Effective onboarding and offboarding are essential for maintaining a secure organizational environment. These processes contribute significantly to risk prevention and overall security.
In this guide, we will delve into the strategies and practices that can help organizations successfully onboard and offboard employees while minimizing potential security risks.
Today, the processes of onboarding and offboarding have transcended their traditional administrative roles. They now stand as critical pillars of an organization’s overall security and risk management strategy.
In an era characterized by complex cyber threats and stringent regulations, the seamless integration of new employees and the careful departure of outgoing ones are more important than ever.

Similar to privilege misuse, there are several cyber risks associated with employees. Most of these are often overlooked while onboarding and offboarding employees, which is where threats are most likely to enter.
Let’s take a look at some of the steps organizations can take to prevent cyber risks associated with employees—a onboarding and offboarding checklist for employees, if you will.
The essence of onboarding and offboarding
Onboarding, the art of introducing new talent to a company’s culture, operations, and expectations, lays the foundation for an employee’s journey within the organization.
Similarly, offboarding, the respectful conclusion of an employee’s tenure, requires meticulous attention to ensure a smooth exit.
Beyond the surface-level formalities, both of these processes hold the potential to either bolster an organization’s security or expose it to potential risks.
Risk prevention
Though not immediately evident, the ties between onboarding, offboarding, and risk prevention are strong.
A robust onboarding process ensures that incoming employees are educated about the company’s security policies and protocols right from the start. This not only fosters a culture of security awareness but also cultivates responsible data handling practices.
Conversely, a well-orchestrated offboarding process reduces the risk of data breaches and unauthorized access following an employee’s departure.
Swiftly revoking access credentials, transferring duties, and conducting thorough data backups help plug potential security gaps that could be exploited by malicious actors.

A holistic approach to security
Taken together, onboarding and offboarding employees act as the bookends of a comprehensive security approach. Effective onboarding establishes a solid base of security awareness and knowledge among employees from day one.
Likewise, a well-executed offboarding process ensures that exiting employees leave the organization with their access and knowledge gracefully curtailed, minimizing the chances of data leaks and breaches.
In the following sections, we’ll delve into the strategies and components that constitute successful onboarding and offboarding processes. From verifying employee backgrounds to harnessing technology for streamlined workflows, this guide will provide a roadmap for integrating new hires while safeguarding organizational security.
By embracing the principles outlined here, organizations can pave the way for a secure and resilient future—one that starts with the initial onboarding handshake and concludes with the final keystroke of a thorough offboarding process.
Onboarding process: Mitigating initial risks
A robust onboarding process is a cornerstone of risk prevention in organizations. It serves as the first line of defense against potential security vulnerabilities and sets the tone for an employee’s approach to security.
Effective onboarding extends beyond the mere orientation of new employees. It encompasses background checks, verification procedures, and systematic training in security protocols.
By ensuring that employees are equipped with the right tools and knowledge, organizations can mitigate initial risks associated with unfamiliarity and oversights.
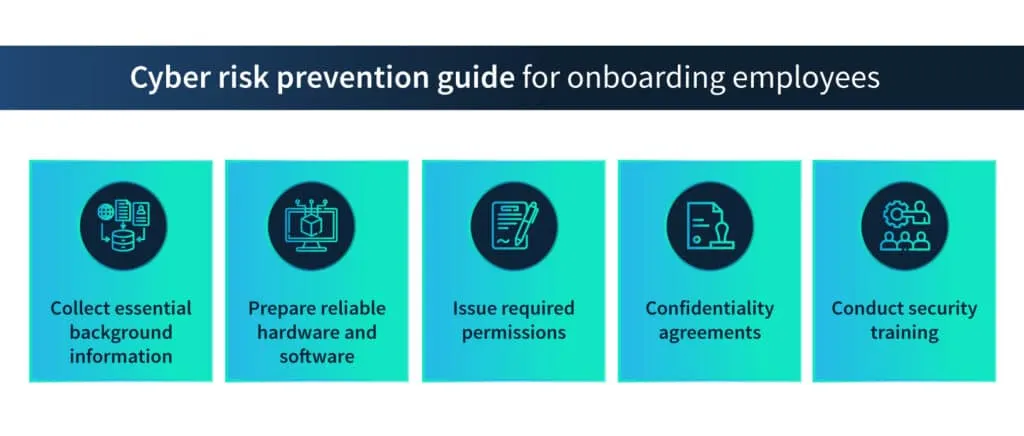
Background checks and verification
Thorough background checks are essential before welcoming a new member to the organization. Verifying an individual’s history, credentials, and references helps identify any potential red flags that might pose security or compliance risks. This step establishes a foundation of trust between the organization, its employees, and its clients.
