Honing vendor risk assessment with Scrut Automation

Back in 2013, Target, one of America’s biggest retailers, suffered a harrowing data breach. Its hackers got away with 41 million credit and debit records and 70 million customer records.
The reason for the breach: Their third-party HVAC company fell for a phishing email.
To avoid a similar fate, vendor risk management should be a vital part of an organization’s security strategy.
Since most organizations today rely on external vendors to fulfill various operational needs, vendor risk assessment is non-negotiable when it comes to managing vendor risks.
In this blog, we will explain what vendor risk assessment is, highlight its importance, provide eight key steps to perform an effective assessment and explore Scrut’s solutions for enhancing vendor assessment for your organization.
What is vendor risk assessment?
Vendor risk assessment is the systematic process of identifying and evaluating the potential risks associated with engaging third-party vendors.
It involves identifying and analyzing vulnerabilities within vendor relationships and measuring their potential impact on the organization.
The assessment is carried out by evaluating the vendor’s security controls, values, goals, policies, procedures, and other relevant factors. Vendors are typically made to fill out a vendor risk assessment questionnaire that requires them to share information about their security controls.
Why is Vendor Risk Assessment Important?

Major security incidents such as the SolarWinds attack and Colonial Pipeline attack, which were major supply chain breaches, call attention to the need for vendor risk assessment.
Here are some reasons why it is important for an organization to perform a thorough vendor risk assessment.
1. Prevents data breaches
Vendors are potential entry points for cybercriminals since they often have access to sensitive data or critical systems.
Performing a thorough risk assessment enables organizations to identify vulnerabilities in the vendor’s security posture and assess their data protection measures. This helps in determining if the vendor is likely to pose risks to the organization’s security.
2. Reduces operational risks
Vendor risk assessment allows organizations to evaluate the capabilities, performance history, and business continuity plans of their vendors. This reduces the likelihood of operational interruptions caused by the inefficiency of service providers.
3. Promotes compliance
It is mandatory for organizations to comply with regulatory frameworks, industry standards, and data protection laws. Associating with vendors who do not adhere to these requirements can result in severe legal and financial consequences.
Performing vendor risk assessments helps in evaluating the compliance posture of vendors, enabling organizations to choose partners that align with their regulatory obligations.
4. Protects reputation
If your vendors engage in unethical practices, suffer from frequent breaches, or fail to meet quality standards, your organization will be guilty by association. Unethical or negligent vendors can damage your company’s reputation.
Vendor risk assessment helps evaluate the reputation, stability, and past performance of your vendors, which ensures the protection of your organization’s reputation.
How to perform vendor risk assessment?
It is important for organizations to conduct vendor risk assessment before engaging with any third-party vendor. This assessment serves as a crucial step to evaluate potential risks associated with the vendor. Only after a thorough assessment and approval can the vendor be considered safe to work with.
Here are five key steps involved in a thorough vendor risk assessment.
1. Identify the typical risks associated with vendors
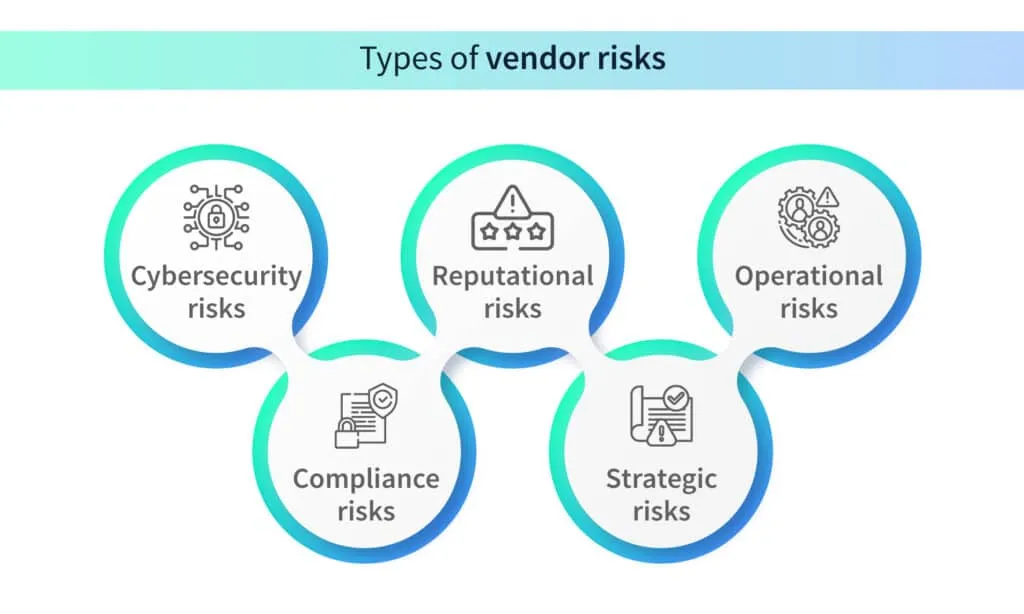
Before diving into the evaluation process, it is important to identify the different risks that could arise when entering into a business agreement with a vendor. It’s crucial to cover all your bases and have a clear understanding of the potential risks associated with different kinds of vendors. Here is a list of the most common vendor risks.
