The cybersecurity imperative: Navigating the CMMC 2.0 assessment for the DIB

Within the critical realm of the Defense Industrial Base (DIB), immediate and verifiable cyber resilience is paramount. The Department of Defense (DoD) introduced the Cybersecurity Maturity Model Certification (CMMC) 2.0 not merely as guidance, but as a critical contractual mandate. Its core purpose is direct: to ensure every organization entrusted with Controlled Unclassified Information (CUI) possesses the security measures to protect it.
For companies preparing for the Foundational (Level 1) or Advanced (Level 2) tiers, the CMMC assessment is the definitive proving ground. It is the mandatory process, whether via self-assessment or a Third-Party Assessment Organization (C3PAO), to officially prove your security controls are implemented and operating effectively. This journey is not an insurmountable hurdle, but a clear, practical expedition that requires precision. Understanding the assessment process is the essential first step to achieving compliance and securing your future DoD contracts.
This guide will serve as your essential map, navigating the precise assessment steps, exposing common preparation pitfalls, and illustrating how modern compliance solutions can automate and accelerate your journey to CMMC certification, detailing the critical investment in time and resources required.
What is a CMMC assessment?
The CMMC assessment is the Department of Defense's systematic methodology for verifying that an Organization Seeking Certification (OSC) has successfully implemented the requisite security controls to safeguard sensitive government information. It is the mandatory validation step in the journey, confirming that the controls are not just theoretical but operational within the OSC's environment. This rigorous scrutiny provides the DoD with the necessary assurance that the DIB is protecting Federal Contract Information (FCI) and CUI commensurate with the risk.
The assessment path diverges significantly between the CMMC levels. For Level 1 (Foundational), which covers FCI, the assessment is typically an annual self-assessment performed by the OSC itself, with compliance affirmed by a senior official and documented in the Supplier Performance Risk System (SPRS). This path provides a straightforward, repeatable process for establishing basic cyber hygiene.
For Level 2 (Advanced), which mandates protection for CUI and aligns with the 110 requirements of NIST SP 800-171, the compliance burden escalates. While some non-prioritized CUI programs allow for an annual self-assessment, prioritized acquisitions require a rigorous triennial third-party assessment conducted by an authorized CMMC C3PAO.
These C3PAOs function as independent arbiters, systematically examining not only the cybersecurity practices, the specific technical configuration and implementation of controls, but also the organizational processes that ensure their continuous maintenance and effectiveness. This comprehensive, three-year cadence of assurance is designed to verify persistent, not merely temporary, cyber maturity across the DIB.
The CMMC assessment process (step-by-step)
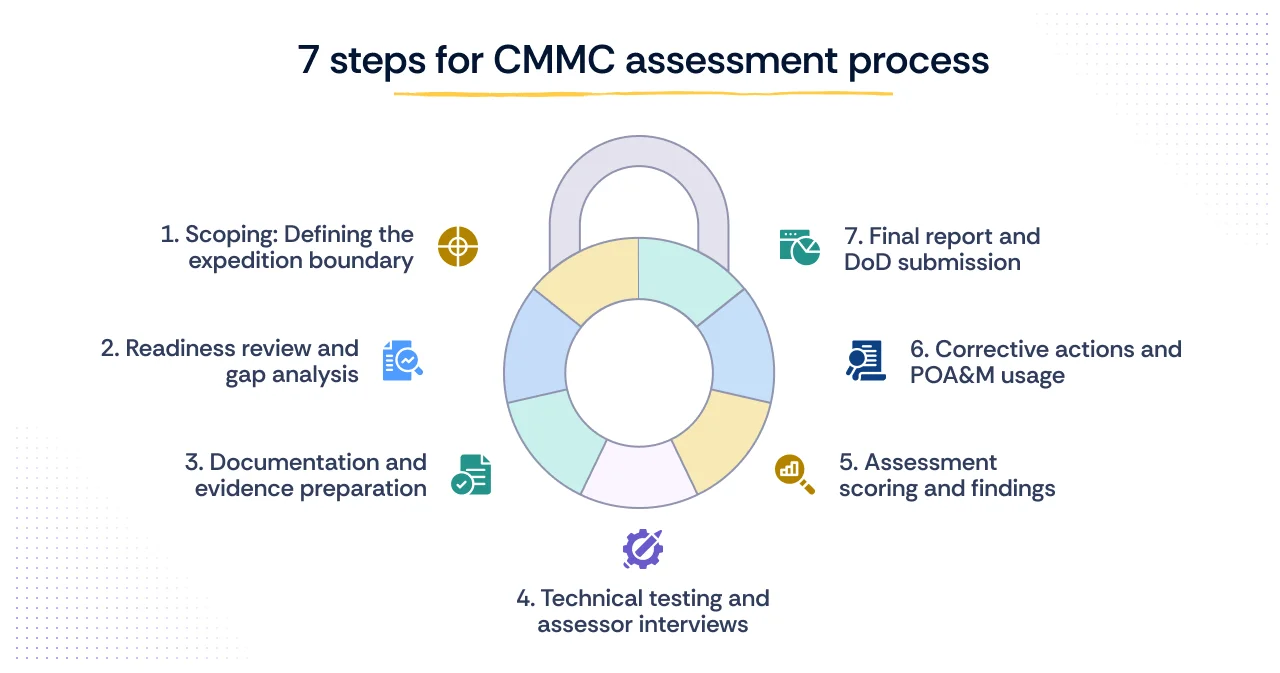
The CMMC assessment is a phased expedition designed to systematically verify an OSC’s security posture. For Level 2, this process culminates in the CMMC C3PAO evaluation, which follows a clear and rigorous methodology.
