In the ever-expanding digital arena, cybersecurity architecture—the strategic design and implementation of security measures addressing vulnerabilities at the system level—emerges as a critical framework for securing sensitive data and fortifying digital systems against a myriad of threats.
As technology advances, so do the capabilities of cyber adversaries. The digital era has brought about a surge in sophisticated cyber threats, including malware, ransomware, and advanced persistent threats (APTs).
These threats pose a serious risk to the confidentiality, integrity, and availability of sensitive information. A breach in one system can have cascading effects, affecting the targeted organization, interconnected entities, and users.
Cybersecurity architecture provides a proactive defense against escalating cyber threats. It can help organizations identify and mitigate potential risks before they manifest.
Cybersecurity architecture vs. traditional cybersecurity approach
To appreciate the value of cybersecurity architecture, it’s essential to recognize its distinctions from traditional cybersecurity approaches.
Why is cybersecurity architecture important?
Cybersecurity architecture is critically important in the contemporary digital arena due to the ever-growing sophistication and diversity of cyber threats. It serves as the bedrock for safeguarding sensitive information, crucial business operations, and the overall integrity of digital ecosystems.
By adopting a comprehensive and strategic approach, cybersecurity architecture transcends traditional, reactive measures and proactively fortifies organizations against an array of threats. It not only defends against known vulnerabilities but also anticipates and adapts to emerging risks, ensuring a resilient defense posture.
Moreover, in an era marked by the continuous evolution of cyber threats, a well-designed cybersecurity architecture is essential for maintaining business continuity, protecting critical assets, and preserving stakeholder trust. It aligns security measures with the overarching goals of the organization, thereby becoming an integral component of effective risk management.
Beyond its defensive role, cybersecurity architecture is crucial for compliance with regulatory standards and industry-specific requirements. Many sectors face stringent regulations regarding data protection and information security.
A robust cybersecurity architecture provides the necessary framework to implement and adhere to these standards, mitigating legal and financial risks associated with non-compliance.
Additionally, as organizations increasingly embrace digital transformation, cybersecurity architecture becomes instrumental in facilitating innovation by ensuring that security measures are seamlessly integrated into new technologies and processes.
A robust cybersecurity architecture is not merely a security measure but a strategic imperative.
Cybersecurity dynamics: Mesh, reference, diagram insights
The evolving landscape of cybersecurity is witnessing the emergence of innovative frameworks, with cybersecurity mesh architecture and cybersecurity reference architecture playing pivotal roles.
Cybersecurity mesh architecture represents a dynamic approach that extends security controls beyond traditional perimeters, allowing for a more flexible and distributed defense strategy. It emphasizes the protection of individuals and devices regardless of their location, reflecting the modern reality of decentralized work environments.
Complementing this, a cybersecurity reference architecture provides a standardized and comprehensive blueprint for designing robust security measures. It serves as a guide for organizations to structure their security frameworks, aligning them with industry best practices and regulatory standards.
Visualizing the intricacies of these architectures is made tangible through a cybersecurity architecture diagram, a graphical representation that maps out the various components, connections, and interactions within a cybersecurity framework.
Such diagrams facilitate a holistic understanding, aiding organizations in the implementation of effective security measures and ensuring a resilient defense against a myriad of cyber threats.