Cybersecurity risks
If any one of your vendors does not enforce adequate cybersecurity measures, your organization becomes vulnerable to cyber-attacks. Vendors who pose cybersecurity risks may have vulnerabilities in their systems, possess inadequate access controls, and enforce weak security practices and data protection measures.
Compliance risks
If your organization engages a vendor that does not comply with laws, regulations, or industry standards, it becomes vulnerable to compliance risks. This could result in your organization being slapped with legal consequences, reputational damage, or financial penalties.
Reputational risks
Vendors with a bad reputation either due to poor security or unethical practices will ruin your organization’s reputation if you engage them. It is important to thoroughly assess the history of vendors before doing business with them.
Additionally, if the vendor suffers a cybersecurity attack, their reputation will be damaged and in turn the reputation of the organization will be dented.
Strategic risks
If a vendor’s strategies clash with the objectives of your organization, it could stand in the way of your business goals. For instance, if they launch a product that competes with your product, it negatively impacts your sales.
Operational risks/business continuity risks
Inefficient vendors could hamper the operations of your business. If they fail to deliver their product or service on time, your organization’s productivity will suffer.
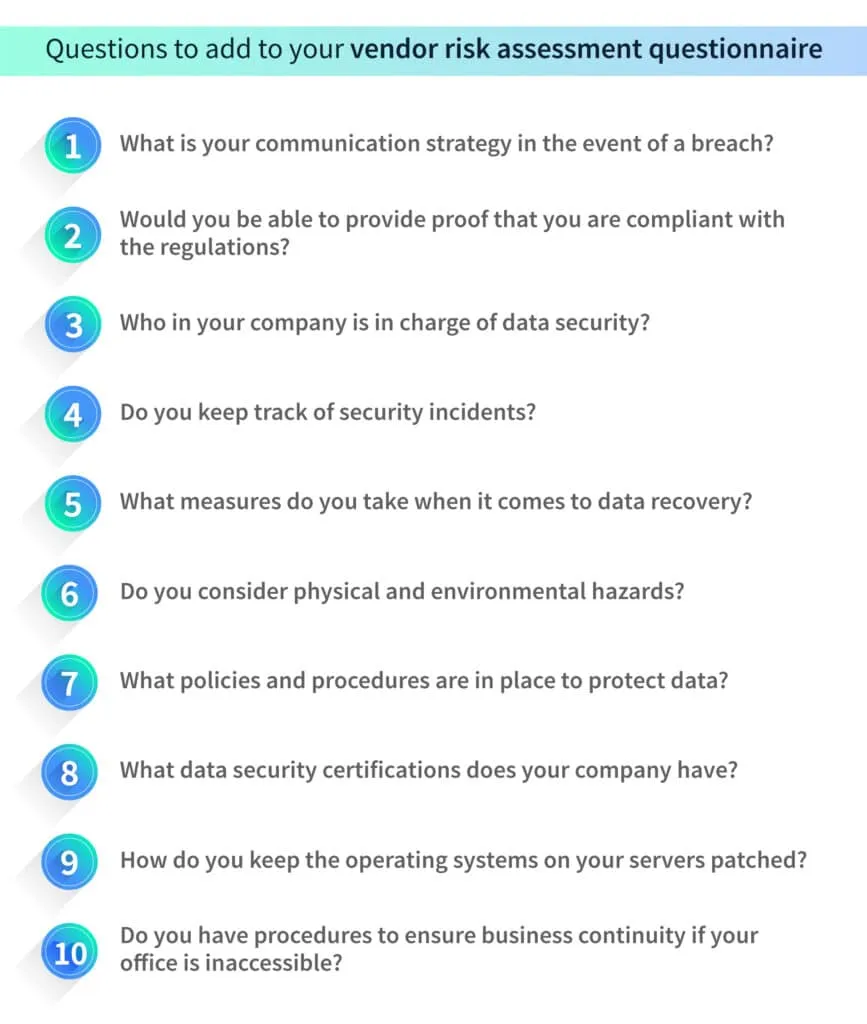
2. Create a vendor risk assessment questionnaire
Getting your vendors to fill out a questionnaire that requires them to detail their security measures helps assess the risk they pose to your organization. The questions should focus on areas such as data security, compliance, financial stability, reputation, and IT infrastructure.
