Choose risk-first compliance that’s always on, built for you.
Go back to blogs
Top 7 CAASM vendors in 2023
Last updated on
February 19, 2025
16
min. read

Today’s complex IT environment demands a security solution that gives complete visibility into all the cyber assets in your organization.
This can be done by a system that continuously locates cyber assets in your environment. That’s where CAASM tools come into the picture.
The main areas of attention for CAASM tools are asset discovery and visibility, vulnerability management, and cloud misconfigurations.
Cyber asset attack surface management (CAASM) platforms can benefit an organization in multiple ways.
They help security teams with:
- Building a complete inventory of all internal and external assets via API integrations with other tools already existing in the organization.
- They can query against the data from this asset inventory data.
- Furthermore, a CAASM solution helps security teams find out vulnerabilities and gaps in security controls.
- With a CAASM solution, security teams can prioritize what issues to resolve first based on the potential damage they can cause.
A CAASM tool like Scrut helps to protect internal assets (like code repositories and users) and external assets (like websites and mobile devices).
It helps security teams answer security questions like:
- Which cyber assets are most critical?
- What would be the severity of impact in case a critical asset is compromised?
- How to respond to a security breach incident?
We have prepared a list of the top CAASM tools. If you are researching CAASM vendors available in the market, you will find this list helpful.
7 Cyber Asset Attack Surface Management Tools
Asset discovery is the foundation of all CAASM solutions. They work on the security principle that you cannot protect something that you cannot identify.
To begin with, a CAASM tool aggregates asset data from many sources and creates a single unified view. It then maps relationship between these assets to gives you the insights into your cybersecurity risks
Now let’s discuss the best 7 CAASM vendors starting with Scrut.
1. Scrut Automation

Scrut’s CAASM gives visibility of all your cyber assets, empowering IT and security teams to overcome cyber asset vulnerability challenges. The platform aggregates cyber assets data using third-party APIs, agents and integrations and provides insights into a single unified dashboard.
Key Features of Scrut CAASM

Scrut Acts as a Single Source for All your Cyber Assets Visibility
By discovering and consolidating all of your cyber assets continuously regardless of where they are located, Scrut automatically creates a complete and up-to-date asset inventory.
As you scale and deploy new resources such as getting more applications, and correspondingly your attack surface is constantly evolving. And if you don’t have real-time visibility into your attack surface at any point in time, there will be resources that will left vulnerable, which you wouldn’t be able to manage or exercise the right kind of control, if you don’t have clear visibility of your attack surface.
Scrut consolidates and normalizes asset data across distributed, multi-cloud environments.
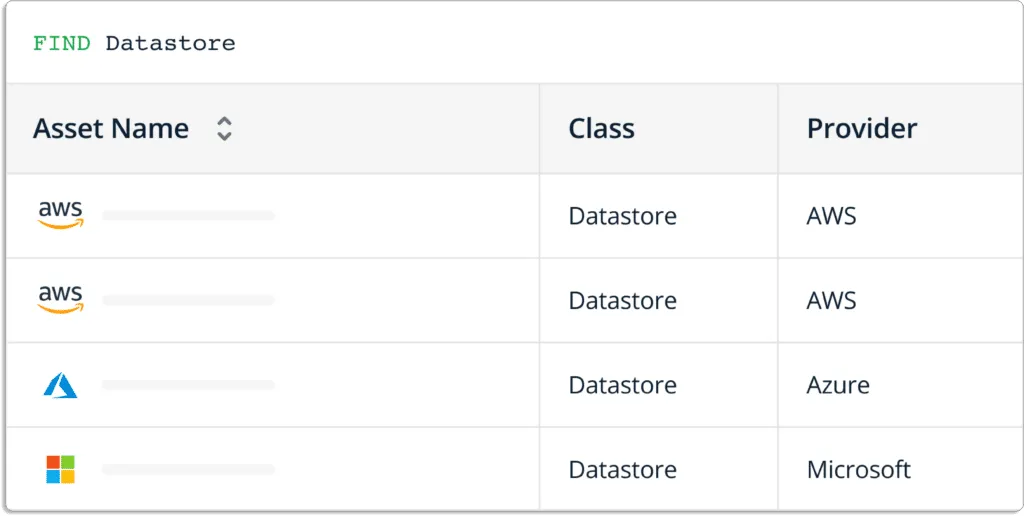
Having complete visility of your assets is important because each of these assets can give attackers an entry point into your organization. You cannot just create the inventory once and update it monthly with the data getting outdated very quickly; you need to update in real time.
