What are SOC 2 audit exceptions and how to prevent them?

When organizations undergo SOC 2 audits, they aim to demonstrate their commitment to security, availability, processing integrity, confidentiality, and privacy.
SOC 2 reports provide valuable insights into an organization's control environment, assuring clients and partners that their data and information systems are in safe hands.
However, while SOC 2 audits strive to validate a company's compliance, it's not uncommon to encounter exceptions during the process. These exceptions are instances where the organization's controls or practices don't fully align with the established SOC 2 criteria. Understanding and addressing these exceptions is crucial to achieving a successful audit.
What are SOC 2 audit exceptions?
SOC 2 audit exceptions are essentially instances of non-compliance. They can arise when certain controls or practices within an organization's information security framework don't meet the defined criteria for security, availability, processing integrity, confidentiality, or privacy.
These SOC 2 exceptions can manifest in various ways, such as unmitigated vulnerabilities, incomplete documentation, or lapses in control implementation. They serve as indicators that specific aspects of the organization's security posture need attention and improvement.
While audit exceptions might sound alarming, they're not unusual. In fact, many organizations encounter exceptions during their first SOC 2 audit. The key is to address these exceptions effectively, demonstrating a commitment to continuous improvement in information security practices.
In this blog, we'll delve into the world of SOC 2 audit exceptions, exploring their types, common causes, and best practices for addressing them.
Types of SOC 2 audit exceptions
During a SOC 2 audit, various exceptions or deviations from expected controls may surface. It's essential to understand these exceptions in detail, as they help pinpoint vulnerabilities and compliance shortcomings. Common types of SOC 2 audit exceptions include:
1. Control gaps
A control gap occurs when there is a failure to implement a control that is necessary for meeting the selected trust service criteria. This could be due to oversight or a misunderstanding of the control's requirements.
2. Operating ineffectiveness
Sometimes, a control may be in place, but it proves ineffective during the audit. This could be due to poor execution or a lack of documented evidence demonstrating control effectiveness.
3. Non-compliance with policies
Audit exceptions may arise when an organization fails to adhere to its internal policies, procedures, or standards related to information security or privacy.
4. Data breach incidents
The discovery of any data breach or security incident that affects the confidentiality, integrity, or availability of sensitive data can lead to exceptions. This is a severe exception that requires immediate attention.
5. Insufficient documentation
Incomplete or missing documentation is a common exception. Without proper records, it's challenging to demonstrate the implementation and effectiveness of controls.
6. Third-party vendor non-compliance
If third-party vendors or service providers who play a role in the organization's controls are not compliant with SOC 2 standards, this can result in exceptions for the audited entity.
7. Employee negligence
Sometimes, SOC 2 exceptions are tied to employee actions, such as mishandling data, violating policies, or neglecting their responsibilities related to security.
Understanding the specific type of exception encountered is crucial, as it guides the corrective actions needed for remediation. Organizations should address these exceptions systematically, with a focus on both short-term mitigation and long-term improvements in their control environment.
Common causes of SOC 2 audit exceptions
Despite best efforts, SOC 2 audit exceptions can arise due to various factors. Understanding the common causes of these exceptions is essential for organizations looking to improve their audit performance:

1. Inadequate planning
Failure to adequately plan for the SOC 2 audit is a frequent cause of exceptions. It includes issues like selecting the wrong trust service criteria, insufficiently preparing staff, or not establishing a well-defined audit timeline.
2. Lack of control documentation
Incomplete, outdated, or inaccurate documentation of controls is a significant cause of audit exceptions. Auditors rely on these documents to assess the effectiveness of controls, so any discrepancies can lead to exceptions.
3. Misalignment with trust service criteria
If an organization's control measures don't align with the selected trust service criteria, exceptions can occur. It's essential to ensure that controls are tailored to address the specific criteria they are intended to cover.
4. Human errors
Human errors, such as data entry mistakes or policy violations, can trigger exceptions. These errors may be unintentional, but they still affect the audit outcome.
5. Insufficient training and awareness
Failure to train employees adequately or raise awareness about the importance of SOC 2 compliance can result in exceptions. Employees need to understand their roles in maintaining controls and complying with policies.
