As businesses move their applications and data to the cloud, the need for robust cloud security becomes more important than ever.
Amazon Web Services (AWS), one of the most popular cloud providers, offers a wide range of security features and services to help protect its customers' data and infrastructure. However, security in the cloud is a shared responsibility between the cloud provider and the customer.
Therefore, it's crucial for organizations to implement their own AWS security best practices to ensure the protection of their sensitive data and maintain compliance with industry regulations.
In this article, we'll discuss the top nine AWS security best practices to help you secure your cloud infrastructure and minimize the risk of a security breach.
What is AWS security?
AWS offers several built-in security features as well as services to help organizations secure their cloud infrastructure. This includes network security, encryption monitoring, identity and access management, and compliance.
However, ensuring AWS cloud security is a shared responsibility.
The organizations using AWS are responsible for securing their own data, systems, and applications, whereas the AWS platform is responsible for maintaining the security of the underlying cloud infrastructure.
That's why it's critical for organizations to learn the best practices for AWS security to enhance their cloud security posture and reduce the risk of cybersecurity threats and incidents.
Importance of AWS cloud security
The importance of AWS cloud security cannot be overstated, especially in today's evolving threat landscape.
While the AWS platform offers a reliable, scalable, and a cost-effective solution for organizations to store and process their sensitive data, it's still vulnerable to potential security threats. This is the main reason why strengthening the security posture of your AWS cloud infrastructure is critically important.
Neglecting to do so can result in dire consequences such as cyber attacks, data breaches, legal penalties, and reputational damage.
Without a doubt, every organization using the AWS cloud platform or planning on using it in near future must take proactive measures to secure their cloud infrastructure from potential threats and protect their sensitive data.
AWS cloud security best practices
Now that we've gone through the overview and importance of AWS security, it's time to discuss AWS best practices for security.
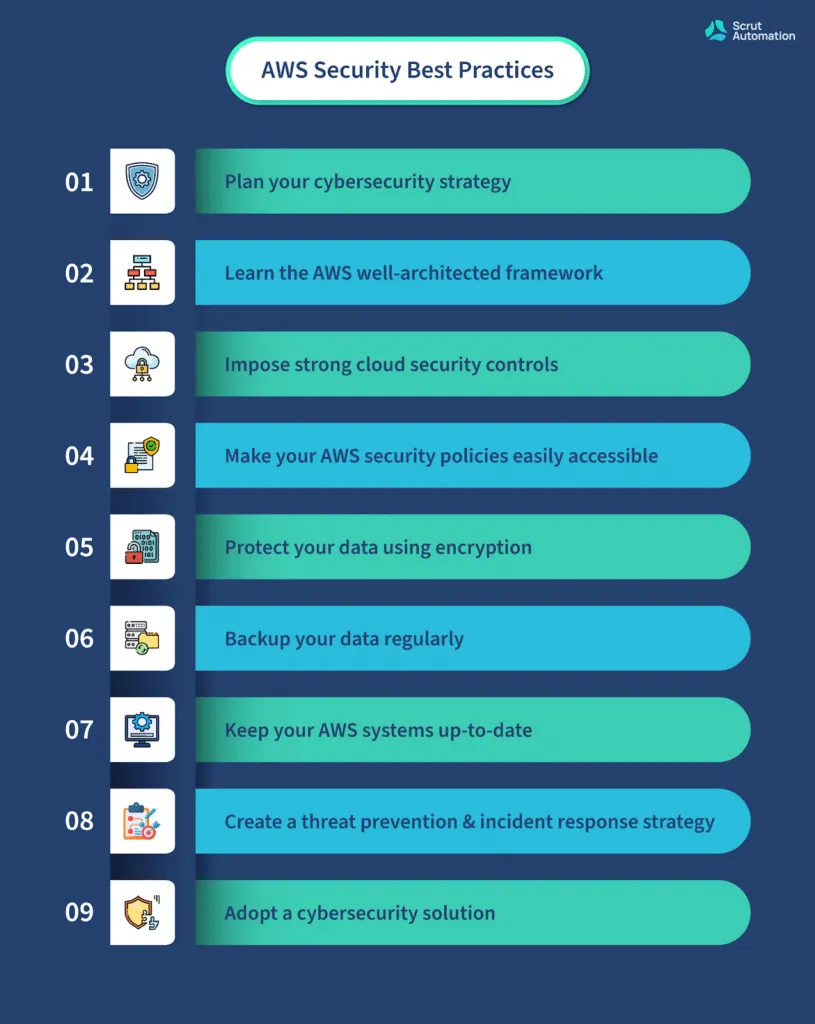
1. Plan your cybersecurity strategy
Having a proper cybersecurity strategy in place is extremely important.