1. Scoping: Defining the expedition boundary
The journey begins by precisely defining the CUI environment, also known as the assessment scope. This critical, pre-assessment step identifies all organizational assets, personnel, and systems that store, process, or transmit CUI. By isolating the environment, the OSC can limit the application of the 110 NIST SP 800-171 requirements only to those in-scope assets, making the preparation more manageable and cost-effective.
2. Readiness review and gap analysis
Prior to engaging the C3PAO, the OSC must conduct a thorough readiness review or gap analysis against the CMMC requirements. This internal self-assessment is essential for minimizing the risk of failure by actively pinpointing deficiencies and allowing for timely, pre-assessment remediation. This proactive step saves significant resources and time during the formal assessment phase.
3. Documentation and evidence preparation
Following the gap analysis, the System Security Plan (SSP) must be finalized, thoroughly documenting how each control is met within the scoped environment. All essential evidence, including screenshots, policy documents, audit logs, and network diagrams, must be meticulously collected and organized. This evidence serves as the primary artifact base that the assessor will examine to confirm the implementation of CMMC controls.
4. Technical testing and assessor interviews
The official assessment phase focuses on validation. The C3PAO team utilizes three primary methods: Examine (reviewing documented evidence), Interview (speaking with subject matter experts to confirm procedures), and Test (technically validating the implementation and operation of security controls). This step determines if practices are not only documented but are effectively embedded within daily operations.
5. Assessment scoring and findings
For each security practice, the assessor assigns a finding of MET (compliant) or NOT MET (deficient). This detailed scoring process provides the OSC with a clear report on its standing against the required maturity level. Failure to meet all required practices often results in a request for corrective action before certification can be granted.
6. Corrective actions and POA&M usage
If the OSC meets a minimum threshold of compliance, they may utilize a Plan of Action and Milestones (POA&M) to document corrective actions for certain allowable deficiencies. Crucially, the POA&M has a strict 180-day deadline for completion and cannot be used for high-weighted, critical controls. This option offers a limited window for remediation without restarting the entire assessment.
7. Final report and DoD submission
Upon successful completion of all required practices or the closeout of all allowed POA&Ms, the C3PAO compiles the final assessment report and submits it for quality assurance review. The final certification status is then uploaded to the DoD's Enterprise Mission Assurance Support Service (eMASS) and registered in the SPRS, confirming the OSC’s eligibility for future DoD contracts.
What assessors look for (the inspection checklist)

For organizations pursuing CMMC Level 2, the C3PAO assessment is the final expedition to determine whether the security practices protecting CUI are not just documented, but verifiably operational. The assessor’s task is to validate compliance with all 110 requirements within the NIST SP 800-171 framework. This inspection checklist spans three critical dimensions of your security posture.
1. The documentation trail
The first point of scrutiny is the alignment of organizational policies, procedures, and practices. Assessors will meticulously examine the SSP to ensure it comprehensively addresses all 110 requirements and accurately describes your system boundary. They look for evidence that your documented policies, governing areas like access management and vendor risk management, are consistent with the actual day-to-day procedures performed by your personnel. A clear, well-maintained documentation trail is often the easiest win or the most common point of failure.
2. Technical and operational evidence
Beyond documentation, assessors investigate the tangible implementation of security controls across the CUI environment. This involves deep dives into several key areas:
- System integrity: Reviewing logs, continuous monitoring outputs, and incident response readiness plans. They will seek proof that you can detect, contain, and report security events involving CUI.
- Asset and configuration control: Validating the completeness of your asset inventory and verifying that system configurations meet established security baselines, including secure engineering practices and timely patching procedures.
- Data protection: Examining the implementation of critical security functions such as encryption for CUI at rest and in transit, and the viability of your backup and recovery solutions.
- Access management: Scrutinizing user provisioning, access review records, and controls enforcing separation of duties and the principle of least privilege.