Key components of cybersecurity architecture
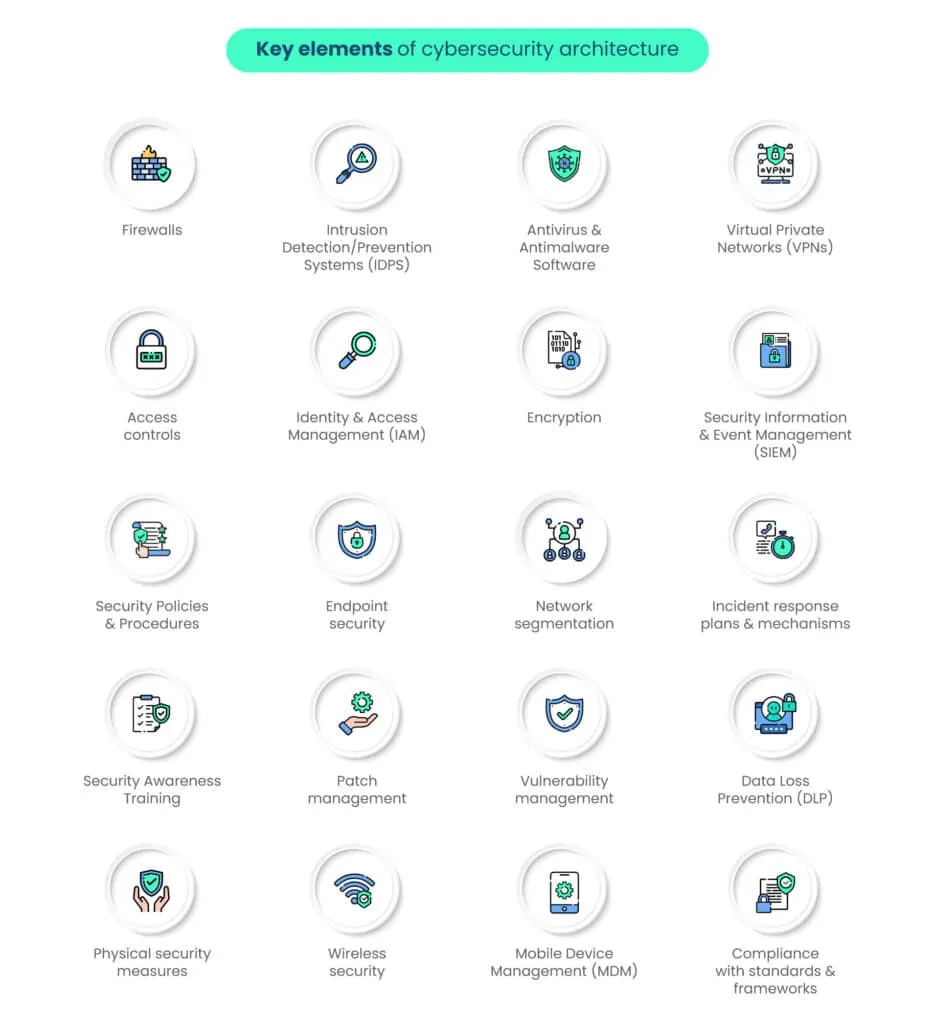
Let’s delve into the core components that constitute cybersecurity architecture and understand how they contribute to a resilient defense strategy.
1. Firewalls
Firewalls act as the first line of defense, monitoring and controlling incoming and outgoing network traffic. In cybersecurity architecture, firewalls are strategically placed to filter and block unauthorized access, preventing malicious entities from compromising the integrity of the network.
2. Intrusion Detection/Prevention Systems (IDPS)
Intrusion Detection Systems (IDS) and Intrusion Prevention Systems (IPS) play a crucial role in identifying and responding to potential threats. IDS monitors network or system activities for malicious actions or security policy violations, while IPS actively prevents or blocks such activities.
3. Antivirus and Antimalware Software
These programs are designed to detect, prevent, and remove malicious software, including viruses, worms, and other types of malware.
4. Virtual Private Networks (VPNs)
VPNs securely connect remote users or networks to the organization’s internal network over the internet, ensuring encrypted communication.
5. Access controls
Access controls are the gatekeepers of digital systems, determining who can enter, access, or modify specific resources. In the context of cybersecurity architecture, effective access controls are essential for maintaining the integrity of a system. Here’s an exploration of their significance:
- Principle of least privilege: Access controls adhere to the principle of least privilege, ensuring that individuals or systems only have access to the resources necessary for their function. This minimizes the potential damage caused by unauthorized access and restricts the lateral movement of attackers within a network.
- Authentication and authorization: Authentication verifies the identity of users, ensuring they are who they claim to be. Authorization then determines the level of access granted to authenticated entities. Together, these access control measures prevent unauthorized individuals from infiltrating secure systems.
- Continuous monitoring for anomalies: Modern access controls incorporate continuous monitoring mechanisms that detect anomalies or suspicious activities. By dynamically adjusting access privileges based on real-time behavior analysis, organizations can respond promptly to potential security threats.
6. Identity and Access Management (IAM)
These solutions manage and secure user identities, authentication, and authorization processes.
7. Encryption
Encryption ensures the confidentiality of data by making it indecipherable to unauthorized entities. Even if an intruder gains access to encrypted data, they will be unable to comprehend its meaning without the proper decryption key.
