Choose risk-first compliance that’s always on, built for you.
Go back to blogs
How to Choose a CSPM Tools -Ask These 5 Questions
Last updated on
February 5, 2025
12
min. read

When looking for a CSPM platform, one of the basic questions to ask yourself is whether the tool supports all the cloud platforms you use or not.
Though most CSPM tools now support all the popular cloud providers (AWS, GCP, and Microsoft Azure), if you use any other cloud vendors (like IBM Cloud, Oracle Cloud, Alibaba Cloud, Digitial Ocean, or any other cloud), you must check this in the beginning.
Additionally, you need to check if the CSPM tool supports multi-cloud and multi-account cloud environments, as most organizations (81%) use multiple cloud service providers.
Even if you are not working with multiple cloud providers today, there are chances that you will work with different cloud providers in future for various reasons—your company’s merger with another company, your company may acquire another company, or to keep costs low and reduce dependency on a particular vendor. In a survey, 90% of companies using multi-cloud strategy said that the strategy is working well for them.
However, a multi-cloud architecture is complex and managing it is difficult. This is because cloud providers have different security settings for the same services. When using services from multiple cloud providers, you also need to manage an increasingly high number of configurations and ensure all of them are correct. Thus, the chances of misconfigurations are also high.
In a survey, 45% of the respondents said they are facing security as a one of the key challenges when using a multi-cloud strategy.
Therefore, your selected CSPM tool must be able to connect with all your cloud providers simultaneously. If it cannot, it wouldn’t be able to find misconfigurations either.
Similarly, many companies have different cloud accounts for production and development environments. AWS (the largest player in the cloud market) recommends creating multiple accounts.
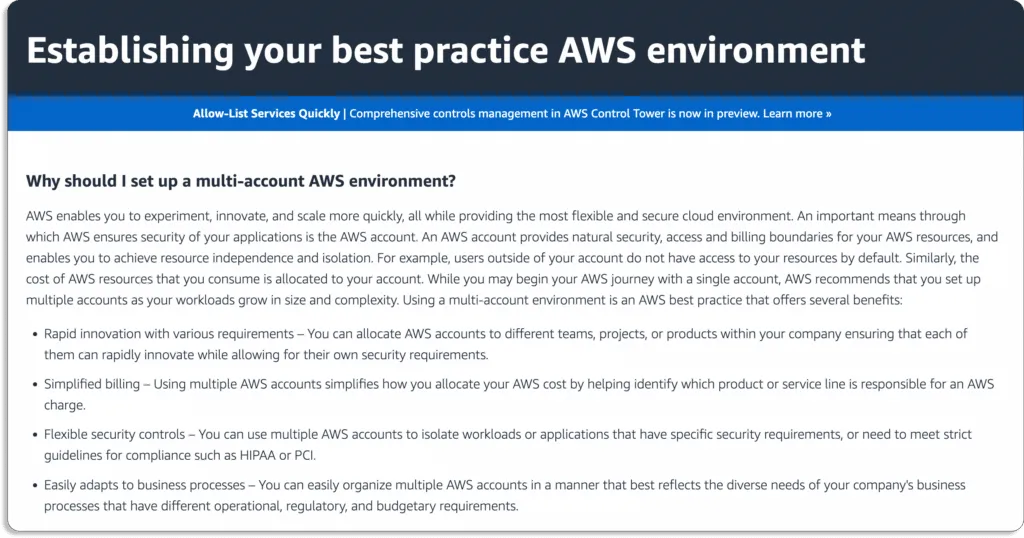
Therefore, the CSPM tool must also capable of connecting with multiple cloud accounts, apart from multi-cloud vendors at once.
Scrut Cloud Security can be connected with multi-cloud and multi-account cloud environments. In less than 10 minutes, you can integrate your entire cloud infrastructure across AWS, Azure, GCP, and others to the Scrut platform.
Once connected, the CSPM tools can automatically discover and build an inventory of all your cloud assets, which becomes the foundation of your cloud security. Unless a CSPM tool discovers a cloud asset, it cannot check its configuration, which brings us to our first question.
