Choose risk-first compliance that’s always on, built for you.
Go back to blogs
How To Choose A CAASM Software
Last updated on
February 5, 2025
8
min. read

As organizations deal with larger and more complex environments, they often face challenges in gaining a comprehensive view of their entire infrastructure, especially when transitioning to cloud-based systems. This is where cyber asset attack surface management (CAASM) becomes crucial. CAASM solutions utilize API integrations to connect with existing data sources and effectively identify and address security vulnerabilities automatically.
With numerous CAASM tools available in the market, it can be overwhelming to determine where to start. This article aims to assist you in evaluating CAASM platforms by outlining key factors to consider.
Cyber Asset Attack Surface Management: An Overview
Cyber asset attack surface management involves a range of activities to constantly assess and improve your digital infrastructure’s security. This includes the ongoing identification, classification, mapping, and analysis of all components within your network, devices, data, and systems.
Whether they are located on-premises or in the cloud, every asset is taken into consideration. The process involves categorizing these assets, giving priority to high-risk areas, and addressing any vulnerabilities identified. Additionally, continuous monitoring of the attack surface is implemented to ensure a proactive approach to security
Cyber asset attack surface management serves as the initial phase in establishing an asset-centric approach for an organization’s attack surface management strategy. This emerging technology aids security teams in addressing challenges related to asset visibility and vulnerability exposure. By utilizing API connections with current tools, it allows organizations to gain comprehensive visibility into their assets. Through querying aggregated data, they can identify vulnerabilities and security gaps, ultimately enabling them to address and resolve these issues effectively.
CAASM solutions integrate data from various tools and sources to provide a comprehensive and continuous understanding of an organization’s entire attack surface. By eliminating blind spots, it enables security operations teams to implement cybersecurity measures and manage risks effectively quickly.
CAASM gathers assets from solutions focusing on specific areas such as endpoints, servers, devices, and applications. Through searches, users can identify any gaps in security tool coverage, such as vulnerability assessment and endpoint detection and response (EDR) solutions, by combining internal and external cyber assets.
Questions You Need To Ask While Selecting A CAASM Software
To ensure comprehensive coverage of your organization’s attack surface, it is important to find software that can effectively handle various aspects. This includes discovering, monitoring, and managing all relevant assets, such as networks, applications, and cloud services. Look for software that offers features like automated asset discovery, vulnerability scanning, and integration.
The following questions will assist users in choosing a cyber asset attack surface management software that meets their organization’s security goals and requirements, making the decision-making process more clear and informed.
An effective CAASM system should be capable of automation and scalability features. Determine how much automation the software offers. Scalability is critical for large organisations or those with complicated infrastructures, as the software must handle a huge number of assets while also providing efficient scanning and analysis.
1. Is the CAASM software compatible with your existing tools for integration?
When selecting a CAASM software, it is important to ensure that it can seamlessly integrate with your current tools, such as vulnerability management systems, security information and event management (SIEM) solutions, and other relevant security technologies. This integration capability allows for discovering assets across your distributed system, regardless of location.
Additionally, verifying that the software is compatible with your company’s operating systems, databases, network architecture, and other essential components is crucial
One notable CAASM tool that fulfils these integration requirements is Scrut. Scrut simplifies the evidence-collection process by providing a comprehensive solution with over 70 integrations. It effectively connects with various application environments, including HRMS and endpoint management systems, as well as other technologies, streamlining the automation of human evidence collection.
Scrut seamlessly integrates with SIEM technologies like Datadog and Splunk and XDR solutions such as Crowdstrike. Furthermore, it integrates with vulnerability management tools like Qualys, AWS Inspector, and Tenable
2. Can the CAASM tool help with risk identification and prioritization?
When selecting a CAASM tool, it is crucial to ensure that it can effectively identify and prioritize critical hazards. Look for a software solution that offers risk prioritization capabilities, allowing you to detect and evaluate vulnerabilities in your assets. Consider the extent and depth of vulnerability coverage, as well as the quality and timeliness of vulnerability updates
The Scrut CAASM solution assists security teams in identifying and prioritizing key risks. The platform monitors the cyber asset environment for issues affecting business-critical assets and the broader infrastructure. The platform identifies highly significant and risky assets, aids users in prioritizing these risks, and provides recommendations for remediation.