6. Inadequate monitoring
Proactive monitoring and continuous testing of controls are vital for SOC 2 compliance. Exceptions may result if organizations fail to monitor their controls effectively.
7. Vendor non-compliance
When third-party vendors or service providers integral to an organization's controls do not meet SOC 2 compliance standards, exceptions can occur.
8. Resource constraints
Limited resources, whether financial or human, can impact the effectiveness of control measures, potentially leading to exceptions.
9. Inadequate incident response
Failing to respond promptly and effectively to security incidents or data breaches can result in SOC 2 exceptions, as it demonstrates an organization's inability to manage risks effectively.
10. Organizational changes
If an organization undergoes significant changes, such as mergers, acquisitions, or restructuring, it can disrupt existing control measures and lead to exceptions.
By recognizing these common causes, organizations can take proactive measures to address them before an audit, thereby reducing the likelihood of exceptions during the SOC 2 audit process. Addressing these issues often involves enhancing internal processes, strengthening training, and ensuring continuous compliance with policies and standards.
How to prevent SOC 2 audit exceptions?
While SOC 2 audits are meticulous, time-consuming processes, and some exceptions may be unavoidable, there are steps your organization can take to minimize the chances of encountering audit exceptions.

Here are key strategies to help you steer clear of common pitfalls:
1. Proactive control maintenance
Regularly assess and update your control environment. Make control maintenance an ongoing process rather than a last-minute scramble before the audit. This includes ensuring that your control objectives are up-to-date and aligned with trust service criteria.
2. Documentation management
Maintain comprehensive documentation for all your controls, policies, and procedures. Document the details of your control objectives, control activities, and control tests. Regularly review and update these documents to reflect your organization's current state accurately.
3. Pre-audit self-assessment
Conduct pre-audit self-assessments to identify potential issues before the external audit. These assessments help you uncover weaknesses and areas of non-compliance, allowing you to address them proactively.
4. Risk assessments
Periodically perform risk assessments to identify potential vulnerabilities and threats. These assessments enable you to align your security controls with emerging risks and evolving business practices, reducing the likelihood of unforeseen exceptions during the audit.
5. Employee training
Invest in comprehensive employee training programs. Ensure that your staff is well-versed in your security policies and control procedures. Well-informed employees are better equipped to follow security protocols, reducing the risk of non-compliance due to human errors.
6. Regular testing
Continuously test your controls to verify their effectiveness. This involves both automated and manual testing procedures. Routine testing can identify control deviations, weaknesses, or failures before the external audit.
7. Third-party vendor compliance
If your organization relies on third-party vendors, make sure they adhere to the necessary trust service criteria. Collaborate with vendors to ensure that their services align with your security requirements. Non-compliance from third parties can lead to audit exceptions.
8. Auditor communication
Foster open communication with your audit team throughout the year, not just during audit periods. Keep them informed about changes in your control environment, and seek their guidance when making alterations to ensure they align with trust service criteria.
9. Incident response readiness
Maintain a well-defined incident response plan and ensure that it's up-to-date. Regularly test the plan to guarantee that your team can respond effectively to security incidents or data breaches.
10. Internal audits
Conduct regular internal audits to evaluate control effectiveness and compliance. Internal audits help you identify and address non-conformities before the external audit, reducing the likelihood of exceptions.
11. Resource allocation
Allocate adequate resources, including budget, staff, and tools, to support your control environment and compliance initiatives. Adequate resources can help maintain a strong control environment and minimize audit exceptions.
By following these proactive strategies and integrating a culture of compliance within your organization, you can significantly reduce the risk of audit exceptions during your SOC 2 audit. Building a robust control environment, keeping records current, and involving employees at every level are key practices that will support a successful audit process.
Addressing SOC 2 audit exceptions
Handling SOC 2 audit exceptions is a crucial step toward ensuring your organization maintains compliance with trust service criteria.
