CMMC automation guide: How to stay audit-ready every day

Within the Defense Industrial Base (DIB), the integrity of Controlled Unclassified Information (CUI) is not merely a policy goal; it is the bedrock upon which critical national security cooperation rests. This foundational requirement has been formalized by the Department of Defense (DoD) through CMMC 2.0, establishing mandatory and verifiable DoD contractor requirements designed to ensure thorough CUI protection. To fully appreciate the compliance expedition ahead, we must recognize its scale: achieving Level 2 mandates the robust implementation of the 110 security controls derived from NIST SP 800-171.
A detailed look into the compliance journey reveals a critical vulnerability in traditional practices. Organizations relying on purely manual evidence gathering, configuration checks, and remediation cycles face a constant drag on efficiency. This inherent sluggishness causes compliance efforts to be periodic rather than persistent, leading directly to potential penalties, delays, and a problematic drift in the required Supplier Performance Risk System (SPRS) score. Without real-time visibility, organizations risk being secure only when they prepare for an audit, failing the DoD’s expectation of continuous assurance.
This crucial gap necessitates a strategic shift toward CMMC automation. Tools like Scrut allow contractors to move beyond the manual scramble. By automating continuous monitoring and evidence collection, CMMC automation transforms the complexity of DoD contractor requirements into manageable, real-time metrics. This not only reinforces superior CUI protection but also ensures that the organization maintains constant audit readiness, resulting in a reliable and stable SPRS score under the demanding framework of CMMC 2.0.
What does CMMC automation mean
CMMC automation is the strategic use of integrated software platforms to continuously monitor security configurations, automatically collect compliance evidence, map that evidence directly to CMMC 2.0 practices, and streamline remediation efforts, ensuring perpetual audit readiness.
This technological approach represents the frontier where security operations meet regulatory requirements, transforming compliance from a periodic burden into an integrated, real-time organizational function.
CMMC automation encompasses several essential, interconnected capabilities:
1. Automated evidence collection and log collection
Rather than relying on personnel to manually access disparate systems for security reports and screenshots, automation tools continuously connect to cloud environments, endpoints, and existing security stacks. They perpetually gather and organize necessary artifacts, logs, and configuration data in the background, fulfilling the requirement for automated evidence collection.
2. Security control alignment and mapping
The system automatically correlates the collected data directly to specific CMMC 2.0 practices and controls. This direct mapping ensures thorough and verifiable security control alignment, confirming that every security measure serves as proof for the compliance posture.
3. Continuous monitoring and ticket syncing
Through persistent, continuous monitoring, the platform identifies any deviation or drift from the required security baseline immediately. If a control fails, for instance, a critical access setting is changed, the system automatically triggers an alert and syncs a remediation ticket to platforms like Jira or ServiceNow, initiating corrective action without delay.
4. Policy automation
Beyond mere data collection, sophisticated automation aids in policy automation, which involves ensuring that underlying security policies are consistently enforced across the technological infrastructure without the need for constant human oversight.
5. Continuous readiness
The collective result of these functions is true continuous readiness, offering an up-to-the-minute, defensible view of the compliance status for systems protecting CUI.
It is crucial to differentiate genuine CMMC automation from "semi-manual tool usage." True automation involves zero-touch data handling: the platform integrates, collects, maps, flags, and initiates remediation autonomously.
Semi-manual usage, however, merely generates a report or dashboard, still requiring compliance teams to manually interpret the data, chase down evidence, and manually update the system of record. CMMC requires annual affirmations of continuous compliance and the retention of evidence.
Why automation matters for CMMC 2.0
The new CMMC 2.0 framework imposes compliance requirements that manual methods cannot sustain. The CMMC Final Rule solidifies cybersecurity as a contractual necessity, introducing structural and temporal obligations that mandate a shift toward automated assurance.
The critical pressures demanding automation
Contractors must navigate several compounding pressures that challenge traditional, periodic compliance efforts:
- The requirement for annual affirmations: While Level 2 organizations benefit from a 3-year assessment cycle, the DoD requires senior-level officials to submit annual affirmations certifying the organization’s continued compliance. This commitment effectively turns compliance into a daily operational obligation. Relying on sporadic manual checks during this long interval inevitably leads to compliance drift, where control configurations subtly misalign, creating severe risk for the affirming official.