In short, Scrut gives you a centralized view of all cloud entities, endpoints, code repositories, users, etc., to identify critical business assets, and prioritize risks across your hybrid and multi-cloud environments.
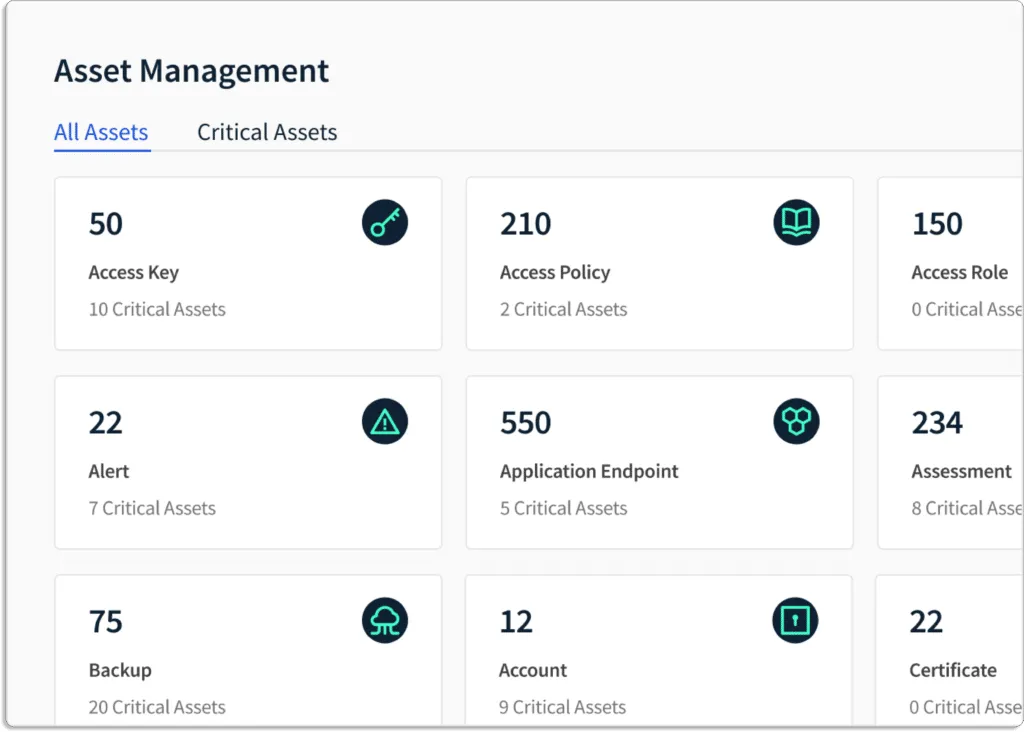
Scrut Helps you Monitor your Attack Surface
With Scrut, you can keep a check on your cyber attack surface with an interactive visual asset map.
As your cloud grows, so will your threat landscape. Scrut continuously identifies, maps, and analyzes ever-spreading attack surfaces to prevent attackers from accessing sensitive information.
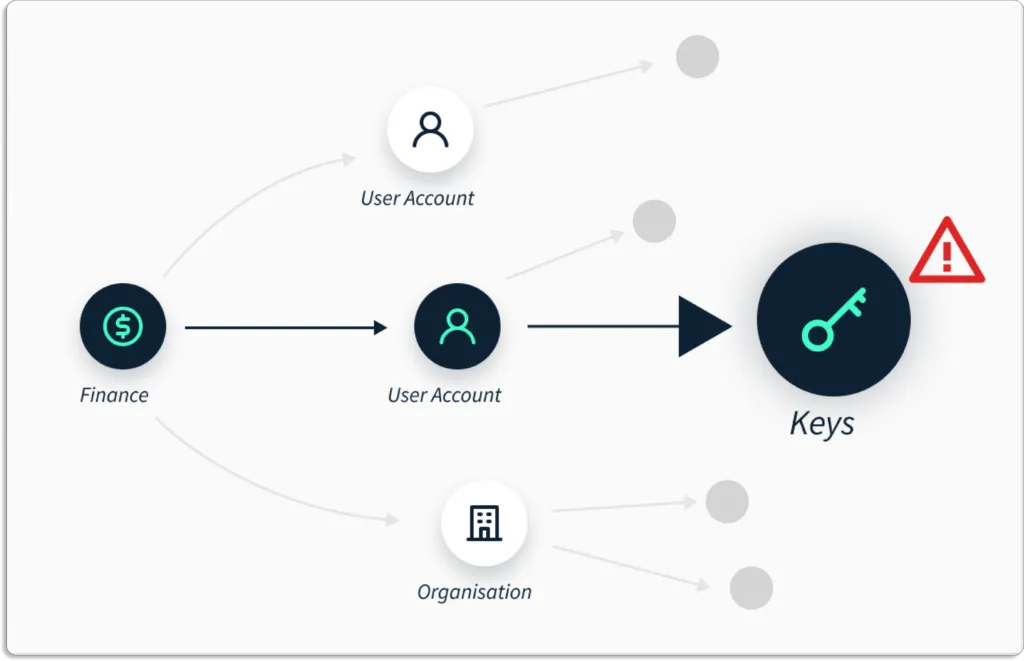
Scrut Helps you Eliminate Tool Fatigue
Scrut gives you deep insights into risks organization-wide. This is unlike other point solutions like CSPM, CIEM, CWPP, and CNAPP, which give you insights into risks only within their individual scope.