Cybersecurity architecture employs encryption to protect data both in transit and at rest. During transmission over networks, protocols like SSL/TLS encrypt data, preventing eavesdropping. At rest, stored data remains secure, guarding against unauthorized access or theft.
Many industries are subject to stringent data protection regulations. Encryption protocols not only fortify cybersecurity but also contribute to regulatory compliance.
8. Security Information and Event Management (SIEM)
These systems collect, analyze, and correlate log and event data from various sources across an organization’s IT infrastructure to identify and respond to security incidents.
9. Security Policies and Procedures
These documented guidelines and rules define the organization’s approach to cybersecurity, including acceptable use policies, incident response plans, and data protection policies.
10. Endpoint security
These solutions protect individual devices (e.g., computers, mobile devices) from cybersecurity threats, including antivirus software, firewalls, and device management tools.
11. Network segmentation
This involves dividing a network into smaller segments to limit the impact of a security breach and prevent lateral movement of attackers.
12. Incident response plans and mechanisms
Incident response mechanisms are the emergency protocols embedded within the cybersecurity architecture to swiftly identify, mitigate, and recover from security incidents.
These mechanisms are crucial for minimizing the impact of cyber threats and ensuring business continuity:
- Early detection through monitoring: Incident response begins with proactive monitoring of networks and systems. Early detection allows organizations to identify anomalies or potential threats, triggering a rapid response before an incident escalates.
- Formalized incident response plans: Cybersecurity architecture includes formalized incident response plans, outlining predefined steps to be taken in the event of a security incident. These plans involve coordinated efforts from IT teams, legal departments, and relevant stakeholders to ensure a unified and effective response.
- Continuous improvement through post-incident analysis: After an incident is resolved, cybersecurity architecture incorporates post-incident analysis. This involves assessing the effectiveness of the response, identifying areas for improvement, and refining incident response plans. Continuous improvement ensures that organizations are better prepared for future incidents.
13. Security Awareness Training
Security awareness training is a crucial component of cybersecurity aimed at educating employees and users about best practices in cybersecurity, potential risks, and the importance of adhering to established security policies.
The training typically covers various aspects, including secure online behavior, password management, identification of common cyber threats like phishing attacks and malware, and the significance of promptly reporting security incidents.
Delivery methods often include a combination of online courses, workshops, and simulated exercises to ensure that employees remain informed about evolving cybersecurity threats.
14. Patch management
Patch management is a systematic approach to maintaining the security of an organization’s software, operating systems, and applications. The primary goal is to ensure that all systems are regularly updated with the latest security patches to address known vulnerabilities. This involves a comprehensive process, including vulnerability assessments, testing of patches in controlled environments, and the timely deployment of patches to eliminate potential entry points for cyber threats.
Effective patch management is critical for preventing the exploitation of known vulnerabilities, reducing the attack surface, and enhancing the overall security posture of the organization.
15. Vulnerability management
Vulnerability management is a proactive strategy focused on identifying, assessing, and prioritizing vulnerabilities in an organization’s systems and networks. The process involves regular vulnerability scanning, risk assessment to evaluate potential impacts and likelihood of exploitation, prioritization based on assessed risks, and the implementation of mitigation strategies. This lifecycle approach ensures that the organization adapts to evolving threats and changes in its IT landscape, maintaining a robust defense against potential security breaches.
16. Data Loss Prevention (DLP)
Data Loss Prevention (DLP) encompasses technologies and strategies designed to prevent unauthorized access, use, and sharing of sensitive data within an organization.
Components of DLP include content discovery to identify sensitive data, real-time monitoring and enforcement of policies to prevent data leakage, encryption of sensitive information, and user education on handling confidential data responsibly.
DLP is essential for maintaining data confidentiality, complying with privacy regulations, and preventing data breaches that could lead to significant financial and reputational consequences.
17. Physical security measures
Physical security measures are implemented to protect the physical access to critical infrastructure components, such as data centers and server rooms, safeguarding against unauthorized entry and potential security breaches.
These measures include access controls, such as card readers and biometric scanners, video surveillance systems to monitor access points, environmental controls like climate control and fire suppression, and the establishment and enforcement of security policies regarding visitor access.
