SOC 2 vs ISO 27001: Which Compliance Framework Should You Choose?

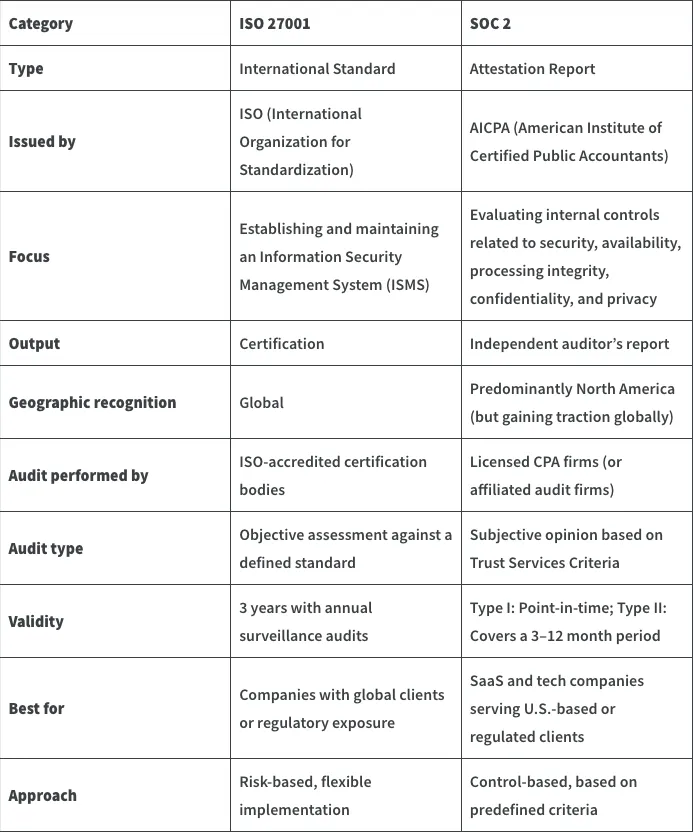
ISO 27001 and SOC 2 are often seen as two sides of the same security coin both widely respected, both audit-driven, but fundamentally different in scope, structure, and recognition. One is a global certification for your security management system. The other is a U.S.-centric attestation report focused on the effectiveness of your controls.
If you're wondering which one to pursue, whether they can replace each other, or how they stack up side-by-side you're in the right place. This guide breaks down the key differences, similarities, mapping potential, and decision criteria for choosing between ISO 27001 and SOC 2 (or doing both). We'll also cover how Scrut supports each standard with features purpose-built for faster, smoother audits.
What are the differences between ISO 27001 and SOC 2?
What is SOC 2?
SOC 2 (System and Organization Controls 2) is a framework developed by the American Institute of Certified Public Accountants (AICPA) to assess how well an organization manages customer data based on five Trust Services Criteria: security, availability, processing integrity, confidentiality, and privacy. Unlike ISO 27001, SOC 2 doesn’t provide a certification — instead, it results in an attestation report issued by an independent auditor (usually a CPA firm).
The latest version of the SOC 2 criteria was updated in 2022, incorporating revisions to align with COSO’s 2013 framework and increasing emphasis on risk assessment and vendor management. Organizations can choose between Type I (a point-in-time review) and Type II (which evaluates control effectiveness over a period, usually 3–12 months).
Is it mandatory to be SOC 2 compliant?
No, SOC 2 is not legally mandatory. The best time to pursue SOC 2 is when your company starts selling to enterprise customers, particularly in the U.S. market, where it’s a common requirement in procurement checklists. Many startups aim for SOC 2 Type I shortly after launching their product, then progress to Type II within the next 6–12 months.
SOC 2 is not legally mandated, so there are no formal penalties for not having it. However, lacking a SOC 2 report can slow down sales, especially if prospects require assurance about your security controls. In some cases, it could be a deal-breaker. So, while the risk isn’t regulatory, it’s very real in terms of revenue and market access.

How to get SOC 2 compliant?
Achieving SOC 2 compliance involves a structured process that varies depending on the type of report — Type I or Type II — your organization pursues. Here’s an overview of the typical timeline, associated costs, and validity period:
Timeline:
- SOC 2 Type I: This report evaluates the design of your security controls at a specific point in time. The preparation and audit process typically spans 1 to 2 months, depending on your organization’s readiness and the complexity of your systems.