Hence, Scrut eliminates screen fatigue, as you are not required to check multiple tools.
The data is presented in a graphical manner for quick visualization. So, it’s easy to find exact security issues in your environment and answer security and compliance questions. Further, you can also build complex queries on relationships between assets to find gaps in your ecosystem.
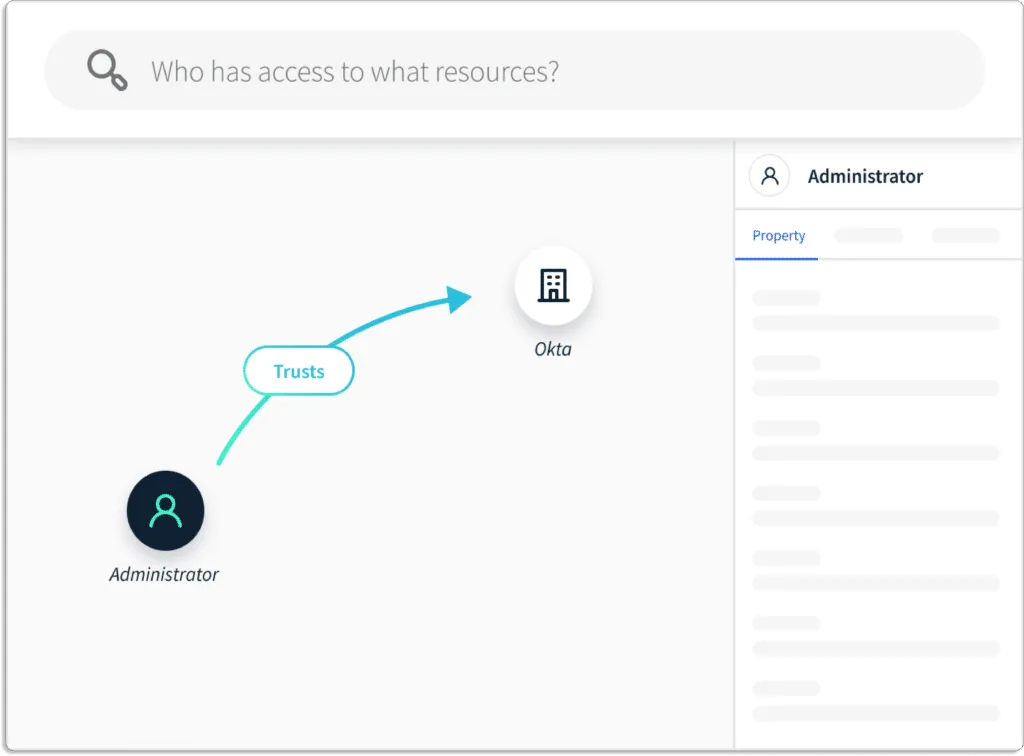
Scrut Enables you to Identify and Prioritize Critical Risks
You can continuously monitor your cyber asset landscape for issues affecting critical business assets and infrastructure.