Integrating physical security measures with overall cybersecurity strategies creates a comprehensive security posture for the organization.
18. Wireless security
Wireless security is dedicated to implementing measures that secure wireless networks, including encryption, access controls, and monitoring.
This involves configuring access points with strong encryption protocols to protect data in transit, restricting connections to authorized devices through robust authentication mechanisms, deploying Wireless Intrusion Detection Systems (WIDS) to detect unauthorized access or malicious activities, and conducting regular audits to identify and address vulnerabilities.
Given the susceptibility of wireless networks to unauthorized access, robust wireless security measures are essential in today’s interconnected environment.
19. Mobile Device Management (MDM)
Mobile Device Management (MDM) focuses on ensuring the security of mobile devices, including smartphones and tablets, used within the organization.
MDM capabilities include device enrollment, policy enforcement for security measures such as password requirements and encryption, remote wipe functionalities for lost or stolen devices, and control over the installation and usage of applications.
MDM helps organizations maintain compliance with security policies, reducing the risk of data breaches and unauthorized access through mobile devices.
20. Compliance with standards and frameworks
Compliance with industry-specific regulations, standards, and cybersecurity frameworks is a foundational aspect of maintaining a baseline level of security and regulatory adherence. Examples include ISO 27001 for information security management systems, the NIST Cybersecurity Framework for overall cybersecurity improvement, and GDPR for data protection and privacy.
Adhering to these standards helps organizations demonstrate their commitment to security, build trust with customers, and avoid legal and financial consequences associated with non-compliance. Incorporating these compliance measures into the broader cybersecurity strategy provides a structured and standardized approach to security governance.
Business resilience through cybersecurity architecture

In the intricate dance between technology and security, the role of cybersecurity architecture extends beyond protection; it becomes a catalyst for business resilience.
1. Maintaining business continuity
a. Proactive defense against disruptions
Cybersecurity architecture, with its proactive approach, serves as a shield against disruptions that could otherwise cripple business operations. By identifying and addressing vulnerabilities, organizations can thwart potential cyber threats and ensure the seamless continuation of essential functions.
b. Reducing downtime and financial losses
In the event of a cyber incident, swift response mechanisms embedded in cybersecurity architecture minimize downtime. The ability to recover quickly reduces financial losses associated with business interruptions, reinforcing the overall resilience of the organization.
c. Disaster recovery integration
Business continuity within the cybersecurity architecture extends to disaster recovery planning. By integrating robust disaster recovery protocols, organizations can swiftly recover data and systems, further fortifying their ability to navigate unforeseen challenges.
2. Protecting critical assets
Cybersecurity architecture involves a meticulous assessment of critical assets within an organization. By identifying and prioritizing these assets, businesses can focus their protective measures where they matter most, ensuring the resilience of their core operations.
a. Safeguarding intellectual property
For many organizations, intellectual property is a cornerstone of competitiveness. Cybersecurity architecture employs encryption, access controls, and other measures to safeguard intellectual property, preventing unauthorized access or theft that could compromise the organization’s competitive edge.
b. Regulatory compliance and data protection
Protecting critical assets also involves compliance with regulatory standards. Cybersecurity architecture aligns with data protection regulations, ensuring that organizations meet legal requirements for the secure handling of sensitive information. This not only protects critical assets but also shields the organization from legal repercussions.
3. Preserving stakeholder trust
a. Building and maintaining trust
Stakeholder trust is a delicate yet invaluable asset. Cybersecurity architecture plays a pivotal role in building and maintaining trust by assuring stakeholders that their data and interactions with the organization are secure. This trust, once established, contributes to the resilience of the business in the face of challenges.
b. Transparent communication during incidents
In the unfortunate event of a security incident, transparent communication is key to preserving stakeholder trust. Cybersecurity architecture incorporates communication protocols that keep stakeholders informed, demonstrating the organization’s commitment to addressing issues responsibly.
c. Reputation management
Cybersecurity incidents can impact an organization’s reputation. Cybersecurity architecture includes measures for reputation management, helping organizations recover trust through transparent communication, swift resolution, and ongoing efforts to enhance security measures.
Implementing cybersecurity architecture

From strategic planning to continuous monitoring and scalability, the successful implementation of cybersecurity architecture is critical for organizations aiming to secure their digital assets effectively.