- The constraint on POA&M reduction: The CMMC Final Rule severely limits the use of Plans of Action and Milestones (POA&Ms). Non-critical deficiencies can be conditionally accepted for up to 180 days, but critical controls must be implemented at the time of assessment. This tight deadline necessitates rapid POA&M reduction, which is infeasible if remediation cycles are slow, manual, and reliant on human coordination.
- The real-time threat environment: The protection of CUI demands continuous diligence. Waiting for a scheduled assessment to uncover a vulnerability leaves a significant window for exploitation, directly opposing the DoD’s goal of strengthening the Defense Industrial Base against advanced threats.
Automation: The solution for continuous assurance
CMMC automation serves as the necessary mechanism to manage these structural pressures. It bridges the gap between the mandated 3-year assessment cycle and the requirement for annual affirmations by providing continuous, verifiable data:
- Reduced human effort and eliminated blind spots: Automation drastically reduces the manual time and staff resources required for compliance maintenance by continuously monitoring security controls and collecting evidence. It actively eliminates the blind spots that facilitate compliance drift, guaranteeing control settings are implemented and enforced across all systems in scope.
- Accelerated POA&M reduction: Automation platforms, such as Scrut, enable immediate gap analysis by automatically flagging non-compliant controls and integrating with ticketing systems to initiate corrective action. This streamlines remediation, facilitating the swift POA&M reduction critical for both conditional and final certification.
- Enabling daily audit readiness: Ultimately, automation ensures that compliance is persistent, not periodic. This continuous posture provides the technical and operational assurance required for the senior official to confidently submit the annual affirmations of compliance, effectively mitigating the risks associated with non-compliance under the CMMC Final Rule.
Key areas where automation helps
The tangible benefit of CMMC automation is the creation of measurable operational improvements across core security domains. Automation transforms controls that are traditionally slow and resource-intensive into continuous, high-fidelity security functions.
Automated system discovery and management
Compliance with CMMC requires a precise understanding of the scope, including every system that processes, stores, or transmits CUI. Automation addresses this foundational need through two functions:
- Automated asset and system inventory: Automation platforms execute continuous asset discovery, automatically identifying and categorizing all in-scope hardware, software, cloud environments, and configuration settings. This constant synchronization eliminates blind spots and ensures that the organization’s System Security Plan (SSP) is always aligned with the real-world operational environment.
- Log and audit trail aggregation: Automation centralizes and aggregates logs and audit trails from diverse sources. This continuous aggregation supports CMMC controls related to auditing and monitoring, ensuring that the necessary evidence is always present for incident response and forensic analysis, a non-negotiable requirement for Level 2 maturity.
Continuous assurance and risk management
Automation replaces manual, periodic checks with persistent, automated controls over personnel and third-party risk:
- Continuous access and privileged review cycles: Managing user permissions is critical for protecting CUI. Automation transforms the burdensome annual manual check into continuous access reviews. The system automatically flags any changes to user roles or privileged access, ensuring that permissions remain minimally necessary and compliant with the principle of least privilege.
- Vendor monitoring and workflow automation: Compliance is not limited to the primary contractor; it extends to the supply chain. Automation enables proactive vendor risk management by integrating with third-party assessment tools. This allows for continuous monitoring of key supplier certifications and the automated creation of necessary remediation workflows if a vendor’s security posture changes.
Proactive threat mitigation
A key strength of automation is its ability to identify and address security flaws faster than manual processes:
- Automated vulnerability detection and tracking: Automation platforms integrate with security scanners to execute continuous vulnerability management. The system automatically imports vulnerability data, maps it directly to the relevant CMMC controls, prioritizes risks based on context, and tracks the status of patches and remediation efforts across the entire asset base.
- Evidence collection tied to controls: The final, overarching benefit is the continuous generation of audit-ready evidence. Every automated function, from asset discovery to vulnerability management, is directly mapped to a specific CMMC control. This linkage ensures that when an auditor asks for proof, the evidence is instantaneously available, eliminating the pre-assessment scramble and guaranteeing true daily readiness.