Here are some examples of questions that could be included in a vendor risk assessment questionnaire.
3. Analyze vendor risk profiles
Once all your vendors have filled out the questionnaire, you will have an idea of the kind of risks they pose. Conduct a detailed analysis of each vendor’s risk profile by reviewing their security practices, financial reports, audit results, and compliance certifications.
Assess potential risks such as data breaches, service disruptions, compliance failures, financial instability, and legal or regulatory issues.
4. Categorize vendors based on their risk profiles
After you’ve analyzed the risk profiles of your vendors, assign scores based on the levels of risk they pose. Higher risk scores should be assigned to vendors who have access to sensitive data, critical infrastructure, or those involved in key operational processes.
Vendors should be categorized based on their criticality and potential impact on your organization.
It is a good idea to avoid engaging with vendors whose questionnaires revealed poor security measures.
5. Develop risk mitigation strategies
The final step is to develop risk mitigation strategies for the vendor categories that you created. This may involve implementing security controls, conducting security assessments, establishing performance metrics, defining contractual obligations related to security and compliance, and conducting regular audits.
Recommended practices for effective vendor risk assessment
There are a few best practices that can help make your vendor risk assessment strategy even better. We’ve listed them below.
1. Promote vendor communication and education
It is necessary to encourage open and continuous communication with vendors to ensure a collaborative approach to risk assessment.
You could share security expectations, incident response plans, and updates on regulatory compliance with your vendors to have them on the same page as your organization.
You could also educate your vendors by providing them with resources to enhance their understanding of security best practices and industry-specific compliance requirements.
2. Assess vendors regularly
Implementing processes for continuous monitoring and evaluation of vendor performance is an effective way of preventing vendor risks. Conducting periodic reviews, audits, and assessments to detect emerging risks ensures continuous compliance and addresses any deviation from agreed-upon security standards.
3. Involve vendors in incident response plans
By collaborating with vendors to develop incident response plans in the event of a breach, you can reduce the risk of supply chain attacks. You must define clear roles and responsibilities with your vendors to ensure an effective response to security incidents or breaches.
How can Scrut boost vendor risk assessment?
In the realm of vendor risk assessment, Scrut stands as a versatile tool, providing an array of features to streamline and fortify the entire process. Let’s explore how Scrut can contribute to a more efficient and effective vendor risk assessment.
Questionnaire creation
Scrut simplifies the questionnaire creation process, offering the flexibility to use pre-built templates or tailor custom ones. Users can set submission and review dates, as well as designate specific reviewers.