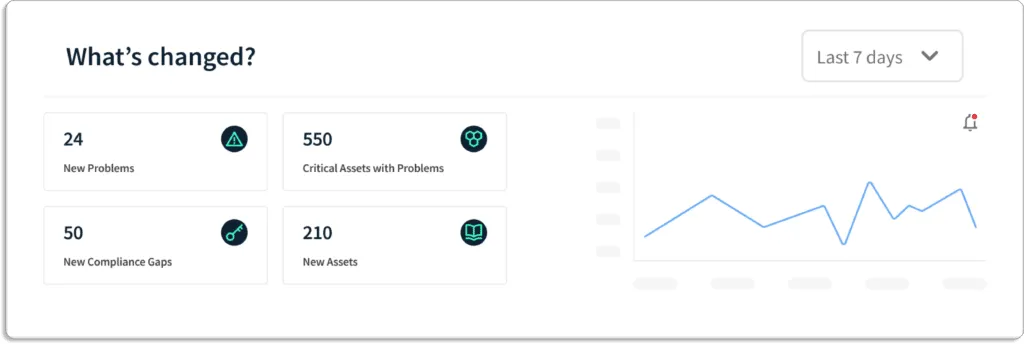
Scrut provides you with a single pane of glass for all the risks. These risks come with a status that helps you prioritize what to work on first.
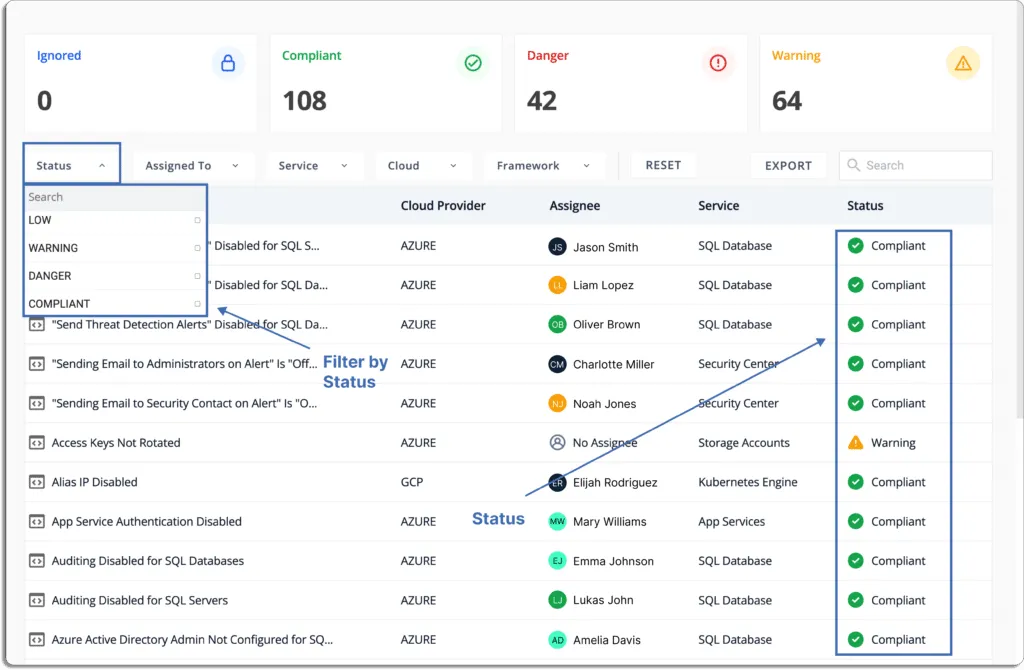
Status
- Danger – Most critical issues. Work on these first.
- Warning – After working on the issues marked as danger, next, you can work on these.
- Low – These risks should be worked on last.
- Ignored – You can override any status to ignore.
- Compliant – Everything is fine. Don’t need to do anything.

Customer Rating
- G2 – 5/5

2. JupiterOne
JupiterOne is a cyber asset attack surface management (CAASM) platform that enables businesses to compile cyber asset data from all of their tools into a single, unified view, which serves as the basis for all security operations.
JupiterOne integrates with your cloud infrastructure, DevOps pipeline, and security tooling to gather reliable asset data in one place. This comprehensive, unified view enables you to manage cyber assets across hybrid and multi-cloud environments effectively.
Key Features
Gain complete visibility across all cyber assets: JupiterOne is a proficient CAASM tool that provides full visibility of your asset inventory. It uncovers all the hidden risks and assesses all the risks to monitor any risk. It discovers structural elements of your environments, such as unknown intensity, user accounts, workloads, and security awareness gaps, to mitigate security risks associated with the organizations.
Query consolidated data: With JupiterOne, your team members can query consolidated data to answer complex questions.