- SOC 2 Type II: This more comprehensive report assesses the operational effectiveness of your controls over a defined period, usually 3 to 12 months. Including preparation, the entire process can take 5 to 17 months.
Cost:
- SOC 2 Type I: Compliance costs generally range from $15,000 to $40,000, encompassing auditor fees, readiness assessments, and any tools or platforms used for automation.
- SOC 2 Type II: Due to its extended scope, costs typically range from $30,000 to $80,000, influenced by factors such as the observation period, audit scope, and organizational complexity.
Validity: SOC 2 reports do not have a formal expiration date; however, they are generally considered valid for 12 months from the date of issuance. To maintain credibility and meet client expectations, organizations often undergo annual audits to provide up-to-date assurance of their control environments.
By understanding these aspects, organizations can better plan and allocate resources to achieve and maintain SOC 2 compliance, thereby demonstrating their commitment to data security and operational excellence.
Who needs to be SOC 2 compliant?
SOC 2 is most commonly required by companies operating in or selling to the United States. It’s especially prevalent in B2B SaaS, cloud, and tech ecosystems, where enterprise clients expect third-party validation of a vendor’s security controls. While SOC 2 is gaining global recognition, it remains primarily a North American standard — so if you’re targeting U.S.-based customers or handling data on their behalf, it’s often considered table stakes.
In terms of industries, SOC 2 is particularly relevant for:
- SaaS and cloud service providers offering platforms that store or process customer data
- Fintech companies managing payment processing, customer identities, or transaction records
- Healthcare and healthtech platforms handling patient information (especially when HIPAA is in play)
- Legal tech, HR tech, and edtech providers entrusted with sensitive user data
- Managed service providers (MSPs) and vendors that plug into clients’ IT environments
In short, if your company offers a digital service and handles customer data — and especially if your customers are asking about your security controls — a SOC 2 report can serve as both a sales enabler and a trust signal.
What are the requirements of getting SOC 2 compliant?
SOC 2 requirements are built around the Trust Services Criteria developed by the AICPA. At a high level, these are the core areas your organization must address:
- Security (mandatory)
- Availability (optional)
- Processing Integrity (optional)
- Confidentiality (optional)
- Privacy (optional)
Within each of these criteria, SOC 2 requires you to implement and maintain controls aligned with five key components of internal control, based on the COSO framework:
- Control environment
- Risk assessment
- Information and communication
- Monitoring of controls
- Control activities
Unlike ISO 27001, SOC 2 doesn’t prescribe specific controls — it gives you flexibility in how you meet the criteria, but the effectiveness of those controls is assessed through an independent audit (either Type I or Type II).
Advantages of getting SOC 2 compliant:
- Widely accepted by U.S. enterprise buyers: A SOC 2 report is often a prerequisite in security reviews, making it easier to close deals with North American clients.
- Demonstrates operational maturity: It validates that your internal controls are not only well-designed but also functioning effectively over time (especially with Type II).
- Tailored to your environment: Unlike rigid certifications, SOC 2 allows flexibility in how you meet the Trust Services Criteria, making it easier to align with your existing processes.
Disadvantages of SOC 2:
- Limited global recognition: SOC 2 holds weight in the U.S., but organizations operating in Europe or Asia may find that clients prefer ISO 27001 instead.
- No formal certification: Since SOC 2 results in an attestation report — not a certificate — some stakeholders may view it as less authoritative than ISO 27001.
- Resource-heavy audit process: Especially for Type II, the audit requires ongoing evidence collection and control monitoring over several months, which can strain smaller teams.
What is the ISO 27001 standard?
ISO/IEC 27001 is an international standard that outlines the requirements for establishing, implementing, maintaining, and continually improving an Information Security Management System (ISMS). Published by the International Organization for Standardization (ISO) in collaboration with the International Electrotechnical Commission (IEC), it provides a systematic approach to managing sensitive company information — from customer data to internal records — and keeping it secure.
The most recent version of the standard, ISO/IEC 27001:2022, introduced updates to better align with today’s threat landscape, including more emphasis on risk treatment, performance evaluation, and control changes in Annex A (which now reflects ISO/IEC 27002:2022).
Is it mandatory to get ISO 27001 certification?
It’s important to note that ISO 27001 is not a legal requirement — but it can be a strong enabler for meeting regulatory obligations like GDPR, HIPAA, or DPDPA. While failing to get certified won’t land you in legal trouble, gaps in your security posture might. For instance, if a data breach occurs and your controls were found lacking, the financial and reputational consequences could be far worse than the cost of certification.