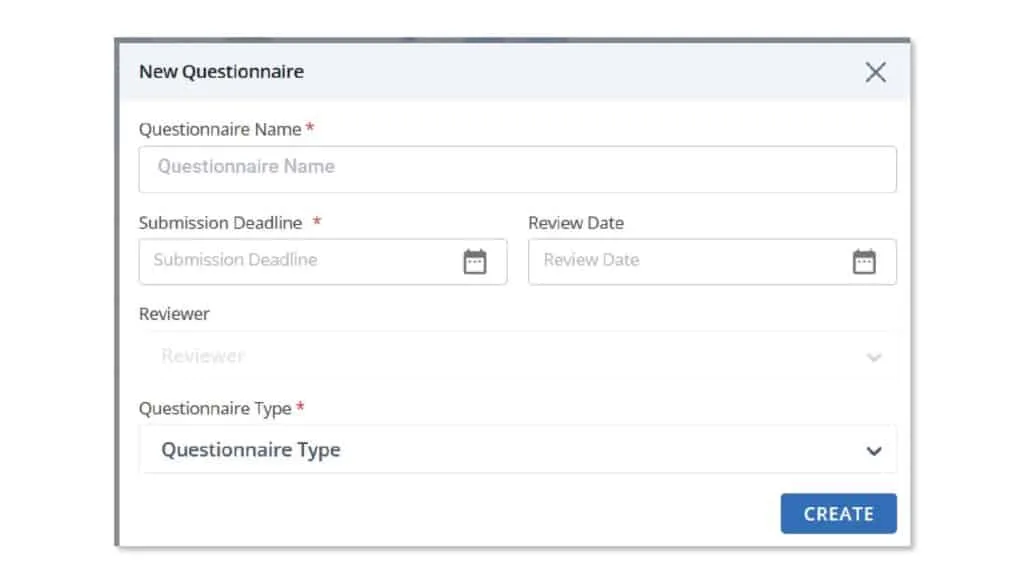
Points of Contact (POCs) can benefit from a dedicated vendor portal, allowing them easy access to answer and submit questionnaires.
The portal also serves as a centralized hub for tracking the status of questionnaires and mitigation tasks, providing a comprehensive overview of ongoing activities.
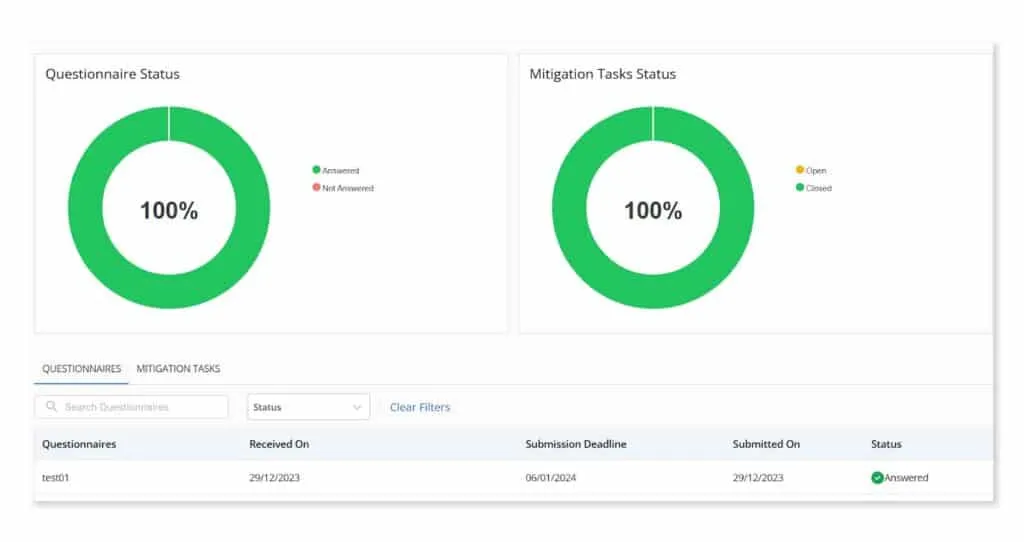
Reminders and pending status tracking
Automated reminders within Scrut ensure timely responses to pending questionnaires. The platform’s intuitive system allows for efficient tracking of mitigation task statuses, with detailed audit logs offering transparency into the progress of each task.
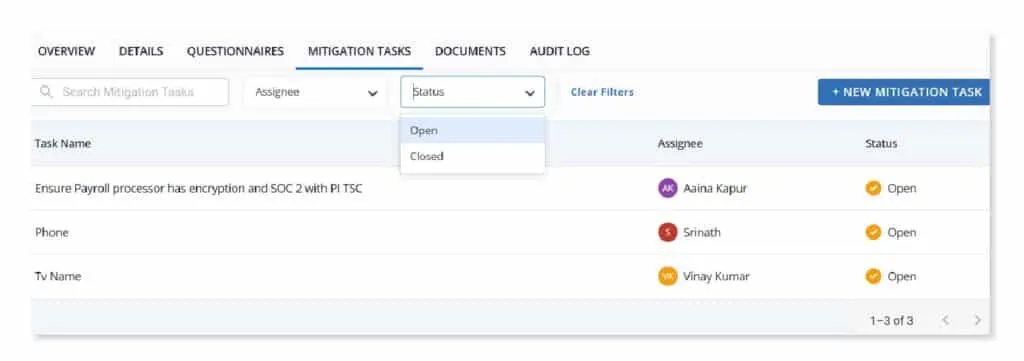
Evaluation and scoring
Scrut offers a structured approach to evaluation by allowing administrators to assign specific domains and reviewers for each question. Reviewers have the flexibility to accept, flag, adjust, or create a mitigation task based on their assessments. The overall risk scores dynamically adjust based on these evaluations.