Accelerate incident response and remediation: JupiterOne helps you proactively find the risks before it happens. It has a strong automated incident response system and accelerates the mitigation strategies, and helps you stay safe from any risks.
Pros
- The platform can quickly visualize relationships in the digital environment by providing automated reports and evidence collection feature.
- It offers security categories to maintain a secure environment and provides efficient observability of IT assets in your organization to control the attack surface.
- It offers JSON language support, which makes it quite simple to build a query and run it quickly.
- The platform’s compliance solution provides cloud network mapping and vulnerability tracking.
- Query AWS resources help you understand the environment, configuration, and overall compliance accurately.
Cons
- There are performance issues in the platform due to rate limiting.
- The SaaS integrations need improvement as some desirable data elements are often not pulled into JupiterOne.
Customer Rating
- G2 – 5/5
3. Noetic
Noetic is a continuous cyber asset management and control platform with full-stack visibility to your organization’s assets. The tool empowers you to identify all the hidden and exposed assets and signify their relationship. It helps you identify gaps and improve efficacy.
Real-time insights: Noetic provides unified visibility across cloud and on-premise systems and covers all assets and entities in the organization. It provides real-time insights into security posture.
Cyber relationship: The tool maps the cyber relationship between the organizations’ assets to identify the security coverage gaps. Also, it discovers misconfigurations and policy violations and prioritizes business risks based on resolution.
Integrations: The software can integrate with any third-party integrations to fully discover the organization’s risk. It provides automated workflows, resolves the risk, and continuously monitors all improvements.
Key Features
- Asset discovery – Noetic accelerates asset discovery and makes it simple to view and understand the relationships between all of your entities and assets. The platform builds an updated single point of truth through a graph database. This connected graph can help security teams quickly detect coverage gaps, address data quality concerns, and prioritize business operations.
- Vulnerability management – The platform enhances vulnerability management capabilities by delivering a consistent perspective of your ever-changing security environment to make decisions based on comprehensive and real-time data.
- Endpoint security – Noetic platform seamlessly integrates with and extends existing endpoint security products by giving organizations complete visibility into their security posture. The tool integrates with endpoint security tools like SentinelOne, CrowdStrike, and Windows Defender ATP to determine and evaluate protection coverage across several tools.
- Identity and access management – Noetic integrates with identity and access management systems to create a unified graph that describes roles, individuals, accounts, accesses, and user activity to the assets and resources you are safeguarding.
4. Axonius
Axonius platform enhances security coverage by providing complete insights into the attack surface, including internal and external. The tool offers automated response actions by normalizing, aggregating and deduplicating data from security and IT solutions.
Key Features
- Complete inventory of your environment – It provides a full, always up-to-date inventory of all assets based on data from hundreds of deployed sources. With Axonius, there is no need to install agents, traffic sniffing and network scanning.
- Query to identify vulnerabilities and gaps – With Axonius query wizard, you can easily detect surface coverage gaps, policies and controls validation, and perform quick investigations.
- Remediate risks and vulnerabilities – It provides automated trigger whenever an asset deviates from policies.
Pros
- The tool provides complete visibility by connecting and gathering information from the majority of the products.
- With Axonius, users can aggregate CSV reports and make API calls to many data sources. For example – users can get records from antivirus, Active Directory, etc. all in one report.
- The platform aggregates data from several sources and provides useful APIs to other systems with a collaborative support team.
- The tool provides dashboards with all required metrics of data and alerts about all the security issues and identifies security controls on endpoints efficiently.
Cons
- The query capabilities is not up to the mark and lack few queries such as if-else queries and provides no way to organize the metric cards stored accordingly.
- The platform doesn’t provide efficient graphs or visibility features that help users to understand the data reporters more efficiently.
- Sometimes the connectors don’t sync up properly.
Customer Rating
- Capterra- 5/5
5. Brinqa
Brinqa is a CAASM tool that seamlessly integrates all security and business data sources into a unified knowledge graph. It provides automated data transformations, normalization, and correlation with the Brinqa connector framework.
Brinqa’s cyber risk service provides cyber asset attack surface management through knowledge-driven insights. It transforms security, contextual and threat data into insights. These insights empower organizations to identify their risk and provide risk assessments for mitigating security issues.
Key Features
- Risk assessment: It provides an efficient risk awareness program and process to apply consistent strategies across your security solutions, asset repositories, and attack surfaces. It turns the insights into targeted, automated, and tracked actions to improve cyber risk management.