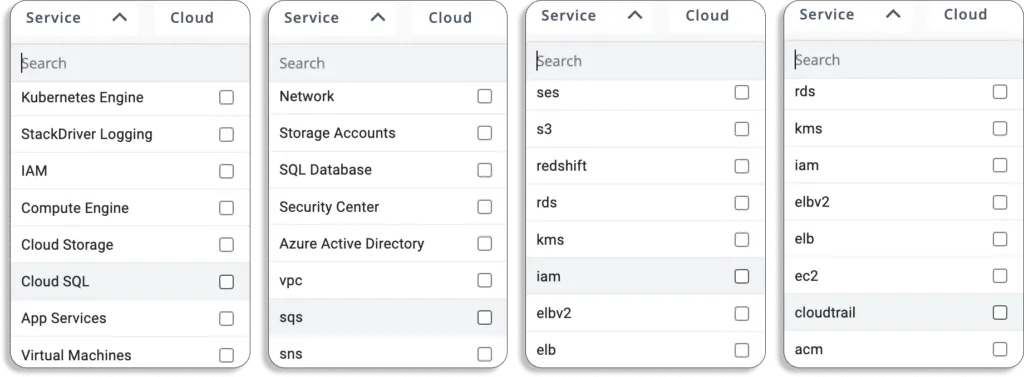
1. Does it have any limitation on the number of services it covers? Or What cloud services are covered?
In the past, CSPM technologies were primarily used to monitor storage and computing resources. However, today enterprises are increasingly utilizing various service types, such as serverless, containers, Kubernetes, etc. As a result, checking the services a CSPM tool covers becomes crucial.
At Scrut, we cover all the major services and help you establish full-stack security for all your cloud-native deployments.
Below we have listed all the services that we cover, and this list keeps on increasing regularly as we cover more services.
2. How good is the cloud security monitoring capability?
In its simplest form, a CSPM tool scans the cloud assets and checks their configurations against a list of cloud service configuration rules in its database. The better the list is in its database, the better the CSPM tool would be.
When it comes to cloud security monitoring, the most comprehensive list of cloud security rules available today is CIS benchmarks from the Center of Internet Security.
CIS benchmarks are a set of globally recognized and consensus based best practices. These guidelines are developed with a global community of security experts. They help security practitioners implement and manage their cyber security defenses—and proactively safeguard against emerging risks.

These benchmarks are available for most cloud providers, like AWS, GCP, Azure, Oracle Cloud, and IBM Cloud.
Scrut Cloud Security automatically tests your cloud configurations against 200+ cloud controls across CIS benchmarks to maintain a strong InfoSec posture. It also provides simple automated workflows to fix the misconfigurations as they occur. You can also customize your security controls for scanning.
At Scrut, we take a different approach to security and compliance. We believe that if you have run your groundwork for cloud security, you are better prepared to get compliant. Compliance is a byproduct of being secure.
3. How actionable are the insights from the CSPM tool? Or Does it help you in risk prioritization?
Monitoring your cloud is not the end goal of buying a CSPM tool. Ultimately, you need actionable insights from your CSPM tool for any drift from your security or compliance posture.
It’s common to have such drift in the cloud and nobody wants their CSPM tool to send them thousands of alerts for the same.
There is a risk associated with every misconfiguration. Most CSPM tools send unnecessary alerts for every misconfiguration resulting in a spammy and undesirable experience.
When we talk to CISOs, one of the major problems they tell us is that of alert fatigue. Their teams already receive a lot of alerts every month from various security tools, and they cannot keep up with all of them.
If your CSPM tools join the bandwagon, the chances are high that you might miss out on important notifications.
Therefore, your CSPM tools should be capable of providing context behind misconfigurations. With the context into these misconfigurations, you can identify those alerts that require your utmost attention. In short, your CSPM tool should be capable of risk prioritization.
Now, let us see how risk prioritization works in Scrut Cloud Security.