Background information of the employees includes but is not limited to
- Their educational background – The organization must ascertain that the employee is qualified as they claim to be. In the view of cybersecurity, this step helps the organization determine how much knowledge one can expect from the employee regarding cyber threats.
- Their experience – The background check with their previous employers can reveal whether the employee can be trusted with sensitive information. A sour experience with a previous employer can be acceptable only if it is not repetitive. You can check whether the employee has tried to cause harm to their previous employer digitally or physically.
Verification can go a long way toward hiring reliable employees. Background checks can be done by the HR department or can be entrusted to outside agencies.
Training and orientation for security protocols
The initial days of onboarding are crucial for introducing employees to the organization’s security protocols. This includes guidelines for data protection, password management, and secure communication practices. Comprehensive training instils a security-conscious mindset that becomes ingrained in an employee’s daily actions.
Reliable hardware and software
If the employee is working remotely, it is advisable to send them hardware loaded with the required software and applications. If the employee chooses to use their own hardware, it must be checked for possible malware.
Hardware used by the employees—whether in the office or a remote setting–should be bought from reliable dealers, as in several cases, the hardware is pre-installed with malware. Quarantine the new hardware and check it for bugs before using it in your business.
Before allowing the employees to use hardware, your IT department must blocklist websites that can pose cyber threats. If any repair is required, the hardware should only be sent to trustworthy parties.
Buy software from developers and do not download from dodgy sources to prevent malware attacks. Installation of additional software should require administrative rights to block employees from downloading malicious content. In addition, update your software regularly to patch the known vulnerabilities.

Ensuring authorized access
Granting the right level of access to new employees is a delicate balance. Providing necessary access while avoiding over-entitlement helps prevent data breaches and internal threats. Role-based access control ensures that each employee can only access the resources essential for their job responsibilities.
Permission to access the organization’s databases must be given per employees’ need to know. In short, if they need the information to perform their job, share it; otherwise, don’t. The new employees might also need official email addresses and new IDs to access shared software.
Make the software and database access password protected. Passwords are your first line of defense in the cyberworld. Most of the time, employees are required to change the password set up by the IT department while creating their IDs.
However, employees tend to go along with the same password and create vulnerabilities. Ensure that your new employees use their own passwords instead of generic ones and that their passwords are strong.
Confidentiality agreements
In organizations where information is imperative, confidentiality agreements are given to the new employees to sign. These confidentiality agreements must be written with legal help as they are binding on both parties.
Ensure that any agreements with their previous employers do not bind the new employees. For example, some organizations have contractual agreements with their employees that they will not share client details with outside parties.
In the subsequent sections, we’ll delve into the components that make up a successful onboarding process, including pre-arrival preparations, first-day orientation, and ongoing training. These steps collectively contribute to creating a workforce that not only understands security best practices but actively participates in the risk prevention efforts of the organization.
Components of an effective onboarding process
A well-structured onboarding process is the cornerstone of a security-conscious organization. It goes beyond a simple orientation and encompasses various phases that equip employees with the knowledge, tools, and resources needed to contribute to a secure work environment.
Let’s delve into the key components that constitute an effective onboarding process:
1. Pre-arrival phase
Before a new employee even steps through the office doors, a thoughtful pre-arrival phase sets the tone for a seamless onboarding experience.
Clear communication and expectations: Initiating open communication with new hires about their first day, required documentation, and what they can expect helps alleviate any uncertainties and nerves.
Preparing required documentation: Streamline administrative processes by preparing essential paperwork in advance. This allows employees to focus on learning rather than drowning in paperwork.
2. First day orientation
The first day serves as the official introduction to the company’s culture, values, and security measures.
Introduction to Policies and Compliance: Deliver a comprehensive overview of company policies, including data handling, cybersecurity, and ethical conduct. This ensures that new employees understand the rules from the outset.
