Choose risk-first compliance that’s always on, built for you.
Go back to blogs
Strong cybersecurity as a revenue enabler
Last updated on
February 2, 2024
12
min. read

Security is commonly perceived as a necessary expense, a safeguard against potential threats both in the physical and digital realms. The traditional view categorizes security measures as a cost center, essential for compliance and risk mitigation.
However, this perspective overlooks the potential of strong cybersecurity practices as a strategic contributor to revenue generation.
When cybersecurity is overlooked from the revenue angle, organizations risk facing detrimental consequences, including potential revenue loss due to security breaches, damage to brand reputation, and loss of customer trust.
In contrast, embracing robust cybersecurity practices becomes a proactive investment in safeguarding revenue streams and cost reduction. Cybersecurity acts as a foundation for building and maintaining customer trust, enhancing brand reputation, and ensuring uninterrupted business operations.
By fostering a secure digital environment, organizations can create a competitive advantage, attract more customers, and ultimately contribute to revenue growth.
In this blog, we delve into the transformative shift in perspective that propels security from being perceived as a mere cost to a dynamic revenue generator, unpack the ways in which security can actively contribute to revenue growth, and suggest key best practices to empower your organization in reaping the substantial benefits of robust security measures.
Security is seen as a necessary expense
Historically, security has been positioned in business books as a line item under “expenses.” Whether it’s investing in physical security measures like surveillance systems and access controls or cybersecurity protocols to fend off digital threats, these expenditures are typically viewed through a lens of compliance and risk avoidance.
Organizations allocate budgets for security primarily to meet regulatory requirements, protect sensitive data, and avoid the potentially devastating consequences of security breaches. While this perspective is valid, it falls short of recognizing security’s broader impact on business success.
Cybersecurity is a must in a trust-driven economy
In today’s business environment, where trust is a currency in high demand, security transcends its traditional role. Customers, partners, and stakeholders now view security as an integral part of the overall brand value.
With increasing incidents of data breaches and cyber-attacks, individuals and organizations are more cautious about where they place their trust. Consequently, businesses that demonstrate a commitment to robust security practices gain a competitive edge by fostering trust and credibility.
In addition to its role in fostering trust and credibility, security also plays a pivotal role in cost reduction. Robust security practices serve as a preventive measure against potential data breaches and cyber-attacks, mitigating the financial repercussions associated with such incidents.
By investing in proactive security measures, businesses can avoid the exorbitant costs of incident response, legal actions, regulatory fines, and the extensive efforts required to rebuild customer confidence post-breach.
Thus, security emerges not only as a guardian of trust but also as a strategic tool for minimizing financial risks and preserving the overall financial health of an organization.

The multi-faceted impact of data breaches on organizations
A data breach casts a wide-ranging shadow over an organization, profoundly affecting its financial stability, reputation, and operational efficiency. The immediate financial consequences are significant, encompassing costs associated with incident response, legal proceedings, regulatory fines, and potential settlements.
Reputational damage is swift and severe, with trust eroding among customers, partners, and stakeholders. The fallout extends to customer trust erosion, leading to customer churn and a potential loss of lifetime value. Legal and regulatory ramifications further compound the challenges, with lawsuits and fines adding to the post-breach burden.
Operationally, the disruption is palpable as incident response activities and corrective measures divert resources and attention, impacting productivity and customer service.
The long-term consequences are equally impactful. Increased security costs become an ongoing concern as organizations invest in fortifying their cybersecurity infrastructure.
Intellectual property loss, potential supply chain risks, and the compromised morale and productivity of employees contribute to a complex web of challenges. Rebuilding trust and restoring the organization’s standing in the marketplace become prolonged endeavors, impacting its ability to attract new customers, secure partnerships, and maintain a competitive edge.
The cautionary tale of the Equifax data breach
In 2017, Equifax, one of the largest credit reporting agencies globally, suffered a massive data breach that exposed the personal information of nearly 147 million individuals. The breach included sensitive details such as names, Social Security numbers, birth dates, addresses, and in some cases, even driver’s license numbers.
The fallout from the Equifax breach was swift and severe. Individuals who entrusted their financial information to Equifax faced the risk of identity theft and financial fraud. The incident not only eroded trust among consumers but also had far-reaching consequences for Equifax’s brand reputation.