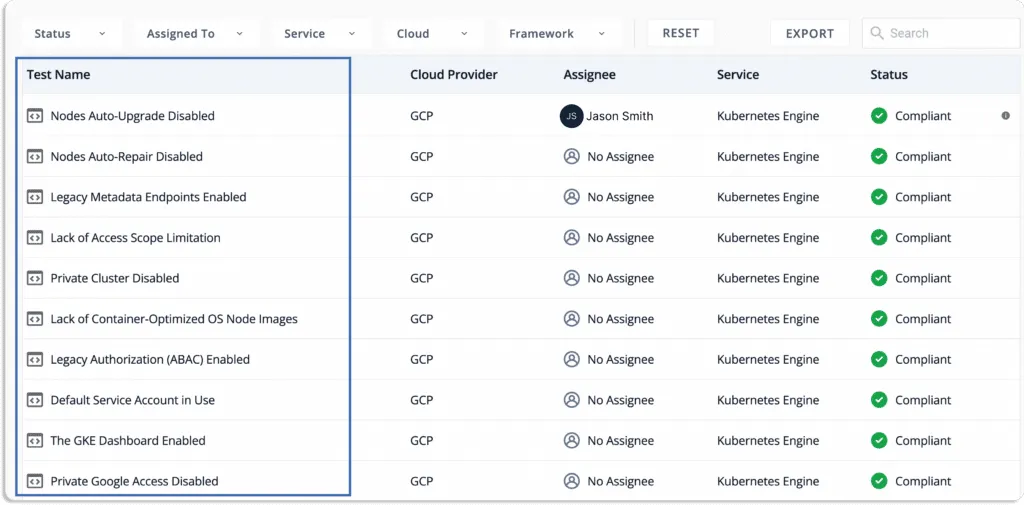
In Scrut, the overall status of your cloud environment is displayed on the main menu of the tests module.
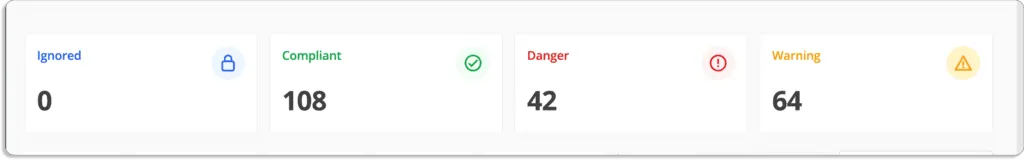
Scrut also gives a status for every cloud resource. And when any cloud resource is not compliant with your security requirements, you will see any of these status:
- Danger – Most critical issues, and thus need foremost attention. Work on these first.
- Warning – After you’ve addressed the issues marked as “danger”, you can move on to these.
- Low – These are low-priority risks and can be addressed later
You can filter the misconfigurations by status.
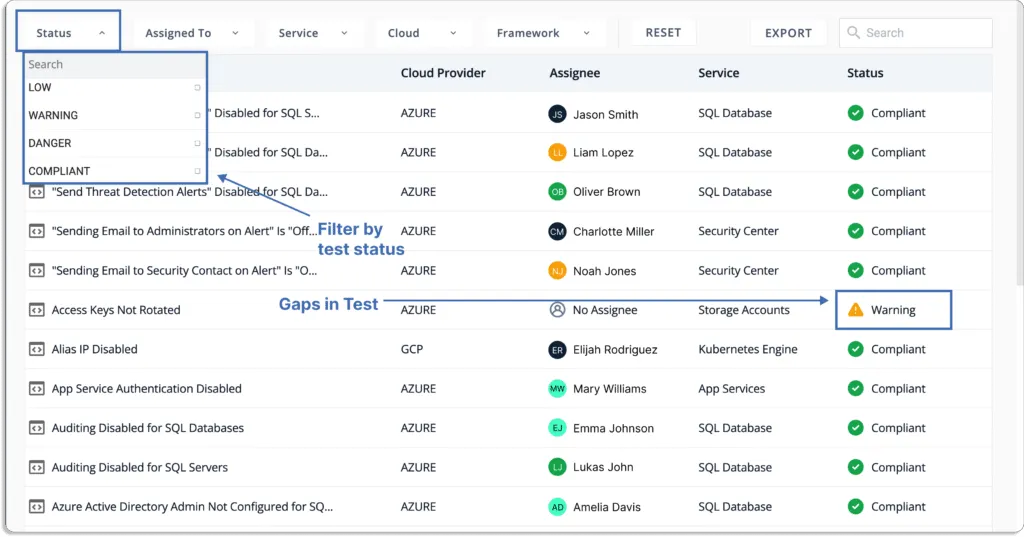
Moreover, Scrut maps these misconfigurations with your overall risk management plan. Hence, you also know their priority not just in your cloud security posture but your overall information security posture.