How automation strengthens your SPRS score
The SPRS scoring system, which tracks the required NIST SP 800-171 self-assessment score, serves as a mission-critical indicator of a contractor’s compliance status for the DoD. A reliable, defensible score is paramount for both contract eligibility and maintaining the integrity of the cyber posture. CMMC automation directly strengthens this score by ensuring its accuracy, consistency, and defendability.
Ensuring honest, evidence-backed scoring
The SPRS score is derived directly from an organization's implementation of the 110 security requirements outlined in NIST SP 800-171. Under manual compliance methods, calculating this score often relies on periodic documentation and self-reporting, which can be vulnerable to human error or score inflation.
Automation resolves this by enforcing evidence-backed scoring:
- Real-time assessment verification: Automation platforms continuously monitor the infrastructure, collecting direct, verifiable evidence, such as logs, configuration files, and system settings, for every NIST SP 800-171 requirement. This evidence proves the requirement is actually implemented and operating effectively, transforming the score calculation from a subjective exercise into an objective, automated process.
- Mitigation of score drops: Manual processes inevitably lead to compliance drift, causing sudden, unexpected score drops when a control lapses. Automation provides real-time updates on requirement status, instantly flagging any deficiency. This immediate visibility allows for remediation before the negative score deduction is formalized, ensuring the contractor’s SPRS submission is always accurate and optimized.
Defending the score during assessment
The ultimate verification of the SPRS scoring is the Certified Third-Party Assessment Organization (C3PAO) assessment for CMMC Level 2. Automation eliminates the discrepancies and the scramble that can compromise this process:
- Consistency across cycles: Since the automated system maintains continuous real-time updates and evidence collection, the security posture presented to the C3PAO during the formal assessment is identical to the posture reported in the initial SPRS submission. This consistency eliminates surprises and builds immediate credibility with the assessor.
- Defensible evidence package: During the assessment, automated platforms provide a complete, traceable package of evidence-backed scoring. Auditors can trace every point assigned to the NIST SP 800-171 requirements back to its source, a log, a configuration, or an access review, without manual intervention. This dramatically speeds up the auditing process and ensures the reported SPRS scoring is entirely honest and transparent, avoiding the severe risks associated with score inflation.
What to look for in a CMMC automation platform
Selecting the correct CMMC automation platform is a critical investment that determines the long-term efficiency and defensibility of your compliance program. The ideal tool must function as a comprehensive operating system for compliance, moving far beyond simple documentation and providing continuous, automated assurance. A formal review should prioritize tools that meet the following checklist of operational capabilities:
Core automation and integration capabilities
The platform must eliminate manual intervention by providing seamless connectivity to your security ecosystem:
- Native integrations with core systems: Look for deep, native integrations with foundational technologies. This includes major cloud providers (AWS, Azure, GCP), endpoint security tools, identity and access management systems (IDAM), and ticketing platforms (Jira, ServiceNow). Effective integration ensures automated data flow without needing custom, brittle APIs.
- Automated evidence capture and mapping: The tool must continuously connect to these integrated systems to capture evidence (logs, configurations, policies). This collected data must then be automatically mapped directly to the 110 NIST SP 800-171 security requirements. A strong evidence library is the backbone of defensible compliance.
- Alerts for control drift: A key feature is the ability to send immediate, contextual alerts when a security setting or configuration drifts out of compliance with a CMMC practice. This proactive alerting mechanism is essential for mitigating risks before they become serious deficiencies.
Management, workflow, and security features
Beyond data collection, the platform must simplify the governance and organizational aspects of compliance:
- Clear dashboards showing control status: The platform must provide intuitive dashboards that offer a real-time, holistic view of the CMMC compliance status. These dashboards should clearly show which controls are implemented, which are failing, and the overall SPRS score, allowing senior management and compliance teams to assess risk at a glance.
- Policy, training, and vendor workflows: The platform should facilitate key organizational and third-party processes. This includes providing workflows for policy management, tracking employee security training completion, and automating the monitoring and management of vendor risk information and certifications.