If you're migrating to AWS cloud for the first time, know that it's important to have a well-defined cybersecurity strategy before you start deploying your applications on the AWS cloud.
Your cybersecurity strategy should include a risk assessment, threat modeling, and a mitigation plan. Additionally, you should also identify potential risks and vulnerabilities to your cloud infrastructure and put measures in place to mitigate them.
Doing so will help to maintain compliance with relevant industry standards & regulations and be more proactive in preventing potential cyber attacks.
2. Learn the AWS well-architected framework
Like we mentioned earlier, AWS is not directly responsible for the security of your cloud environment. However, it does provide abundant resources to help organizations strengthen the security posture of their cloud infrastructure.
So if you're planning on adopting the AWS cloud in your organization, you must go through the AWS Well-Architected Framework. It provides guidance and instructions for designing and operating secure and cost-effective systems in the cloud.
Here are the key pillars of AWS Well-Architected Framework.
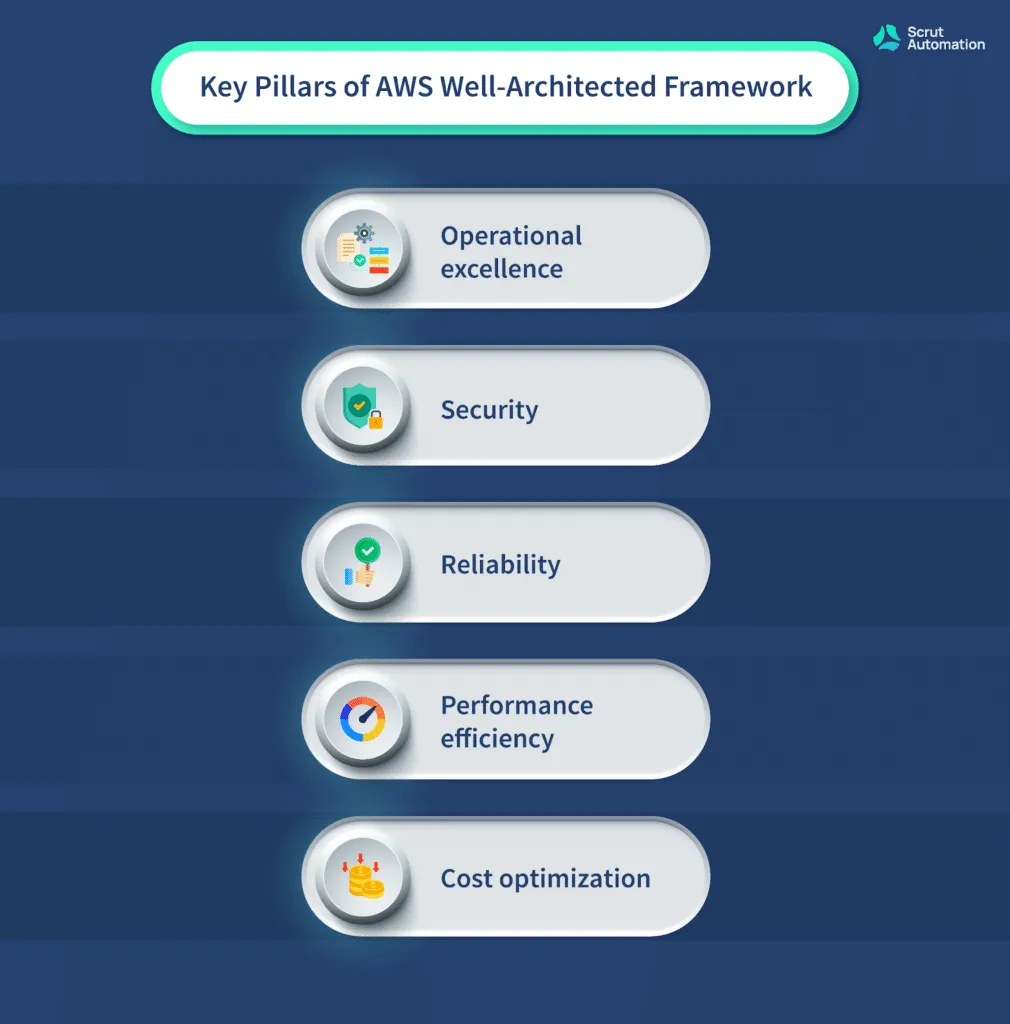
By learning and implementing the AWS well-architected framework in your organization's cloud infrastructure, you can ensure that your applications are safe from potential cyber attacks.
3. Impose strong cloud security controls
Imposing strong cloud security controls is a must for every organization to secure their AWS cloud infrastructure.