1. Strategic planning for effective defense
a. Assessing organizational needs and risks
Before implementing cybersecurity architecture, organizations must conduct a comprehensive assessment of their needs and risks. This involves understanding the unique aspects of their operations, the types of data they handle, and the potential threats they face. By identifying specific vulnerabilities, organizations can tailor their cybersecurity architecture to address their most pressing concerns.
b. Defining clear objectives and goals
Strategic planning necessitates the definition of clear cybersecurity objectives and goals. These objectives should align with the organization’s overall business strategy. Whether the focus is on protecting customer data, intellectual property, or ensuring compliance with industry regulations, well-defined goals guide the implementation of effective cybersecurity measures.
c. Budgeting and resource allocation
Implementing cybersecurity architecture requires financial investment and resource allocation. Organizations must allocate sufficient budget and resources to ensure the successful execution of their strategic plan. Balancing the cost of cybersecurity with the potential consequences of a security breach is crucial for making informed budgetary decisions.
2. Continuous monitoring and adaptation
a. Real-time threat detection
Continuous monitoring involves the real-time observation of network and system activities to detect anomalies or potential security threats. Implementing tools and technologies that provide visibility into the organization’s digital environment enables proactive responses to emerging risks.
b. Incident response protocols
Cybersecurity architecture incorporates incident response protocols that dictate the steps to be taken in the event of a security incident. Continuous monitoring allows organizations to detect incidents promptly, triggering the activation of predefined response plans. This proactive approach minimizes the impact of security breaches and accelerates recovery efforts.
c. Regular security audits and assessments
To ensure the ongoing effectiveness of cybersecurity architecture, organizations conduct regular security audits and assessments. These evaluations identify areas for improvement, verify compliance with security policies, and assess the resilience of existing defense mechanisms. Continuous monitoring and adaptation involve a commitment to refining security measures based on the insights gained from these assessments.
3. Scalability for businesses
a. Tailoring solutions to organizational size
One of the strengths of cybersecurity architecture lies in its scalability. Implementing a scalable architecture involves tailoring solutions to the specific size and needs of the organization. Whether a small business or a large enterprise, the principles of cybersecurity architecture can be adapted to provide effective defense without unnecessary complexity.
b. Modular and flexible design
A scalable cybersecurity architecture is characterized by a modular and flexible design. This allows organizations to add or adjust security measures as their needs evolve. Whether scaling up due to business growth or adapting to new threats, a well-designed architecture accommodates changes without major disruptions to operations.
c. Considerations for resource-constrained environments
Smaller organizations may operate with resource constraints, making it crucial to prioritize security measures based on risk. Cybersecurity architecture offers flexibility in choosing solutions that align with the organization’s budget and resource limitations, ensuring that even businesses with fewer resources can implement effective defense strategies.
Common challenges in implementing cybersecurity architecture
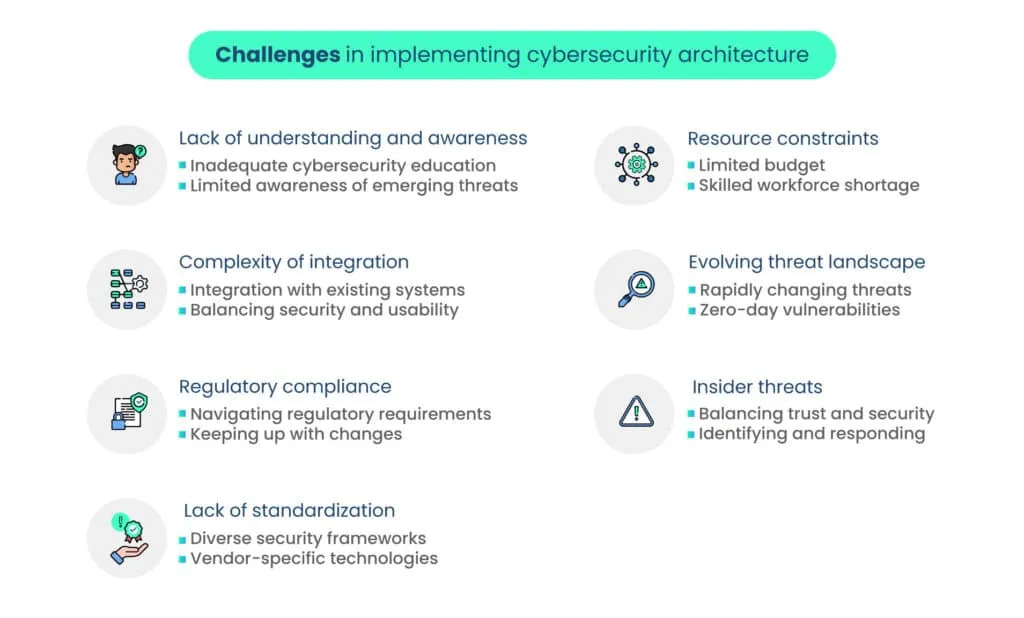
Implementing cybersecurity architecture comes with its share of challenges. Understanding and addressing these hurdles are crucial for organizations striving to establish a resilient defense. Let’s explore these common challenges:
1. Lack of understanding and awareness
- Inadequate cybersecurity education: Organizations may lack a clear understanding of cybersecurity architecture, necessitating investment in cybersecurity education.
