The National Institute of Standards and Technology Cybersecurity Framework (NIST CSF) is a cornerstone of NIST’s cybersecurity initiatives, which plays a crucial role in developing and maintaining cybersecurity standards and guidelines. The CSF provides a structured approach to managing and mitigating cybersecurity risks and offers a flexible framework that can be tailored to suit the unique needs of various organizations, making it an invaluable tool in guiding them toward effective cybersecurity practices.
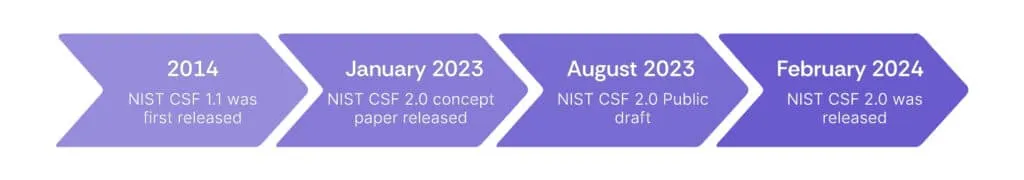
NIST has recognized the evolving nature of cybersecurity threats and technology trends, and as a result, it has periodically updated the CSF to ensure its relevance and effectiveness.
The proposed revisions in NIST CSF 2.0 represent a major update to the framework, aligning it with current cybersecurity challenges and providing organizations with updated guidance on safeguarding their digital assets.
In this blog, we will delve into the key changes and enhancements introduced in CSF 2.0, shedding light on how these revisions can benefit organizations in their cybersecurity efforts.
Background information
The NIST CSF version 1.1 is a comprehensive guideline that provides organizations with a structured approach to managing and improving their cybersecurity posture. It was initially released in 2014 and received an update in version 1.1 in April 2018.

Scope of NIST CSF 2.0
The expansion of the scope in NIST CSF 2.0 signifies a significant evolution of the framework compared to its previous version.
Here’s an elaboration of how the expanded scope aims to address a wider range of cybersecurity challenges and risks faced by organizations:
NIST CSF 2.0 functions

NIST CSF 2.0 continues with the five original functions, namely Identify, Protect, Detect, Respond, and Recover. And introduces a new function that serves as the core component of the framework – Govern. These functions provide a structured approach to managing and improving an organization’s cybersecurity posture. Here are the NIST CSF 2.0 functions:
1. Identify
This NIST CSF function involves understanding and managing cybersecurity risks. Organizations must identify the assets they need to protect, the potential threats they face, and the vulnerabilities in their systems. It sets the foundation for effective risk management.
2. Protect
The Protect function focuses on implementing safeguards to protect against cybersecurity threats. This includes measures such as access control, data encryption, and security training for personnel. It aims to ensure the security of critical assets.
3. Detect
Detecting cybersecurity events and incidents is crucial. This NIST CSF function involves continuous monitoring and timely detection of security breaches or anomalies. Early detection allows for a rapid response to mitigate the impact.
4. Respond
In the event of a cybersecurity incident, the Respond function guides organizations in responding effectively. It includes activities like incident response planning, communication, and containment of the incident to minimize damage.
5. Recover
The Recover function addresses the restoration of normal operations after a cybersecurity incident. It involves recovery planning, system restoration, and the analysis of the incident to prevent future occurrences.
6. Govern
NIST CSF 2.0 introduces a new function called “Govern.” This NIST CSF function emphasizes the importance of cybersecurity governance and management. It involves establishing leadership, policies, and procedures to ensure the organization’s cybersecurity efforts are well-managed and aligned with business objectives.

