppliers and vendors can vary depending on the industry and the organization’s needs.
However, here are some common examples:
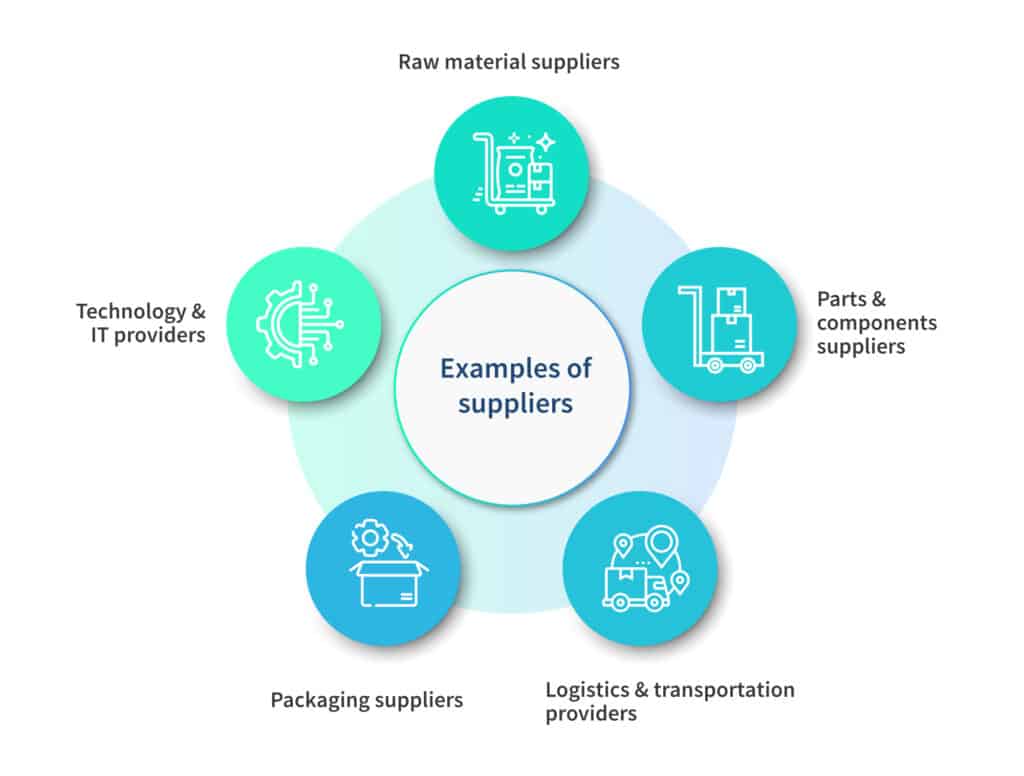
1. Raw material suppliers
These suppliers provide the necessary raw materials or components that are used in the manufacturing or production process. For instance, in the automotive industry, suppliers may provide steel, rubber, glass, or electronic components.
2. Parts and components suppliers
These suppliers specialize in providing specific parts or components required to assemble finished products. They may supply items like circuit boards, engines, fasteners, or specialized components for various industries.
3. Logistics and transportation providers
These vendors offer transportation services to move goods from suppliers to the organization’s facilities or between different locations within the supply chain. This can include freight companies, shipping companies, airlines, or trucking companies.
4. Packaging suppliers
These vendors provide packaging materials and solutions to protect and present products during transportation and storage.
5. Technology and IT providers
These suppliers offer technology solutions to support supply chain management and operations. They may provide software systems for inventory management, order processing, or enterprise resource planning (ERP) solutions.
6. Equipment and machinery suppliers
These vendors provide the necessary equipment and machinery for manufacturing or production processes. They can include suppliers of machines, tools, automation equipment, or specialized equipment required for specific industries.
7. Maintenance and repair service providers
These vendors offer services to maintain and repair equipment or machinery used within the supply chain. They may provide on-site technicians, spare parts, or maintenance contracts to ensure smooth operations.
8. Utilities and energy suppliers
These vendors provide essential utilities such as electricity, water, or gas to power the organization’s operations. They ensure the availability of necessary resources for production and distribution.
What does SCRM entail?
Implementing SCRM practices helps organizations to effectively identify, assess, and mitigate risks within their supply chains, thereby enhancing resilience and ensuring smooth operations even in the face of potential disruptions.
Here are some common processes associated with SCRM:
1. Supply chain mapping
SCRM begins with mapping out the entire supply chain to gain a holistic understanding of its structure. This includes identifying all the tiers, suppliers, subcontractors, and other dependencies within the supply chain network.
By visualizing the complete chain, organizations can better comprehend how each element connects and influences the overall supply chain’s functionality.
2. Understanding dependencies and vulnerabilities
With the supply chain mapped out, the next step is to analyze the various tiers and dependencies. This involves assessing the critical components, suppliers, and activities that are essential for smooth operations.
By understanding these dependencies, organizations can identify potential vulnerabilities and points of failure within the supply chain. This knowledge is crucial for proactive risk management.
3. Risk assessment
SCRM involves a comprehensive risk assessment process that evaluates risks associated with suppliers. This assessment covers various aspects, including geopolitical factors, natural disasters, transportation disruptions, and supplier financial instability.
By conducting a thorough risk assessment, organizations can identify potential threats that may impact the supply chain and take proactive measures to mitigate them.
4. Contingency planning
To ensure business continuity, organizations must develop robust contingency plans. These plans are designed to address potential disruptions in the supply chain, considering the identified risks and vulnerabilities.
Contingency planning involves creating alternative strategies, backup suppliers, redundancy plans, or inventory management techniques that can be implemented in the event of a supply chain disruption.
It aims to minimize the impact of disruptions and maintain the flow of goods and services.
5. Collaboration
SCRM emphasizes the importance of collaboration with suppliers and partners within the supply chain. By working closely with suppliers, organizations can establish shared risk management strategies.
This collaboration involves open communication channels, frequent information sharing, and joint efforts to enhance supply chain resilience.
By fostering strong relationships with suppliers, organizations can collectively address risks and proactively adapt to changing circumstances.
Conclusion
Vendor Risk Management (VRM), Third-Party Risk Management (TPRM), and Supply Chain Risk Management (SCRM) are distinct approaches that organizations employ to manage different aspects of risks associated with external relationships.
While VRM focuses on assessing and mitigating risks associated with individual vendors, TPRM manages risks posed by a broader range of third-party relationships. SCRM, on the other hand, focuses specifically on managing risks within the extended supply chain.
Understanding these differences allows organizations to adopt targeted risk management strategies and ensure the security, continuity, and resilience of their operations in an interconnected business environment.
Using a tool like Scrut will help manage all associated risks with vendors, service providers, and suppliers. Schedule a demo today to learn more.
FAQs
What is vendor risk management?
Vendor risk management is the process of assessing and managing the risks associated with working with third-party vendors, suppliers, or service providers.
What is third-party risk management?
Third-party risk management encompasses the management of risks associated with all external parties, including vendors, suppliers, contractors, service providers, consultants, or any other external entities that have access to an organization’s systems, data, or resources.
What is supply chain risk management?
Supply chain risk management involves identifying, assessing, and managing the risks within a complex network of suppliers, vendors, manufacturers, distributors, and logistics providers that make up an organization’s supply chain.
Table of contents


