- Role-based access controls: To protect the integrity of the data and maintain segregation of duties, the platform must support robust role-based access (RBAC). This ensures that only authorized personnel can view, edit, or approve evidence and documentation, fulfilling CMMC's own access control requirements.
- Secure data handling practices: Given that the platform will house sensitive evidence and system configurations, it must demonstrate secure data handling. Verify the platform's own security posture, including data encryption (at rest and in transit) and its commitment to industry-leading security certifications.
Common myths about CMMC automation
As organizations transition to CMMC automation, several pervasive CMMC misconceptions often cloud the understanding of its role. It is vital to clarify these myths, recognizing that automation is a powerful facilitator of compliance, not a magic replacement for all security governance.
Practical steps to introduce automation in your environment
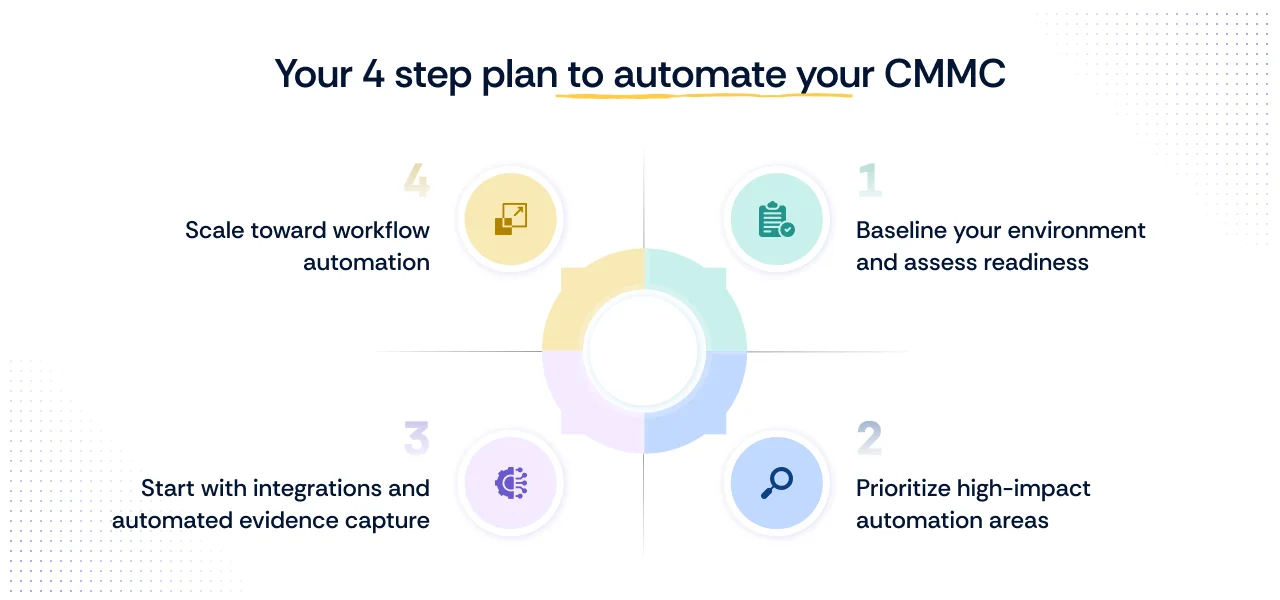
Introducing CMMC automation into a complex environment requires a structured and deliberate approach. It is not an overnight task, but rather an implementation roadmap that strategically transitions your organization from manual, periodic checks to continuous, automated compliance. This approach ensures maximum efficiency while meeting stringent DoD contractor requirements.
Step 1: Baseline your environment and assess readiness
Before deploying any tools, a clear understanding of your current posture is necessary for automation readiness.
- Define scope and baselines: Clearly identify all systems, assets, and boundaries that process, store, or transmit CUI. This is the official scope that automation will cover.
- Establish a manual baseline: Conduct an initial, manual self-assessment to determine your current SPRS score and generate a working POA&M. This provides the starting point against which automation's effectiveness will be measured.
- Identify automation gaps: Map the 110 NIST SP 800-171 requirements to your current security tooling to determine which controls are already partially met and which require new evidence sources.