After all, you're responsible for securing and protecting your cloud workloads, not AWS.
This means you need to implement proactive measures to ensure that your customer as well as organizational data is protected from cyber attacks.
Following are some of the most important cloud security controls you can consider implementing for minimizing the risks of a security breach:
- Clearly define user roles - Defining user roles can help to ensure that employees have access only to the resources they need to perform their job. This helps to prevent unauthorized access to sensitive data, systems, and applications, which ultimately lowers the risk of a cyber attack.
- Conduct privilege audits - Privilege audits usually involve reviewing and monitoring the user privileges to make sure that they're appropriate and up-to-date. By conducting privilege audits on a regular basis, organizations can identify and prevent potential cybersecurity threats before they turn into a successful security breach.
- Implement a strong password policy - A strong password policy is an essential aspect of cloud security. A strong password is one that is difficult to guess or crack, and it should be changed regularly. Implementing a strong password policy that requires users to create complex passwords and change them frequently can help prevent unauthorized access to your systems and data.
- Use Multi-factor authentication (MFA) - Finally, it is recommended to use multi-factor authentication (MFA). For the uninitiated, MFA adds an extra layer of security that makes it mandatory for everyone to provide additional authentication (i.e. fingerprint or OTP) beyond their password. This helps prevent unauthorized access even if a user's password is compromised.
Incorporating these security controls for your cloud infrastructure can significantly reduce the risk of unauthorized access to your data resulting from poor security practices.
However, it is crucial to ensure consistent enforcement and adherence to these controls throughout your organization for them to be effective in providing protection against security threats.
4. Make your AWS security policies easily accessible
One of the most important aspects of a good cybersecurity strategy is making sure that your AWS security policies are easily accessible to your team.
This can include policies related to access control, network security, encryption, and incident response.
By making these policies accessible, you can ensure that everyone in your organization understands the importance of security and knows how to act in accordance with your policies.
This, in turn, can help to ensure that everyone is aware of the importance of these policies and strictly adhere to them.
5. Protect your data using encryption
Encryption, as you may already know, is a critical component of AWS security.
By encrypting your data, you can prevent unauthorized access and ensure that your data remains secure even if it is intercepted or stolen. But most importantly, encryption is mandatory for certain regulatory compliances as well.
That's why it's critical to encrypt all of your data, even if it's not mandatory for compliance.
AWS offers a number of encryption options, including server-side encryption, client-side encryption, and transit encryption. This helps to make it easy to encrypt sensitive data within your cloud environment.
All you have to do is get acquainted with these options and choose the one that best meets your needs.
6. Backup your data regularly
Backing up your data regularly is absolutely essential and non-negotiable.
You will at least have your peace of mind in case you need to recover your sensitive data in the event of hardware failure, accidental deletion, or even a cyber attack.
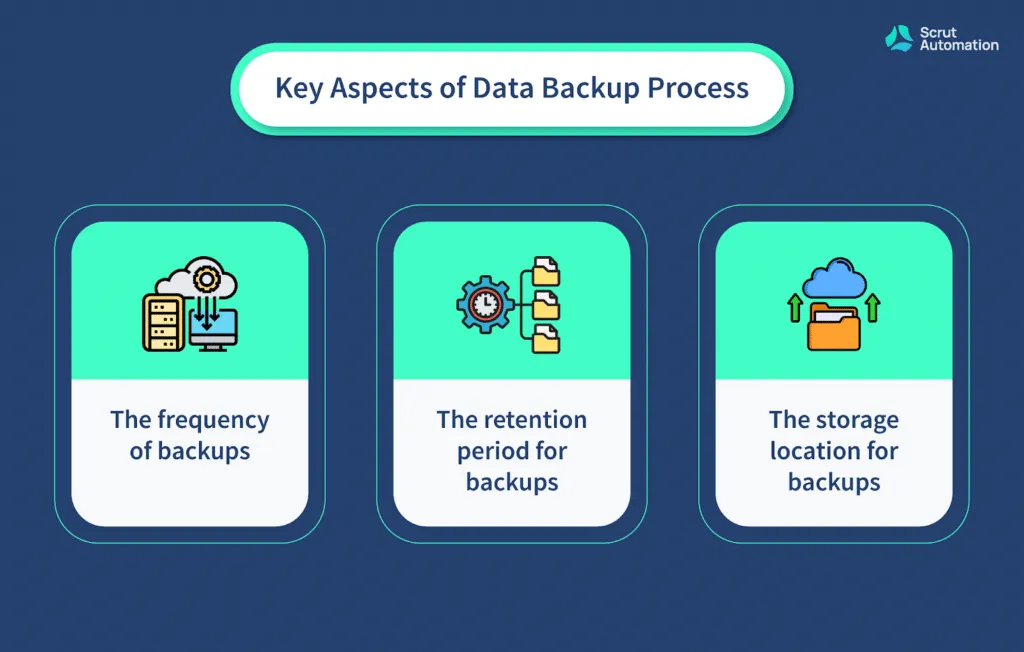
When backing up your data, it's important to consider the following aspects:
- The frequency of backups
- The retention period for backups
- The storage location for backups
Fortunately, AWS already offers various backup options such as Amazon EBS, Amazon S3, and AWS Backup.