Two new appendices for NIST CSF 2.0
The NIST Cybersecurity Framework 2.0 introduces two new appendices, which are intended to offer additional resources and information to assist organizations in effectively implementing the framework:
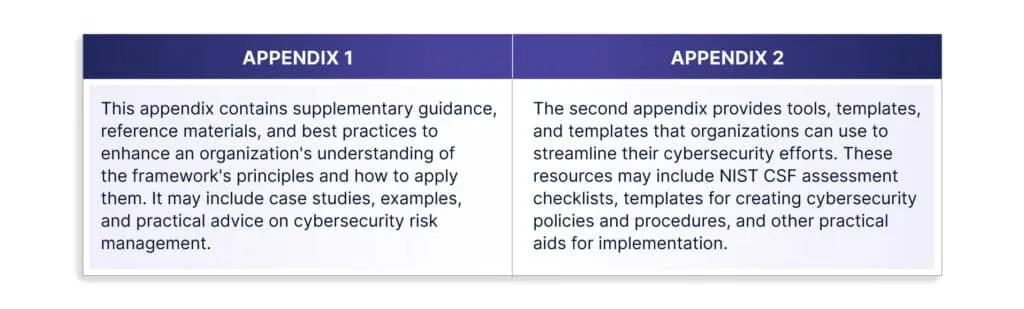
These new appendices are valuable additions to the NIST Cybersecurity Framework as they aim to provide organizations with comprehensive support in their cybersecurity endeavors. By offering both guidance and practical tools, the framework becomes a more versatile and accessible resource for organizations looking to enhance their cybersecurity practices and manage risks effectively.
These appendices reflect NIST’s commitment to continuously improving the framework to address evolving cybersecurity challenges and provide organizations with the necessary tools and guidance to protect their information and assets.
CSF 2.0’s focus on enhancing cybersecurity supply chain risk management
Managing the supply chain has been a widespread challenge for cybersecurity experts. If your company collaborates with supply chain partners or outsources services, you need to be vigilant about third-party risks.
CSF 2.0 aims to address the growing need to minimize third-party risks by broadening its coverage of the supply chain.
NIST CSF 2.0 is set to incorporate more specific outcomes related to Cybersecurity Supply Chain Risk Management (C-SCRM) to assist organizations in tackling third-party risks.

Improved and enhanced features of NIST CSF 2.0
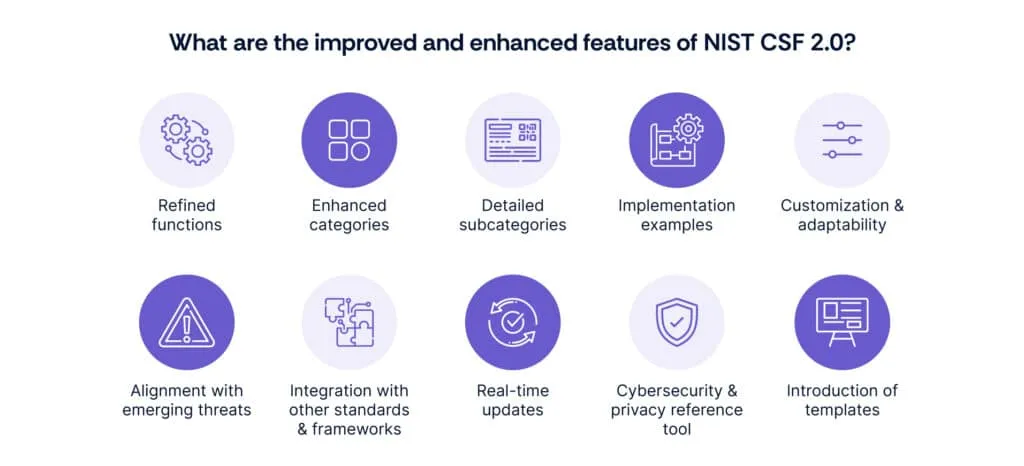
The NIST CSF 2.0 is anticipated to introduce several improved and enhanced features to offer better support to organizations in their cybersecurity efforts. These enhancements aim to provide organizations with more comprehensive and adaptable tools for managing cybersecurity risks effectively:
1. Refined functions
CSF 2.0 refines the core NIST CSF functions that guide organizations in structuring their cybersecurity practices. These functions serve as the foundation for building a robust cybersecurity strategy.
2. Enhanced categories
The framework includes updated and expanded categories that help organizations categorize and prioritize their cybersecurity activities. This enhancement will enable organizations to address a wider range of cybersecurity challenges.
3. Detailed subcategories
CSF 2.0 introduces more detailed subcategories, providing organizations with specific guidance on how to implement cybersecurity measures effectively. These subcategories offer actionable recommendations for enhancing security.
4. Implementation examples
The updated framework includes a wealth of implementation examples that illustrate how different organizations have successfully implemented cybersecurity practices. These real-world cases can serve as valuable references for organizations looking to improve their cybersecurity posture.