For example, look at these two cloud-related items from a risk register.
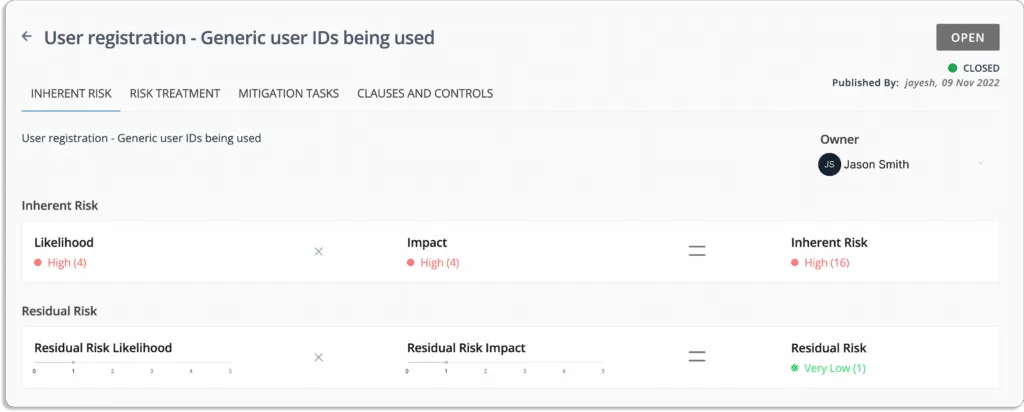
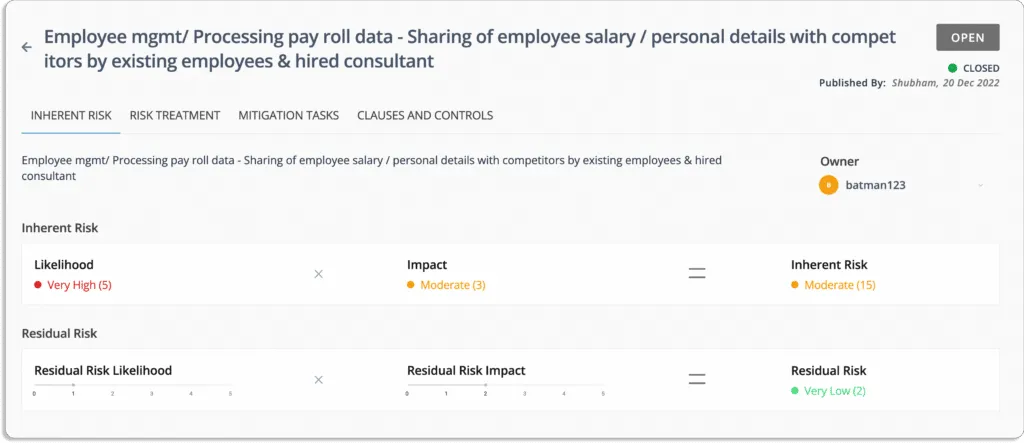
Scrut not only scores the risk items automatically, but also helps you with their remediation. Once the misconfigurations are identified and prioritized, you should not be wondering how to solve them.
4. How does it help you with the remediation of non-compliant resources?
CSPM solutions also help in remediating the misconfiguration issues in different capacities. Some CSPM solutions give your action items on how to solve the issues while a few others automatically remediate it for you, if provided the necessary permissions.
Note that the automatic remediation feature comes with equally steep pricing. So you need to balance the both.
When it comes to Scrut Cloud Security, it ensures that your public cloud accounts are always compliant and secure. When misconfigurations occur, Scrut alerts you with actionable recommendations for remediation.
