The user access review is a systematic process that involves periodically assessing and validating the access privileges granted to both employees and third-party individuals for various resources such as data, applications, and systems. The primary goal of this review is to strike a balance: granting users the appropriate access rights necessary for a productive work environment while ensuring that no one has access to resources they do not require for their job responsibilities.
It’s crucial for any organization to categorize its data based on relevance and restrict access exclusively to authorized individuals. This practice serves as a crucial safeguard, as it helps in mitigating potential vulnerabilities within the organization. By limiting access to only what is necessary, it reduces the potential attack surface and, consequently, the likelihood of a cybersecurity breach. User access review stands as one of the most dependable procedures for ensuring information security compliance. Let’s delve deeper into the specifics of user access reviews.
How to conduct a user access review?
An organization must conduct a user access review periodically. This means, depending on the requirement of the organization, the access review should be conducted quarterly, half-yearly, or yearly on a regular basis. If there are security incidents, then the review must be conducted when the organization discovers the intrusion. Plus, a review is needed if the organization faces any major administrative or strategic change. An organization must follow the steps below to conduct these user access reviews.
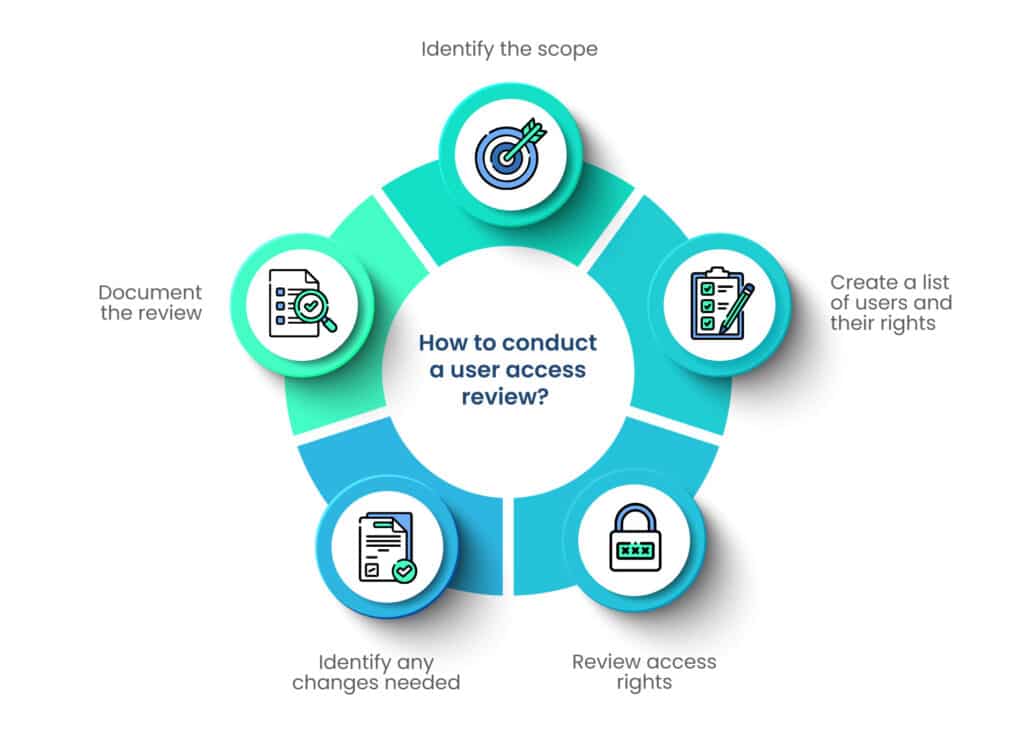
Step 1: Identify the scope
The scope of user access review depends on many factors, including the size of the organization, its industry, the sensitivity of its data, and the laws and regulations it falls under. These factors differ for each organization; therefore, the scope of user access review will also differ.
The scope should include the active as well as the inactive accounts in the system. It must include an unbiased review of all data access given to the employees, contractors, and third parties.
Step 2: Create a list of users and their rights
In this step, the organization must create a list of all of its users, including the employees who are not working for the company anymore but have access to the organization’s database. This employee list should be bifurcated into sections according to the roles and responsibilities of each employee and the data access they would need to carry out that role. Always remember to remove the rights of the employees once they leave the organization; otherwise, they can use them for malicious purposes.
Data should also be segregated on the principles of relevance and sensitivity. If the data is more sensitive, it should be shared with fewer employees and vice versa. Then the employees should be given access to the data as per the requirement.
Step 3: Review access rights
In this stage, the organization reviews the access rights on paper to know whether the rights given to the employees are excessive. If the management finds that the employees are given more rights than they need, the rights can be rescinded.