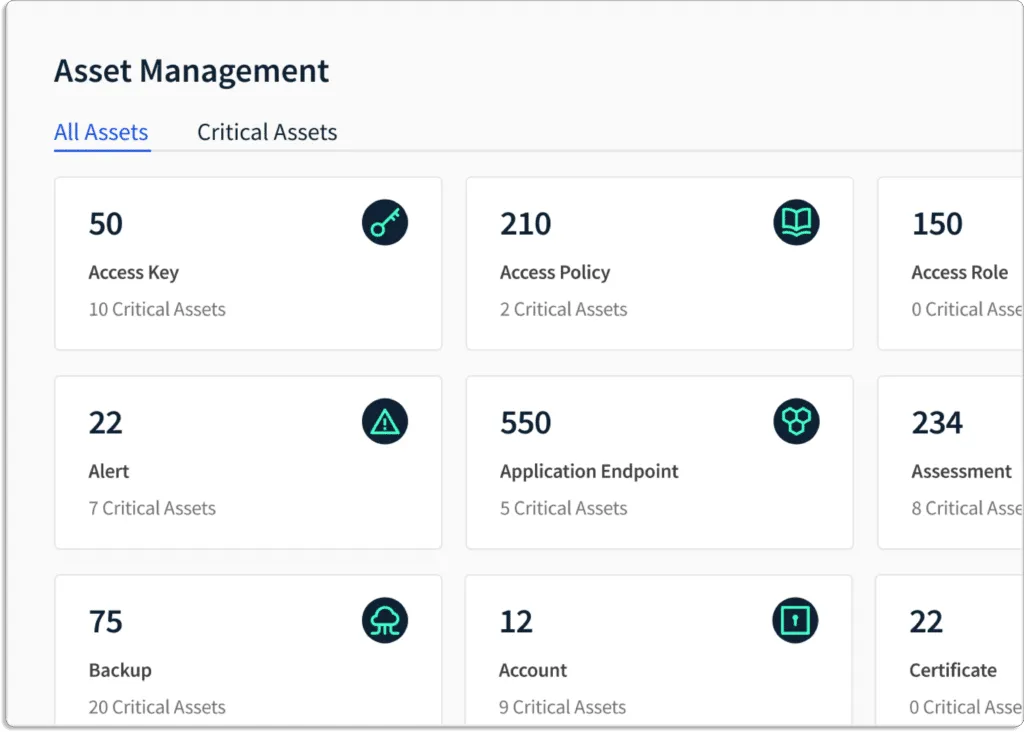
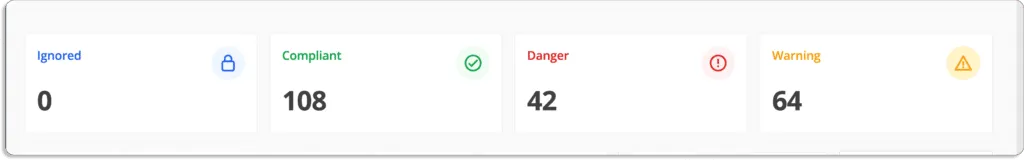
It enables you to focus on the important problems, as shown in the screenshot below.