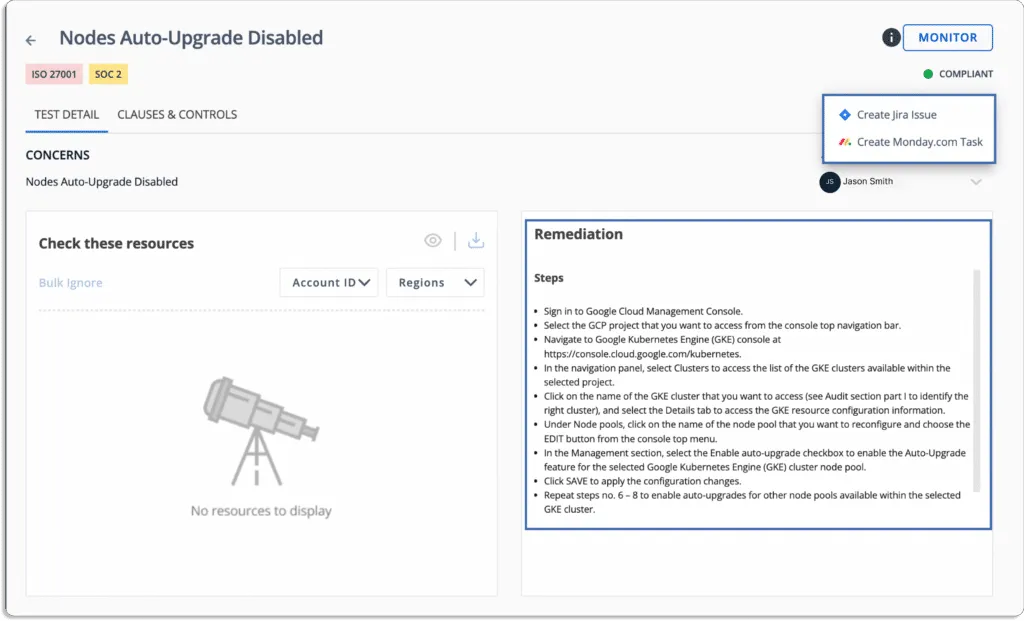
Thus, you can fix cloud misconfigurations preemptively before they are exploited by a malicious agent.
Apart from providing action items for resolving each issues, Scut comes with task management and workflow management capabilities.
Scrut Cloud Security helps drive accountability for remediation. We believe that every control should have an owner responsible for all the misconfigurations associated with that control. This practice ensures that if any security or compliance issues arise, it gets resolved within time.
In Scrut, you can assign every test to an owner who would be responsible for resolving it.
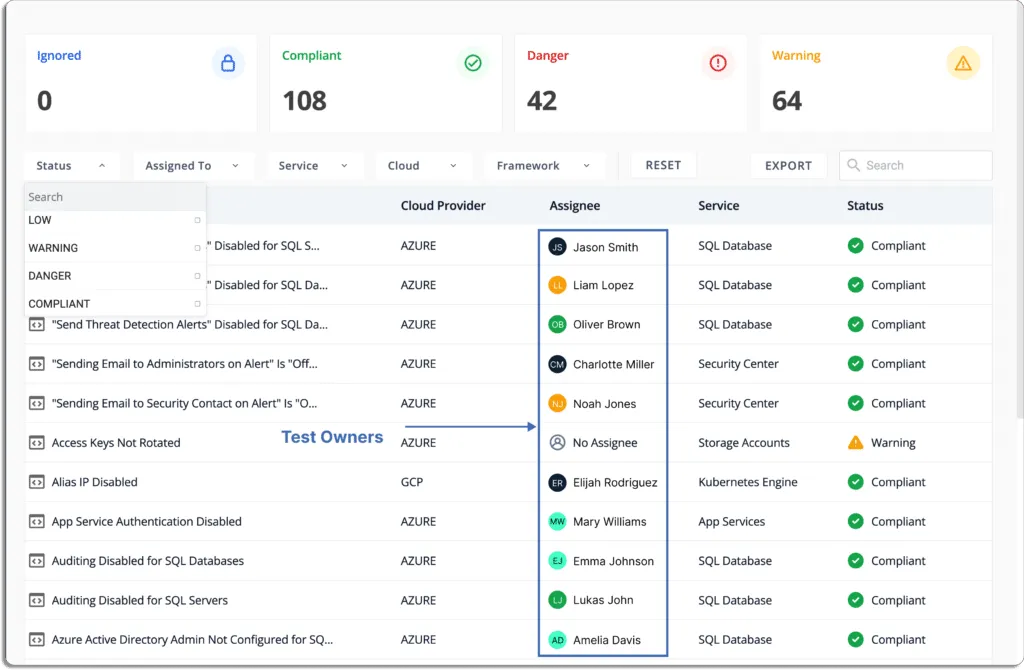
They can delegate these resources to their team members.
