Staying ahead of cyber threats is an ongoing challenge for organizations worldwide. In response to the dynamic nature of cybersecurity threats, government agencies continually update their guidelines and requirements to provide organizations with effective defense strategies.
Multi-Factor Authentication (MFA) has emerged as a vital strategy to enhance security across various digital platforms. By requiring users to provide multiple forms of verification before granting access, MFA significantly reduces the risk of unauthorized access, even if a password is compromised.
Aligning with the new MFA guidelines ensures that organizations are equipped to defend against unauthorized access, phishing attacks, and other security breaches.
In this blog, we will explore the new MFA guidelines and offer practical steps to help organizations align with these standards.
Understanding Multi-Factor Authentication (MFA)
MFA is a security mechanism that requires users to provide two or more verification factors to gain access to a resource, such as an application, online account, or network. This process adds an extra layer of security beyond just a username and password.
How MFA works: Types of factors
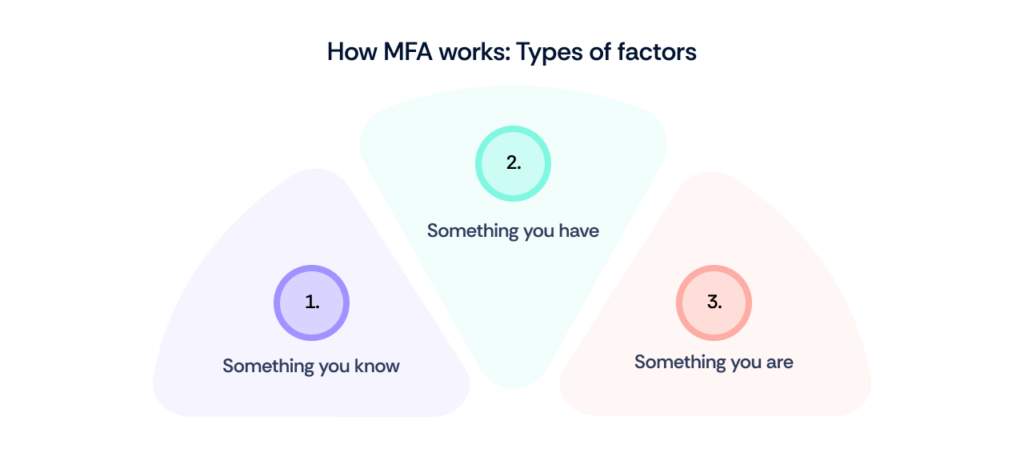
MFA typically involves three categories of factors:
- Something you know: This is usually a password or PIN that the user must remember. While effective, relying solely on this factor can leave systems vulnerable if the password is stolen or guessed.
- Something you have: This factor includes physical devices that the user possesses, such as a smartphone (for receiving a text message or using an authentication app), a security token, or a smart card. This adds a tangible element that must be physically present for authentication.
- Something you are: This involves biometric verification, such as fingerprint scans, facial recognition, or voice recognition. This factor is unique to each individual, making it extremely difficult for an unauthorized user to replicate.
Benefits of implementing MFA
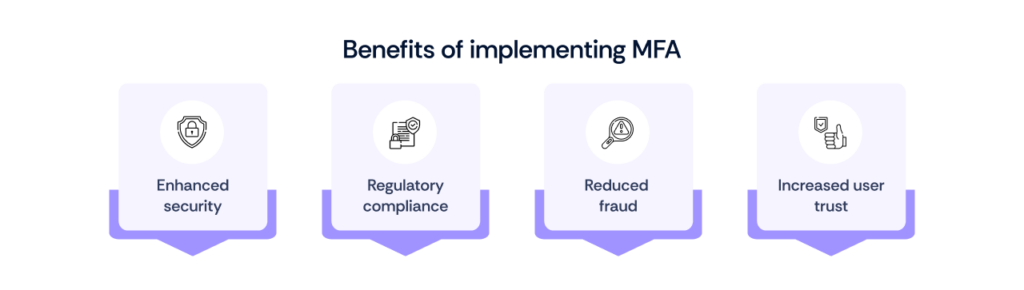
Implementing MFA offers numerous benefits, including:
- Enhanced security: MFA significantly lowers the risk of unauthorized access, even if a password is compromised.
- Regulatory compliance: Many industries require MFA as part of compliance with data protection regulations.