The authorized employees can access the data by using the credentials provided by the organization. If they don’t have the right credentials, they can’t access the data—it’s that simple. The employees must protect these credentials and not share them with anybody else.
Step 4: Identify any changes needed
After deciding which employee will get how much access, the organization should give access rights. It is crucial to observe the employees’ work after giving them access to know whether they are able to perform their duties or not.
If an employee is not able to perform their duties due to the lack of access, the management can consider giving them more access. A test run can be conducted to know if all the employees have adequate access. If the management finds any loopholes during the test run, they can be solved before implementing the system.
Step 5: Document the review
The last step is to document the whole access review process for future use. If there is any type of confusion in the future regarding access rights, the documents can give clarification. In addition to this, in case there is a data breach, the management can pinpoint the areas from where the data has been stolen. It can also seal off the data flow to minimize the effects of the data breach. A clearly documented access review can help the management take quick steps.
How can user access review help in infosec compliance?
User access reviews are crucial for the organization to maintain information security. They also help in following compliance standards and frameworks. Some examples of infosec compliance that require regular user access reviews are given below.
HIPAA
Health Insurance Portability and Accountability Act (HIPAA) is a US federal law that sets the standards for protecting sensitive patient information. This information is called protected health information or PHI. People who are expressly authorized are given access to the PHI of the patients.

The security rule of HIPAA requires the covered entities to maintain appropriate safeguards to protect PHI while maintaining confidentiality, integrity, and availability (CIA) of information. Moreover, the administrative safeguards recommended by HIPAA are designed to limit the access of PHI to those who need it to perform their duties. It requires the covered entities to have “security management processes” to implement measures to “reduce risk and vulnerabilities” to the data. Therefore, the organizations covered under HIPAA must conduct regular user access reviews.
PCI-DSS
Payment Card Industry Data Security Standard (PCI-DSS) is a global standard for organizations that hold credit cards and cardholders’ data. It was designed by major credit card companies to protect the data of credit cardholders and is widely accepted worldwide. The following are some of the requirements by PCI-DSS regarding user access reviews:
- PCI-DSS requirement 7: Data should be accessible to authorized users only. The principles of “least privilege” and “need-to-know” basis must be followed throughout the organization. No data that is not required for the performance of duties should be shared with the employee.
The organization must define access requirements for each role and provide access to data based on these requirements. If any exceptions are there to these requirements, they must be documented with the reasons for such exceptions. Except for the users who are expressly authorized to access the data, the setting must be tuned to “deny all.” All the affected parties should know and follow these rules.
- PCI-DSS requirement 12: This requirement mandates the organization to review the access policy at least once a year or when there are environmental changes. This requirement also specifies rules to use alternate technologies and devices in the organization to ensure that the user access review is not just for the data.
SOX
Sarbanes-Oxley Act (SOX) is a federal law of the United States of America that sets rules and requirements for corporate governance and financial reporting. User access review is one of the most important requirements of SOX to ensure the accuracy and reliability of an organization’s financial information. Financial information should be released only to a handful of people who need the data to perform their responsibilities.
Section 404 of SOX requires public companies to establish and maintain an adequate internal control structure and procedures for financial reporting. It requires the management to verify the effectiveness of the company’s internal controls over financial reporting (ICFR). Although SOX Section 404 doesn’t specifically mention user access review, it is deemed to be included in the internal controls. While conducting 404 audits, the companies must assess their access reviews to ensure that the financial information passed on to the stakeholders is true and fair.
What are the benefits of user access reviews?
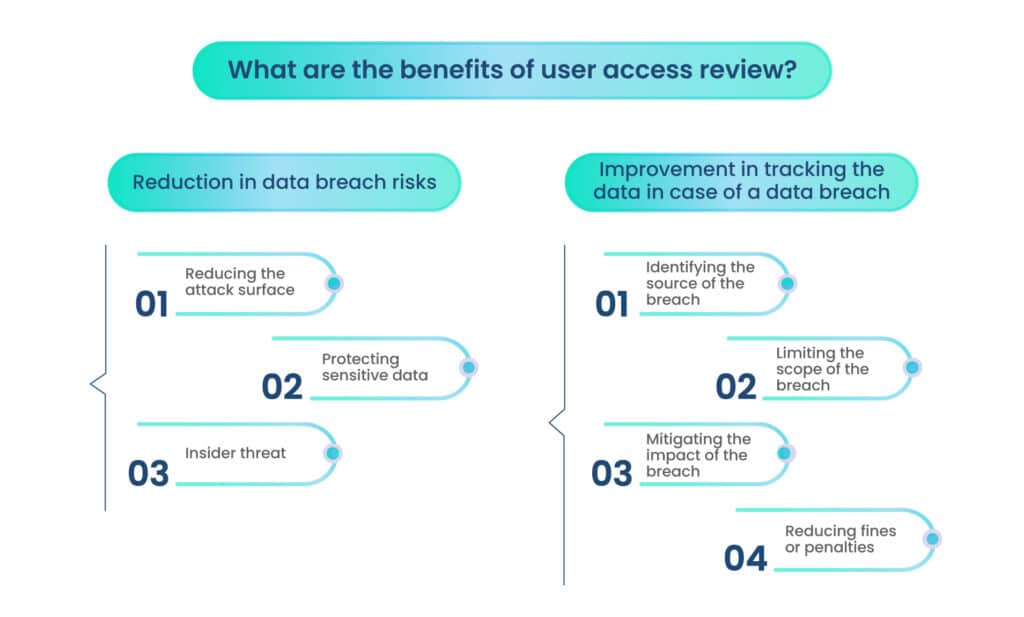
Reduction in data breach risks
In The Cost of Data Breach Report – 2022, IBM reported that 21% of the breaches were due to human error, including those caused unintentionally through the negligence of employees or contractors. The report also confirms that with adequate identity and access management, the organization can save an average of $224,396 from the total cost of a data breach.