Issuing Access Credentials: Provide employees with access cards, security badges, and login credentials required to navigate the organization’s physical and digital spaces securely.
3. Training and education
Continuous education is a cornerstone of maintaining a security-conscious workforce. Regular training sessions equip employees with the skills they need to keep security top of mind.
Cybersecurity Best Practices: Introduce new hires to the fundamentals of cybersecurity, including recognizing phishing attempts, using strong passwords, and safeguarding sensitive information.
Overview of Physical Security Measures: Educate employees about physical security protocols, such as badge usage, access control, and reporting suspicious activities. This ensures that security extends beyond digital realms.
Each of these components serves a crucial purpose in establishing a secure foundation for employees.
By meticulously attending to the pre-arrival phase, first-day orientation, and ongoing training, organizations foster a workforce that is well-versed in security protocols, compliant with regulations, and poised to actively contribute to risk prevention.
Through this holistic onboarding approach, organizations not only welcome new talent but also imbue them with a security-first mindset that permeates their every action and decision.
Offboarding Process: Minimizing Departure-Related Risks
While onboarding sets the stage for a secure work environment, the offboarding process is equally critical in preventing potential security risks that can arise from an employee’s departure.
A well-structured offboarding process ensures that exiting employees leave the organization with their knowledge and access gracefully curtailed, safeguarding sensitive information and reducing the risk of data breaches.
Offboarding encompasses all of the actions required to properly part ways with an employee after their resignation, termination, or retirement.
When done correctly, a straightforward offboarding procedure promotes a smooth transition for both the firm and the departing employee. It also plays a critical role in risk management, as employees can have access to a lot of information during their tenure. Remote work has added some more challenges to an already difficult task.
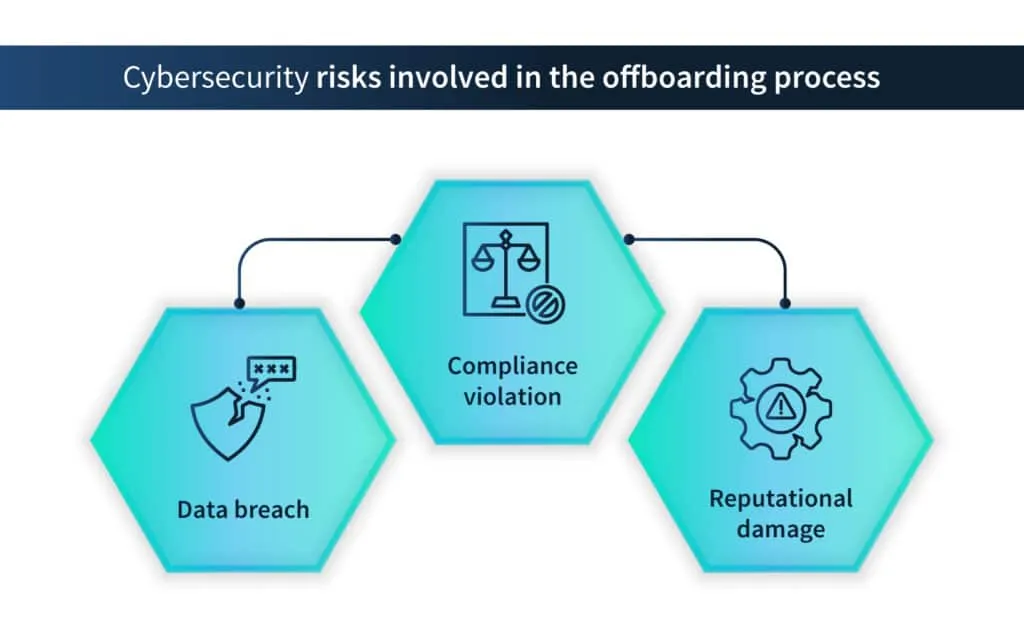
Cybersecurity risks involved in the offboarding process include:
- Data breach – Intentional or unintentional damage to the database by using the login credentials given to them while working.
- Compliance violations – There are compliance violations when there is a data breach. Disgruntled employees – present or former – might use their positions to cause damage to the organization by leaking the data. This can lead to major compliance issues.