- Reduced fraud: By adding additional verification steps, organizations can minimize the risk of identity theft and fraud.
- Increased user trust: Users feel more secure knowing their accounts are protected by multiple layers of authentication.
Also read: Ahead of the curve: Preparing for NHS MFA Multi-Factor Authentication policy
Key organizations influencing MFA guidelines
Several key organizations play a pivotal role in shaping MFA guidelines, including:
- National Institute of Standards and Technology (NIST): NIST provides a framework for organizations to follow, offering comprehensive guidelines on authentication processes, including MFA.
- International Organization for Standardization (ISO): ISO develops international standards that help organizations implement effective security measures, including those related to MFA.
- Payment Card Industry Security Standards Council (PCI SSC): For organizations handling credit card transactions, the PCI SSC has specific requirements for MFA to protect sensitive payment information.
Together, these organizations help ensure that MFA practices evolve in line with emerging threats and technological advancements, providing a framework for organizations to follow to enhance their security posture.
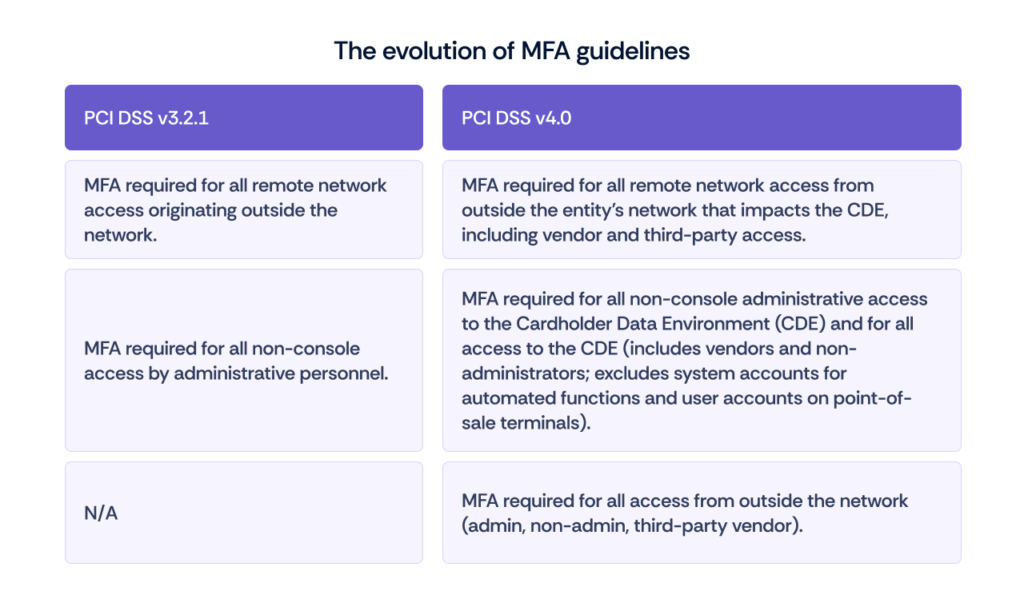
The evolution of MFA guidelines
MFA guidelines have evolved from basic password policies to complex security frameworks. Initially focused on password strength and single-factor authentication, the rise in cyber threats highlighted the need for multifaceted approaches, resulting in comprehensive MFA standards.
Recent updates reflect advancements in technology and security threats, emphasizing user experience alongside security. New guidelines address the integration of biometric methods and mobile authentication, which have become increasingly popular.
Also read: Why Organizations Need Multiple Authentication Protocols
Why Organizations Need Multiple Authentication Protocols
PCI Security Standards Council’s key changes to MFA standards

Here are the key changes to the MFA guidelines:
1. Adoption of phishing-resistant MFA – Transitioning from OTP to FIDO2 devices
Phishing attacks pose a significant threat to organizations, exploiting traditional authentication methods like passwords and OTPs. Phishing is the most prevalent cybersecurity threat, the most frequent cause of a breach, and the second most harmful threat to an organization’s bottom line.
The IBM Security Cost of a Data Breach Report 2023 found that breaches that resulted from phishing cost an average of USD 4.76 million.
To combat this, the NIST MFA guidelines suggest that organizations adopt phishing-resistant MFA solutions, such as FIDO2 (Fast Identity Online 2) devices, to mitigate the risks associated with phishing attacks.

Implementing these measures is essential for achieving a ‘Maturity Level 2’ posture.