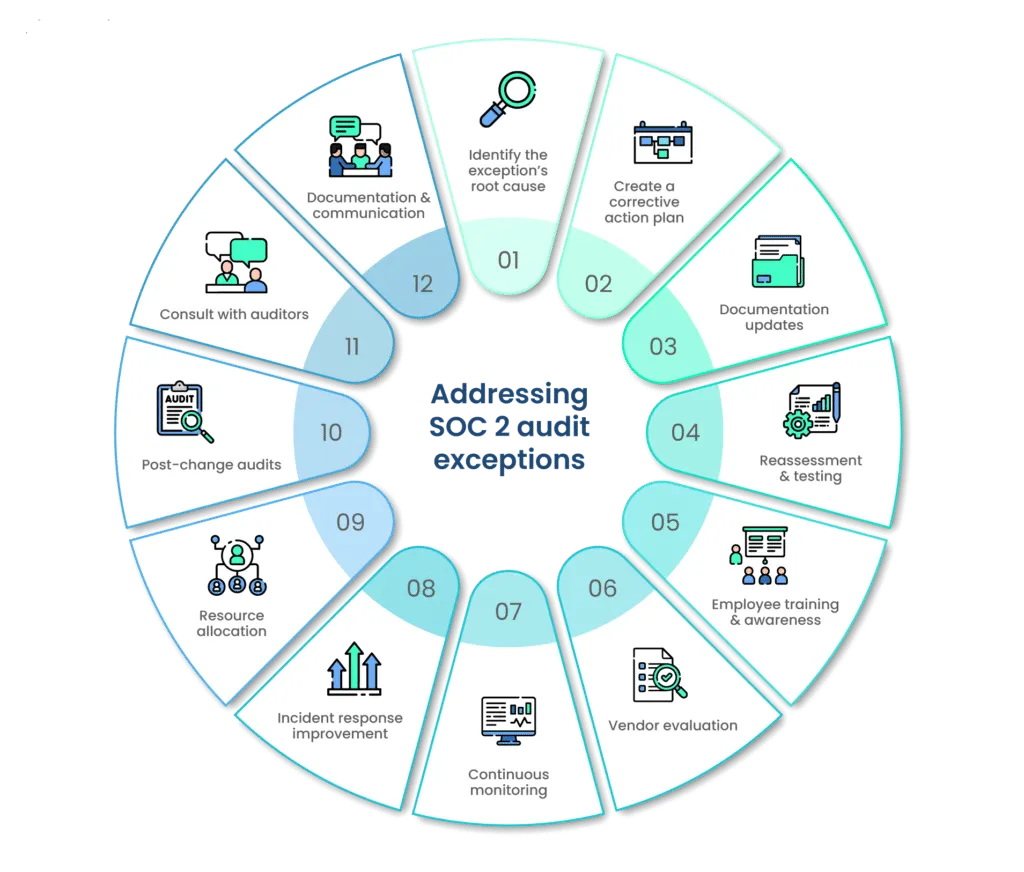
Here's a more detailed exploration of how to address and resolve SOC 2 audit exceptions:
1. Identify the exception’s root cause
Before initiating any corrective action, it's essential to pinpoint the root cause of the audit exception. This requires a thorough examination of the audit report and discussions with auditors to gain a comprehensive understanding of what led to the exception.
2. Create a corrective action plan
Once the root cause is identified, it's time to create a corrective action plan. This plan should outline the specific steps your organization will take to address the exception and ensure compliance with the relevant trust service criteria.
3. Documentation updates
Update your control documentation to align with the trust service criteria and address the exceptions. Ensure that controls are properly documented and any discrepancies are rectified.
4. Reassessment and testing
Reassess the controls that led to the exceptions and conduct additional testing to ensure their effectiveness. This may involve conducting an internal audit of these controls or implementing a third-party audit to validate compliance.
5. Employee training and awareness
If exceptions were caused by employee errors or inadequate training, prioritize training programs and awareness initiatives. Educate your staff about their responsibilities in maintaining controls and complying with policies to prevent future exceptions.
6. Vendor evaluation
If vendor non-compliance contributed to exceptions, engage with your vendors to ensure they meet the necessary SOC 2 compliance standards. Collaborate with them to address compliance gaps and maintain robust control measures.
7. Continuous monitoring
Enhance your organization's monitoring and testing procedures to ensure that controls remain effective. Implement real-time monitoring systems to promptly identify and address any issues that might lead to exceptions.