5. Customization and adaptability
CSF 2.0 emphasizes the importance of customization and adaptability, allowing organizations to tailor the framework to their specific needs and environments. This flexibility ensures that the framework remains practical for a wide range of organizations.
6. Alignment with emerging threats
The updated framework takes into account emerging cybersecurity threats and challenges, ensuring that organizations can address current and future risks effectively.
7. Integration with other standards and frameworks
CSF 2.0 provides guidance on integrating with other cybersecurity standards and frameworks, making it easier for organizations to harmonize their cybersecurity efforts. It will continue collaborating with the International Organization for Standardization (ISO), as numerous ISO documents make references to the CSF, in order to maintain the integration of documentation.
NIST has several cybersecurity and privacy-related frameworks, such as the Risk Management Framework, Privacy Framework, National Initiative for Cybersecurity Education (NICE) Workforce Framework for Cybersecurity, and Secure Software Development Framework. These frameworks currently have connections with the CSF. These frameworks continue to exist separately but will be cited as guidance in CSF 2.0 and related materials like mappings. This change is suggested because CSF 1.1 was released before the Privacy Framework.
8. Real-time updates
Over time, some CSF resources became outdated because updates weren’t reflected in the documentation. NIST is moving to online updatable references in CPRT to address this and is seeking community input for CSF mappings, including for CSF 2.0.
9. Cybersecurity and privacy reference tool
CSF 2.0 was presented using the NIST Cybersecurity and Privacy Reference Tool (CPRT). CPRT offers an enhanced digital interface to access NIST cybersecurity references and a more adaptable way to grasp the connections among standards, guidelines, frameworks, and technologies.
10. Introduction of templates
NIST wants to create a simple template for CSF Profiles, offering a format and key areas to include. Organizations can still use their own formats but can use these templates to simplify Profile development. NIST encourages both public and private sectors to share or create example profiles for various sectors, threats, and use cases.
Also Read: Best Software for NIST Compliance in 2025
Winding up
In summary, the proposed revisions in NIST CSF 2.0 mark a significant advancement in cybersecurity frameworks. With an expanded scope, enhanced features, and a focus on emerging challenges like supply chain risks, CSF 2.0 equips organizations with updated guidance to navigate today’s cyber threats.
As cybersecurity threats evolve, NIST’s commitment to continuous improvement ensures CSF 2.0 remains a valuable resource for organizations, helping them mitigate risks and safeguard their digital assets effectively.
Ready to elevate your cybersecurity posture with the latest advancements in NIST CSF? Explore the power of Scrut’s cutting-edge solutions – Click here to schedule a demo and fortify your defenses today!
FAQs
1. How does NIST CSF 2.0 differ from its previous version?
CSF 2.0 introduces new functions, expanded appendices, and enhanced features to provide more comprehensive and adaptable tools for managing cybersecurity risks effectively. It also focuses on cybersecurity supply chain risk management and introduces improvements like refined functions and enhanced categories.
2. What are the key changes introduced in NIST CSF 2.0?
NIST CSF 2.0 expands its scope to encompass a wider range of cybersecurity challenges, introduces a new “Govern” function emphasizing cybersecurity governance, and enhances features such as implementation examples and customizable templates.
3. How does NIST CSF 2.0 address supply chain risks?
NIST CSF 2.0 incorporates specific outcomes related to Cybersecurity Supply Chain Risk Management (C-SCRM), helping organizations minimize third-party risks by integrating C-SCRM across various functions within the framework core and extending the scope of C-SCRM outcomes within existing categories.





