- Reputational damage – Data breaches can cause significant damage to the reputation of the organization. Customers might think twice about buying from an organization whose data has been compromised.
Steps for maintaining cybersecurity while offboarding
Although the offboarding process differs in every organization, here are some of the absolutely necessary steps for maintaining cybersecurity while offboarding employees.
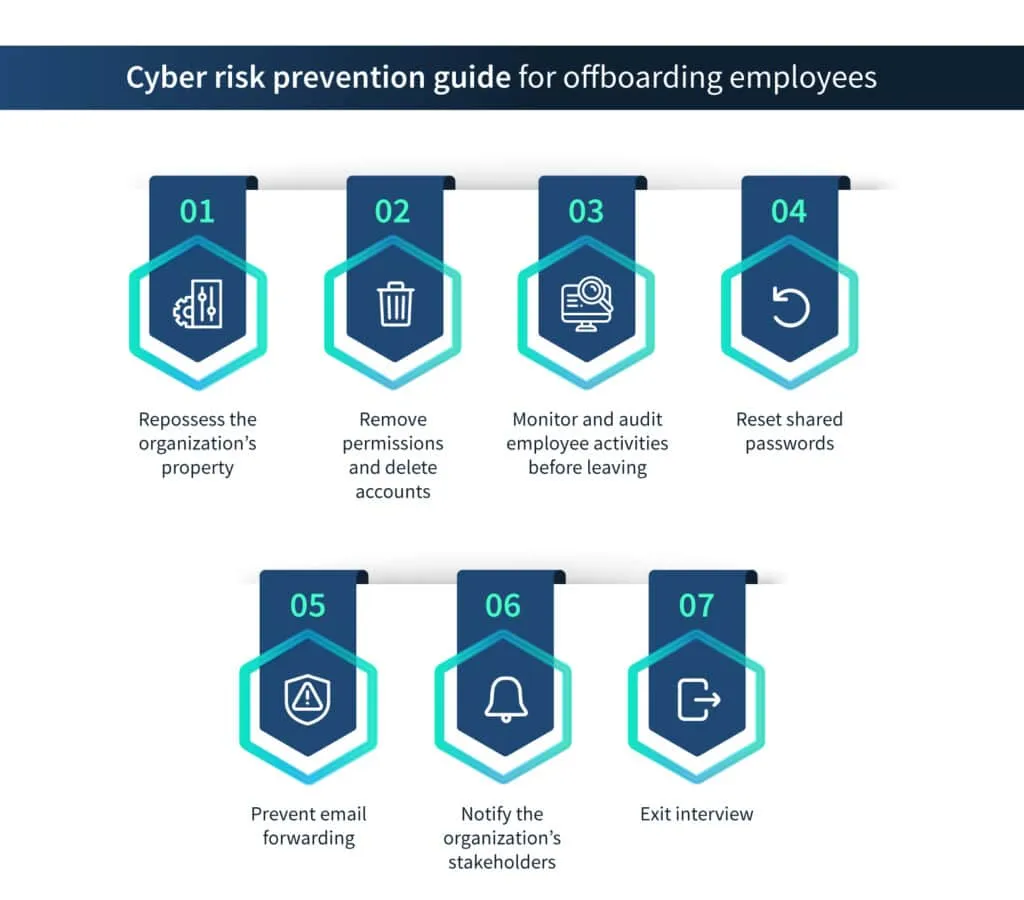
Repossess the organization’s property
Employees are given organizational property to perform their duties. There must be a list of all the hardware and other properties given to employees, and they should all be collected at the end of the employee’s tenure.
The hardware should be checked for any malware that might have been installed while the employee was using it. Also, if there are any repairs needed, they must be done soon.
Remove permissions and delete accounts
This is the most important step for cybersecurity that organizations often overlook. The employees are given permission to access databases and applications of the organization. When they stop working, these permissions should be rescinded; otherwise, they can be used to steal data maliciously.
Account IDs created for the employees to use the software should be deleted; otherwise, ex-employees can use the company software for their own purposes, which often have malicious intentions.
Monitor and audit employee activities before leaving
Most organizations mandate a notice period for employees. Sometimes, employees use this notice period to cause harm to the information system or steal data that can be used to further their careers.