8. Incident response improvement
Strengthen your incident response plan and procedures to manage security incidents and data breaches more effectively. This will demonstrate your ability to handle risks adequately.
9. Resource allocation
Address any resource constraints by allocating the necessary funds and personnel to support compliance initiatives. This ensures that your control measures remain robust.
10. Post-change audits
After significant organizational changes, such as mergers or restructuring, conduct post-change audits to validate that control measures remain intact and effective.
11. Consult with auditors
Collaborate with your auditors to gain insights into corrective actions and verify that the exceptions are adequately resolved. Auditors can provide guidance to ensure compliance with trust service criteria.
12. Documentation and communication
Properly document all corrective actions and maintain clear communication with your audit team throughout the resolution process. Transparent communication demonstrates your commitment to resolving exceptions.
Addressing SOC 2 audit exceptions is not merely about rectifying the immediate issue but also involves a commitment to maintaining ongoing compliance. Through diligent effort, organizations can mitigate exceptions, enhance their control measures, and ensure long-term adherence to trust service criteria. This commitment strengthens their data security and boosts customer trust in their services.
Continuous improvement for future audits
Continual improvement is a fundamental aspect of SOC 2 compliance. Addressing SOC 2 audit exceptions is not just about fixing the current issues; it's also about fortifying your organization's ability to meet future audits with ease.
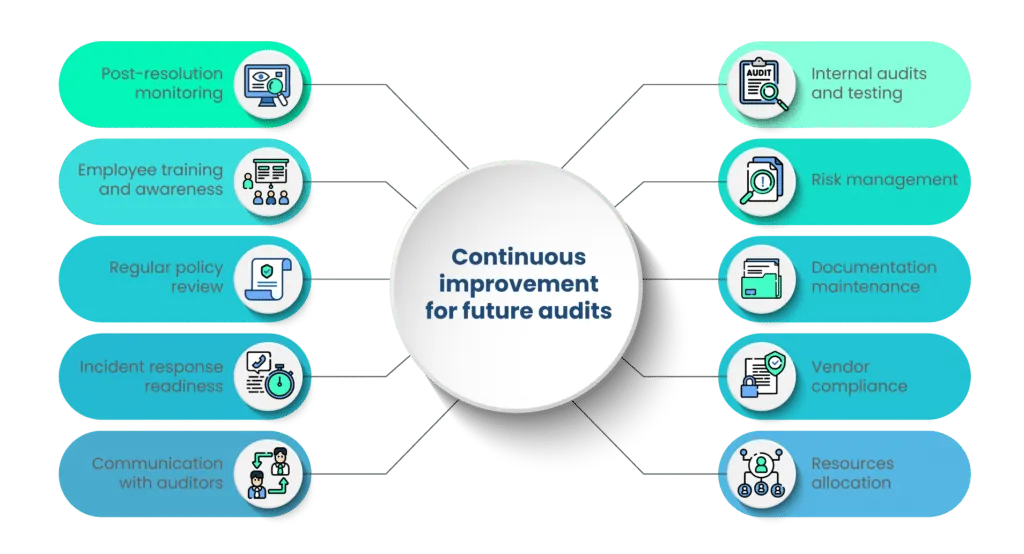
Here's how to adopt a proactive approach to ensure continuous improvement for upcoming SOC 2 audits:
1. Post-resolution monitoring
After addressing audit exceptions, it's vital to maintain a robust post-resolution monitoring process. This entails keeping a close eye on the controls and procedures that were the source of exceptions. Regular monitoring helps ensure that these controls remain effective and compliant with trust service criteria.
2. Internal audits and testing
Conduct regular internal audits and testing of your controls and security policies. These audits serve as proactive assessments to identify vulnerabilities, weaknesses, or any deviations from compliance standards. By identifying issues before the external audit, you can rectify them promptly.
3. Employee training and awareness
Employee training and awareness programs play a critical role in maintaining the effectiveness of your controls. Periodic training sessions help keep your staff updated on security policies, ensuring that they are well-prepared to follow established procedures and prevent non-compliance issues.
4. Risk management
A key part of continuous improvement is enhancing your organization's risk management strategy. This involves identifying and assessing new risks, especially in a rapidly evolving cybersecurity landscape. Adjust your security controls to address emerging threats and vulnerabilities effectively.
