JupiterOne is a cyber asset attack surface management (CAASM) platform. It enables security teams to solve persistent asset visibility and vulnerability challenges.
With JupiterOne, security teams can make a full inventory of all their assets, get a centralized view of all their cloud entities, find their most important business assets, and rank their risks across hybrid and multi-cloud environments.
It gives you a complete, graphical view of your threat landscape. This lets you find security loopholes quickly, fix them in order of importance, and reduce your cyber asset attack surface.
Since CAASM is an emerging technology, there is not much information available on CAASM tools. Thus, it’s challenging to select one.
So, we have listed the best 8 JupiterOne alternatives to make it easy for you to make an informed decision.
Before we discuss the alternatives, let’s first see JupiterOne key features and drawbacks.
Key features of JupiterOne
JupiterOne integrates with cloud infrastructure, DevOps pipeline, and security solutions to collect and present reliable asset data in one place. This comprehensive, unified view enables security teams to effectively manage cyber assets across hybrid and multi-cloud environments.
Now, let’s see the key features of JupiterOne.
- JupiterOne assists security teams in addressing persistent asset visibility and vulnerability issues.
- With JupiterOne, users can gain complete visibility across all the cyber assets.
- Users can get an understanding of the relationships between cyber assets and quickly identify security and compliance issues.
- The platform identifies the scope of vulnerabilities, threats, and gaps.
- The team members can query consolidated data to answer complex questions about their IT environment.
- JupiterOne continuously monitors changes in your IT environment and helps you stay compliant.
Although JupiterOne is one of the major players in the CAASM space, it is not the best option for every case.
Now let’s see some of the drawbacks of JupiterOne.
Drawbacks of JupiterOne
- Can be overwhelming due to a lot of features; to be able to get the most benefit out of it, you need to spend a considerable amount of time learning about its features.
- There may be instances of missing data from SaaS tools integrations.
- Inaccurate mapping of relationships between assets is a frequent problem. Asset relationship mapping is the foundation of how a CAASM platform works. Unless the mapping is correct, other features like search would not give accurate results.
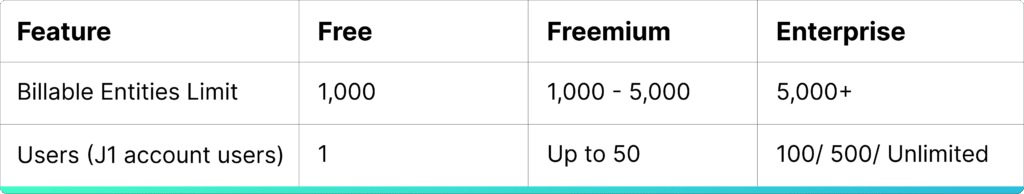
- Since the pricing is based on number of assets, it is expensive as most organizations have cyber assets in tens of thousands.
- You may face performance issues due to rate limiting. Rate limiting is used by software vendors to prevent users from sending more than a particular number of requests in a period of time.

- No module on vendor risk management.
Now, let’s discuss the best 8 JupiterOne alternatives.
Scrut – The Best Alternative to JupiterOne

Scrut’s CAASM enables you to gain visibility of all your cyber assets, empowering IT and security teams to overcome cyber asset visibility and vulnerability challenges.
The platform
- aggregates all your cyber assets and
- provides insights into a single unified dashboard,
… which acts as a strong foundation for all security activities.
Key Features of Scrut

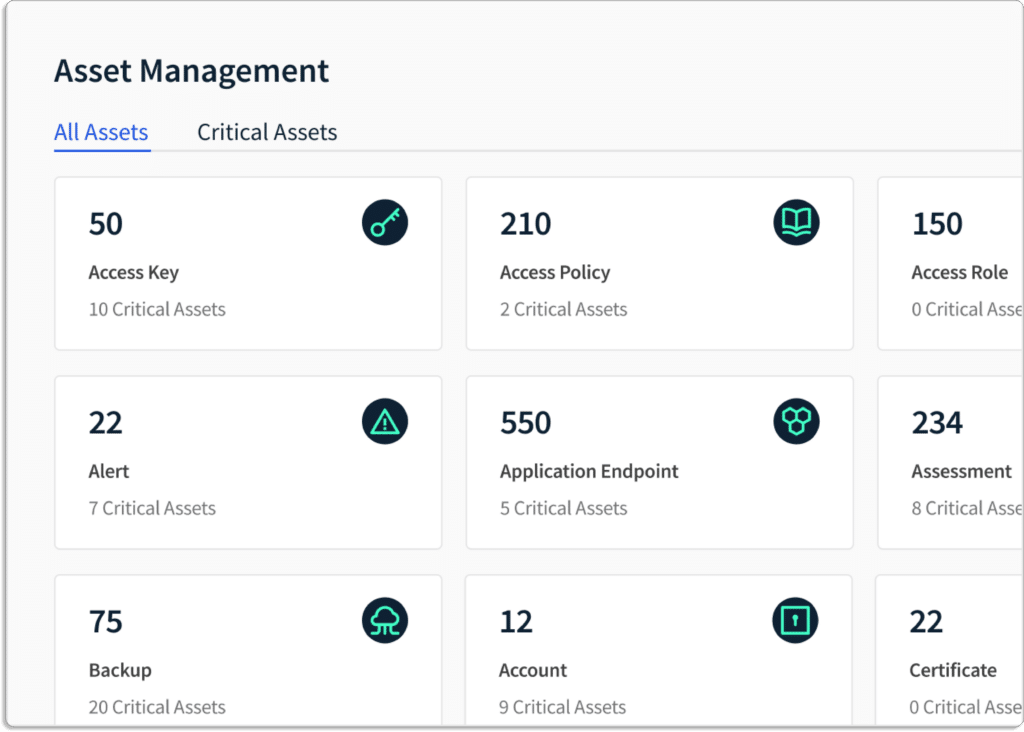
- Centralized Visibility of All Cyber Assets – Scrut assists you in discovering and consolidating all of your cyber assets, regardless of where they are located.