There are no formal penalty charges for not having ISO 27001 — because again, it’s voluntary. Many organizations pursue it to meet vendor due diligence requirements, improve their security posture, or expand into new markets. That said, it’s often expected — if not explicitly mandated — in sectors that deal with sensitive or regulated information.
How to get ISO 27001 standard certification?
Achieving ISO 27001 certification involves a structured process to establish, implement, and maintain an Information Security Management System (ISMS). The journey begins with defining the ISMS scope, conducting a risk assessment, implementing necessary controls, and documenting policies and procedures. Once the ISMS is operational, an accredited certification body conducts a two-stage audit to assess compliance.
Timeline: For small to mid-sized organizations, the certification process typically spans 3 to 6 months, depending on the existing security posture and resource availability. Larger or more complex organizations may require additional time to achieve readiness.
Cost: The total cost of ISO 27001 certification varies based on several factors, including organizational size, complexity, and the chosen certification approach. ISO 27001 costs can range from $15,000 to $60,000.
Validity: Once obtained, the ISO 27001 certificate is valid for three years. However, organizations must undergo annual surveillance audits to ensure continued compliance. At the end of the three-year cycle, a recertification audit is required to maintain the certification status.
By following this structured approach and considering the associated timelines and costs, organizations can effectively achieve and maintain ISO 27001 certification, demonstrating a robust commitment to information security.
Who needs the certification?
ISO 27001 isn’t tied to any single country — it’s a globally recognized standard. While SOC 2 is more commonly requested by U.S.-based companies, ISO 27001 tends to be the preferred (or sometimes required) framework in Europe, Asia-Pacific, the Middle East, and other regions where international operations or multi-jurisdictional compliance is a factor. It’s also widely accepted by multinational clients, especially those in regulated industries.
Some of the industries where ISO 27001 is most applicable include:
- Technology and SaaS companies (especially those handling customer data or offering cloud-based services)
- Finance and fintech, where data security is essential for compliance and trust
- Healthcare, particularly for aligning with privacy-focused regulations like HIPAA
- Legal and consulting firms that manage client-confidential information
- Manufacturing and critical infrastructure, where data protection impacts operations and supply chain resilience
In short, if your organization stores, processes, or transmits sensitive data — and especially if you’re selling to global enterprises — ISO 27001 is worth considering.
What are the requirements of ISO 27001?
ISO 27001:2022 outlines requirements across the following core areas:
- Context of the organization
- Leadership
- Planning
- Support
- Operation
- Performance evaluation
- Improvement
In addition to these clauses, organizations must also address:
- Annex A: A reference list of 93 controls grouped under 4 themes:
- Organizational controls
- People controls
- Physical controls
- Technological controls
These are the mandatory structural components defined in the main body of the ISO 27001 standard. Annex A helps you select which specific security controls are relevant, but the clauses above form the core of what the standard expects you to build and maintain as your ISMS.
Advantages of ISO 27001
- Recognized globally by customers and regulators: ISO 27001 certification signals that your organization follows best practices for information security — a key trust factor when working with international clients or entering new markets.
- Improves security posture through a structured approach: The standard helps you identify risks, implement controls, and continuously improve — making your security program proactive instead of reactive.
- Speeds up procurement and due diligence cycles: Many enterprise buyers prefer or require ISO 27001 as part of their vendor assessments, helping you close deals faster and with less friction.
Disadvantages of ISO 27001
- Time- and resource-intensive: Implementing ISO 27001 requires a dedicated team, process changes, and months of preparation — which can be a strain for smaller or fast-moving companies.
- Ongoing maintenance is non-negotiable: Certification isn’t a one-time task. Annual surveillance audits and continuous documentation upkeep are essential to stay compliant.
- May not align with regional expectations: In the U.S., especially for SaaS companies, prospects may prioritize SOC 2 over ISO 27001 — making the certification less impactful for sales if you’re focused solely on North American clients.
Which framework to choose for your company?
Choosing between ISO 27001 and SOC 2 comes down to who your customers are, where they’re based, and how they evaluate trust. If you’re selling to U.S.-based clients — particularly in SaaS, fintech, or cloud — SOC 2 is often the baseline they expect. But if your business spans multiple geographies or serves clients in Europe, Asia, or regulated sectors, ISO 27001 tends to carry more weight due to its international recognition.