Using any of these options, you can store your backups in multiple regions to make sure they're protected at all times against any kind of disaster or data loss.
Just make sure to regularly test your backups to ensure they are working properly. This can help you identify any issues before a real incident occurs and give you confidence in your backup strategy.
7. Keep your AWS systems up-to-date
AWS regularly releases security patches, bug fixes, and updates to address vulnerabilities and protect against new threats.
However, it is your responsibility to keep your AWS systems up-to-date is crucial in maintaining the security of your environment and to protect against vulnerabilities and exploits.
What's more, the AWS platform provides automatic updates for some services through different tools.
Amazon Inspector, for example, is an automated security assessment tool that can help you test the security of your applications and identify any potential vulnerabilities.
AWS Systems Manager is another tool you can consider using for automating the patching of your systems and making sure they're always up-to-date.
On top of all these, you can even configure your environment to receive notifications when new updates are available.
8. Create a threat prevention & incident response strategy
To ensure maximum security of your AWS cloud infrastructure, you have to have a comprehensive threat prevention & incident response strategy in place.
Ideally, this strategy should cover the three key aspects of your cloud security such as threat prevention, detection, and response.
Prevention:
The first step in creating a threat prevention strategy is to identify potential threats and vulnerabilities.
For this, you can consider using AWS's built-in security features (i.e. AWS Shield & AWS WAF) to protect against DDoS attacks and web application attacks.
You can even adopt third-party cloud security tools and services such as antivirus software or intrusion detection systems to further enhance your organization's security posture.
Detection:
Sometimes, even with the best cloud security measures in place, it's still possible for a security breach to occur.
That's why it's important to have a robust detection system in place.
Specifically, we recommend using AWS CloudTrail and Amazon GuardDuty to monitor your environment for suspicious activities.
This can include unauthorized access attempts, unusual traffic, and other similar patterns.
Response:
Along with the detection, you also need to have a clear and effective response plan in place.
This can help to contain the incident, prevent collateral damage, and restore normal operations as quickly as possible.
Additionally, you should also have a clear communication strategy in place to inform relevant stakeholders including your customers and partners about the security incident and its impact.
9. Adopt a cybersecurity solution
Last but not least, you must also consider adopting a robust and reliable cybersecurity solution such as CAASM (Cyber Asset Attack Surface Management) to strengthen the security of your AWS environment.
What is CAASM? — it's a new-age cybersecurity solution that can help you detect and respond to threats quickly, and can provide you with the visibility you need to monitor your environment effectively.
Simply put, adopting a third-party solution provides you with additional layers of security.
This, in turn, can help to protect your organization from potential cyber threats and ensure the security of your critical data, systems, and applications.
Protect your environment with these AWS security practices
Securing your AWS environment requires a multi-layered approach that covers both technical and human factors.
By staying updated on the latest security best practices and fostering a culture of security, you can minimize your risk and protect your infrastructure and applications.
Remember, AWS security is not a one-time task but a continuous process that requires vigilance and commitment.
While the AWS platform provides several security features, it's crucial to implement a multi-layered security approach that covers all aspects of your infrastructure and applications.
FAQs
Is AWS a secure platform?
Yes, AWS (Amazon Web Services) is generally considered a secure platform. It has a comprehensive set of security features and services that are especially designed to help protect customer data and infrastructure from potential cyber threats and vulnerabilities.
How can you make your AWS account more secure?
There are several steps you can take to make your AWS account more secure such as enabling multi-factor authentication (MFA), reviewing and updating access controls regularly, and using encryption for sensitive data to name a few.
How can you securely access and manage AWS instances?
To securely access and manage AWS instances, you should use SSH (Secure Shell) or RDP (Remote Desktop Protocol) to connect & configure security groups, monitor instances for security threats, and keep systems updated with latest patches. These measures will help ensure that your AWS instances are secure and protected against potential threats.
Which is the best tool for AWS security?
There is no single "best" tool for AWS security as it depends on your specific needs and requirements. AWS provides a range of security tools and services that can help you secure your environment. This includes, AWS identity and access management, AWS security hub, AWS GuardDuty, and AWS key management service.