- Limited awareness of emerging threats: Staying informed about evolving threats can be challenging, requiring regular training programs and community engagement.
2. Resource constraints
- Limited budget: Many organizations, especially smaller ones, struggle with budget constraints for cybersecurity initiatives.
- Skilled workforce shortage: The shortage of skilled cybersecurity professionals hampers effective implementation and management.
3. Complexity of integration
- Integration with existing systems: Integrating cybersecurity with existing systems can be complex, requiring careful planning and testing.
- Balancing security and usability: Striking the right balance between security and usability is an ongoing challenge.
4. Evolving threat landscape
- Rapidly changing threats: Adapting to the rapidly changing threat landscape requires continuous monitoring and threat intelligence integration.
- Zero-day vulnerabilities: Zero-day vulnerabilities pose a significant challenge, demanding proactive measures such as threat hunting and timely patch management.
5. Regulatory compliance
- Navigating regulatory requirements: Navigating complex regulatory requirements is time-consuming, requiring dedicated efforts.
- Keeping up with changes: Staying updated with regulatory changes is essential to ensure ongoing compliance.
6. Insider threats
- Balancing trust and security: Balancing trust and security is delicate, requiring the implementation of user behavior analytics and robust access controls.
- Identifying and responding: Timely identification and response to insider threats demand comprehensive monitoring systems and incident response plans.
7. Lack of standardization
- Diverse security frameworks: Diverse security frameworks make standardization challenging, requiring organizations to navigate varying standards.
- Vendor-specific technologies: The presence of vendor-specific technologies complicates integration, emphasizing the need for industry standardization efforts.
Factors to consider for long-term effectiveness of cybersecurity architecture

As organizations invest in cybersecurity architecture, ensuring its long-term effectiveness is paramount. Let’s delve into the key factors that contribute to the enduring effectiveness of cybersecurity architecture:
1. Alignment with business objectives
- Strategic alignment: Cybersecurity architecture should align with the overarching business objectives of the organization. A cohesive strategy ensures that security measures complement rather than hinder business operations.
- Continuous review: Regularly reviewing and adjusting cybersecurity measures in response to changes in business objectives, operations, or industry landscape is crucial for maintaining alignment.
2. Comprehensive risk assessment
- Regular risk assessments: Periodic risk assessments help organizations identify new threats, vulnerabilities, and potential impacts. Continuous monitoring ensures that the cybersecurity architecture evolves in response to emerging risks.
- Prioritization of risks: Understanding and prioritizing risks based on their potential impact on the organization allows for targeted and effective mitigation strategies.
3. Robust incident response planning
- Scenario-based planning: Developing incident response plans based on realistic scenarios enhances preparedness. Regularly testing these plans ensures that the organization can respond effectively to various cyber threats.
- Continuous improvement: Post-incident analysis and continuous refinement of incident response plans contribute to a more resilient cybersecurity posture.
4. Integration of emerging technologies
- Adopting innovative solutions: Cybersecurity architecture should be adaptable to integrate emerging technologies. Keeping abreast of technological advancements helps organizations stay ahead of evolving cyber threats.
- Scalability: Ensuring that the architecture can scale with the adoption of new technologies accommodates the growth and changing needs of the organization.