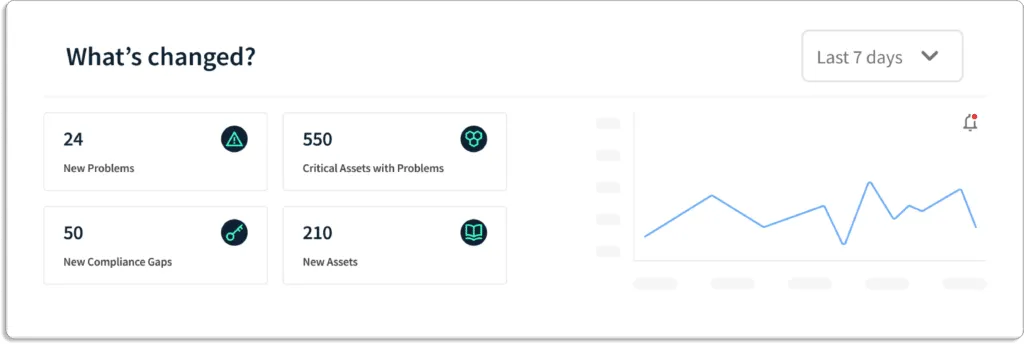
With Scrut, you can concentrate on addressing the most important problems at hand. The tool presents data in a graphical format for easy visualization, allowing you to quickly identify specific security vulnerabilities in your environment and address any security and compliance concerns.
Moreover, Scrut offers a unified view of all risks, categorizing them based on their status (Ignored, Compliant, Danger, Warning), helping you determine which issues should be addressed first.
3. Can It Facilitate Asset Data Discovery?
The software should provide complete visibility into your organization’s asset universe and should discover all asset data. The solution should assist users in managing all internal and external assets efficiently and serve as a single source of truth for asset data. CAASM automatically develops a complete and up-to-date asset inventory by continuously detecting and combining all of your cyber assets.
Scrut platform brings together and standardizes asset data from various cloud systems. The solution offers a unified view of all cloud entities, allowing users to identify essential business assets and prioritize risks across your public, private, hybrid, and multi-cloud settings.
4. Does The Tool Provide Continuous Compliance Support?
Consider whether the solution meets your industry’s regulatory needs. Look for capabilities that can assist you in remaining in compliance with regulatory regulations, such as the General Data Protection Regulation (GDPR), the Payment Card Industry Data Security Standard (PCI DSS), or the Health Insurance Portability and Accountability Act (HIPAA), etc.
Scrut CAASM ensures the necessary security and compliance controls are implemented once essential assets are identified. Scrut provides a unified experience for ensuring compliance with numerous information security frameworks. The Scrut platform supports various frameworks, including: SOC 2, SOC 3, ISO 27001, ISO 27701, ISO 27017, ISO 27018, ISO 22301, ISO 20000-1, GDPR, HIPAA, HiTrust, FedRamp, CMMC, CCPA, PCI DSS, CSA Star, CMMI – DEV, CMMI – SVC, GLB, NIST 800 171.
5. Does The Tool Provide Cloud Security Monitoring?
One of the important features of the CAASM platform is continuous cloud security monitoring. A CAASM platform should continuously monitor your assets for newly identified security vulnerabilities, flaws, misconfiguration, and compliance concerns. Continuous security monitoring is crucial as it enables organizations to review their overall security architecture and ensure compliance with internal information security policies.
Additionally, the solution should also offer the ongoing Centre for Internet Security (CIS) Foundations Benchmarking, which covers logging, access control, monitoring, identity management, networking, and other areas.
Let’s explore the functionality of Scrut Cloud Security.
Scrut is designed to provide ongoing monitoring of cloud security and identify any misconfigurations to help users maintain compliance and protect their data proactively. By leveraging the tool, you can ensure that your cloud accounts meet the required compliance standards.
Scrut evaluates your cloud configurations against 200+ cloud control across CIS benchmarks to maintain a robust information security posture. The platform supports all key service types, such as serverless, containers, and Kubernetes, enabling you to implement full-stack security for all your cloud-native deployments.