The statistics elevate the need to assess human behavior to protect the organization’s systems. The data breach risks can be mitigated by:
A. Reducing the attack surface
User access reviews limit information access to authorized people only, thereby reducing the attack surface and the data breach risks. An attack surface is a sum of all the network parts that an attacker can use to gain entry into the organization’s systems.
B. Protecting sensitive data
If the organization loses sensitive information about the customers or other stakeholders, it can also become a victim of secondary attacks. Therefore, it is necessary to prevent attackers from getting their hands on sensitive data. User access reviews ensure that the sensitive data is accessible to the bare minimum of people. Hence, it can be protected better.
C. Insider threat
IBM also reported that about 12% of the breaches were caused due to insider threats. Insider threats include employees or contractors who are given access to the organization’s network to get the job done; however, they leak the information to the attacker due to malicious intentions or negligence.
User access reviews help the organization assess privileges given to the employees periodically. Thus, the management can ensure the visibility of the data flow. The employees are also aware that only some of them have access to sensitive information, and if leaked, their activities will be observed under a microscope. Therefore, they will think twice before leaking the information.
Improvement in tracking the data in case of a data breach
We saw how the user access review could improve the cybersecurity posture of an organization. But what happens when the organization becomes a victim of a data breach? User access reviews can assist the organization in this case too.
As the management periodically carries out user access reviews, it has a clear-cut understanding of which data is stored where and who is able to access this data. In case of a breach, the management needs to take the following actions related to the user access review.
A. Identifying the source of the breach
The management can easily verify which users had access to the compromised data and where the attack began. Whether there is a malicious insider or negligence on an employee’s part can be known faster.
B. Limiting the scope of the breach
The management has clear visibility of the data flow in the organization. When a breach is discovered, the management can stop the flow of information from that point onward to prevent additional data from being stolen.
C. Mitigating the impact of the breach
The management can reduce the impact of the breach by revoking access to compromised accounts, notifying affected users, and implementing effective measures for a more secure future.
D. Reducing fines or penalties
When there is a breach, the organization must report it to the regulatory authorities. When they investigate the breach, the regulators often look into how compliant the organization has been. Penalties and fines are levied if they find that the organization has not complied with the regulations. User access review is one of the core requirements of all the regulations, and by not carrying it out, the organization increases its chances of fines and penalties.
Conclusion
In a nutshell, the user access review is a process of providing data access on a least privilege basis. If an employee doesn’t need the information to perform their duties, they are not given access to the data.
Organizations must make detailed documentation of user access reviews to form a policy to protect their data. The user access review is part of compliance standards and frameworks, including HIPAA, PCI-DSS, and SOX.
Moreover, user access reviews also help the organization prevent data breaches by reducing the attack surface and increasing the visibility of the data flow. Additionally, user access reviews can be helpful in the event of a data breach, as the management can follow through with the breach effectively. It helps in reducing the fines and penalties, as the management can prove that it has taken adequate measures to prevent a data breach.
Take the first steps towards user access review, or get your process verified by experts at Scrut. Schedule a demo to learn how Scrut can help you manage compliance requirements.
FAQs
1. What is a user access review?
A user access review is the process of ensuring that only authorized users have access to data and systems. It is useful in ensuring data privacy and security.
2. What are the main benefits of user access reviews?
The main benefits of user access reviews are a reduction in data breaches and an improvement in responding to data breaches.
3. How often should you conduct a user access review?
Typically, user access reviews are conducted annually. However, in case there is a breach or a change in organizational structure, they are conducted soon after the event.





