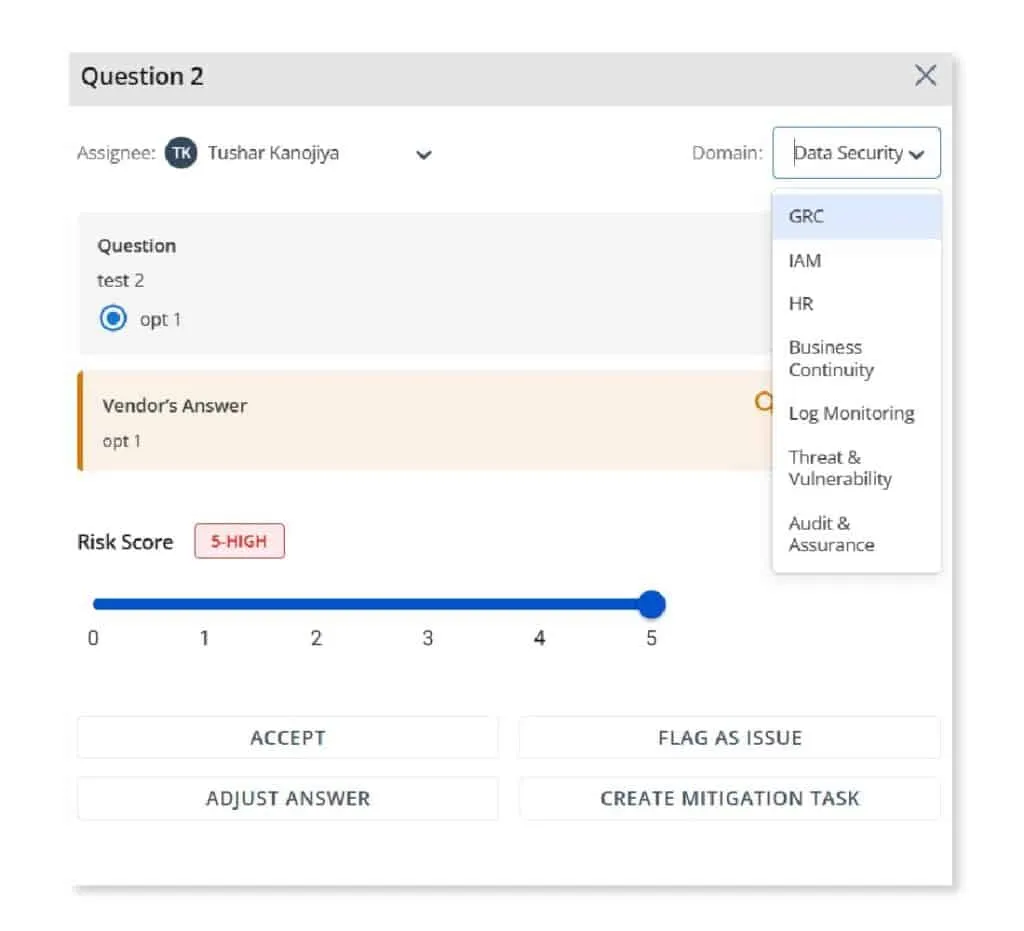
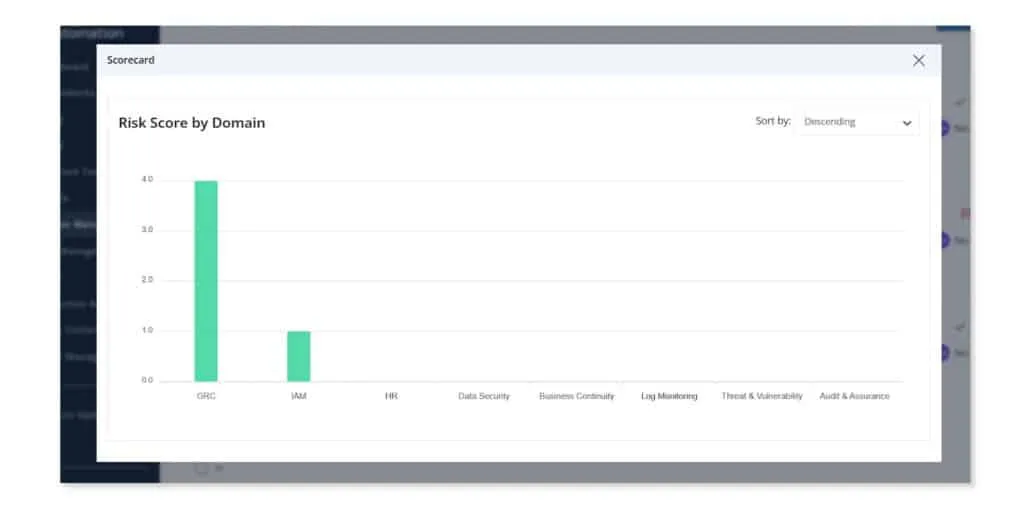
Repository of submitted documents
Scrut facilitates an organized repository for each vendor, housing questionnaires and documents related to mitigation tasks. Documents play a pivotal role in assessing a vendor’s risk profile, compliance with regulations, and potential impact on the organization. Scrut efficiently categorizes and tracks documents as Vendor Documents, Questionnaires, or Mitigation Tasks, providing clarity on their source and purpose.
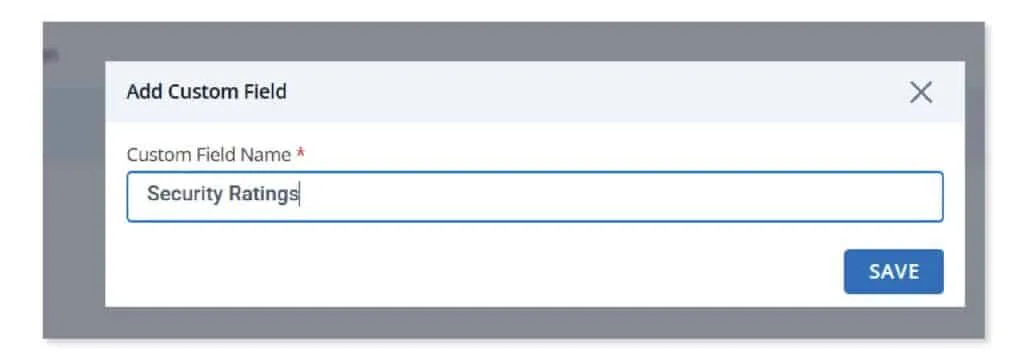
Custom fields – Region, type, security ratings
Acknowledging the importance of flexibility, Scrut allows businesses to define and capture additional information about vendors. Users can customize vendor profiles with specific fields such as region, security ratings, or revenue impact. This tailored approach to vendor categorization assists in better planning and operations, recognizing that a one-size-fits-all strategy may not be suitable.
Conclusion
Vendor risk assessment plays a crucial role in safeguarding organizations from potential security threats and vulnerabilities associated with vendor services. By conducting comprehensive assessments, your organization can identify and mitigate risks related to data breaches, service disruptions, compliance failures, and reputational damage.
Using Scrut’s range of solutions can help in not only streamlining but fortifying the entire vendor risk assessment process. Schedule a demo today to learn more.
FAQs
1. What is vendor risk assessment?
Vendor risk assessment is the systematic process of identifying and evaluating the potential risks associated with engaging third-party vendors.
2. What is a vendor risk assessment questionnaire?
A vendor risk assessment questionnaire is a form that requires vendors to detail their security measures in order to assess the potential risks they could pose to an organization.
3. How to perform vendor risk assessment?
• Identify types of risks
• Create a vendor risk assessment questionnaire
• Analyze vendor risk profiles
• Categorize vendors based on risk profiles
• Develop risk mitigation strategies


