- Risk management: An organization can have multiple risks at once present within the systems. It is important to analyze and prioritize all the risks to manage those properly. A managed environment provides better risk mitigation strategies. The tool provides enterprise-grade risk management solutions that provide risk-aware prioritization and remediation of threats.
- Risk remediation: The identified risks need to be handled in the organizations. The tool provides future-proof solutions that develop and apply necessary knowledge to make informed decisions for risk remediations. It improves the system’s security posture using its most effective and efficient security actions.
Pros
- The platform analyzes security data by automating routine security processes and providing useful insights.
- The platform provides security with a trust plugin feature.
Cons
- The features are costly compared to other software.
Customer Rating
- G2- 4.6/5
6. Sevco
Sevco security uses a modern approach to asset intelligence to strengthen the security posture. The tool manages the asset inventory for giving a complete real-time asset ecosystem view. Its CAASM platform aggregates inventory information from multiple sources for comprehensive report generation.
Sevco is a cloud-native CAASM platform that provides multiple benefits to your organization.
- Sevco identifies gaps and vulnerabilities in security tools deployment and coverage, and provides proper risk mitigation strategies to safeguard your system from hackers.
- It improves incident response capabilities and provides real-time asset inventory details for your understanding of the states and making informed decisions.
- The tool ensures continuous adherence to endpoint compliance build standards to be safe from legal issues and maintains customers’ trust in the organization.
Key Features
Data collection and processing pipeline: Sevco enables your organization to collect data and create an automated processing pipeline using native API integrations. A single data source does not provide all the necessary details. Thus, Sevco’s multi-sourced approach provides comprehensive and accurate visibility to your organization’s asset inventory by leveraging several existing tools.
Aggregation and correlation: Organization’s asset inventory is dynamic and is always changing. It provides continuous real-time asset inventory details to better understand security measures. The tool does exactly that by providing a detailed overview of your daily operations related to asset inventory and ensuring all the data streams are analyzed for to make comprehensive reports.
Asset Telemetry: Sevco generates asset telemetry for every change detected by any of your tools with the continuous data flow. The platform records every event. It generates asset telemetry for continuous data processing pipeline changes. For example – when a device’s IP address changes or when it appears in a different physical location. Furthermore, its asset telemetry can be easily searched to help in your investigations.
API integration configurations: Sevco highlights risks and gaps by providing real-time asset inventory with Venn diagrams.
Data publication: The tool feeds data into existing procedures and processes in systems like SOAR (security orchestration automation and response) and SIEM (security information and event management) platforms.
Pros
- The platform provides easy integration with different technologies that enhance your cyber attack surface management and offers feedback on ways to improve your organization’s overall security.
- It provides data insights in a single dashboard and you can use the reports to close the vulnerabilities.
Cons
- In terms of data sources and reporting features, the product still has some catching up to do. For example – roadmap items need to be fixed.
- Queries occasionally need to be adjusted because of complex reporting.
Customer Rating
- Gartner- 4.9/5
7. Cyberpion
Cyberpion’s security platform identifies and neutralizes threats by protecting the external attack surface. Organizations can gain visibility and control of risks streaming from websites, clouds, PKI, and DNS misconfigurations.
The Cybepion tool has automated protection capabilities and blocks attackers with an immediate active protection system. It prioritizes your risks and provides relevant solutions for mitigating the threats. It detects and fixes vulnerabilities before they become potential threats and lead to data breaches.
Key Features
External attack surface discovery: Cyberpion discovers all the external assets of your organization that are exposed to the internet and can lead to cyber-attacks if any vulnerability is available. It provides a strong asset discovery engine that examines third-party connections of your system and maps the online attack surface to find all the hidden assets.
External attack surface evaluation: After discovering all the assets and third-party connections Cyberpion enables evaluation strategies to decide what to do with the risk issues. It helps you to make informed decisions on what elements to keep, initiate, or remove from your organization. The tool provides complete visibility of your external asset surface and helps security teams to analyze and eliminate assets and connections that are vulnerable to external threats.External attack surface management: After assessing strategies, it is important to resolve the issues by eliminating unnecessary assets or third-party connections. Cyberpion helps you to manage your relevant assets by focusing on only the assets essential to business and the security team eliminates the other irrelevant assets. This results in protection against the exploitation of data breaches of your organization by hackers.
Table of contents


