The platform automatically creates a complete and updated asset inventory. It provides a centralized view of all cloud entities to identify critical business assets, and prioritize risks across your hybrid and multi-cloud environments.
The platform offers complete visibility into your external and internal attack surfaces to improve security control coverage and trigger custom, automated response actions.
- Minimize Your Attack Surface From a Single Platform – As your cloud grows, so will your threat landscape. You can drill into asset details, identify the areas for threats, and drastically reduce your cyber attack surface with Scrut’s interactive visual asset map.
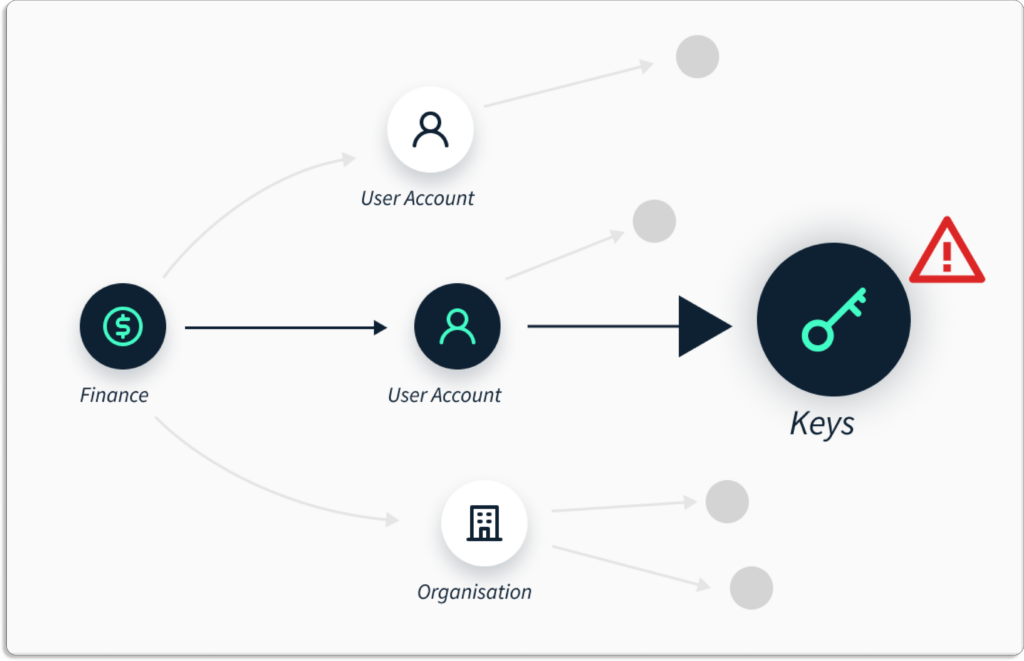
- Derive Meaningful Contextual Insights – Scrut stores your organization’s cyber asset data—and the relationship data between those assets. This data helps you to gain deeper security insights based on contextual knowledge.
The data is presented in a graphical manner for quick visualization. So, it’s easy to find exact security issues in your environment, and answer security and compliance questions.