5. Employee training and awareness
- Continuous training programs: Regularly educating employees about cybersecurity best practices is essential. Building a security-aware culture reduces the risk of human error and strengthens the overall defense.
- Phishing simulations: Conducting phishing simulations helps employees recognize and resist social engineering attacks, contributing to a more resilient security posture.
6. Regulatory compliance
- Adherence to regulations: Ensuring ongoing compliance with industry-specific and regional regulations is vital. Regular audits and assessments help identify and address any compliance gaps.
- Proactive compliance monitoring: Proactively monitoring regulatory changes ensures that the cybersecurity architecture remains aligned with evolving legal requirements.
7. Vendor management
- Continuous vendor assessment: Regularly evaluating and assessing the security practices of third-party vendors is crucial. Ensuring that vendors adhere to security standards contributes to the overall resilience of the organization.
- Secure integration: Verifying the security of integrated third-party solutions prevents potential vulnerabilities introduced through external systems.
8. Data lifecycle management
- Data classification: Classifying and categorizing data based on sensitivity allows for targeted security measures. Protecting sensitive data throughout its lifecycle is critical for maintaining trust and compliance.
- Secure data disposal: Establishing secure procedures for data disposal ensures that sensitive information is not inadvertently exposed at the end of its lifecycle.
9. Regular security audits
- Independent audits: Conducting regular independent security audits provides an unbiased assessment of the effectiveness of cybersecurity measures.
- Continuous improvement: Using audit findings to drive continuous improvement in security measures enhances the long-term resilience of the cybersecurity architecture.
10. Executive leadership involvement
- Top-down commitment: Executive leadership should demonstrate a commitment to cybersecurity by actively participating in decision-making and resource allocation.
- Cybersecurity culture: Fostering a cybersecurity-aware culture from the top down reinforces the importance of security throughout the organization.
Wrapping up
In the dynamic digital world, robust cybersecurity architecture is a strategic imperative, serving as a proactive defense against a range of cyber threats. It ensures business resilience, protects critical assets, and preserves stakeholder trust.
Continuous improvement through regular assessments, incident response testing, training, and audits is crucial for a resilient cybersecurity posture that evolves with the changing threat landscape. As organizations navigate the digital frontier, cybersecurity architecture becomes a vital strategic compass in an era defined by technological dynamism.
Scrut invites you to experience firsthand how its innovative solutions can elevate your security posture. Contact Scrut today to schedule a demo tailored to your organization’s needs. Secure your digital future with Scrut, your trusted partner in cybersecurity.
Frequently Asked Questions
1. What is cybersecurity architecture, and how does it differ from traditional cybersecurity measures?
Cybersecurity architecture refers to the strategic design and implementation of security measures within a digital environment. Unlike traditional cybersecurity, which may focus on individual components, architecture encompasses a comprehensive, structured approach to safeguarding an entire system or network.
2. Why is cybersecurity architecture important in today’s rapidly evolving digital landscape?
The digital landscape is constantly evolving, and cyber threats are becoming more sophisticated. Cybersecurity architecture is crucial as it provides a proactive and strategic defense, anticipating and mitigating potential risks before they manifest. It ensures a robust framework for protecting sensitive data and maintaining the integrity of digital systems.
3. What are the key components of an effective cybersecurity architecture?
An effective cybersecurity architecture typically includes elements such as firewalls, intrusion detection/prevention systems, encryption protocols, access controls, and incident response mechanisms. Additionally, it involves strategic planning, risk assessment, and continuous monitoring to adapt to emerging threats.
4. How does cybersecurity architecture contribute to overall business resilience?
Cybersecurity architecture is integral to business resilience by preventing and minimizing the impact of cyberattacks. It helps maintain business continuity, protects critical assets, and preserves the trust of customers and stakeholders. A well-designed architecture ensures that a business can withstand and recover from cyber incidents efficiently.
5. Can small businesses benefit from implementing cybersecurity architecture, or is it primarily for larger enterprises?
Cybersecurity architecture is beneficial for businesses of all sizes. While larger enterprises may have more complex infrastructures to protect, small businesses are equally susceptible to cyber threats. Implementing a tailored cybersecurity architecture ensures that security measures are proportionate to the size and needs of the business, providing a scalable and cost-effective defense against potential cyber risks.