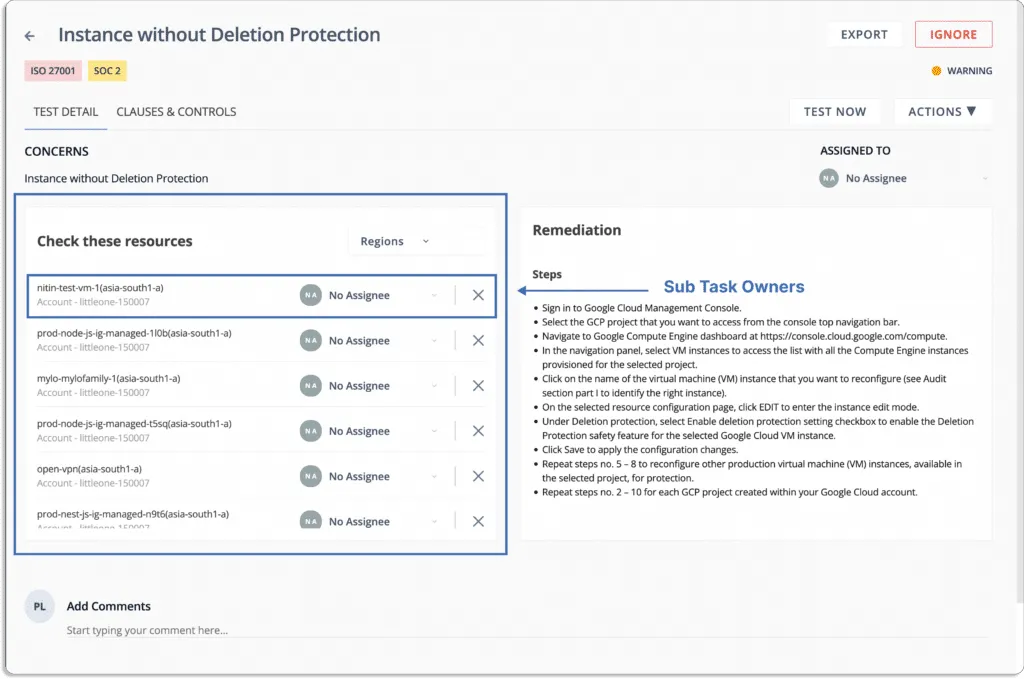
When any deviation from security policy occurs, the notifications can directly be sent on your existing communication platform, like Slack.