Maturity Level 2 refers to a defined stage in the Cybersecurity Framework (CSF) developed by NIST, indicating that an organization has established basic security practices and is developing a proactive security posture. It is part of security maturity, focusing on improving processes and capabilities beyond initial ad-hoc measures.
Transitioning from OTP to FIDO2 can be challenging. While FIDO2 offers a secure alternative, organizations face challenges due to legacy systems and the continued use of OTPs.
To facilitate a smooth transition, organizations can implement MFA solutions that support both FIDO2 and OTP authentication.
This allows for:
- A gradual shift from OTPs to more secure methods.
- Balancing security, usability, and compatibility.
2. Cessation of sole reliance on biometric authentication
The Essential Eight guidelines have revised their recommendations regarding biometric authentication, suggesting that it should not be the only method used to secure systems.
Although biometric options like fingerprints and facial recognition provide convenience and added security, relying on them exclusively can lead to significant risks.

A key concern is the rise of generative AI technologies, which can mimic voices with just a few samples. This undermines the trustworthiness of voice recognition as an authentication method. Organizations need to be cautious when using biometric authentication, taking into account its limitations and potential vulnerabilities.
While biometrics can strengthen security when combined with other authentication methods, they should not be the sole means of granting access.

3. New MFA system configuration to prevent misuse
To comply with PCI DSS v4.0, particularly Requirement 8.5, your MFA systems must be configured to prevent misuse.
Here’s a breakdown of the key characteristics your solution must meet:
- Immunity to replay attacks: Your MFA solution must disrupt replay attacks, where an attacker intercepts and reuses a valid user’s message to gain unauthorized access.
- No bypass allowed: MFA must not allow bypasses unless explicitly granted by management, preventing attacks through malicious applications or intercepted MFA codes.
- Use of independent factors: MFA must use at least two independent factors, not just two different passwords or possession factors.
- All authentication factors must be successful: Access should only be granted if all required authentication factors are successfully provided.
These new requirements are considered best practices until March 31, 2025, after which they become mandatory.
4. Use of diverse authentication methods
The new MFA guidelines emphasize the use of diverse authentication methods to enhance security. Recommended methods include:
- Biometric authentication: Utilizes unique biological traits such as fingerprints, facial recognition, or iris scans.
- Hardware tokens: Physical devices that generate time-sensitive codes, such as RSA SecurID or YubiKey.
- SMS and email codes: One-time passcodes sent via SMS or email, though these are considered less secure than other methods.
- Authenticator apps: Mobile applications like Google Authenticator or Authy that generate time-based one-time passwords (TOTPs).
- Push notifications: Alerts sent to mobile devices that users can approve to authenticate.