In the aftermath of the breach, Equifax faced legal scrutiny, regulatory fines, and a significant loss of customer confidence. The incident served as a wake-up call for businesses, highlighting the real-world consequences of failing to prioritize and safeguard sensitive data.
Equifax delayed public notification of its data breach for six weeks, and its executives faced allegations of insider trading. It was disclosed that they had sold Equifax stock before informing the public about the breach.
The Financial Conduct Authority fined Equifax £11,164,400 for jeopardizing the security of UK consumers’ data.
The Equifax breach exemplifies how a single security incident can reverberate through an entire industry, prompting customers and stakeholders to reevaluate where they place their trust and regulators to prosecute shoddy security practices.

Reframing security as a value-driven proposition
To unlock the full potential of security in contributing to revenue generation, organizations must shift their mindset. Rather than viewing security as a mere cost center, it should be recognized as a value-driven proposition. This shift involves acknowledging the following key aspects of security’s role in business success:
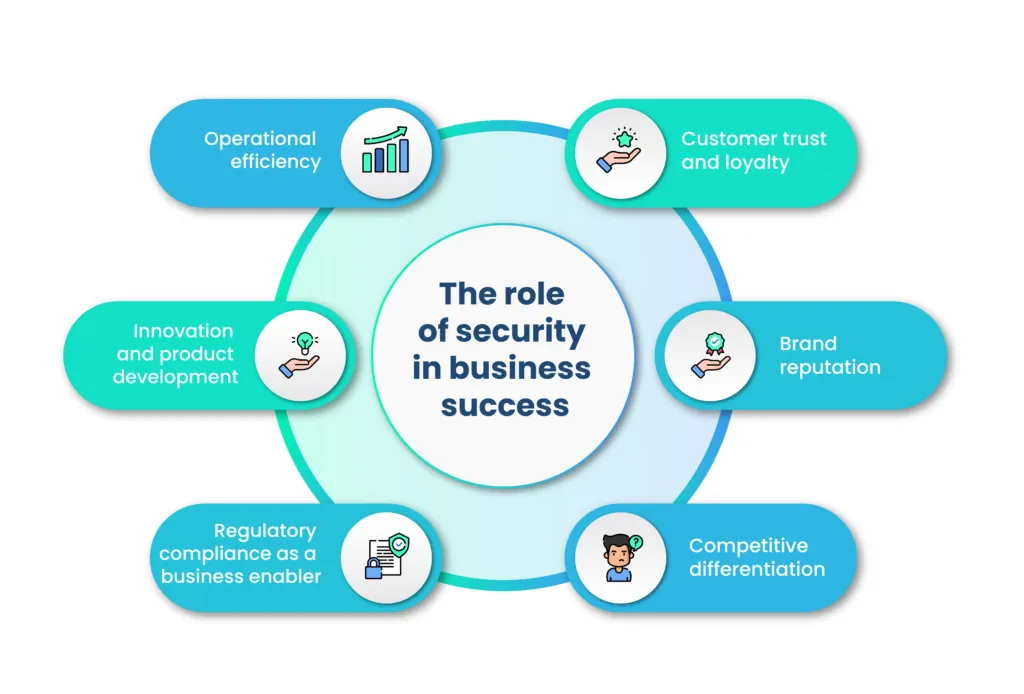
A. Customer trust and loyalty
In a trust-driven economy, customer trust is paramount. Security breaches not only compromise data but erode trust, often irreparably. On the flip side, robust security practices enhance an organization’s credibility. Customers are more likely to engage with businesses they trust, leading to increased loyalty and repeat business. Security, therefore, becomes a revenue enabler by solidifying customer relationships.
B. Brand reputation
Security incidents can tarnish a brand’s reputation, resulting in financial losses and customer churn. On the other hand, a strong security posture enhances brand reputation. Organizations that prioritize and communicate their commitment to security create a positive perception in the market. A reputable brand attracts more customers, partners, and investment opportunities, directly impacting revenue streams.
C. Competitive differentiation
In crowded markets, where products and services often seem interchangeable, security can be a powerful differentiator. Businesses that invest in and communicate their robust security measures stand out as reliable and trustworthy. This differentiation can sway customer decisions in favor of the more secure option, providing a competitive advantage that translates into increased market share and revenue.