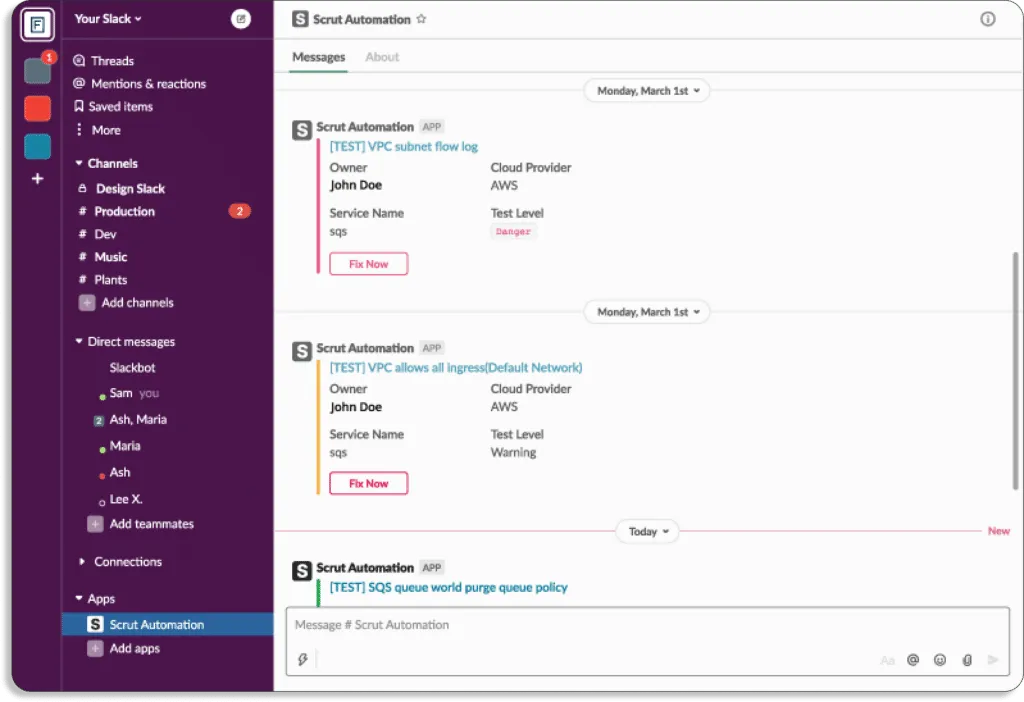
Additionally, Scrut allows you to create tickets for misconfigurations in your IT service management tools, like Jira, directly from the platform.
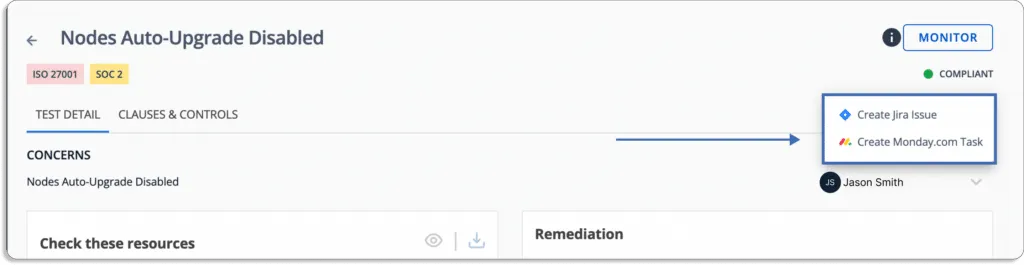
5. Does it help you stay compliant with the required security and privacy frameworks?
The capability of CSPM tools to evaluate a company’s cloud infrastructure against different industry and regulatory requirements is another crucial feature.
If your organization has specific regulatory requirements, you should go with a CSPM solution that supports those frameworks.
You also need to consider how it will benefit you during audits. An effective tool for managing cloud security posture will perform continuous compliance checks to detect any system misconfiguration.
Therefore, you should consider how the CSPM tool can assist you in adhering to the required privacy and security requirements. Compliances you need to comply with depend on the regions you want to operate in, your sector, and the preferences of your customers.
For example,
- If you are a software company selling in the USA market, you must be compliant with SOC 2.
- If you are a healthtech company operating in the USA market, you must be compliant with HIPAA.
- If you store data of EU users, you must be compliant with GDPR.
- If you store debit or credit card information, you must comply with PCI DSS.
Many CSPM tools come with out-of-the-box support for these popular frameworks. For example, Scrut supports over 20 compliance frameworks.
Furthermore, it maps controls with their respective frameworks. This helps your auditors to easily find the test you have done, see the correction task when it was carried out, and by whom, without any intervention from the DevOps team.
Let’s say you’re going for ISO 27001 audit.
As shown in the below screenshot, your auditor can directly see the test you have done (A.9.1.1).