These acts are not only immoral but are also illegal. When the employee leaves the organization, and especially when they leave with a grudge, appropriate audits must be conducted to verify whether the departing employee has downloaded too much data, inserted malware into the information system, or did any activity that they might not do under normal circumstances.
Reset shared passwords
There are many accounts, such as wifi networks and accounting software, where multiple employees share passwords. These passwords must be changed as soon as one of the employees leaves the organization.
Such passwords are often set according to a predetermined pattern, like a combination of employee name and ID number. If any employee leaves the organization, these patterns must be changed too; otherwise, they can guess another employee’s password to enter the organization’s information system.
Prevent email forwarding
A common hack used by departing employees is to forward the organization’s emails to their personal email addresses. This will keep them in the loop even after they have left the organization. The IT department must ensure that the leaving employee has not used this trick on any of the organization’s email addresses or other employees’ email addresses.
Notify the organization’s stakeholders
An employee is a representative and, in many ways, an agent of the organization. They represent the organization when communicating with suppliers, customers, shareholders, or even other employees. So, if the employee leaves the organization, these stakeholders must be informed.
They should know the exact date from which they are leaving and the circumstances under which they are leaving the organization. It helps the organization to protect itself in many ways.
Exit interview
What has cybersecurity to do with an exit interview? Well, nothing as such, but HR can gauge the employee’s feelings in the exit interview. This will help them know whether the employee is unhappy and likely to cause damage to the organization.
If HR thinks that that is the case, they must promptly inform the IT department to ensure they are on a without.
The significance of proper offboarding
An ineffective offboarding process can inadvertently create security vulnerabilities. Without proper management of access credentials, data, and responsibilities, former employees might retain unauthorized access, inadvertently or maliciously compromising an organization’s security.
Key components of an effective offboarding process
An effective offboarding process goes beyond the collection of company property. It’s a comprehensive strategy that encompasses several crucial components.
Resignation/notice period:
Initiation of Departure Process: When an employee submits their resignation, it’s essential to promptly initiate the offboarding process. This ensures ample time to complete all necessary tasks before their departure.
Collection of Company Property: This phase involves retrieving items such as laptops, access cards, security badges, and any other company-owned materials issued to the employee.
Data and access management
Revoking Unnecessary Access: Revoking access to systems, databases, and resources that are no longer required for the role prevents former employees from accessing sensitive information after their departure.
Transfer of Responsibilities and Data Backup: Responsibilities should be smoothly transitioned to other team members to prevent gaps in operational tasks. Additionally, performing a thorough data backup helps ensure that critical information is retained even after an employee’s departure.
Exit interview component
Feedback Collection for Process Enhancement: Conducting exit interviews provides departing employees with the opportunity to provide feedback on their experience. This feedback can help identify areas for process improvement and enhance the organization’s overall operations.
By executing these components meticulously, organizations minimize the risk of unauthorized access, data leaks, and other potential security breaches associated with an employee’s departure. A comprehensive offboarding process ensures that an employee’s departure is as secure and smooth as their entry into the organization.
Automation and technology in onboarding and offboarding
Today, leveraging automation and technology has become paramount in enhancing the efficiency, accuracy, and security of onboarding and offboarding processes. By integrating advanced tools and systems, organizations can streamline these critical procedures while minimizing the potential for errors and security gaps.
Streamlining with Human Resources Information Systems (HRIS)
Human Resources Information Systems (HRIS) play a pivotal role in managing employee data securely and efficiently. These platforms facilitate seamless onboarding by automating administrative tasks such as document collection, data entry, and employee record creation. Similarly, during offboarding, HRIS aids in the systematic revocation of access and the secure archiving of essential records.
Access management tools
Automated access management tools enable organizations to assign and revoke access credentials swiftly and accurately. These tools ensure that access rights align with an employee’s role and responsibilities, reducing the risk of unauthorized access during their tenure and after departure.
Auditing and compliance monitoring
Automation enables real-time monitoring and auditing of access logs, ensuring that permissions are aligned with company policies and compliance regulations. This proactive approach enhances an organization’s ability to identify and rectify potential security breaches swiftly.
Communication and collaboration among departments
Effective onboarding and offboarding require seamless communication and collaboration between various departments, including Human Resources, IT, Security, and Management.