Here’s a concise overview of the key changes in MFA guidelines primarily defined by NIST and aligned with compliance standards like PCI DSS:
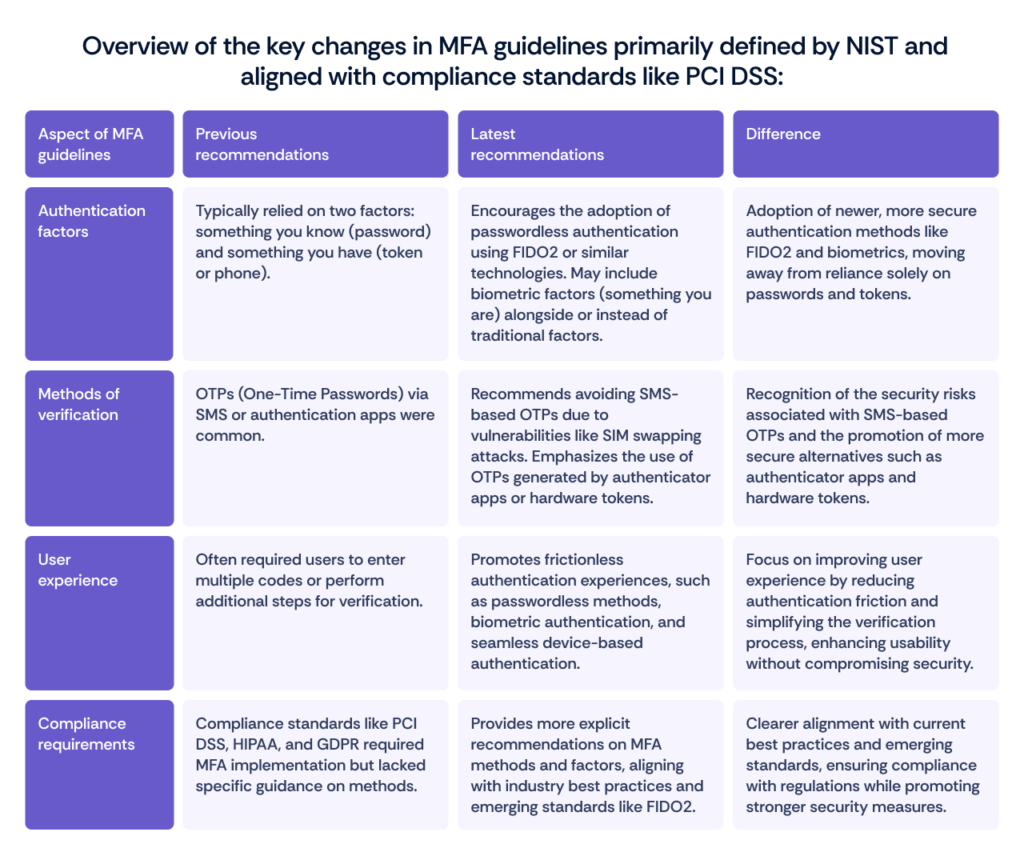
These changes reflect a shift towards more robust, user-friendly, and standards-based approaches to authentication, emphasizing the importance of security, usability, and compliance in modern MFA strategies.
Also read: Multi-cloud Security – Overview and Challenges
Multi-cloud Security – Overview and Challenges
Steps to align with the new MFA guidelines
The expansion and addition of MFA requirements in PCI DSS v4.0 may seem overwhelming, but understanding these changes will help you evaluate and adjust your current MFA solutions to ensure compliance.
As your organization plans the transition to PCI DSS 4.0, consider all the new and changed requirements and their implementation timelines.
Conduct a v4.0 readiness assessment of prior MFA configurations and access privileges to ensure compliance with this updated mandate.
1: Assess current MFA practices
- Evaluate existing authentication methods
- Review current MFA solutions in place.
- Identify which methods are being used and their effectiveness.
- Identify gaps in compliance
- Compare current practices against the latest guidelines to spot deficiencies.
- Assess whether existing methods meet security requirements and user needs.
2: Adopt recommended authentication methods
- Conduct an overview of compliant technologies
- Explore options such as biometrics, hardware tokens, and authenticator apps.
- Evaluate which technologies best fit your organization’s needs and infrastructure.
- Ensure integration with existing systems
- Ensure that new MFA solutions can seamlessly integrate with current systems and applications.
- Plan for potential system updates or changes required for integration.
3: Educate users and develop training materials
- Educate users on MFA:
- Conduct training sessions to help users understand the importance and functionality of MFA.
- Address common concerns and misconceptions about the MFA process.
- Develop resources for training sessions:
- Develop comprehensive training materials, including guides, videos, and FAQs.
- Utilize workshops and webinars to provide hands-on experience with MFA tools.
4: Conduct regular testing and stay informed on updates
- Schedule routine security assessments:
- Schedule regular assessments to evaluate the effectiveness of MFA practices.
- Test the resilience of MFA systems against potential threats.
- Stay informed on future guideline changes:
- Keep abreast of updates from key organizations (e.g., NIST, ISO) regarding MFA practices.
- Participate in industry forums and training to remain knowledgeable about evolving security standards.

Also read: What to expect in the new PCI DSS 4.0?
What to expect in the new PCI DSS 4.0?
Common challenges faced when aligning with the new MFA guidelines

Best practices for implementing the new MFA guidelines
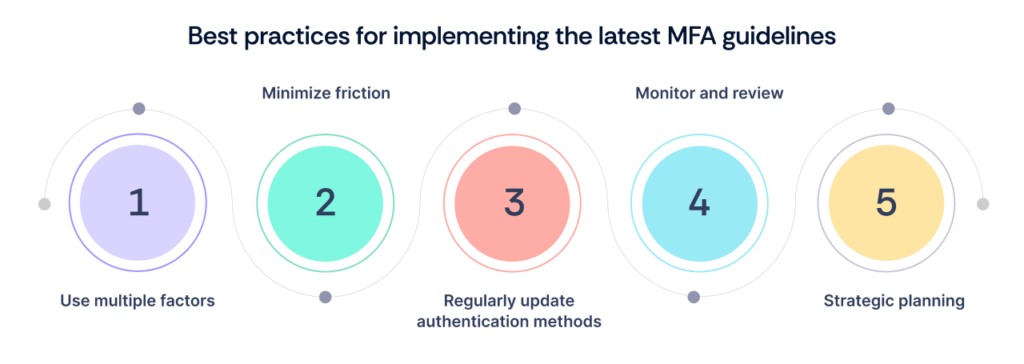
To effectively implement MFA, organizations should follow these best practices:
- Use multiple factors: Combine different types of authentication factors—something you know (like a password), something you have (like a token), and something you are (like biometrics)—to enhance security.