Step 2: Prioritize high-impact automation areas
Automation efforts should first target controls that are the most labor-intensive or carry the highest risk of compliance drift.
- Evidence collection: Prioritize the controls that require frequent, tedious artifact collection (e.g., system configuration checks, log reviews). Automating these provides immediate and measurable relief to compliance teams.
- High-risk controls: Focus on controls prone to misconfiguration, such as those related to access, logging, and monitoring, as failures here carry the highest point deductions in SPRS scoring.
Step 3: Start with integrations and automated evidence capture
The first practical deployment phase is establishing the continuous data flow necessary for continuous monitoring.
- Integrate foundational tools first: Begin by establishing integrations with your most critical sources of truth: your cloud service provider (CSP) environments, identity provider (IdP), and ticketing system.
- Automate evidence first: Configure the platform to perform continuous automated evidence collection from these sources. Ensure the platform successfully pulls data, maps it to the relevant CMMC practices, and creates a central, automated evidence library. This provides the technical foundation for continuous readiness.
Step 4: Scale toward workflow automation
Once evidence is flowing reliably, scale the automation to cover high-volume organizational workflows.
- Access and vendor workflows: Introduce automation for continuous access reviews and privileged role-based access management. Next, integrate the platform with vendor monitoring tools to manage supply chain risk efficiently.
- Vulnerability management: Automate vulnerability management workflows by integrating vulnerability scanners. The platform should automatically track the remediation status of critical flaws and link them to the relevant CMMC controls, ensuring rapid POA&M reduction.
- Monitor and refine: Continuously monitor the automated system's reports and dashboards. Use the real-time updates to refine remediation steps and ensure your organization remains continuously aligned with DoD contractor requirements for CUI protection.
How Scrut supports CMMC automation
When you bring Scrut into your CMMC journey, you get automation that works quietly in the background while giving you a clear view of what’s happening. You can connect your cloud, identity tools, endpoints, ticketing systems, and training platform through 100+ integrations. Scrut then pulls evidence automatically, maps it to NIST SP 800-171, and all CMMC practices using its library of more than 1500+ pre-mapped controls, and updates your control status every 24 hours with insights from over 400 automated tests.
You don’t have to chase screenshots or track training by hand. Scrut shows whether each user has completed required CMMC training, flags missing attestations, and keeps your policies current with around 200 expert-built templates and an advanced AI-driven policy builder. You also get automated alerts for control drift, vendor risk workflows, access reviews, and vulnerability findings. All of this lives in one dashboard, so you always know your actual readiness before the assessor walks in.
Frequently asked questions about CMMC automation
What is the primary goal of CMMC automation?
The primary goal is to ensure continuous readiness for CMMC 2.0 and sustained CUI protection. Automation transforms compliance from a periodic effort before an assessment into a dynamic, day-to-day operational state by constantly collecting evidence.
How does CMMC automation affect my SPRS score?
It strengthens your SPRS scoring by enabling evidence-backed scoring. Automation provides real-time updates on control status, eliminating compliance drift and ensuring your reported score is accurate and defensible during a C3PAO assessment.
Does CMMC automation replace the need for my compliance team?
No. Automation eliminates the manual labor of evidence gathering and monitoring, but it does not replace human oversight. Compliance teams are still required to define policies, interpret data, and submit final annual affirmations.
What are the most critical features to look for in an automation platform?
Key features include native integrations with your cloud and identity systems, a strong evidence library, automated evidence collection mapped directly to NIST SP 800-171, and clear dashboards showing control status.
What are annual affirmations, and how does automation help?
Annual affirmations are the commitment by a senior official (required during the 3-year assessment cycle) that the organization remains continuously compliant. Automation provides the constant monitoring and evidence required to confidently certify compliance year-round, mitigating the risk of non-compliance.
Can automation help me with POA&M reduction?
Yes. Automation accelerates POA&M reduction by instantly identifying failed controls, initiating remediation tickets in real-time, and tracking the fix status. This drastically reduces the time required to resolve deficiencies and meets the strict 180-day deadline imposed by the CMMC Final Rule.


