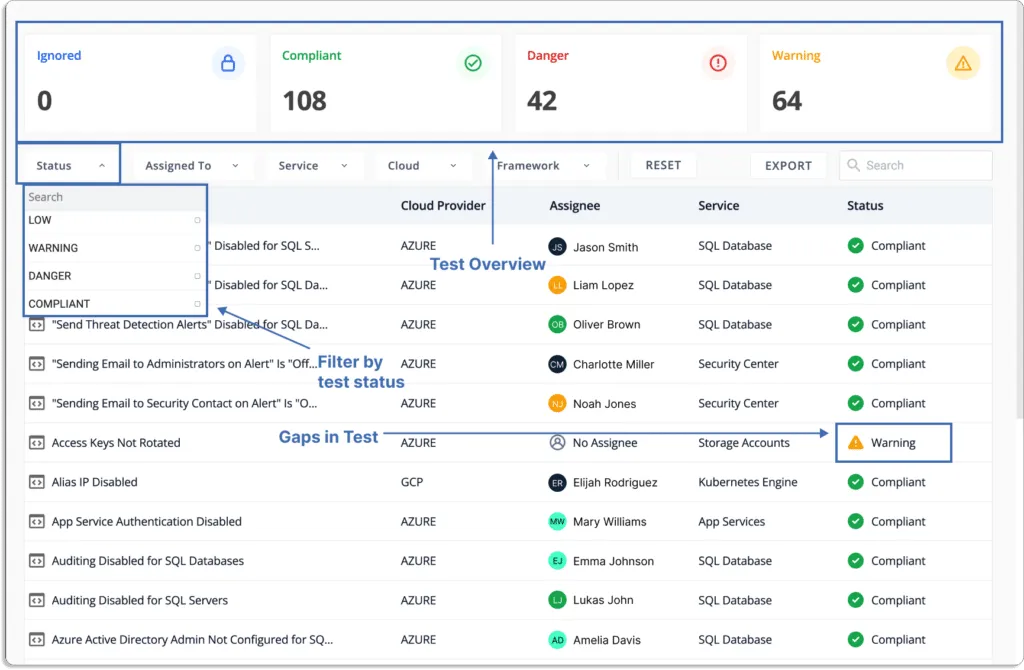
The tool provides actionable items for solving problems to assist users in resolving difficulties quickly, as shown in the screenshot below.
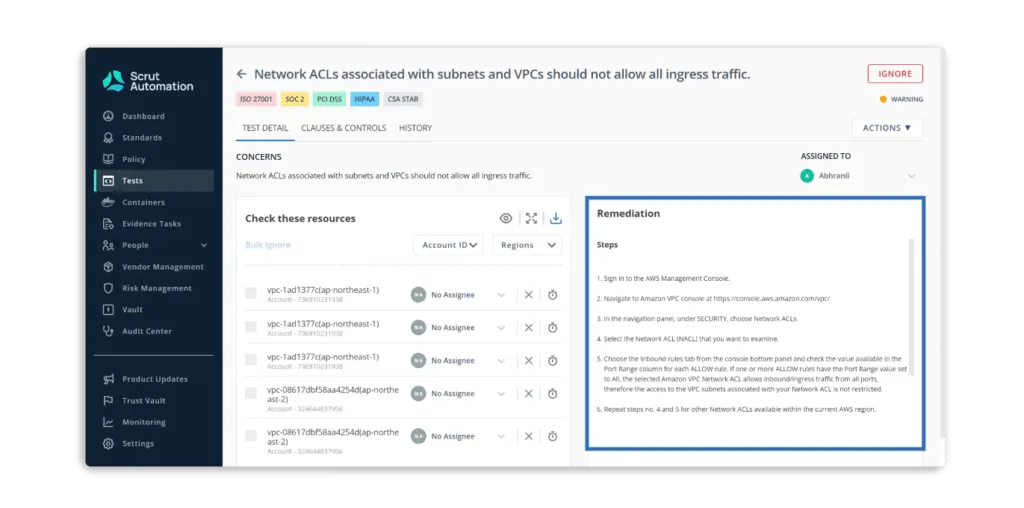
Scrut CAASM helps users effectively identify and gather all their cyber assets, no matter where they are stored. It enhances security control coverage and enables customized, automated responses by providing complete visibility into both external and internal attack areas. Click here to learn more about Scrut CAASM software.

Table of contents