5. Regular policy review
Keep your security policies and procedures up to date. Regularly review and update these documents to reflect changes in technology, industry standards, and compliance requirements. Ensure that the policies align with trust service criteria and that employees have access to the latest versions.
6. Documentation maintenance
Documentation is a cornerstone of SOC 2 compliance. Continuously maintain your control documentation, including control descriptions, policies, and procedures. Keep these documents accurate and aligned with your actual practices. Ensure that they are readily accessible to employees and auditors.
7. Incident response readiness
Maintain and improve your incident response plan to effectively manage security incidents and data breaches. Regularly test this plan to ensure that your organization can respond swiftly and efficiently in case of a security breach.
8. Vendor compliance
If your business relies on third-party vendors, ensure that they remain compliant with the trust service criteria. Collaborate with vendors to address any non-compliance issues and mitigate risks related to their services.
9. Communication with auditors
Establish open lines of communication with your audit team. Regularly consult with them to discuss any changes, issues, or improvements related to compliance. Auditors can provide guidance to help your organization align with trust service criteria.
10. Resources allocation
Allocate the necessary resources for ongoing compliance initiatives. Ensure that your organization has the budget, staff, and tools needed to maintain a robust control environment.
By adopting a proactive and continuous improvement approach, your organization can stay ahead of the curve regarding SOC 2 compliance. This not only ensures a smoother audit process but also enhances your overall data security and builds trust with customers and partners.
Continuous improvement for future audits is an ongoing commitment to protecting sensitive information and demonstrating your dedication to maintaining strong control measures.
Wrapping Up
In the dynamic arena of information security and compliance, SOC 2 audit exceptions are common. They serve as valuable feedback mechanisms that help organizations improve their security practices and adhere to compliance standards.
By recognizing these exceptions, taking corrective actions, and committing to ongoing improvement, organizations can enhance their data security and build trust with clients, partners, and stakeholders.
SOC 2 audits are not just about compliance; they are an opportunity to strengthen your security posture, demonstrating your dedication to protecting sensitive information. Embrace the audit process as a means to refine your cybersecurity practices and foster a culture of vigilance. Ultimately, addressing SOC 2 audit exceptions proactively sets the stage for future success in an ever-evolving digital landscape.
With Scrut, compliance teams can minimize the manual work required to maintain compliance for SOC 2 audits. Schedule your demo today to see how it works.
Frequently Asked Questions
1. What are SOC 2 audit exceptions? SOC 2 audit exceptions are instances where an organization's controls and processes deviate from the criteria set by the American Institute of Certified Public Accountants (AICPA). These exceptions can occur due to various reasons, including misconfigured controls, lapses in documentation, or non-compliance with security policies.
2. How can organizations proactively identify potential SOC 2 audit exceptions? To proactively identify potential audit exceptions, organizations should conduct internal assessments and readiness checks. This includes reviewing control frameworks, conducting mock audits, and continuously monitoring and improving their security practices. By addressing issues in advance, businesses can reduce the likelihood of encountering exceptions during the SOC 2 audit.
3. What steps should organizations take when they encounter SOC 2 audit exceptions? When organizations encounter SOC 2 audit exceptions, they should immediately address the identified issues. This involves investigating the root causes, developing action plans to rectify the exceptions, and enhancing control implementations. Communication with the auditing firm is crucial to ensure that the exceptions are adequately resolved.
4. What are some common types of SOC 2 audit exceptions? Common types of SOC 2 audit exceptions may include issues related to data protection, access controls, change management, and security incident response. These exceptions vary by industry and organization, but many share similarities in their root causes.
5. How can organizations minimize the impact of SOC 2 audit exceptions and maintain compliance with SOC 2 standards? Organizations can minimize the impact of SOC 2 audit exceptions by promptly addressing and resolving identified issues. Transparency in communication with the auditing firm is essential. Furthermore, a proactive approach to security and compliance, continuous monitoring, and regular internal audits can help reduce the occurrence of exceptions, safeguard the organization's reputation, and maintain compliance with SOC 2 standards.


