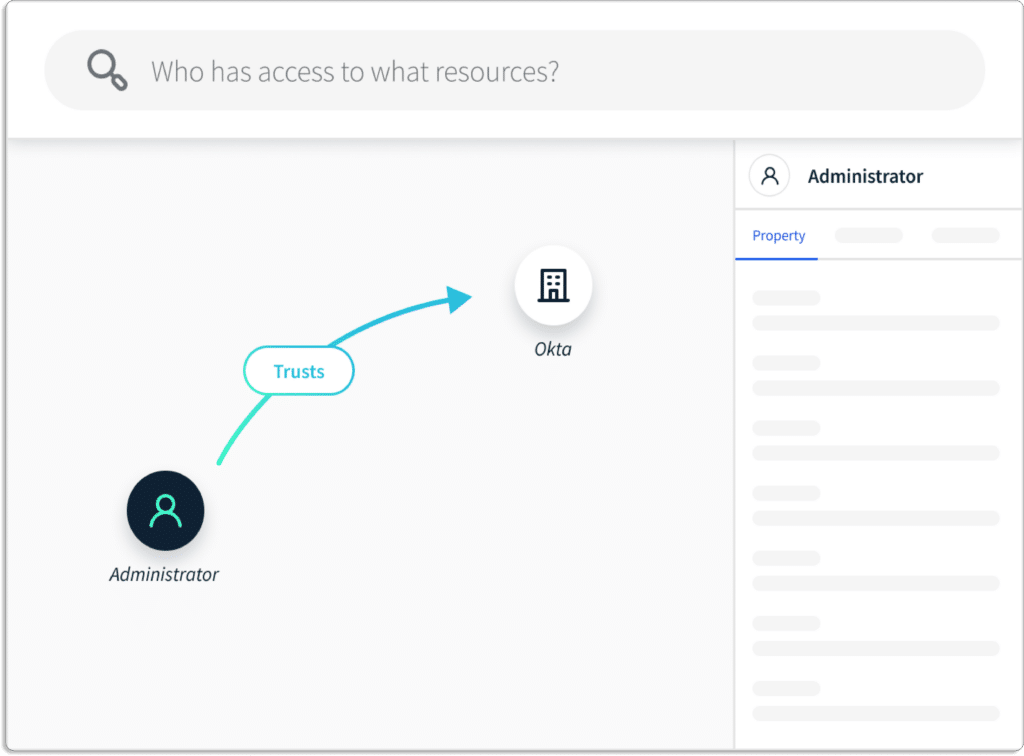
- Streamline Complex Asset Landscapes – Scrut consolidates and normalizes asset data across distributed, multi-cloud environments. Users can search for information from various cloud providers, applications, and services.

- Identify and Prioritize Critical Risks – You can continuously monitor your cyber asset landscape for issues affecting business-critical assets. The platform provides alerts based on data-driven rules to help you identify problems and monitor drift in your environment. Scrut allows you to concentrate on the issues that are important to you.

Customer Rating
- G2 – 5/5
Rest 7 JupiterOne Alternatives
1. Axonius
Axonius provides complete visibility into the external and internal attack surface by aggregating, normalizing, and deduplicating data from security solutions to improve security control coverage and trigger custom, automated response actions. The platform constantly updates assets inventory based on information from hundreds of already deployed sources.
Key Features
- Simple to identify coverage gaps, verify controls and rules, and accelerate investigations with the help of the Axonius Query Wizard.
- Axonius gives you a comprehensive and up-to-date list of all your assets.
- The platform automatically applies security policies to protect assets against attack.
- With Axonius Security Policy Enforcement Center, users can decide the custom actions they want to trigger automatically whenever an asset deviates from policies.
Pros
- It is easy to create and save queries to reconcile assets.
- This software solution aggregates CSV reports and API calls to various data sources.
Cons
- Occasionally connectors don’t sync up properly and show more than one cyber asset overlaid in an entry.
Customer Rating
- Capterra- 5/5
2. Noetic
Noetic takes a proactive approach to manage cyber assets and controls, allowing security teams to see, understand, and optimize their cybersecurity posture. The platform assists security teams in better understanding cyber risks in their environment by creating a map of the relationship between all of their assets and entities.
Key Features
- With Noetic, all assets and entities within the enterprise are covered by unified visibility across cloud and on-premises by giving real-time insights on security posture and cyber risk.
- Noetic platform provides security coverage gaps by mapping the relationships between assets in the landscape.
- It offers fully integrated orchestration and automation workflows to identify issues once and address them continuously.
- It provides real-time analytics to prioritize security updates for critical assets and applications.
- Through standardized, extendable APIs, Noetic integrates with third-party products to provide a complete extensible schema for new use cases.
3. Panaseer
Panaseer CAASM is a single centralized intelligence platform that combines data from your vulnerabilities, endpoints, and other security sources to provide complete visibility of your asset inventory and identify vulnerability control gaps.
Key Features
- Custom and automated data queries allow you to identify security control gaps and prioritize remediation campaigns.
- Panaseer CAASM platform lets you focus on fixing the vulnerabilities that pose the most business risk by enriching your data with business context, asset ownership, and relationships.
- Provides continuous up-to-date security inventory by integrating with existing asset management (such as CMDBs) and endpoint management tools (such as SCCM).
Pros
- Panaseer provides auto-generated reports in real time. The auto-generated report includes detailed insights about security metrics, investments, risk, and areas for improvement.