The synergy of these departments is pivotal in maintaining a secure and efficient transition for employees.
Cross-functional communication
Constant communication ensures that all departments are on the same page regarding employee onboarding and offboarding. This collaboration facilitates the timely allocation of resources, such as access credentials and necessary equipment, while preventing unnecessary delays.
Coordinated efforts for security protocols
Close collaboration between HR, IT, and Security teams ensures that security protocols are consistently enforced. From verifying employee backgrounds to monitoring access, each department’s expertise contributes to a secure onboarding and offboarding experience.
Transitioning knowledge and responsibilities
Collaboration facilitates a smooth transition of knowledge and responsibilities during offboarding. By sharing insights with incoming employees or distributing tasks among existing team members, the organization minimizes disruptions and ensures continuous operations.
Continuous improvement and adaptation
In a rapidly evolving age of technology and security threats, the importance of continuous improvement in onboarding and offboarding processes cannot be overstated.
Organizations must recognize that these processes are not static; they require regular evaluation, adaptation, and enhancement to effectively address emerging security challenges.
Staying ahead of emerging threats
As security threats continue to evolve, so must our strategies. Regularly reassessing the effectiveness of onboarding and offboarding practices helps identify potential vulnerabilities and provides opportunities to update security protocols accordingly.
Adapting to regulatory changes
The regulatory landscape is dynamic, with data protection and privacy regulations frequently undergoing revisions. By staying abreast of these changes and adjusting onboarding and offboarding practices to align with new requirements, organizations ensure compliance and reduce legal risks.
Ongoing training and education
Empowering HR and IT teams with ongoing training equips them to handle new security challenges effectively. Regular workshops, seminars, and engagement with industry experts ensure that your staff is well-equipped to implement the latest security practices.
Conclusion: Building a secure and cohesive work environment
Any change in an organization’s setup, including onboarding and offboarding of employees, can create cyber vulnerabilities. Cyber hygiene is not just about having a strong password, it extends to many other areas as well.
In the realm of onboarding and offboarding, security isn’t just a checkpoint; it’s a continuous journey. By embracing the comprehensive strategies discussed in this guide, organizations can not only integrate employees smoothly but also cultivate a security-first culture that permeates every aspect of their operations.
From the moment a new employee steps through the door to the graceful exit of a departing colleague, the principles of risk prevention and security consciousness guide the way.
An effective onboarding process sets the stage for employees to become active participants in safeguarding sensitive information, while a meticulous offboarding process ensures that organizational security remains intact even after they’ve left.
By consistently fine-tuning these processes, adapting to emerging threats, and nurturing collaboration between departments, organizations can build a work environment that is not only secure but also cohesive and resilient.
In this journey, the commitment to continuous improvement is your organization’s compass, steering you toward a future where the integration and departure of employees contribute to your overall security posture. Book a demo with Scrut to know more about the role it can play in the cyber risk scenario.
Effective onboarding is crucial for risk prevention because it educates new employees about security protocols and policies from day one. By instilling security awareness and responsible data handling practices, onboarding contributes to a culture of vigilance and reduces the likelihood of security breaches.
Technology plays a significant role in streamlining onboarding and offboarding processes. Human Resources Information Systems (HRIS) automate administrative tasks, access management tools ensure accurate permissions, and auditing tools help monitor compliance in real-time. Leveraging technology enhances efficiency and minimizes human errors.
Inadequate offboarding procedures can lead to security vulnerabilities such as unauthorized access and data breaches. Former employees might retain access to sensitive information, creating potential risks for the organization. A well-structured offboarding process ensures a smooth exit while safeguarding sensitive data and preserving security.
Onboarding and offboarding processes should be regularly reviewed and updated to align with evolving security threats and regulatory changes. As new risks emerge, organizations should adapt their processes to address these challenges effectively and ensure that employees receive the latest security training.
Collaboration between HR, IT, Security, and Management departments is essential for successful onboarding and offboarding. Open communication ensures that all aspects of security are addressed comprehensively, from verifying employee backgrounds to revoking access after departure. A united effort minimizes gaps and ensures a secure transition for employees.





