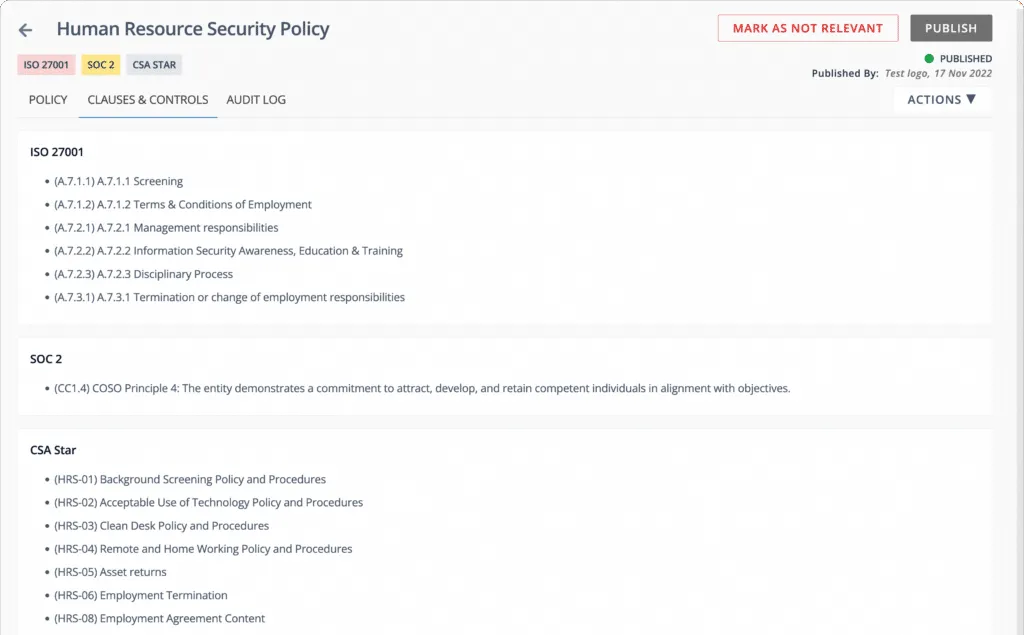
Moreover, Scrut gives you 100% coverage, rather than sample coverage, which increases the credibility of your organization.
Ultimately, this helps you complete the audit faster.
How Scrut Cloud Security Helped Typesense Improve their Cloud Security Posture for SOC 2 Type 2 (A Case Study)
Now, let’s discuss how Typesense improved their cloud security posture with Scrut Cloud Security.
Typesense, now our customer, is an open source search engine. They reached out to us with the goal of getting compliant with SOC 2 Type 2.
They needed visibility into their cloud risks, to be able to build a strong cloud posture before undergoing the audit. However, they discovered that it was challenging to monitor their AWS infrastructure due to the enormous number (in thousands) of EC2 instances.
With quick, agentless deployment, Scrut Cloud Security relieved them from the complexity of monitoring their cloud environment.
As a result, they were able to successfully finish their SOC 2 audit at a 5x faster rate.
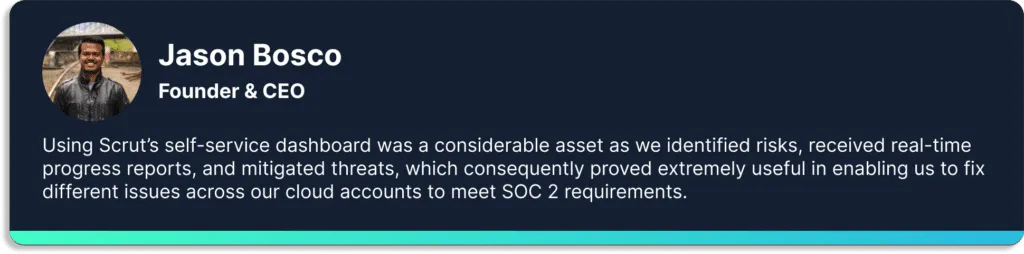
Here is what Jason Bosco, founder, and CEO of Typesense, has to say about Scrut.
Getting Started with Scrut Cloud Security
Now, if you are looking to try Scrut, you can book a demo.
Getting started with Scrut is easy and quick.

Table of contents


