- The platform allows for the creation of analytical reporting dashboards with insights into cyber risk areas and a single snapshot view for quick decision-making and is simple to set up.
Cons
- Limited integration capability with alerting and incident monitoring tools.
Customer Rating
- Gartner- 4.2/5
4. Brinqa
Brinqa is a cyber risk management platform that presents a complete and accurate picture of your IT and security ecosystem with the Brinqa Cyber Risk Graph. The platform integrates all relevant cybersecurity information into a standardized, searchable risk model.
Key Features
- Brinqa Cyber Risk Graph provides a real-time representation of an organization’s infrastructure and apps and precisely describes interconnections between assets and business services.
- The platform serves as a knowledge source for organizational cyber risk.
- The platform provides a common framework and language for all cybersecurity data.
- It creates a medium through which any system or process can be integrated and enable risk analysis and management.
Pros
- It is a powerful tool for collecting, correlating, and analyzing security data to deliver actionable insights and streamline standard security processes.
- Simple to use.
Customer Rating
- G2- 4.6/5
5. Wiz
Wiz’s agentless scanning technology provides complete vulnerability visibility through a single cloud-native API connector, allowing workloads to be continuously assessed without needing ongoing maintenance.
The platform detects hidden nested Log4j dependencies and CISA KEV exploitable vulnerabilities in virtual machines, containers, container registries, serverless functions (Lambda), and virtual appliances.
Furthermore, it prioritizes remediation by concentrating on the resources that have been effectively exposed or have a large blast radius.
Key Features
- It provides context for the risks identified by the Wiz Security Graph and detects suspicious events and threats using Wiz Research’s constantly updated rules.
- Custom feeds can be used to extend agentless malware scanning and collect samples, workload logs, and other forensics from cloud workloads.
- It provides built-in dynamic scanning that validates external exposures by simulating what a potential attacker sees outside your environment.
Pros
- Wiz’s simple integration allows the team to implement the technology quickly and better understand the cloud footprint. This enables users to prioritize efforts in hardening and securing cloud assets in a timely and decisive manner.
- The platform provides complete visibility in cloud attack surfaces. When presenting threat landscapes to executives and newcomers alike, prioritizing issues that provide context rather than raw CVSS scores is extremely valuable.
Cons
- Wiz does not yet support API discovery and inventory.
Customer Rating
- G2- 4.9/5
6. Aquasec
Aqua secures development and production applications across VMs, containers, and serverless workloads. Aqua DTA categorizes detected behaviors into MITRE ATT@CK framework categories, allowing SecOps and forensics teams to see the entire kill chain. With this understanding, the security teams can strengthen weaknesses in their security infrastructure.
Key Features
- The platform detects and remediates vulnerabilities and malware as soon as possible, allowing only safe artifacts to pass through your CI/CD pipeline.
- Aquasec uses a secure container sandbox to detect and mitigate advanced threats and unknown malware in container images.
- Identify hidden risks in your container CI pipeline.
- Safely detect sophisticated malware before deployment.
- The platform protects your containerized applications from malicious attacks.
Pros
- Aquasec allows users to see detailed results and filter them based on specific properties.
- The platform’s threat analysis and mitigation reports include automatic scan visualizations that ensure the information needed to prevent malicious activity.
Cons
- The Aqua platform’s UI/UX has several issues, particularly with the sign-up/sign-in flow, authentication, alerts, and results display.
Customer Rating
- G2- 4.5/5
7. Sevco
Sevco is a real time cyber asset management platform that offers a cutting-edge solution to asset intelligence that improves your security posture and IT procedures. It automatically combines your inventory sources and gives you a holistic, accurate, and up-to-date picture of your asset ecosystem.
The platform automatically combines data about your inventory from several sources to give you a continuous and unified view of it.
Furthermore, its rigorous methodology produces an accurate source of truth to publish to your current IT and security systems by giving quality enhancements for tools in your environment.
Key Features
- Identifies security tool deployment and coverage gaps and improves incident response by providing unparalleled, detailed asset state information at any time.
- The platform generates asset telemetry for changes detected by a constant data pipeline and deploys in minutes using native API integrations with your existing tools.
- Sevco’s cloud-native platform automatically scales into meet your needs and provides a data collection and processing pipeline by integrating to existing sources via native APIs.
- Dashboard displays live asset inventory via interactive Venn diagrams to quickly highlight gaps and risks.
- Data publication feeds into existing processes and procedures in systems such as CMDB and SIEM/SOAR platforms.
Pros
- Sevco provides so much insight for product licensing, such as log-in and log-out information, which can be used to detect anomalies and reclaim product licenses.
Cons
- Sometimes, queries need adjustments.
Customer Rating
- Gartner- 4.9/5



.webp)

