D. Regulatory compliance as a business enabler
While regulatory compliance is often seen as a box to check, it can be leveraged as a business enabler. Meeting and exceeding compliance standards not only avoids penalties but also opens doors to new markets. Many industries require vendors and partners to adhere to specific security standards. By proactively aligning with these standards, organizations position themselves to access a broader customer base and secure lucrative partnerships, directly impacting revenue potential.
E. Innovation and product development
Security is not just about protecting existing assets but also about fostering innovation. A secure environment provides a stable foundation for research and development. When organizations are confident in their ability to protect intellectual property and sensitive information, they are more likely to invest in groundbreaking innovations. These innovations, in turn, can lead to the development of new revenue streams and market opportunities.
F. Operational efficiency
Security measures, when integrated into business processes, contribute to operational efficiency. The reduction in security incidents translates to uninterrupted operations, minimizing downtime and associated costs. An efficient business operation can respond more quickly to market demands, capitalize on emerging opportunities, and ultimately drive revenue growth.
Best practices for embracing strong cybersecurity as a revenue enabler
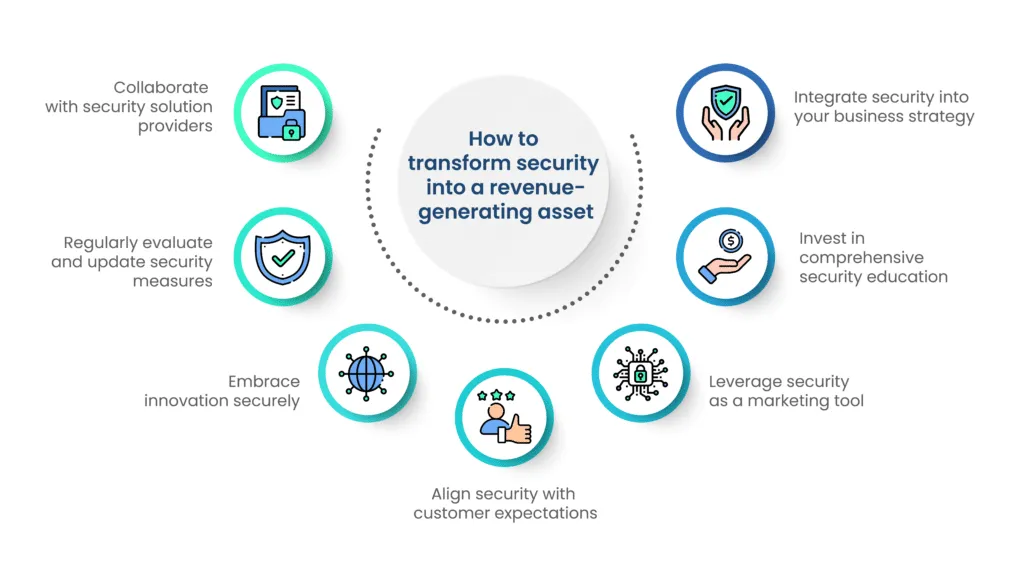
To fully harness the revenue-enabling potential of security, organizations can adopt best practices that go beyond compliance and risk avoidance.
Here are key strategies to transform security into a strategic asset for revenue generation:
A. Integrate security into your business strategy
Security should be integrated into the core of the business strategy. Align security objectives with overall business goals, ensuring that security is not an afterthought but a fundamental component of decision-making processes.
Example
Microsoft has consistently integrated security into its business strategy. With the introduction of its cloud platform, Azure, Microsoft made security a foundational element.
The company emphasizes security in its marketing materials, positioning Azure as a secure cloud solution. By aligning security with broader business goals, Microsoft has attracted enterprises seeking a secure and scalable cloud environment.
B. Invest in comprehensive security education
Educate employees at all levels about the importance of security. A well-informed workforce is more likely to adhere to security best practices, reducing the risk of human error that can lead to security incidents.
Example
Google invests significantly in comprehensive security education for its employees. The company provides extensive training on security best practices, including phishing awareness and data protection.
Google’s security education programs contribute to creating a cybersecurity-aware workforce, reducing the risk of security incidents stemming from human error.
C. Leverage security as a marketing tool
Communicate security measures as part of the organization’s marketing strategy. Highlighting security certifications, compliance, and transparent practices can serve as a powerful marketing tool, attracting security-conscious customers.