3. Validation through triangulation
The C3PAO validates these elements using a process of triangulation, ensuring confidence in the findings. They utilize three primary techniques to establish control as MET:
- Examine: Reviewing documentation, policies, procedures, and evidence (artifacts).
- Interview: Speaking with personnel and subject matter experts (SMEs) to confirm understanding and execution of security practices.
- Test: Technically validating the implementation and operation of security controls, often through observation or requesting a live demonstration of a control.
Successful organizations ensure that their security stance is defensible across all three validation methods, making the assessment less of a surprise audit and more of a predictable, evidence-based review.
Common reasons for CMMC failure and how to prevent them
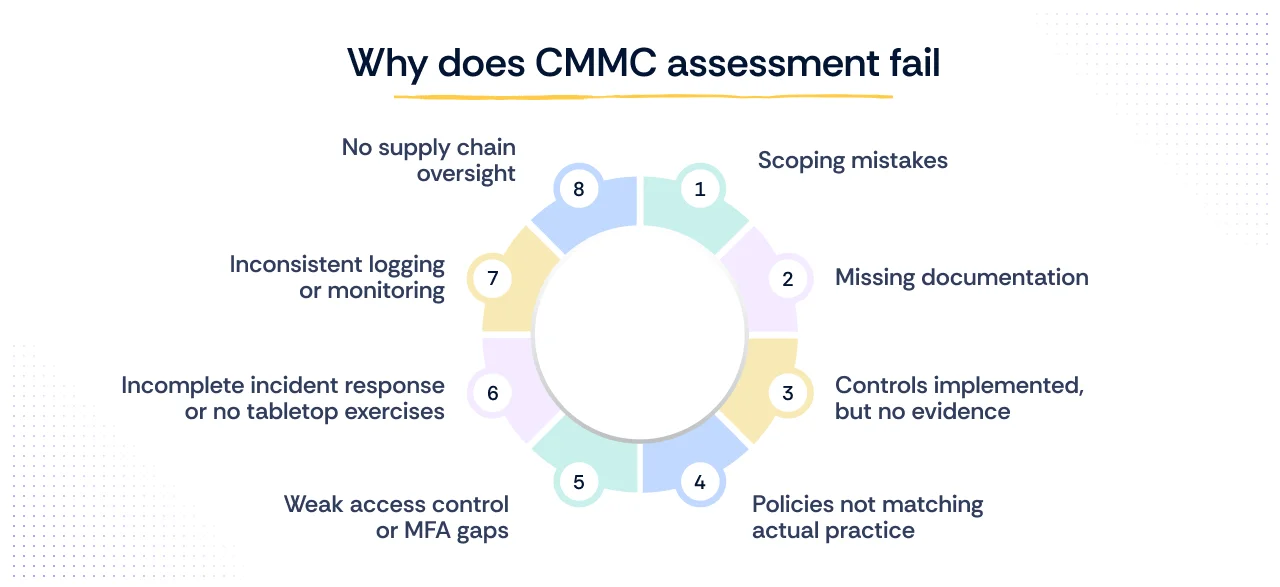
The pursuit of CMMC certification is often undermined not by a lack of intent but by critical missteps during the preparation phase. Organizations must recognize that the assessment is less about finding flaws and more about verifying a complete, mature security ecosystem. We now examine these common navigational hazards in detail, providing proactive prevention strategies for each to ensure your expedition to CMMC compliance remains on course.
1. Scoping mistakes
This is the single largest reason for immediate failure. Under-scoping, failing to include all systems and devices that handle CUI, creates security gaps that are fatal to certification. Conversely, over-scoping unnecessarily adds cost and complexity by including non-CUI systems in the demanding Level 2 assessment.
To prevent this: Conduct a verifiable asset inventory and define the SSP’s clear CUI boundary early in the process, ensuring all components are accounted for.
2. Missing documentation
Assessors frequently find instances where the SSP is vague, incomplete, or generic. Without clear, comprehensive documentation, the OSC fails to demonstrate that it has systematically planned for compliance across all 110 requirements.
To prevent this: Centralize all documentation, utilizing established templates for the SSP and policies, and ensure all documents are reviewed and signed by management.
3. Controls implemented, but no evidence
The mantra of the assessment is "prove it." Even if a control is technically running, the inability to produce readily available, timely evidence of its operation, such as current access review records or configuration snapshots, results in a "NOT MET" finding.
To prevent this: Implement continuous monitoring and automated evidence collection for all security controls, ensuring artifacts are consistently generated and immediately retrievable.
4. Policies not matching actual practice
This represents a crucial disconnect between governance and execution. If documented policies governing areas like employee onboarding/offboarding or data handling do not accurately reflect the organization's unique processes, the assessor cannot validate operational maturity.