- Minimize friction: Strive for a user-friendly experience by reducing the number of steps required for authentication while maintaining strong security measures.
- Regularly update authentication methods: Keep pace with technological advancements by regularly updating authentication methods to ensure they remain effective.
- Monitor and review: Continuously monitor authentication attempts and review any suspicious activity to maintain security vigilance.
- Strategic planning: Implementing sophisticated MFA measures requires careful planning to ensure effectiveness and operational efficiency. Key considerations include:
- Allocate budget and resources: Allocate sufficient budget and resources for MFA implementation, taking into account infrastructure upgrades and ongoing maintenance costs.
- Foster employee engagement: Foster successful adoption through comprehensive training and communication efforts to promote understanding and compliance with new security measures.
- Balance security and user experience: Ensure that stringent security protocols do not disrupt business operations or impede productivity. Striking the right balance will help organizations transition from traditional methods like passwords and tokens to more secure authentication solutions such as FIDO2 and biometrics.
- User-centric design: Implement MFA solutions that are intuitive and easy to use to encourage user adoption.
- Contextual authentication: Employ risk-based authentication methods that adjust security measures based on user behavior, location, and device.
- Feedback mechanisms: Enable users to provide feedback on the MFA process to identify pain points and areas for improvement.
By focusing on these best practices and guidelines, organizations can maximize the effectiveness of their MFA measures while minimizing disruption to daily operations.
Also read: Top 15 PCI DSS Compliance Software
Top 15 PCI DSS Compliance Software
Wrapping up
The MFA guidelines serve as a crucial roadmap for organizations striving to bolster their defenses against evolving threats. MFA emerges as a cornerstone in this defense strategy, from phishing-resistant solutions like FIDO2 devices to strategic implementation considerations.
Organizations must prioritize strategic planning, employee engagement, and operational efficiency in alignment with these guidelines. Balancing security measures with business objectives ensures seamless MFA adoption without compromising productivity.
For tailored MFA solutions aligned with the new guidelines, Scrut offers advanced authentication technologies designed to safeguard your organization’s digital assets. Contact Scrut today to fortify your cybersecurity defenses.
Frequently Asked Questions
What is Multi-Factor Authentication (MFA), and why is it important?
MFA is a security measure that requires users to provide two or more verification factors to gain access to a system. These factors typically include something the user knows (like a password), something they have (like a smartphone), or something they are (like a fingerprint). MFA is crucial for enhancing security because it adds an extra layer of protection, making it more difficult for unauthorized users to access sensitive data or systems, even if they have obtained login credentials.
What are the common methods used in MFA implementation?
Common methods of MFA implementation include SMS codes, authenticator apps (like Google Authenticator or Authy), biometric verification (such as fingerprint or facial recognition), hardware tokens, and email verification. Each method offers varying levels of security and usability, and the choice often depends on the specific needs and preferences of the organization or individual.
How do the new MFA guidelines differ from previous recommendations?
The new MFA guidelines may differ from previous recommendations in terms of emphasizing the importance of using more secure authentication methods, such as hardware tokens or biometric verification, over less secure methods like SMS codes. Additionally, they may include updated best practices for implementing MFA across different platforms and devices, as well as recommendations for addressing emerging threats and vulnerabilities.
What industries or sectors benefit most from adopting MFA?
Industries or sectors that deal with sensitive information, such as finance, healthcare, and government agencies, benefit the most from adopting MFA. However, MFA is increasingly becoming a standard security practice across all industries due to the growing prevalence of cyber threats and the need to protect digital assets and user data from unauthorized access.





