Example
Salesforce, a leading customer relationship management (CRM) platform, leverages its robust security measures as a key marketing tool. The company highlights its adherence to industry standards and certifications, such as ISO 27001.
Salesforce’s transparent approach to security serves as a competitive advantage, attracting businesses that prioritize data protection and compliance.
D. Align security with customer expectations
Understand customer expectations regarding security and tailor security practices to meet those expectations. By aligning security measures with customer priorities, organizations can enhance customer satisfaction and loyalty.
Example
Amazon, with its e-commerce and cloud services, aligns its security practices with customer expectations. The company places a strong emphasis on data privacy and security, especially in its Amazon Web Services (AWS) division.
By consistently meeting and exceeding customer expectations for secure and reliable services, Amazon has built trust and loyalty, directly impacting its revenue.
E. Embrace innovation securely
Foster a culture of innovation within the organization while maintaining a secure environment. Security should be an enabler of innovation, providing the confidence to explore new ideas and technologies without compromising data integrity.
Example
Tesla, known for its innovative electric vehicles and energy solutions, embraces innovation securely. The company has implemented robust security measures to protect its intellectual property, including advanced encryption and access controls.
Tesla’s commitment to security enables it to innovate confidently, knowing that sensitive information remains protected.
F. Regularly evaluate and update security measures
The threat landscape evolves continuously, and security measures must evolve in tandem. Regularly evaluate and update security protocols to address emerging threats and maintain a proactive security posture.
Example
Meta, the parent company of Facebook, regularly evaluates and updates its security measures in response to evolving threats.
The company invests in advanced threat detection technologies and collaborates with the cybersecurity community to identify vulnerabilities.
By staying proactive in the face of emerging threats, Meta ensures the security of user data and maintains user trust, crucial for its advertising-driven revenue model.
G. Collaborate with security solution providers
Engage with security solution providers that offer innovative tools and platforms that can help demonstrate your organization’s security posture. Solutions like Scrut’s Trust Vault can demonstrate your company’s commitment to security in a dynamic and effective manner, contributing to enhanced customer trust and potential revenue growth
Conclusion
In conclusion, security is not merely a necessary expense; it is a strategic asset with the potential to drive revenue growth and business success.
As organizations navigate the complex landscape of modern business, reframing security as a value-driven proposition is essential.
By building and maintaining trust through robust security practices, businesses can differentiate themselves, foster customer loyalty, and unlock new revenue streams.
Solutions like Scrut’s Trust Vault exemplify the transformative potential of security, providing a dynamic platform that streamlines processes, enhances transparency, and positions security as a catalyst for revenue generation. Schedule a demo today to learn more about its benefits!
FAQs
1. Why is cybersecurity often perceived as a necessary expense?
Cybersecurity is traditionally seen as a cost center primarily focused on compliance and risk mitigation. Organizations allocate budgets to safeguard sensitive data and meet regulatory requirements, viewing security measures as an essential but unavoidable expense.
2. What consequences can organizations face when cybersecurity is overlooked from the revenue angle?
Neglecting cybersecurity from a revenue perspective can lead to detrimental consequences, including potential revenue loss due to security breaches, damage to brand reputation, and loss of customer trust. It limits the ability to capitalize on opportunities in the digital marketplace.
3. How does robust cybersecurity contribute to revenue generation?
Embracing robust cybersecurity practices becomes a proactive investment that safeguards revenue streams. It acts as a foundation for building and maintaining customer trust, enhancing brand reputation, and ensuring uninterrupted business operations. This, in turn, creates a competitive advantage, attracts more customers, and contributes to revenue growth.
4. Can overlooking cybersecurity impact cost reduction?
Yes, overlooking cybersecurity can result in significant costs related to incident response, legal actions, regulatory fines, and efforts to rebuild customer confidence post-breach. Robust security practices serve as a preventive measure, reducing financial risks and preserving the overall financial health of an organization.
5. How can security contribute to brand reputation and trust in a trust-driven economy?
In a trust-driven economy, security is integral to brand reputation. Demonstrating a commitment to robust security practices enhances credibility and fosters trust among customers, partners, and stakeholders. This positive perception attracts more customers, ultimately impacting revenue streams.
Table of contents


