Also worth noting: SOC 2 is not part of a larger umbrella framework, while ISO 27001 is part of the ISO/IEC 27000 family, which includes related standards like ISO 27002 (controls guidance), ISO 27017 (cloud security), and ISO 27701 (privacy). So, if your long-term roadmap includes privacy or cloud-specific compliance, ISO 27001 gives you a structured foundation to build on.
ISO 27001 and SOC 2: A case for dual compliance
For companies operating across borders or serving both U.S. and international clients, dual compliance with ISO 27001 and SOC 2 isn’t just a nice-to-have — it’s a strategic advantage. While SOC 2 satisfies procurement and trust expectations in the U.S., ISO 27001 carries weight in global markets and with clients in regulated sectors.
Together, they offer a more complete security assurance story: SOC 2 shows your controls are working effectively over time, while ISO 27001 proves you’ve built a structured, risk-based information security program. With overlapping control areas and tools like Scrut that support both frameworks in parallel, achieving dual compliance is more attainable than ever — without doubling your effort.
ISO 27001 and SOC 2 mapping
While ISO 27001 and SOC 2 follow different approaches — one offering a certification and the other an attestation report — they share a lot of common ground when it comes to security controls and risk management principles. Both frameworks require organizations to implement processes for access control, incident response, change management, vendor oversight, and continuous monitoring.
This overlap makes it possible (and efficient) to pursue both standards in parallel. Many organizations begin with one and layer in the other by aligning internal documentation, leveraging shared evidence, and mapping controls across both frameworks.
For instance:
- ISO 27001’s Annex A controls map closely to SOC 2’s Trust Services Criteria
- Risk assessment and treatment in ISO 27001 aligns with SOC 2’s risk identification and mitigation requirements
- ISO’s internal audit and management review requirements correspond to SOC 2’s monitoring and governance expectations
If you’re planning to serve both U.S. and international clients, a dual approach can help you satisfy broader customer demands with less incremental effort.
How can Scrut help to automate the process with ISO 27001 and SOC 2?
Scrut simplifies compliance with both ISO 27001 and SOC 2 by automating the overlapping parts and tailoring support for what makes each framework unique.
For ISO 27001, Scrut offers pre-mapped Annex A controls, an in-built risk register, and ready-to-use ISMS documentation — all aligned with the 2022 update. It also automates evidence collection and audit tracking, so you’re always prepared for surveillance and recertification.
For SOC 2, Scrut maps your controls to the Trust Services Criteria and tracks Type I and Type II audit progress with a real-time dashboard. It continuously monitors control effectiveness and streamlines auditor collaboration with scoped access.
Most importantly, Scrut identifies common controls across both frameworks, so you only implement them once. That means less duplicate work, faster readiness, and a smarter path to dual compliance.
Achieve SOC 2 and ISO 27001 compliance—automated, audit-ready, and all in one platform. Get started with Scrut today.

FAQs
Can I replace ISO 27001 standard with SOC 2?
Not exactly. While there’s some overlap, SOC 2 and ISO 27001 serve different purposes. ISO 27001 is a certification for an organization’s information security management system (ISMS) and is recognized globally. SOC 2, on the other hand, is an attestation report primarily used in the U.S. to evaluate the operational effectiveness of specific controls. If you’re targeting international clients or need a structured ISMS, ISO 27001 is the better fit. If you’re focused on U.S. markets and enterprise SaaS, SOC 2 might be sufficient — but most growing companies eventually pursue both.
What are the similarities between ISO 27001 and SOC 2?
- Both require a risk-based approach to managing information security
- They cover similar domains: access control, incident management, vendor management, and change control
- Each demands documented policies, control implementation, internal reviews, and external audits
- Continuous improvement is core to both frameworks
Which SOC report is closer to an ISO report?
SOC 2 Type II is the closest equivalent to ISO 27001 in terms of depth. While ISO 27001 certifies your overall ISMS, SOC 2 Type II assesses the operating effectiveness of your controls over a period (typically 3–12 months), giving stakeholders insight into how reliably your security practices are followed in day-to-day operations.
What other SOC reports are closest to ISO 27001?
SOC 1 and SOC 3 are also part of the SOC family, but they serve different goals:
- SOC 1 focuses on financial reporting controls and has little overlap with ISO 27001
- SOC 3 is a more general-use report based on SOC 2 but lacks detailed findings — it’s more of a marketing summary
Among these, only SOC 2 aligns closely with the principles and structure of ISO 27001.


