To prevent this: Conduct internal audits and validate policies with operational teams annually, ensuring written procedures match the security reality on the ground.
5. Weak access control or MFA gaps
Operational deficiencies often center on high-impact controls. Failure to implement robust access control or to apply Multi-Factor Authentication (MFA) across all required accounts signals a critical vulnerability in the primary gate to CUI, resulting in a low score.
To prevent this: Enforce MFA everywhere, especially for remote and privileged access, and perform rigorous, documented access reviews quarterly.
6. Incomplete incident response or no tabletop exercises
An effective program requires preparedness. Failure to maintain an actionable incident response plan, or neglecting to validate it through regular tabletop exercises, shows a lack of operational maturity required for sustained protection of CUI.
To prevent this: Develop a comprehensive, written plan and conduct mandatory, recorded tabletop exercises biannually to test team coordination and communication.
7. Inconsistent logging or monitoring
Assessors look for proof of continuous vigilance. Inconsistent logging, which lacks necessary fidelity or retention, hinders the ability to detect and investigate security events, preventing the demonstration of effective continuous monitoring practices.
To prevent this: Standardize logging formats and retention policies across all in-scope systems, ensuring logs are protected from tampering and actively reviewed daily.
8. No supply chain oversight
A significant oversight is the neglect of third-party risk. If an OSC’s own security posture is dependent on a vendor who is non-compliant or whose risk is unmanaged, the entire CUI environment remains vulnerable. Vendor compliance must be assessed and monitored.
To prevent this: Require all relevant vendors to provide CMMC certification or equivalent proof of compliance, and integrate vendor risk management into your compliance program.
CMMC assessment timeline and costs
The CMMC assessment journey represents a significant commitment. To clearly chart the expected investment, the timeline and cost variables for the Foundational (L1) and Advanced (L2) levels are detailed in the comparison table below.
Achieving CMMC readiness with Scrut
The complexities of the CMMC assessment, particularly the recurring burden of evidence and documentation for L2, can overwhelm even the most prepared OSC. Scrut is the essential tool for the modern compliance explorer, transforming assessment preparation from a chaotic manual exercise into a precise, continuous operation.
Scrut fundamentally solves the evidence gap. It directly integrates with your cloud and security systems to facilitate continuous evidence collection, logging, and monitoring verification. This replaces manual screenshot collection, ensuring that evidence is always current and immediately retrievable by the C3PAO. Furthermore, Scrut provides version control of documents, such as the SSP, ensuring policies are always the latest version and consistently mapping practices to verifiable artifacts.
By providing a centralized compliance workspace, Scrut significantly reduces manual errors and scoping issues. It clearly defines the in-scope environment and automatically checks for control implementation across that boundary. This proactive, always-on readiness significantly lowers the cost and stress of the triennial assessment, ensuring the OSC is perpetually prepared for recurring assessments and audit scrutiny with minimal internal effort.
Ready to reduce your L2 preparation time from months to weeks and secure your passage into the Defense Industrial Base (DIB)?

CMMC assessment frequently asked questions
1. What is the key distinction between CMMC Level 1 and Level 2 assessments?
Level 1 (Foundational) requires an annual self-assessment and focuses on protecting FCI (Federal Contract Information). Level 2 (Advanced) requires a triennial third-party assessment by a C3PAO (CMMC Third-Party Assessment Organization) for critical programs, and focuses on protecting the more sensitive CUI (Controlled Unclassified Information).
2. What is the single biggest reason companies fail a CMMC assessment?
The largest failure point is scoping mistakes. Organizations frequently under-scope by excluding systems that process, store, or transmit CUI, which creates non-compliant security gaps that are fatal to certification.
3. How long does it typically take to prepare for a CMMC Level 2 assessment?
Preparation for Level 2 compliance usually takes between 6 and 18 months, depending on an organization's initial security maturity. The formal C3PAO assessment phase itself only takes a few weeks.
4. What is the role of evidence in a CMMC assessment?
Evidence is crucial. Assessors validate compliance using three methods: Examine, Interview, and Test. Even if a control is implemented, failure to produce readily available, documented evidence (like current audit logs or configuration records) results in a "NOT MET" finding.
5. Can a Plan of Action and Milestones (POA&M) be used to pass a CMMC assessment?
A POA&M can be used for conditional certification in Level 2 to address certain allowable deficiencies, but it cannot be used for high-weighted, critical controls. Any authorized POA&M must be closed out within a strict 180-day deadline.
6. How can compliance automation platforms like Scrut help with the CMMC process?
Automation directly addresses the most common failure points by providing continuous evidence collection, ensuring documentation version control (for the SSP), and reducing manual errors to achieve perpetual readiness for the triennial C3PAO assessment.


















